Configure API-Based Data Protection Policy for SaaS
![]() For supported software information, click here.
For supported software information, click here.
Versa Networks API-based data protection protects and secures organization data that resides in software as a service (SaaS) and infrastructure as a service (IaaS) applications. You create an API data protection policy under a tenant in Concerto to configure API data protection. The policy contains a set of rules, and you can configure event-based rules (based on an event generated by the SaaS or IaaS applications) or schedule-based rules (the rule triggers on a specific date or time). A scheduled-based rule scans the objects at rest (referred to as a retro scan).
Each rule contains two parts. The first part of the rule categorizes the SaaS or IaaS object on which to apply the policy. The second part defines the actions to take on the SaaS or IaaS objects that match the rules.
This article describes how to create event-based and schedule-based API data protection policy rules for SaaS.
Configure an Event-Based SaaS API Data Protection Policy Rule
- Go to Configure > Security Service Edge > Advanced Security > API-Based Data Protection > Policy Rules.

The following screen displays.

- To customize which columns display, click Select Columns, and then click the columns to select or deselect the ones that you want to display. Click Reset to return to the default column display settings.
The options are:- Selected Application Instance
- Schedule
- Action
- Security Profiles
- Notification Profile
- Status
- Select the SaaS tab and then select the Event Based subtab. The following screen displays.

Click the Add icon. The following screen displays with Step 1, SaaS Applications, selected by default.
Add icon. The following screen displays with Step 1, SaaS Applications, selected by default.

- Select the SaaS application to which to apply the rule.
- Click Next to go to Instance. Any previously configured instances display.

- Select an instance, or click the
 Add icon to add a new instance. If you click the Add icon, a screen similar to the the following screen displays.
Add icon to add a new instance. If you click the Add icon, a screen similar to the the following screen displays.
Note: The Add Instance screen will vary depending on which application you choose. For information about configuring instances for all cloud applications, see Configure Cloud Applications To Use with API-Based Data Protection.

- Fill in the required information, then click Next or 3 to go to Users & Groups.

- By default, all users and groups are included in the policy rule. Click Customize to specify the users and groups to include in the rule. The Users & Groups screen displays, with the Include tab and User Groups subtab selected by default.
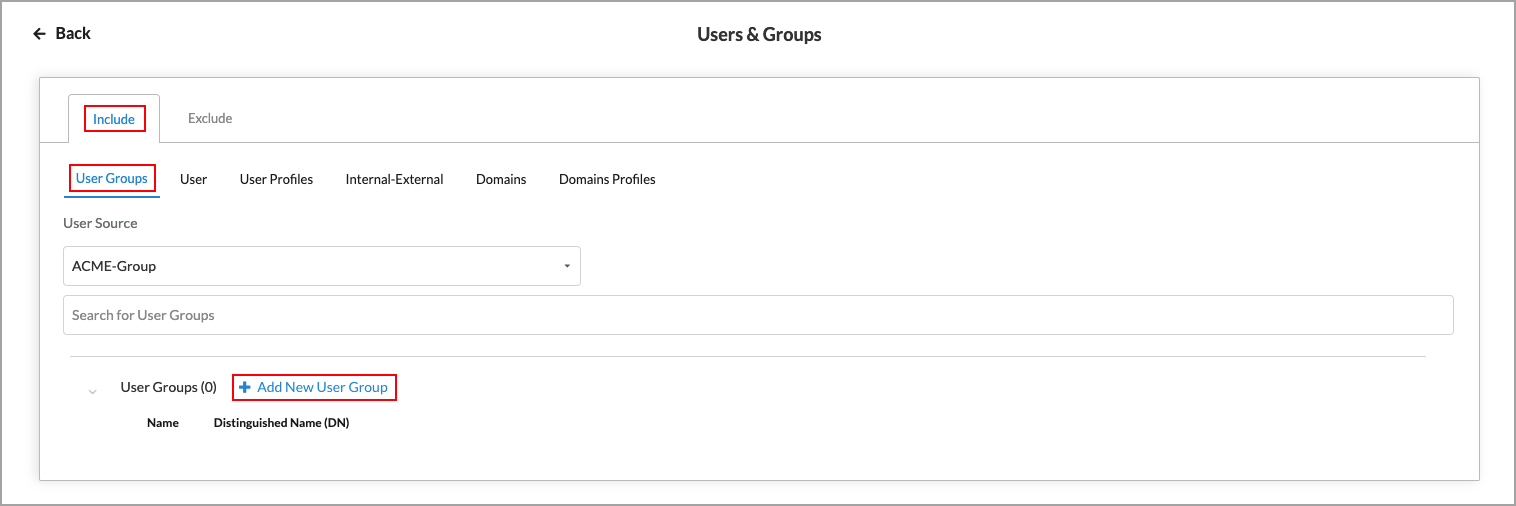
- Select a user source from the User Source drop-down list. The previously configured user groups display. Select one or more user groups to include in the rule.
- You can click + Add New User Group to add an additional user group.

