Configure and Activate SASE Gateway Devices
![]() For supported software information, click here.
For supported software information, click here.
This article provides step-by-step procedures for configuring and activating SASE gateway devices on supported Versa Networks hardware appliances.
To configure and activate SASE gateway devices, you do the following:
- Create a site using a software license.
- Create a SASE gateway device configuration for the site. When you save the device configuration, it is stored in the Titan cloud portal. You should configure WAN interfaces, and add or change any required LAN and WAN ports before deployment, because you cannot do so after you activate the SASE gateway.
- Deploy the device configuration to the Versa Controller node, to inform the Controller node that the configuration exists.
- Activate the appliance.
Create a Site for Private SASE Gateway
To create a site for the CSG770 model, CSG1000 series, CSG2500 model, CSG5000 model, and vCSG series appliances:
- Log in to Titan Portal as an MSP.
- Enter your username and password, and then click Login.
- In the Organizations dashboard, click the MSP provider organization in the grid.

- Click Configure in the left menu bar to display the Configure dashboard.
- Click one of the license package icons to display the available license packages. To add the site to the honeycomb, drag the license package onto the dashboard.
- CSG700 Series
- CSG1000 Series
- CSG2000 Series
- CSG5000 Series
- cCSG Series
- vCSG Series

- In the New Site: Configuration window, select a region and then click Continue.

- Enter information for the following fields, and then click Next.

Field Description Site Name Enter a name for site. Address Enter the street address, zip code, city, state, and country. Latitude and Longitude - Autogenerate—Click the Autogenerate toggle to enable the determination of latitude and longitude coordinates automatically.
- Manual—Click the Manual toggle to enable the determination of latitude and longitude coordinates manually. This is the default.
Topology Click to configure the site role:
- Configure as Hub—Configure the device as a hub in a hub-and-spoke topology.
- Configure as Hub Controller—Configure the device as a hub controller in a hub-and-spoke topology. This device takes up a dual role of a hub and a Controller node. This function is typically required when branches are connected to a private MPLS network that has no direct access to the Versa Networks–hosted Controller node in the public internet.
- Configure as Spoke—A hub must already be configured to configure a spoke.
- Full Mesh—Configure the device as part of a full-mesh topology
HA Mode Click to configure two appliances in a high availability (HA) pair. For more information, see Configure and Activate a High Availability Site. Service (Group of Fields) - Service Type
Displays the type of the device. - Device Name
Enter a name for the device. A user cannot change the device name after creating the device. - Device Model
Enter the device model. - Serial Number
Enter the serial number of the device, which is printed on the bottom of the CSG appliance. - Image Version
(Optional.) Select the Versa Operating SystemTM (VOSTM) software version of the device. The user must select the software version before deploying the device. For SASE gateway and remote access VPN deployments, the VOS software version must be 21.3.x or higher. Contact Versa Networks Customer Support before you upgrade SASE gateway or remote access VPN devices. If SASE gateway and remote access VPN devices are up and running with the latest Release 21.3.x, and if you undeploy and re-activate the same devices, you must perform a software upgrade for these devices because the devices come up running the latest Release 21.2.x latest software. If the devices are up and running older versions of Release 21.2.x, you must upgrade the devices to the latest Release 21.3.x software. - Service Add-ons
Select the services to add to the site. Site Description Enter a text description for the site. The description can be a maximum of 128 characters. Note that for HA devices, the site description is common for both primary and secondary devices. - Click Save. Titan Portal saves the new site information in the Titan cloud and creates a honeycomb for the site.
Configure a Private SASE Gateway Device
- In the Organizations dashboard, click the MSP organization in the grid.

- In the Configure dashboard, hover over the device in the honeycomb and click Configure to open the site information window.

- Click Next to open the Configuration > Network screen, and then click the WAN box.

- In the Network > WAN screen, enter the static IP address for the WAN1 Port0 interface. Note that you cannot configure DHCP on a SASE gateway WAN interface.

