Configure CASB Profiles
![]() For supported software information, click here.
For supported software information, click here.
Cloud Access Security Broker (CASB) is on-premises or cloud-based policy enforcement that secures the data flowing between users and cloud applications in order to comply with corporate and regulatory requirements. CASB applies enterprise security policies when users access cloud-based resources.
As more applications move to the cloud, CASB addresses the following challenges to securing data:
- Implement data-centric policies to authorize or control.
- Analyze data access and changes to data stored in software-as-a-service (SaaS) clouds.
- Implement access control for files, applications, and users.
- Identify user downloads, uploads, and file sharing.
In addition, CASB secures cloud services and access to direct cloud-to-cloud deployments.
The Versa Operating SystemTM (VOSTM) CASB functions as inline software, leveraging the VOS deep packet inspection (DPI) software to monitor user activity, enforce security policies, and provide granular access control for cloud applications. Versa Networks also supports API integration with SaaS applications. This API integration makes use of API calls to SaaS applications, inspects user activities and contents, enforces security policies, and provides granular access control for SaaS applications. The CASB action can match the risk level and activity of multiple cloud applications, and can allow, deny, or restrict access to shadow IT.
To enforce CASB security policies, you create one or more CASB profiles, specify match criteria for applications, and then associate CASB profiles with an internet protection rule. For Releases 12.1.1 and later, you add CASB rules to configure CASB profiles. You can also add constraint profiles to configure constraints from and to users or user groups. You associate constraint profiles with CASB profiles.
Versa inline CASB deployment features include:
- Support for ~80 SaaS applications; more applications and activities are added through continuous security package updates
- Used where it is possible to decrypt TLS
- Deployed through VOS
- Works through the Versa Cloud Gateway or an appliance running VOS, typically through a corporate network
- Granular actions—Login, upload, download, video, chat, and additional actions
- Operates at the network layer using a reverse proxy mechanism
- No additional authorization needed because this is a proxy
- Risk classification from extremely low to extremely high risk
- Complements API-DP
Note: If you use offline CASB, see Configure Offline CASB Profiles for more information.
To use CASB, you must be using premium security pack (SPack) Version 1939 or later.
Configure a Custom CASB Profile
For Releases 12.1.1 and later.
- Go to Configure > Security Service Edge > Real-Time Protection > Profiles.

The following screen displays.

- Select the Cloud Access Security Broker (CASB Inline) tab.
- To customize which columns display, click Select Columns, and then click Applications to display or hide the applications. Click Reset to return to the default columns settings. The options are:
- Rules
- Actions
- Select the CASB Profiles tab.
- Click the
 Add icon to create a profile. The Create Cloud Access Security Broker Profile screen displays.
Add icon to create a profile. The Create Cloud Access Security Broker Profile screen displays.

- In Step 1, Rules, click Add Rules to create CASB rules. You must add at least one rule to proceed. The Add CASB Rules screen displays. Each application has four icons to the right. Hover over these icons to see support information for Windows, Android, MacOS, and iOS.

- In Step 1, Applications, select one or more cloud applications for which you want to configure actions. You can also search for applications to select. For more information about supported applications, see Supported Applications and Activities, below.
- Click Next to go to Step 2, Activities. The screen displays the applications that you selected in Step 1, Applications.

- Select the application activities for which you want to configure actions.
- To add or remove applications, click Add/Remove Application. The Step 1, Application, screen displays again. You can now delete previously selected applications or add additional applications to the CASB rule.
- If you delete an application, click Next to return to the Step 2, Activities.
- If you add an application, click Next to return to the Step 2, Activities, select the activities for the new application.
- Click Next to go to Step 3, Constraints to select constraints for applications.

- Click Select Profile to select a constraint profile. The User Constraints Profile screen displays.