- In the Add User Group popup window, enter a name in the User Group field and enter a distinguished name for the user group.
- Click Add.
- You can click + Add New User Group to add an additional user group.
- Click the User subtab.
- Select a user source from the User Source drop-down list. The users in that source display.

- Select one or more users to include in the rule.
- You can click + Add New User to add additional users.

- In the Add User popup window, enter a name and a work email address for the user.
- Click Add.
- You can click + Add New User to add additional users.
- Click the User Profiles tab.

- Select one or more user profiles.
- Click + Add New User Profile to add an additional user profile.
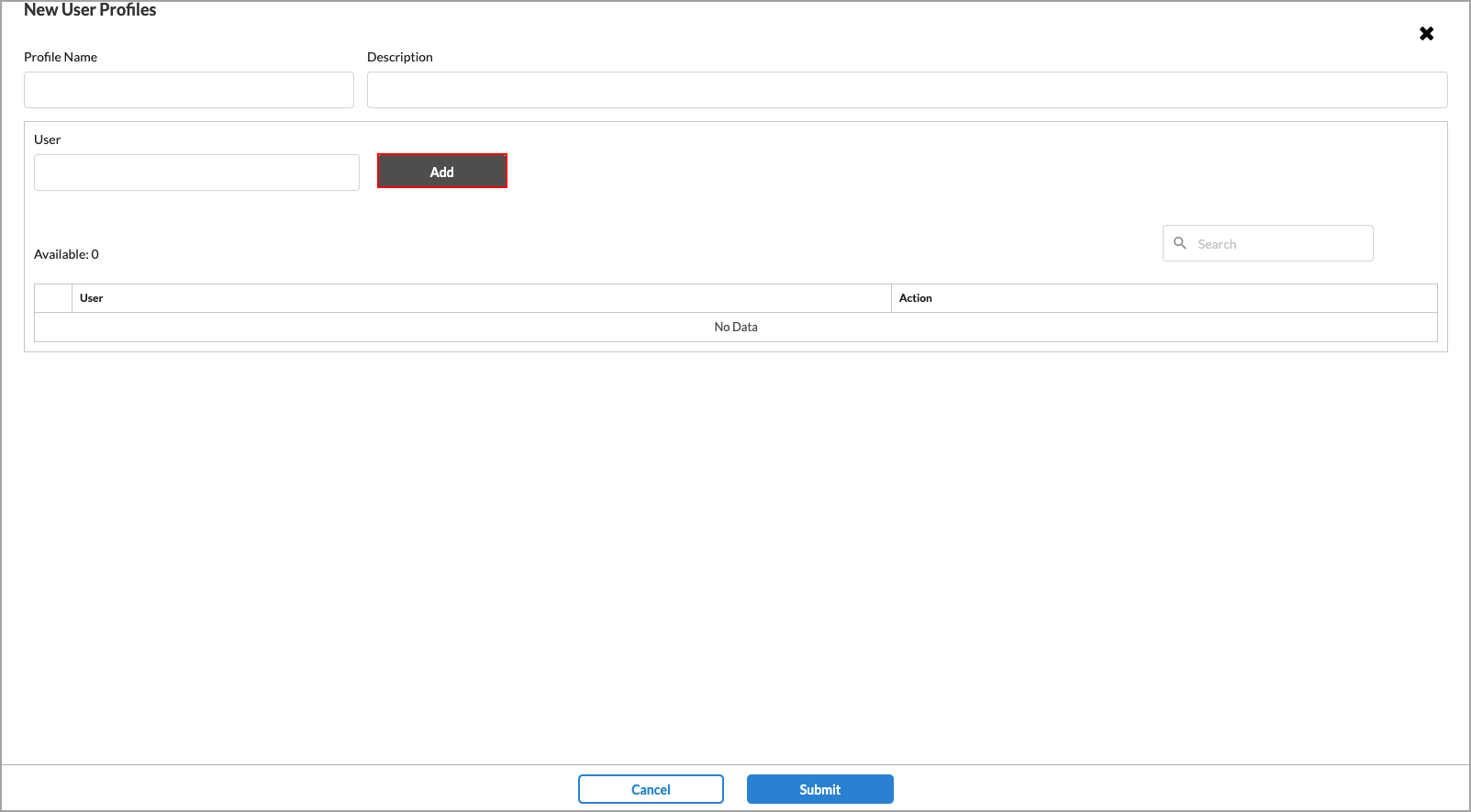
- Enter a name for the profile in the Profile Name field.
- (Optional) Enter a description.
- Enter a name for the user in the User field.
- Click Add. The user is added to the Available list. You can add additional users to the list.