- Click a circuit role. MSPs can configure WAN interface priorities for SASE gateway tenants and can change the priority of a WAN interface whenever required. For an existing SASE gateway tenant, you publish the configuration to inherit the WAN priority from the provider. For a new tenant, the WAN priority configuration is inherited from the provider.
- Hot Standby—For internet-bound traffic, a hot-standby circuit has a lower preference than the primary circuit. For SD-WAN traffic, the circuit has the same default preference as the primary circuit. You can create rules to steer traffic to the interface.
- Primary—Interface that sends SD-WAN and DIA traffic.
- Click Advance Configurations (Customized). Select the gateway and click Continue. If the circuit is and internet circuit, other branches in the network can use this circuit for remote internet breakout. If the link is MPLS, other branches can use this link to communicate with sites connected on the MPLS underlay network.

- Click Save.
- Click the LAN box to open the Network > LAN > Ethernet Ports screen.

- Select LAN1 Port1, and then click the delete icon to delete the LAN port.

- Go to Network > WAN and click +WAN to configure Port1 as the WAN2 secondary port.

- Click Continue.

- Click Save.
- Click the LAN box to open the Network > LAN > Ethernet Ports screen.

- Click the VLAN Tagging toggle to enable the VLAN in the SASE gateway LAN interface to connect the server. A user must enable VLANs on all required LAN ports for SASE gateway before the device is deployed and activated. A user cannot enable VLANs after activating a SASE gateway.
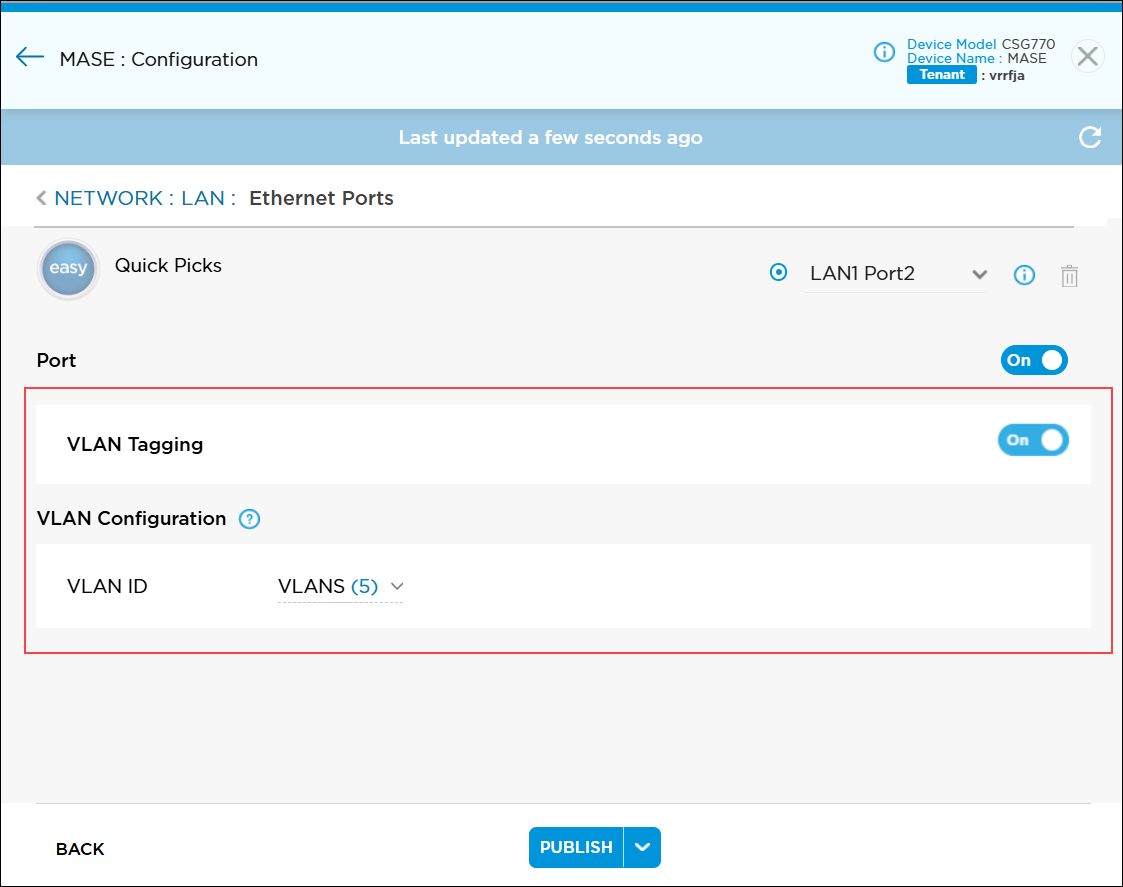
- Click Select VLAN ID and then click the
 icon.
icon.