- Select a constraint profile and click Save. You can select only one constraint profile for a CASB rule. To create a new constraint profile, click
 Create New. For more information, see Configure Constraint Profiles, below.
Create New. For more information, see Configure Constraint Profiles, below. - In the Add CASB Rules screen, click Next to go to Step 4, Risk Level.

- Select the risk level, which can be Lowest Risk, Low Risk, Medium Risk, High Risk, and Highest Risk. A color is associated with each selected risk level.
Note: If you configure an application activity match and a risk match in the same CASB rule, the risk and application activity matches are processed with a logical AND operator. For example, if Application A is low-risk, Application B is medium risk, and Application C is high risk, and the activity from Application A Activity1, from Application B Activity2, and from Application C Activity3 is configured along with risk match High risk, then only Application C Activity3 traffic will hit that rule.
- To select all risk levels, click Enable All.
- Click Next to go to Step 5, Actions.

- Select a predefined or custom action to perform when there are no matching criteria. For more information, see Configure Custom Security Actions. The predefined actions are:
- Allow—Allow cloud applications.
- Block—Block cloud applications.
- Drop Session—Drop cloud application sessions.
- Reject—Reject cloud applications.
- In the Notification Profile field, select a profile to send email notifications.
- To configure a new notification profile, click
 Create New. For more information, see Configure a Notification Profile.
Create New. For more information, see Configure a Notification Profile. - Click Next to go to Step 6, Review and Submit.

- In the General section, enter a name for the CASB profile and, optionally, a description.
- For all other sections, review the information. To make changes, click the
 Edit icon.
Edit icon. - Click Save.
- In the Create Cloud Access Security Broker Profile screen, click Next to go to Step 2, Action, to select the default action to perform when there are no matching criteria. By default, applications that do not match any criteria are allowed. Enter information for the following fields.

Field Description Action Select the user-defined or predefined action to perform when there are no matching criteria. The predefined actions are:
- Allow—Allow cloud applications.
- Block—Block cloud applications.
- Drop Session—Drop cloud application sessions.
- Reject—Reject cloud applications.
Enable Logging Click to enable CASB logging. Notification Profile Select a profile to send email notifications. Click  Create New to create a new notification profile. For more information, see Configure a Notification Profile.
Create New to create a new notification profile. For more information, see Configure a Notification Profile. - Click Next to go to Step 3, Review and Submit.

- In the General section, enter a name for the CASB profile and, optionally, a description and tags. A tag is an alphanumeric text descriptor with no spaces or special characters. You can specify multiple tags added for the same object. The tags are used for searching the objects.
- For all other sections, review the information. To make changes, click the
 Edit icon.
Edit icon. - Click Save.
Configure a Custom CASB Profile (for Releases 11.4 and Earlier)
- Go to Configure > Secure Services Edge > Real-Time Protection > Profiles.