- Click Remove to remove a user name from the list.
- When you have finished adding users to the profile, click Submit.
- Click the Internal-External tab.

- Select one of the following users to add to the rule.
- None
- Internal
- External
- Both
- Click the Domains tab. The following screen displays any previously configured domains.

- Select a domain to add to the rule.
- If no domains are listed or if you want to add a new domain, click + Add New Domain.
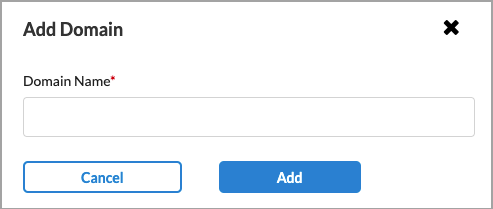
- In the Add Domain popup window, enter a valid domain name, such as versa-networks.com, then click Add. You can add additional domains.
- You can then add one or more of the new domains to the rule.
- If no domains are listed or if you want to add a new domain, click + Add New Domain.
- Click the Domain Profiles tab. The following screen displays any previously configured domain profiles.

- Select one or more domain profiles to add to the rule.
- Click + Add New Domain Profile to create additional profiles.
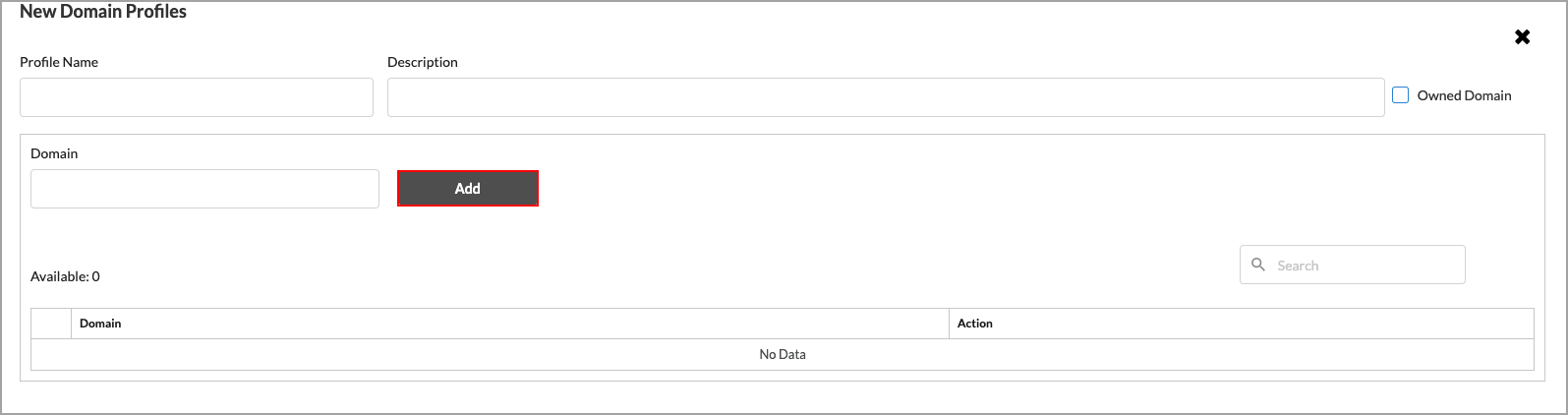
- Enter a name for the domain profile in the Profile Name field.
- (Optional) Enter a description.
- Enter a valid domain name, such as versa-networks.com.
- Click Add. The domain profile is added to the Available list.