- In the Add VLAN ID popup window, enter information for the following fields.

Field Description VLAN Name (Required) Enter a name for the virtual LAN. VLAN ID (Required) Enter a name for the virtual LAN. MTU (Required) Enter the maximum transmission unit size, in bytes, of the largest protocol data unit that the port can receive or transmit. Note that in Release 10.0, you cannot change the default MTU value.
Range: 72 through 9000 bytes
Default: 1500 bytesIP Address/Mask (Required) Enter the IP address and prefix length. The prefix length must be /25. VRRP Click the slider to enable VRRP. - Virtual IP Address
Enter a valid IPv4 address. The virtual IP address and VLAN IP address/mask must be in the same IP subnet. - Priority
Enter the priority to assign to the interface. The interface with the higher or highest priority becomes the VRRP active router.
When you configure a VRRP priority value, be aware that value can be reduced by various objects that VRRP can track, such as interfaces, routes, monitor objects, and HA state. When you choose a priority value, you must make sure that you account for a worst-case scenario so that the priority never goes below 0. As an example, consider a VRRP group that is configured on the interface LAN1Port0 (vni-0/0.0) with priority of 200 and that is tracking the interface LAN1Port1 (vni-0/1.0), which has a priority cost of 20. When the LAN1Port1 (vni-0/1.0) goes down, its priority cost is subtracted from the configured priority of 200. As a result, the current (dynamic) priority becomes (200 – 20), or 180. In this example, the LAN1Port1 (vni-0/1.0) interface is the tracking object.
Range: 1 through 255
Default: 100
DHCP Server Click to configure DHCP server settings and DHCP client options. For more information, see Configure DHCP Settings and Configure Custom DHCP Options. DHCP Relay Click to configure DHCP relay settings. For more information, see Configure DHCP Relay Settings. - Click
 and then click Continue.
and then click Continue. - Click Save, and then click the down arrow next to Save to display the Deploy popup window.
- Click Deploy. Note that you can deploy a SASE gateway like a normal device and you can activate it using the global ZTP, WiFi, and Versable methods. To deploy and activate a device, see Deploy a Device Configuration and Activate an Appliance.
Note: In a private gateway, locking and unlocking devices are not supported, and you cannot reassign, add, or delete LAN or WAN interface after the port is activated. Also, you cannot undeploy and redeploy the SASE gateway after it is activated. To redeploy a SASE gateway, you must first deactivate the gateway.
Install Certificates for VSA
A certificate authority (CA) is an entity that issues digital certificates that are used to verify the ownership of a public key. The digital certificates allow a party to trust the signature that is made by a private key that corresponds to the certified public key.
After a Titan device requests a certificate from a CA server, the CA server issues the certificate. You then need to upload the certificate to the CA database so that it can be used for verification.
Before you upload a CA certificate, you must upload a key file with the extension .key.
The key file, certificate file, and CA chain file that you import to the private SASE gateway must have the same name as the SASE gateway or remote access VPN device FQDN. For example, if the private SASE gateway FQDN is SASEQA1test.com, the filenames must be as follows:
- Key filename—SASEQA1test.com.key
- Certificate filename—SASEQA1test.com.crt
- CA chain filename—ca.SASEQA1test.com.crt (The CA chain filename is a combination of root CA and intermediate CA)
To upload a key file:
- Locate the device in the grid, and then click the 3-dot icon in the Action column to display available actions.

- Click Upload CA Certificates and then click Upload Key.

- In the Add Key popup window, enter the following information.