The following screen displays.
- Select the Cloud Access Security Broker (CASB Inline) tab.
- To customize which columns display, click Select Columns and then click Applications to display or hide the applications. Click Reset to return to the default columns settings.
- Click + Add to create a profile. The Create Cloud Access Security Broker Profile screen displays.
- In Step 1, Select Application, select the cloud applications for which you want to allow or block activities. You can also search for applications to select.
- Click Next to go to Step 2, Activities and Constraints, to allow and block activities for the selected cloud applications, or to disable an application.
- By default, the
Access Allow toggle button for each application is enabled. To bypass CASB processing for an application, click the toggle button. The
Access Allow button then turns grey.
- Click
Edit to allow or block the activities of an application. In the Edit popup window, click the toggle button to allow or block application activities. For example, you can allow or block file download, login, post, or file upload for Facebook.
- Click Done.
- Click Next to go to Step 3, Default Action, to select the default action to perform when there are no matching criteria. By default, applications that do not match any criteria are allowed. Enter information for the following fields.
Field Description Default Action Select the default action to perform when there are no matching criteria:
- Allow—Allow cloud applications.
- Block—Block cloud applications.
- Drop Session—Drop cloud application sessions.
- Reject—Reject cloud applications.
Enable Logging Click to enable CASB logging. - Click Next to go to Step 4, Review and Submit.
- In the General section, enter a name for the CASB profile and, optionally, a description and tags.
- For all other sections, review the information. To make changes, click the
 Edit icon.
Edit icon. - Click Save. The CASB profile is displayed in the Cloud Access Security Broker (CASB Inline) tab.
Configure Constraint Profiles
For Releases 12.1.1 and later.
You configure CASB constraint profiles to control which users and groups can access the activities configured in CASB. You can apply the CASB constraint profiles when you configure a CASB profile rule. The following table shows activities and applications that you can configure as a CASB constraint.
| Activity | Description | Applications |
|---|---|---|
| Call From User | Users who can initiate a call in the application | MS Teams–audio |
| Call To User | Users who can receive a call in the application | MS Teams–audio |
| Send From User | Users who can send content in the application | Outlook |
| Share From User | Users who can share content in the application | Sharepoint Online |
| Share To User | Users who can received shared content in the application. | Box, Dropbox, One Drive, Sharepoint Online |
To add constraint profiles:
- In the Cloud Access Security Broker (CASB Inline) tab, select Constraints Profiles.

- Click + Add. The Create Constraints Profile screen displays. In Step 1, From Users/User Groups, configure a custom constraint profile.

- Select the external directory type, and then add users in the Users Tab.
- Select the User Groups tab, and then select user groups.
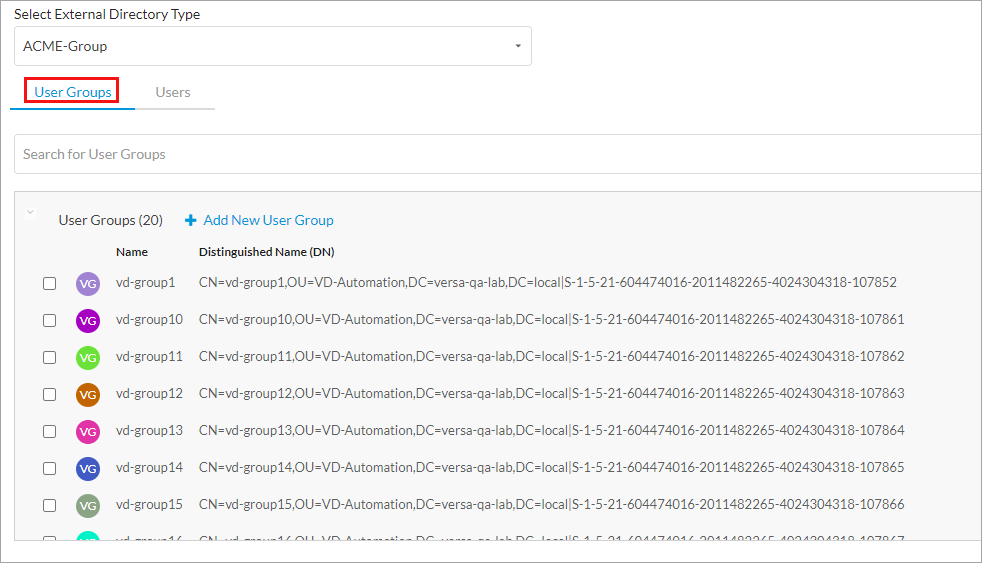
- Click Next to go to Step 2, To Users/User Groups screen.

- Select the external directory type, and then add users in the Users Tab.
- Select the User Groups tab, and then select user groups.

- Click Next to go to Step 3, Review and Submit.