- Click Remove to remove a domain profile from the list.
- When you have finished additional domain profiles to the list, click Submit.
- Select the Exclude tab. By default, all users and groups will have the security enforcements applied to them. If you do not want to accept the default settings, you can select the specific users or groups for the security posture.

- The subtabs under the Exclude tab are the same as the subtabs under the Include tab. See Step 8 through Step 22 for information about configuring these subtabs.
- Click the
 Back arrow to return to Step 3, Users & Groups, then click Next or 4 to go to Security Profiles.
Back arrow to return to Step 3, Users & Groups, then click Next or 4 to go to Security Profiles. - Choose the profile for the rule, as follows:
- Allow—Select Allow to allow all traffic that matches the rule to pass through. If you select this option, go to Step 29.

- Profiles—Select Profiles to choose one or more predefined fEduser-defined profiles.

- Allow—Select Allow to allow all traffic that matches the rule to pass through. If you select this option, go to Step 29.
- If you select Profiles, you can select the following profile types:
- Data Loss Prevention (DLP)—See Configure Offline Data Loss Prevention for more information.
- Offline Cloud Access Security Broker (CASB)—See Configure Offline CASB Profiles for more information.
- Advanced Threat Protection (ATP)—See Configure Advanced Threat Protection for more information.
- Click Next or Step 5 to go to Notification Profile.

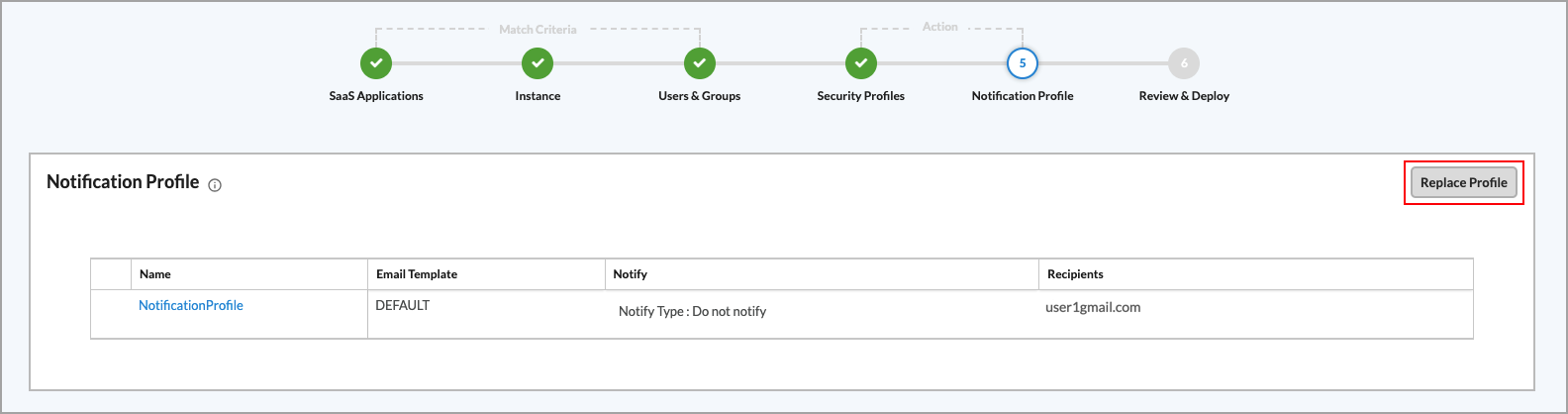
- Click Select Profile. The following screen displays any previously configured profiles. You can use a previously configured profile or you can create a new notification profile.