- Enter a key name and password.
- Click Browse file to select the key file to upload. The file must be in .key format.
- Click System Key to store the key file at system level for SASE gateway and remote access VPN. Selecting this option is mandatory. Note that you must select System Key after you upload the key file.
- Click Add.
- Click Upload CA Certificates, and then click Upload Certificate.

- In the Add CA Certificate popup window, enter the following information.

- Enter a certificate name.
- Select the key file name.
- Click Browse file to select the CA certificate file to upload. The file must be in .crt, .cer, or .pem format.
- Click System Certificate store the certificate file at system level for SASE gateway and remote access VPN. Selecting this option is mandatory. Note that you must select System Certificate after you upload the certificate file.
- Click Add. The certificate file is displayed.
- Click the
 icon to download the file.
icon to download the file.
- Click Upload CA Certificates and then click Upload CA Chain.

- In the Add CA Chain popup window, enter the following information.

- Enter a CA chain name.
- Click Browse file to select the CA chain file to upload. The file must be in .crt format.
- Click System CA Chain to store the CA chain file at system level for SASE gateway and remote access VPN. Selecting this option is mandatory. Note that you must select System CA Chain after you upload the CA chain file.
- Click Add.
Manage Captive Portal Ports
To configure captive portal ports:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb, and click Configure to open the site information window.
- Select the Miscellaneous tab, and then click the Manage Captive Portal link.

- In the Captive Portal Port Number popup window, enter information for the following fields and then click Continue. You must configure all WAN ports with a WAN port captive portal configuration.

Field Description Network Name (Required) Click Please Select. In the Network Name popup window, click a WAN network. HTTP Enter the HTTP port number to use to redirect captive portal pages over HTTP. The default port is 44990. For a SASE gateway, use port 80. HTTPS Enter the HTTPS port number to use to redirect captive portal pages over HTTPS. The default port is 44991. For a SASE gateway, use port 443. - Click Continue. For more information, see Configure Miscellaneous Parameters.
Add the SASE Gateway Service
An MSP, a store admin, or a reseller provider organization can select cloud gateway services and order the VSPA and VSIA services. You can select available SASE gateways and advanced services such as VLAN and port details. Note that you can select cloud gateway services as a SASE gateway to get the service. If you have already added a SASE gateway, but then you cannot select the cloud gateway option.
After you order cloud gateway service for a tenant, you can upgrade the service tier, users, or bandwidth. For more information, see Upgrade or Renew SASE Gateway Licenses.
If a store admin adds a tenant to a SASE gateway, the tenant onboarding progress can be viewed from the task list of the individual organization, not from the store admin organization task list.
To add a SASE gateway service:
- In the Organizations dashboard, locate the organization in the grid, click the 3-dot icon, and then click Add Devices.

- In the Add Device Details popup window, click the Cloud Gateway button.
- Select gateway type SASE, and then enter information for the following fields.

Field Description Service Tier Select the service tier:
- Essential—Only firewall and URL filtering are available.
- Professional—All security services are available, including firewall, URL filtering, antivirus, IPS, and TLS decryption.
License Type Select the license type:
- User
- Number of Users—Enter the number of authorized users. You must add minimum 50 users. For a local user, the maximum number of users is 255. In User license type, a user can select Versa Secure Internet Access (VSIA) service and Versa Secure Private Access (VSPA) service.
- Bandwidth
- SASE (VSIA and VSPA) Bandwidth—Select the combined SASE bandwidth for VSIA and VSPA services. If you select 250 Mbps, the total allocated bandwidth for VSIA and VSPA services is 250 Mbps. In Bandwidth license type, VSIA and VSPA services are selected by default.

- SASE (VSIA and VSPA) Bandwidth—Select the combined SASE bandwidth for VSIA and VSPA services. If you select 250 Mbps, the total allocated bandwidth for VSIA and VSPA services is 250 Mbps. In Bandwidth license type, VSIA and VSPA services are selected by default.
Gateway Region Select the SASE gateway regions.
If you do not select any VLAN ID, the organization ID is taken as the VLAN ID by default. You must deploy and activate all SASE gateways with the similar LAN port numbers. Otherwise, the system configures the tenant on the first available LAN port.
- Advanced
Click to enter the VLAN ID and port details for the SASE gateway services. If you do not select a VLAN ID, the organization ID is used, by default, as the VLAN ID.