- In the General section, enter a name for the constraints profile and, optionally, a description and tags.
- For all other sections, review the information. To make changes, click the
 Edit icon.
Edit icon. - Click Save.
Associate a CASB Profile with a SASE Internet Protection Rule
To allow or deny traffic, you associate a CASB profile with a SASE internet protection rule. CASB secures the data flowing between users and cloud applications in order to comply with corporate and regulatory requirements.
To associate a CASB profile with a SASE internet protection rule:
- Go to Configure > Real-Time Protection > Internet Protection.
- In the Internet Protection Rules List screen, click + Add to create a rule. The Create Internet Protection Rule screen displays. For more information, see Configure SASE Internet Protection Rules.
- Select the Security Enforcement screen, and then select Profiles.
- Select the Cloud Access Security Broker (CASB Inline) tab, and then enable CASB.

- Select User-Defined Profiles, and then select the CASB profile to associate with the internet protection rule.

- Click Next.
- In the Review & Deploy screen, enter a name for the profile.
- Review internet protection rule. To make changes, click the
 Edit icon.
Edit icon. - Click Save to create the new profile.
Configure IPS-Based CASB Support
For Releases 12.2.1 and later.
You can use IPS-based signatures with CASB to protect against known threats and prevent malicious access attempts. IPS identifies malicious activity using signatures, which are rules for matching suspicious software or patterns in an application's traffic and are stored in a database of known threats.
To load the IPS signatures for use with CASB, create an IPS profile with app-activity as the class type and alert as the predefined action. You then use this user-defined IPS profile along with a CASB profile in an access-policy rule, such as an internet protection rule or a private application protection rule.
To create an IPS profile for use with CASB:
- Go to Configure > Real-Time Protection > Profiles.

The following screen displays.
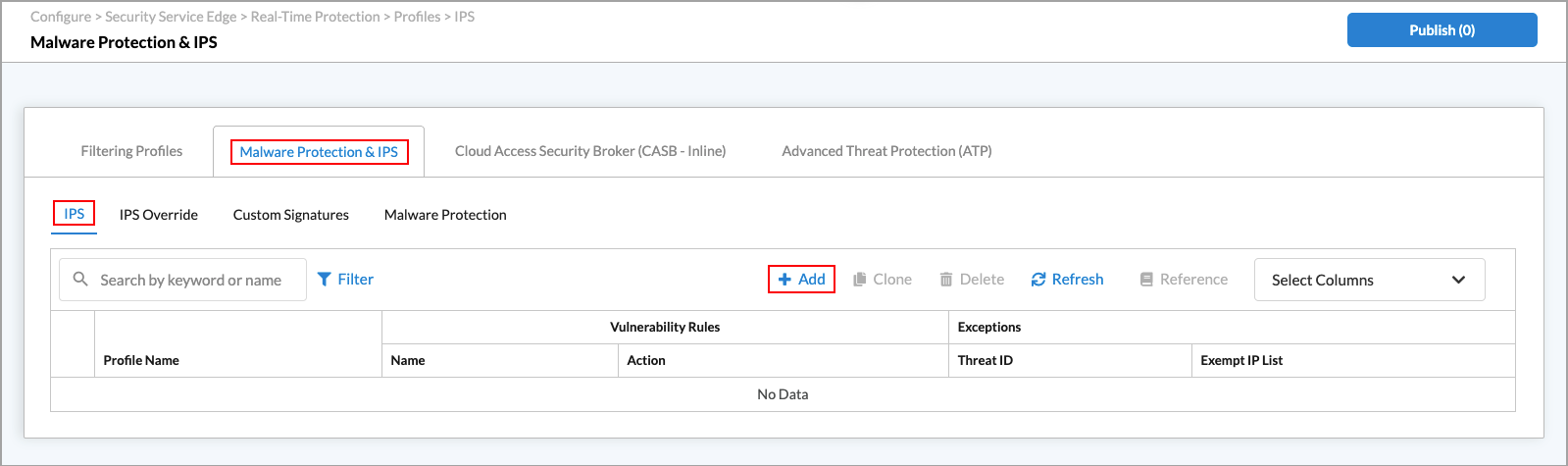
- Select Filtering Profiles in the horizontal menu bar, then select IPS in the submenu bar.
Note: In Release 12.2.2, the the IPS subtab was moved under the new Malware Protection & IPS tab.
- Click the
 Add icon to create a new IPS profile. The following screen displays.
Add icon to create a new IPS profile. The following screen displays.