- To use a previously configured profile, select the profile, then click the
 Add button at the bottom of the screen. The profile is added to the main Notification Profile screen.
Add button at the bottom of the screen. The profile is added to the main Notification Profile screen.
- To create a new notification profile, click the
 Add icon in the upper right corner of the screen. For information about creating notification profiles, see Configure Notification Profiles.
Add icon in the upper right corner of the screen. For information about creating notification profiles, see Configure Notification Profiles. - After selecting a notification profile, you can replace it with a different one. To replace the current notification profile, click Replace Profile. The Notification Profile list screen displays.
- Select a new profile and click the
 Add button to replace the previous profile.
Add button to replace the previous profile. - Click Next or Step 6 to go to Review & Deploy, then enter the following information.

Field Description Name (Required) Enter a name for the new rule. Rule is Enabled Click the slider to enable the rule. - Review the configuration. Click the
 Edit icon in any section to make changes.
Edit icon in any section to make changes. - Click Save to create the new rule.
Configure a Schedule-Based SaaS API Data Protection Policy Rule
- Go to Configure > Security Service Edge > Advanced Security > API Based Data Protection > Policy Rules.

- If you have not previously configured a SaaS schedule-based policy rule, the following screen displays.

Click Create Job to configure a new policy rule. The SaaS Schedule Based configuration screen displays with Step 1, SaaS Applications, selected by default. Go to Step 1d below.
- If you have previously configured a SaaS schedule-based policy rule, the following screen displays.

- To customize which columns display, click Select Columns, and then click the columns to select or deselect the ones that you want to display. Click Reset to return to the default column display settings.
The options are:- Selected Application
- Instance
- Action
- Security Profiles
- Notification Profile
- Enabled
- Click the
 Add icon to configure a new policy rule. The SaaS Schedule Based configuration screen displays with Step 1, SaaS Applications, selected by default.
Add icon to configure a new policy rule. The SaaS Schedule Based configuration screen displays with Step 1, SaaS Applications, selected by default.

- If you have not previously configured a SaaS schedule-based policy rule, the following screen displays.
- Select an application, the click Next or 2 to go to Instance.

- To customize which columns display, click Select Columns, and then click the columns to select or deselect the ones that you want to display.
- To add an instance:
- Click the
 Add icon.
Add icon.
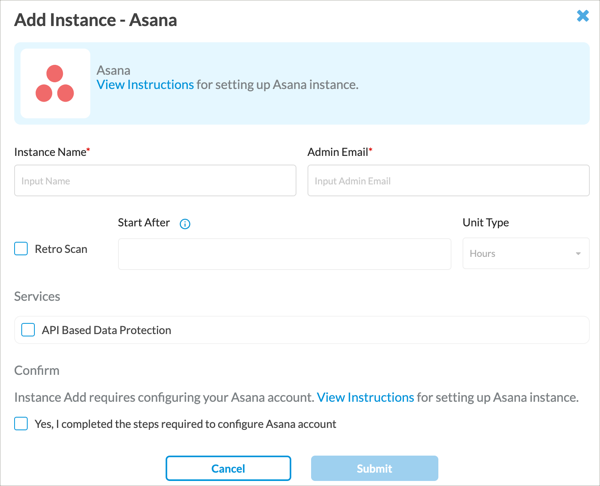
- Enter information for the following fields.
Field Description Instance Name Name of the SaaS application instance. Admin Email Administrator email address. Retro Scan Click to scan and protect all the files that are present.
Start After
Enter time to grant access and configure policies/rules for this instance before starting the retroactive scan. Unit Type Enter the units for the Start After field, either hours or minutes. Services Click API-Based Data Protection. Confirm Click Yes to verify you have completed the steps required to configure the associated account. - Click Submit.
- Click the
- Click Next or 3 to go to Users & Groups. The following screen displays.