When you add a new gateway to an existing tenant and you want to assign a VLAN ID to the gateway, because VRRP is enabled on the LAN, you must enter the same VLAN ID and port used for the tenant. To determine the VLAN ID assigned to a tenant, navigate to Network > LAN > LAN Profiles > VLAN Profile, and then select the VLAN in the VLAN Tags section.
SASE Gateway Options For the User license type, select the SASE gateway options:
- Versa Endpoint Client Service
- Versa Secure Private Access (VSPA) Service
Subscription Duration Click to select the length of the subscription:
- 1 year
- 3 years
- Click Submit.
Configure a VLAN Profile and VRRP for SASE Gateway Tenants
The Virtual Router Redundancy Protocol (VRRP) is a network protocol used to provide high availability (HA) by creating a virtual IP address that multiple routers share. VRRP allows you to have one or more backup routers when you are using a statically configured router on a LAN. If the active, or master, router fails, a backup router takes over and continues to forward packets. For VRRP, you configure a virtual IP address, that is shared among two or more routers. One router is designated the master and the others are backup routers. If the master router fails, the virtual IP address is mapped to the IP address of one of the backup routers.
The virtual IP address serves as a default gateway for hosts on a LAN. If the primary router fails, a backup router takes over the virtual IP address, ensuring uninterrupted connectivity for devices. VRRP helps enhance network reliability and minimize downtime by providing a seamless transition between active and standby routers.
When an active router goes down, VRRP switches over to a backup router in 3 seconds. If all the WAN connections of an active router go down, VRRP switches over to a backup router in 22 seconds.
If you disable VRRP, ensure that you change the IP address in the subnet, and then commit the change to having duplicate IP addresses when you publish the configuration.
Before you configure VRRP for an existing SASE gateway in Titan Portal, you must configure an IP SLA monitor in Versa Director with the following parameters. For more information, see Configure IP SLA Monitor Objects. Titan Portal creates IP SLA monitor automatically when a user deploys and activates a new SASE gateway. If you do not have access to Versa Director, contact Versa Customer Support.
- Name—Name the IP SLA monitor LAN.
- Monitor Type—Select ICMP for the type of packets to send to the IP address.
- Routing Instance—Select the routing instance as Provider LAN-VR routing instance.
- IP address—By default, Titan Portal supports LAN monitor IP address 8.8.8.8. If required, user can change the IP address in Versa Director, and commit the configuration.
Virtual routing and forwarding (VRF) is a multisegmented network topology that is part of the organization's VPN. A VRF allows you to configure and maintain more than one instance of the routing and forwarding table in the same router. To configure routing, you must associate a VRF with a specific LAN port.
To use custom VRFs for a tenant in the SASE gateway device, you must lock the device, create and attach a custom VRF to the LAN port for the tenant, and then publish the configuration. When you publish the configuration, the custom VRF displays in the SASE gateway device for the MSP to add the custom VRF for the tenant. For more information, see Configure LAN Connections.
Only an MSP can enable multiple custom VRFs on the SASE gateway device for a tenant and attach it to the default LAN port. The default LAN port is the port for which the default VLAN is associated when you order the SASE gateway services for tenants. This LAN port is the default interface configured with the default VRF.
An MSP can create a new VLAN with a custom VRF when configuring the LAN profile and Ethernet from the tenant-level. An MSP can select the custom VRF on the SASE gateway tenant in the tenant modification mode. You can select different tenants in a provider organization and select different VRFs to the tenants. Note that a custom VRF cannot be added to a provider organization.
After the VRF option is enabled for a tenant organization, an administrator cannot disable it using the create or edit organization window. By default, one VRF is created with the name of the organization and all the initial LAN ports are associated with this VRF. You cannot delete the default LAN-VRF after it is created.
Note: An MSP, store administrator, or a provider must contact Versa Customer Support to delete a SASE gateway tenant with a custom VRF configured.
An MSP or a customer must contact Versa Customer Support to delete a custom VRF associated with the SASE gateway.
To configure VRRP on a SASE gateway LAN interface:
- Log in to Titan Portal as a store admin, MSP, or reseller.
- Enter your username and password, and then click Login.
- In the Organizations dashboard, click the MSP provider organization in the grid.