- Select Step 1, Vulnerability Rules, then click the
 Add icon. The Add Vulnerability Rule screen displays with Section 1, Common Vulnerabilities and Exposures (CVE) and Signature Set selected by default.
Add icon. The Add Vulnerability Rule screen displays with Section 1, Common Vulnerabilities and Exposures (CVE) and Signature Set selected by default. - Select Section 2, General, then select app-activity under Class Type.
Note: This example shows only the steps needed to configure the IPS profile for use with CASB. For complete information about configuring user-defined IPS profiles, see Configure Custom IPS-Filtering Profiles.

- Select Section 6, Enforcement.
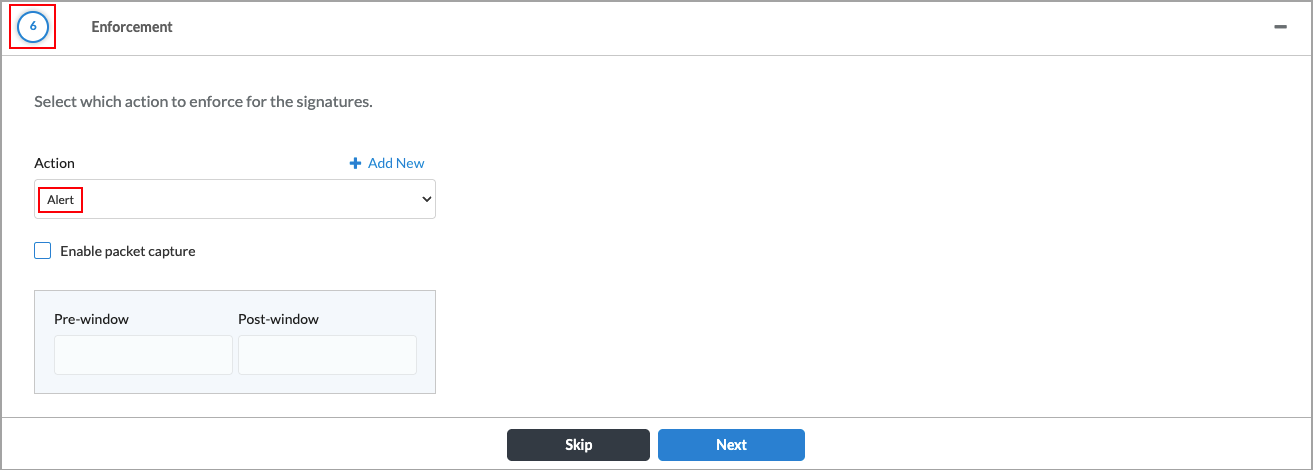
- Select Alert from the Action list.
Note: You must select the Alert action for the profile to be created successfully.
- Complete creating the profile as shown in Configure Custom IPS-Filtering Profiles.
To use the IPS profile in an access-policy rule:
Note: The following procedure uses an internet protection policy rule.
- Go to Configure > Real-Time Protection > Internet Protection.

The following screen displays.

- Click the
 Add icon. The Create Internet Protection Rule screen displays.
Add icon. The Create Internet Protection Rule screen displays. - Select Step 6, Security Enforcement.
Note: This example shows only the steps needed to configure the security enforcement for an internet protection rule. For complete information about configuring internet protection rules, see Configure SASE Internet Protection Rules.

- Select the Profiles section of the Security Enforcement screen, then select the Malware Protection & IPS tab and the Intrusion Protection System (IPS) panel. The Easy IPS profile is selected by default.
In Release 12.2.2, the the IPS subtab was moved under the new Malware Protection & IPS tab.
- Click the down arrow in the IPS panel to display all available IPS profiles.