- By default, all users and groups are included in the policy rule. Click Customize to specify the users and groups to include in the rule. The Users & Groups screen displays, with the Include tab and User Groups subtab selected by default.

- Select a user group source from the User Source drop-down list.
- If you select a user group, you click + Add New User Group to add additional user groups.

- Enter a user group name, a distinguished name (DN), and then click Add.
- If you select a user group, you click + Add New User Group to add additional user groups.
- Click the User tab.

- If you select a user, you can click + Add New User to add additional users.

- Enter a name for the user.
- Enter a work email address for the user.
- Click Add.
- If you select a user, you can click + Add New User to add additional users.
- Click the User Profiles tab.

- Select one or more user profiles.
- Click + Add New User Profile to add one or more additional user profiles.

- Enter a name for the profile in the Profile Name field.
- (Optional) Enter a description.
- Enter a name for the user in the User field.
- Click Add. The user is added to the Available list. You can add additional users to the list.

- Click Remove to remove a user name from the list.
- When you have finished adding users to the profile, click Submit.
- Click the Internal-External tab.

- Select one of the following internal-external users to add to the rule.
- None
- Internal
- External
- Both
- Click the Domains tab. The following screen displays any previously configured domains.
- Select a domain to add to the rule.

- If no domains are listed, click + Add New Domain.

- Enter a valid domain name, such as versa-networks.com, then click Add. You can add additional domains.
- You can then add one or more of the new domains to the rule.
- If no domains are listed, click + Add New Domain.
- Click the Domain Profiles tab.

- Select one or more domain profiles to add to the rule.
- Click + Add New Domain Profile to create additional profiles.

- Enter a name for the domain profile in the Profile Name field.
- (Optional) Enter a description.
- Enter a valid domain name, such as versa-networks.com.
- Click Add. The domain profile is added to the Available list.

- Click Remove to remove a domain profile from the list.
- When you have finished additional domain profiles to the list, click Submit.
- Select the Exclude tab. By default, all users and groups are excluded in the policy rule. Click Customize to specify the users and groups to exclude from the rule.
Note: The subtabs under the Exclude tab are the same as the subtabs under the Include tab. See Steps 7 through 18 for information about these subtabs.
- Click Next, or click the
 Back arrow to return to Step 3, Users & Groups, then click Schedule.
Back arrow to return to Step 3, Users & Groups, then click Schedule.

- Select the frequency with which a scan will be performed. The options are Non-Recurring Time, Hourly, Daily, Weekly, and Monthly.
Field Description Non Recurring Time Select this option to perform the scan once only. Enter the following:
- Start Date—The date to perform the scan.
- Start Time —The time to begin the scan.
Hourly Select this option to perform the scan once per hour. Enter the following:
- Start Date—The date to start the scan.
- Start Time—The time to start the scan
- End Date—The date to end the scan.
Daily Select this option to perform the scan once per day. Enter the following:
- Start Date—The date to start the scan.
- Start Time—The time to start the scan.
- End Date—The date to end the scan.
Weekly Select this option to perform the scan once per week. Enter the following:
- Every—Select how often to perform the weekly scan. For example, select 1 to perform the scan every week, select 2 to perform the scan every two weeks, etc.
- On—Select the day of the week on which to perform the scan. You can select multiple days, and the scan will be performed once per week on the specified days.
- Start Date—The date to start the scan.
- Start Time—The time to start the scan.
- End Date—The date to end the scan.
Monthly Select this option to perform the scan once per month. Enter the following:
- Every—Select how often to perform the monthly scan. For example, select 1 to perform the scan every month, select 2 to perform the scan every two months, etc.
- Start Time—The time to start the scan.
- End Date—The date to end the scan.
- Click Next to go to Security Profiles. The following screen displays.