- In the Configure dashboard, hover over the device in the honeycomb and click Configure.

- In the configuration window, click Tenant, select the tenant on which to configure VRRP, and then click Continue.

- Click the LAN box to open the Network > LAN screen.

- Click LAN Profiles to configure a VLAN profile and VRRP.

- In the Network > LAN > LAN Profiles > VLAN Profile screen, enter information for the following fields.

Field Description VLAN Name (Required) Enter a name for the virtual LAN. VLAN ID (Required) Enter a virtual LAN identifier.
Range: 0 through 4094
Default: None
MTU Enter the maximum transmission unit size, in bytes, of the largest protocol data unit that the port can receive or transmit. Note that in Release 10.0, you cannot change the default MTU value.
Range: 72 through 9000 bytes
Default: 1500 bytesVRF (Required) Select a VRF instance. You must add the VRF only to the default LAN port for which default VLAN is associated when you order the SASE gateway services for a tenant. To create a custom VRF, see Configure LAN Connections.
An MSP, store administrator, or a provider must contact Versa Customer Support to delete a SASE gateway tenant with a custom VRF configured.
IP Address/Mask (Required) Enter the IP address and prefix length. The prefix length must be /25. VRRP Click the slider to enable VRRP. Virtual IP Address
Enter a valid IPv4 address. The virtual IP address and VLAN IP address and mask must be in the same IP subnet. Priority
Enter the priority to assign to the interface. The interface with the higher or highest priority becomes the VRRP active router.
When you configure a VRRP priority value, be aware that value can be reduced by various objects that VRRP can track, such as interfaces, routes, monitor objects, and HA state. When you choose a priority value, you must make sure that you account for a worst-case scenario so that the priority never goes below 0. As an example, consider a VRRP group that is configured on the interface LAN1Port0 (vni-0/0.0) with priority of 200 and that is tracking the interface LAN1Port1 (vni-0/1.0), which has a priority cost of 20. When the LAN1Port1 (vni-0/1.0) goes down, its priority cost is subtracted from the configured priority of 200. As a result, the current (dynamic) priority becomes (200 – 20), or 180. In this example, the LAN1Port1 (vni-0/1.0) interface is the tracking object.
Range: 1 through 255
Default: 100
-
Click Add VLAN and then click Publish.
To enable VRRP in an existing VLAN profile:
- Navigate to Network > LAN > LAN Profiles > VLAN Profile.
- In the VLAN Tags section, select the VLAN profile on which to enable VRRP, and then enter information for the following fields.

Field Description VRRP Click the VRRP slider to enable VRRP. Virtual IP Address Enter a valid IPv4 address. The virtual IP address and VLAN IP address and mask must be in the same IP subnet. Priority Enter the priority to assign to the interface. The interface with the higher or highest priority becomes the VRRP active router.
Range: 1 through 255
Default: 100
- Click Update VLAN, and then click Publish.
Add Multiple VLANs for SASE Gateway Tenants
An MSP, a store admin, or a reseller with provider organization can activate a private gateway device and purchase SASE gateway services (cloud gateway) for customers.
- Log in to Titan Portal as an MSP.
- In the Organization dashboard, select the organization.

- In the Configure dashboard, click Configure.

- In the configuration window, click Tenant, select the Tenant, and then click Continue.

- Click the LAN box to open the Network > LAN > Ethernet Ports screen.

- Click the VLAN Tagging toggle to enable VLAN in SASE gateway LAN interface to connect the server.

- Click Select VLAN ID and then click the
 icon.
icon.

- In the Add VLAN ID popup window, enter information for the following fields.