- Select the user-defined profile you created. In this example, the profile is named IPS-alert.
- Next, select the Cloud Access Security Broker (CASB-inline) tab in the Profiles section.

- Click the slider to enable CASB.

- In the field labeled "Choose one of the following," select User Defined Profiles.
- Select one of the user-defined CASB profiles that are displayed.
- Complete creating the profile as shown in Configure SASE Internet Protection Rules.
Supported Applications and Activities
The following table lists supported web-based applications, application activities, and best practices. Newer applications and activities are continuously added in the Versa security package (SPack) updates. See Use Security Packages (SPacks) for more information about SPacks.
Note: For applications that support both the login activity and the login failed and login successful activities, you cannot configure both. If you choose the login activity, you cannot choose the login failed or login successful activities. Conversely, if you choose the login failed or login successful activities, you cannot choose the login activity.
| Application | Activities | Best Practices |
|---|---|---|
|
4shared |
Download file, login, login failed, login successful, share, upload file |
Activity: Share Platform: Browser Navigation:
Reason: This activity is not supported because the shareable link is generated from the browser cache. |
|
Amazon AWS |
Login, login failed, login successful |
NA |
|
AOL |
Login |
NA |
|
Atlassian |
Download file, login, login failed, login successful, share, upload file |
Activity: Download Platform: Browser Navigation:
Reason: Atlassian and Jira store generated images and files in the browser cache. When you download these files, they are retrieved directly from the browser cache. |
| Bard | Delete, edit, post, share, upload file | NA |
|
Bitbucket |
Download file, login, login failed, login successful |
NA |
|
Blogger |
Download file, upload file |
Activity: Upload Platform: Browser Navigation:
Reason: Upload activity is not supported because upload traffic is generic and creates false positives due to background traffic. |
|
Box.net |
Delete, download file, login, login failed, search, share, upload file |
Activity: Delete Platform: Browser On a block policy, when a user attempts to delete a file or folder, Box displays the message, "Item successfully moved to trash". |
| ChatGPT | Delete, download file, edit, login, login failed, login successful, logout, post, share, upload file |
Activity: Download |
| Activity: Share Platform: Browser Reason: ChatGPT retrieves the shareable link from the browser cache. |
||
|
Craigslist |
Login, search |
NA |
|
Dailymotion |
Like, login, upload file, watch stream |
NA |
|
Daum Mail |
Download file, search, upload file |
NA |
|
DocuSign |
Download file, login, login failed, login successful, upload file |
NA |
|
Dropbox |
Download file, login, search, share, upload file |
Activity: Logout Platform: Browser |
|
eBay |
Login, login failed, login successful, search, upload file |
NA |
|
Evernote |
Login, login failed, login successful |
NA |
|
Excel Online |
Download file, share, upload file |
Activity: Download Platform: Browser Navigation:
Reason: Excel Online downloads files from the browser cache. |
|
Activity: Share Platform: Browser |
||
|
|
Download file, login, post, upload file |
NA |
| Facebook Messenger | Audio, audio-video, video | NA |
|
Facebook Workplace |
Login, upload file |
NA |
|
Flickr |
Upload file |
NA |
|
GitHub |
Download file, like, login, login failed, login successful, upload file |
Activity: Upload Platform: Browser |
|
Gmail |
Download file, send, upload file |
Activity: Download Platform: Browser Reason: Gmail does not support file uploads that exceed 25 MB. Domain: upload.docs.google.com. |
|
Google Accounts |
Login, login failed, login successful |
NA |
|
Google Docs |
Download file, login, share, upload file |
NA |
|
Google Photos |
Download file, upload file |
NA |
|
Google Talk |
Audio, video |
NA |
|
imo |
Audio, audio video, video |
NA |
|
|
Like, login, login failed, login successful, search, share, upload file |