- Select Allow to allow all traffic that matches the rule to pass through. If you select this option, go to Step 27.
- Select Profiles to choose one or more predefined or user-defined profiles, then select the Advanced Threat Protection (ATP) tab.
- Click the slider bar to enable ATP profiles. Any previously configured ATP profiles display.

- Select an ATP profile, or click
 Create New to create a new ATP profile. If you click
Create New to create a new ATP profile. If you click  Create New, the following screen displays with Step 1, ATP Action, selected by default and previously configured ATP actions displayed. For more information, see Configure Offline Advanced Threat Protection.
Create New, the following screen displays with Step 1, ATP Action, selected by default and previously configured ATP actions displayed. For more information, see Configure Offline Advanced Threat Protection.

- To customize which columns display, click Select Columns, and then click the columns to select or deselect the ones you want to display. Click Reset to return to the default column display settings.
- Select an ATP action from the list, or click the
 Add icon to configure a new ATP action. In the Add ATP Action screen, enter the following information.
Add icon to configure a new ATP action. In the Add ATP Action screen, enter the following information.

Field Description Action Name Enter a name for the ATP action. Send to Sandbox Enabled by default. Click the slider bar to disable the Send to Sandbox option. Pending ATP Action Choose which action to take on a file until the sandbox rules are available from the cloud. The actions are:
- Allow and scan first time
- Block
- Wait until timeout
Sandbox Actions Specify the sandbox actions to take for traffic that is determined to be clean, suspicious, or malicious. The options are:
- Allow
- Alert
- Block
- Reject
- Click Save.
- Click Next or 2 to go to Sandbox Rules. The Sandbox Rules screen displays currently configured sandbox rules, if any have been configured.

Field Description Rule Name Enter a name for the sandbox rule. Description (Optional) Enter a description of the rule. Rule is Enabled Enabled by default. Click the slider bar to disable the sandbox rule. ATP Action Select an ATP action. Click + Add New to add a new ATP action. Select the type of protocol to detect and analyze Select a protocol type. Select the type of files to detect and analyze Select the type of files. Click Select All to select all file types. Select type of file action Select one of the following file actions:
- Download and Upload
- Download
- Upload
Notification Profile Select a notification profile. - Click Save.
- Click Next or 3 to go to Default Actions, then enter the following information.

Field Description Default Action Select a default action to take if there are no criteria matched. The options are:
- Allow
- Alert
- Block
- Reject
Timeout Action Select an action to take if the timeout period is exceeded. The options are:
- Allow
- Alert
- Block
- Reject
Duration to wait before timeout Enter the duration to wait before a timeout occurs.
Range: 1 through 1500
Default: None
- Click Next or 4 to go to Review and Submit.

- Enter a name in the Name field.
- Review the configuration and click the
 Edit icon to make changes as needed.
Edit icon to make changes as needed. - Click Save. The new profile is added to the Notification Profile step.
- Select an ATP profile, if one was not previously selected.
- Click Next or 5 to go to Notification Profile.

- Click Select Profile. The Notification Profile screen displays.

- Select a profile, then click Add. The notification profile displays. Click Replace Profile to replace the notification profile with a different one.

- Click Next to go to Step 6, Review & Deploy, then enter a name for the rule. The rule is enabled by default. You can click the slider bar to disable the rule.

- Review the configuration details. To update the information in a section, click the
 Edit icon and update the information.
Edit icon and update the information. - Click Save to save the SaaS event-based profile.
Supported Software Information
Releases 11.1.1 and later support all content described in this article.