Field Description VLAN Name (Required) Enter a name for the virtual LAN. VLAN ID (Required) Enter the virtual LAN ID.
Range: 0 through 4094MTU (Required) Enter the maximum transmission unit size, in bytes, of the largest protocol data unit that the port can receive or transmit. Note that in Release 10.0, you cannot change the default MTU value.
Range: 72 through 9000 bytes
Default: 1500 bytesVRF (Required) Click the VRF list, and then select a VRF instance. You must add the VRF only to the default LAN port for which default VLAN is associated when you order the SASE gateway services for a tenant. To create a custom VRF, see Configure LAN Connections.
An MSP, store admin, or a provider must contact Versa Customer Support to delete a SASE gateway tenant with a custom VRF configured.
IP Address/Mask (Required) Enter the IP address and prefix length. The prefix length must be /25. VRRP Click the slider to enable VRRP. Virtual IP Address Enter a valid IPv4 address. The virtual IP address and VLAN IP address must be in the same IP subnet. Priority Enter the priority to assign to the interface. The interface with the higher or highest priority becomes the VRRP active router.
When you configure a VRRP priority value, be aware that value can be reduced by various objects that VRRP can track, such as interfaces, routes, monitor objects, and HA state. When you choose a priority value, you must make sure that you account for a worst-case scenario so that the priority never goes below 0. As an example, consider a VRRP group that is configured on the interface LAN1Port0 (vni-0/0.0) with priority of 200 and that is tracking the interface LAN1Port1 (vni-0/1.0), which has a priority cost of 20. When the LAN1Port1 (vni-0/1.0) goes down, its priority cost is subtracted from the configured priority of 200. As a result, the current (dynamic) priority becomes (200 – 20), or 180. In this example, the LAN1Port1 (vni-0/1.0) interface is the tracking object.
Range: 1 through 255
Default: 100
DHCP Server Click to configure DHCP server settings and DHCP client options. For more information, see Configure DHCP Settings and Configure Custom DHCP Options. DHCP Relay Click to configure DHCP relay settings. For more information, see Configure DHCP Relay Settings. - Click
 and then click Continue.
and then click Continue. - To add multiple VLANs to the tenant, repeat Steps 6 through 8.
Edit a SASE Gateway Site
You can edit the address of a site for deployed and activated devices. You must lock the device, edit the site address, and then publish the changes. The address is updated on the honeycomb view and in the map view of the site, and on Versa Director. For more information, see Configure and Activate a Site.
View SASE Gateway Licenses
To manage SASE gateway licenses and devices in the Titan Inventory:
- Click the Inventory icon in the left menu bar to open the Inventory dashboard.
- Select SASE Gateway in the DeviceType field the top of the screen.

Renew or Upgrade SASE Gateway Licenses
You must renew a SASE gateway license before the license expires. If a license has expired, the Configure and Inventory dashboards display the site with license expired status and the network configuration window displays in purple and has read access only. You must renew the license to make any changes to the device configuration.


To renew a SASE gateway license in the Titan Inventory:
- Log in as an MSP and select the tenant organization.
- Click the Inventory icon in the left menu bar to open the Inventory dashboard.
- Select SASE Gateway in the Device Type field.
- Click Renewal.

- In the Renewal popup window, enter the number of days to renew the license.

- Click Submit.
To upgrade a SASE gateway license in the Titan Inventory:
- Log in as an MSP and select the tenant organization.
- Click the Inventory icon in the left menu bar to open the Inventory dashboard.
- Select SASE Gateway in the Device Type field.
- Click Upgrade.

- In the Upgrade popup window, enter the following information.

Field Description Available Gateway Select the Available Gateway. Click Advanced option to enter the VLAN ID and port details for the multitenant gateway services. If you do not select any VLAN ID and port, the organization ID is taken as the VLAN ID and the first LAN port is taken as the port by default. If you are adding a new gateway to a tenant, you must enter the same tenant VLAN ID for the gateway.
VSIA and VSPA User (Group of Fields) - Service Tier
Select the tenant service tier to which to upgrade.
- Additional Number of Users
Enter the number of additional licenses required. - Click Submit.
Supported Software Information
Releases 11.2 and later support all content described in this article.