Activity: Like
Reason: These activities use WebSocket. |
|
Activity: Share Navigation: From Homepage or Profile > Share to. Reason: Share link is created from browser cache. Navigation:
Reason: These activities use WebSocket protocol. |
||
|
Jira |
Login, upload file |
Activity: Login and Upload Platform: Browser Reason: Jira login is not supported due to changes in host configuration. Login and Upload are supported via Atlassian login. |
|
Join.Me |
Upload file |
NA |
|
LastPass |
Download file, login |
NA |
|
Line |
Audio, video |
NA |
|
|
Download file, like, login, login failed, login successful, post, search, upload file |
Activity: Download |
|
Activity: Share |
||
|
Mail.ru |
Download file, login, login failed |
Activity: Login Successful Platform: Browser Reason: There is no option to set a password while creating a new Mail.ru account. A password, however, is required during login. You can login using an OTP, but phone does not receive OTP. |
| Microsoft Co-pilot | Upload file | NA |
|
Microsoft OneNote |
Download file, share |
NA |
|
Microsoft Teams |
Audio, audio video, download file, file transfer, like, search, share, upload file, video |
Activity: Like Platform: Browser Reason: Like is not supported to prevent false positives, because both Skype and Teams use similar traffic patterns. |
| Activity: Download Platform: Browser Navigation:
Reason: Microsoft Teams download happens on SharePoint or OneDrive, depending on the account type. |
||
|
Naver Mail |
Download file, login, login failed, login successful, share, upload file |
Activity: Share Platform: Browser Reason: Shareable link is part of the browser cache. |
| Activity: Upload Platform: Browser Reason: Sending an email with an attachment is blocked. |
||
|
Netflix |
Login, login failed, login successful |
NA |
|
Office 365 |
Login, login failed, login successful | NA |
|
Okta |
Login, login failed, login successful |
NA |
|
OneDrive |
Download file, login, login failed, login successful, share, upload file | NA |
|
OneLogin |
Login, login failed |
NA |
| Outlook | Download file | NA |
| Pandora | Search | NA |
|
PayPal |
Login |
NA |
|
|
Download file, like, login, login failed, login successful, search, share, upload file |
Activity: Share Platform: Browser Navigation: Pinterest.com > hover on an image or open an image > click Share > select Facebook or Messenger Reason: Sharing a photo via Facebook or Messenger is not supported. |
| Activity: Download Platform: Browser Reason: Images are downloaded as part of the background traffic to browser cache. |
||
|
Activity: Upload
Reason: These activities fall under Amazon domain. |
||
|
PowerPoint Online |
Share |
NA |
|
ProtonMail |
Search, upload file |
NA |
|
|
Dislike, download file, like, login, login failed, login successful, post, share, upload file |
Activity: Share Platform: Browser Reason: Only two types of navigation are allowed because whenever the page loads, the link is copied locally. |
|
Salesforce |
Download file, login, login failed, login successful |
NA |
|
ShareFile.com |
Download file, login, login failed, login successful, search, upload file |
Activity: Download, Upload Navigation:
Reason: These activities use Amazon Web Services (AWS) for download. Navigation: People tab > Browse Clients > Add Clients > Import multiple users with Excel > click Template Spreadsheet link to download.
Reason: These navigation methods are used to upload files under Amazon storage domains. |
|
SharePoint Online |
Download file, search, share, upload file |
NA |
|
Shopify |
Login |
NA |
|
Skype |
Audio, audio_video, file transfer, like, video | NA |
|
Slack |
Download file, like, login, login failed, login successful, post, search, share, upload file |
Activity: Download Platform: Browser Navigation: Slack > Home page > Threads tab > Record Video Clip > Record the Video > Stop > Download. |
| Activity: Upload/Share Platform: Browser Reason: For file upload, the file is uploaded to the Slack server before it is shared in a chat session. This generates a Share action for each upload. |
||
| Activity: Like Platform: Browser Navigation: Slack > Home page > Start a Huddle (1 or 2 people/channels to huddle with) > click Start a Huddle > Send a Reaction. |
||
|
SlideShare |
Login, search, upload file |
NA |
|
SoundCloud |
Download file, login, login failed, login successful, search, upload file |
NA |
|
SourceForge |
Download file, login, login failed, login successful, search, upload file |
NA |
|
Spotify |
Download file, like, login, search, upload file |
Activity: Share Platform: Browser Reason: Link is already loaded as part of the browser cache. |
|
Stack Overflow |
Login, login failed, login successful, search, upload file |
NA |
|
Tango |
Audio, video |
NA |
|
Telegram |
Audio |
NA |
|
Trello |
Search, upload file |
Activity: Upload Platform: Browser Reason: Upload Profile Pic and Upload Header Image are redirected to a non-Trello application domain. |
|
Twitch |
Login, share, upload file, watch stream |
NA |
|
|
Like, login, post, search, upload file |
NA |
|
Viber |
Audio, video |
NA |
|
Vimeo |
Comment, like, login, login failed, login successful, search, upload file, watch stream |
Activity: Download File Platform: Browser Reason: When a user uploads a thumbnail image while editing an uploaded video, Vimeo downloads the same file again and stores it in the browser cache. |
|
VMware |
Login, login failed |
NA |
|
Webex |
Audio, audio video, login, search, video |
NA |
|
|
File transfer |
NA |
|
WeTransfer |
Download file, share |
Activity: Upload Platform: Browser Reason: WeTransfer uses Amazon S3 for file storage. You cannot upload a file directly to WeTransfer without initiating a sharing activity, so if you have a policy that blocks WeTransfer Share activity, it also blocks Upload. |
|
|
Audio, audio video, download file, upload file, video |
NA |
|
Word Online |
Download file, share, upload file |
NA |
|
WordPress |
Download file, login, login failed, login successful, upload file |
NA |
|
Xero |
Login, login failed, login successful |
NA |
|
Yammer |
Download file |
Activity: Download Platform: Browser Reason: File Download activity for a corporate account uses SharePoint Online domain. |
|
Yandex |
Login |
NA |
|
Yandex Mail |
Download file |
NA |
|
YouTube |
Broadcast stream, comment, download file, like, search, share, upload file, watch stream |
NA |
| Zalo | Audio, video | NA |
|
Zoom |
Login, login failed, login successful |
NA |
Note: The list shown above is for web-based applications on Windows and Mac platforms. For mobile devices, a subset of the applications are supported, as follows.
| SaaS Application | Web Activities Supported | Mobile Activities Supported—iOS | Mobile Activities Supported—Android |
|---|---|---|---|
| Box.net |
Delete, download file, login, share, upload file |
Mobile App—Login, upload, download | Mobile App—Login, upload, download |
| imo |
Audio, audio video, video |
Mobile App supports the same activities as web | Mobile App supports the same activities as web |
| Line | Audio, video | Mobile App supports the same activities as web | Mobile App supports the same activities as web |
| ShareFile.com |
Download file, login, upload file |
Browser only | Not supported |
| SlideShare |
Login, upload file |
Browser only—Login, upload_file | Not supported |
| SourceForge |
Download file, login, upload file |
Browser only—Login, download_file | Not supported |
| Stack Overflow |
Login, upload file |
Browser only | Not supported |
| File transfer | Mobile App supports the same activities as web | Mobile App supports the same activities as web | |
| Audio, audio video, video | Mobile App supports the same activities as web | Mobile App supports the same activities as web |
You can view the CASB online in Versa Director. In Appliance view, go to Objects and Services > Objects > Predefined > CASB Applications. The following screen displays.

Supported Software Information
Releases 11.2.1 and later support all content described in this article, except:
- Release 12.1.1 adds support for constraint profiles; CASB profiles support CASB rules.
- In Release 12.2.2, the the IPS subtab was moved under the new Malware Protection & IPS tab.
