Configure Application and Domain-Based Traffic Steering for the SASE Client
![]() For supported software information, click here.
For supported software information, click here.
As part of Versa Secure Access (VSA) and Secure Access Service Edge (SASE), you can configure a Versa Operating SystemTM (VOSTM) device to be a secure access portal or a secure access gateway so that a SASE client can connect to it. You can configure portal and gateway services on a single VOS device or on two different VOS devices. When the SASE client is performing user registration, it communicates with the secure access portal. After the registration process completes, the SASE client communicates with the secure access gateway to obtain secure web gateway (SWG) or zero-trust network access (ZTNA) services.
You can configure which applications and domains the SASE client sends to the Versa Cloud Gateway (VCG) and which break out locally to the internet. You can also exclude specific application and domain traffic from the VCG. The default traffic action sends all applications from the installed client directly to the internet without being sent back to the gateway.
This article describes how to create client-based access rules to direct SASE client application and domain traffic using the following services:
- Versa Secure Private Access (VSPA)—Send specific internet applications and domains over the SASE tunnel to the VCG. This scenario uses a split tunnel. A split tunnel allows traffic, like corporate applications, to go through the VCG for inspection, while other traffic, like streaming applications, go directly to the internet.
- Versa Secure Internet Access (VSIA) or VSPA+VSIA—Exclude certain internet applications and domains from the VCG. In this scenario, specific applications and domains are not sent over the SASE tunnel. That is, you specify which applications and domains should bypass the SASE tunnel.
For both scenarios, you create the configuration on the SASE portal using the Concerto orchestrator. This configuration is pushed to the SASE clients during the registration process.
Configure Applications and Domains To Send Over the SASE Tunnel
This procedure explains how to explicitly specify the applications and domains to send over the SASE tunnel to the VCG. You can configure the applications and domains to include, as well as internet bound traffic you want to route locally. This scenario requires a VSPA subscription.
The image below shows split tunneling, where private application traffic and internet applications such as Salesforce, YouTube and Microsoft Office are routed through the VCG. Other internet traffic breaks out locally to the internet.

In the following configuration example, a secure access client-based rule—known as a split tunnel or internet breakout—ensures that specific applications and domains are sent through the SASE tunnel to the VCG for inspection, and then sent to the internet, while other traffic gets routed locally.
To configure a rule where specific applications and domains breakout to the internet:
-
Go to Configure > Security Service Edge > Secure Access > Client-Based Access > Policy Rules.

- Click + Add in the Create Client-Based Access Rule screen.
- Set your match criteria in step 1, Operating System, and step 2, Users and Groups. For example, the screenshot below shows the match criteria for operating system is Windows versions 10, 10 Mobile, and 11.
 In the example below, the match criteria for user groups is Finance. The Enable Rule for the following matched users and user groups is automatically filled in.
In the example below, the match criteria for user groups is Finance. The Enable Rule for the following matched users and user groups is automatically filled in.

- Select step 5, Traffic Action.

- To send all private traffic over the SASE tunnel to the VCG, all internet traffic directly to the internet, and send specific applications and domains over the SASE tunnel to the Versa Cloud Gateway for inspection:
- Select Versa Secure Private Access (VSPA) under the Select subscription type for users matching this rule.
- Select the Breakout To Internet option in the Allow section.
Note: Other available traffic-action options depend on the subscription type assigned to the tenant and on the type of operating system. For information about other subscription and operating system options, see the Configure SASE Traffic Action Rules for Secure Client-Based Access section in Configure SASE Secure Client-Based Access Rules.
- Enter a message to display after a user successfully logs into the VCG in the Display Message after Successful Connection field. In this example, the message is Welcome to Your Company Website.
- In the Search for Applications field, either use the search bar to type an application name, or select from the Pre-Defined Applications section by clicking the icons. You can also click + Add New to create a user-defined application. In this example, the Salesforce, YouTube, and Microsoft Office applications are allowed.
- Configure the remaining steps in the workflow (step 6 through step 8), as needed.
- Go to step 9, Review and Submit, and add a name to the rule.
- Set the rule order for this rule based on your requirements.
- Click Save.
- Once the changes are published, you can verify the configuration was successful.
Verify Internet Breakout Traffic Steering Using the Versa Client
The following procedure shows how to verify the internet breakout scenario.
To verify the changes are published to the gateway:
- Log into the Versa client, click the
 Settings icon in the top right of the popup window, and then click Reregister. The client displays the welcome message highlighted in green at the bottom of the window.
Settings icon in the top right of the popup window, and then click Reregister. The client displays the welcome message highlighted in green at the bottom of the window. - Select the enterprise, and then select the gateway.
- In the Gateway Details screen, click Advanced Settings > Traffic Steering.
- To verify split tunnel is active, confirm that the Split Tunnel option is enabled with the toggle in the on position as highlighted in the following image.

- To view the routing table, open a command prompt in Windows and enter route print after you connect to the gateway.
A routing table displays. The example output below shows only one default route that points to the local interface IP address, 10.163.104.25, highlighted in blue. The VSPA private routes also point to the VCG tunnel interface IP address, 10.200.2.38. An example of a route is highlighted in yellow.

- To ensure the routing tables are updated for the included applications, you must first browse the applications that you have included for them to appear on the routing table. Check the routing table output to confirm the application route entries are included (in this example, Salesforce, YouTube, and Microsoft Office).
In the example output below, note that along with the routes shown in the previous example, additional routes corresponding to the applications that were included for inspection are visible and point to the VCG tunnel interface IP address, 10.200.2.38. These routes are highlighted in green.

Configure Applications and Domains To Not Send Over the SASE Tunnel
With the VSIA or VSPA+VSIA services, some deployments require routing all traffic through the gateway, but also require excluding specific internet application traffic from the VCG. To do this, you create secure client-based access rules to send specific applications to the VCG and select the applications that need to break out locally. With this configuration, all traffic goes to the gateway, except for the selected applications and domains you choose to exclude. This is a common use case when the enterprise is aware that these applications are already secured or can bypass the SASE tunnel to reduce the unnecessary bandwidth consumption on the VCGs.
In the following image, all internet traffic is sent to the VCG. Applications and domains, such as Zoom and OpenDrive, that do not require extensive security inspection are blocked from being sent to the VCG and pass directly to the local gateway.

Configure Applications To Bypass the Versa Cloud Gateway
To exclude certain applications from the VCG, use the option to Send Apps to Versa Cloud Gateway. This turns off split tunneling and allows selected application traffic, such as OpenDrive and Zoom, to be forwarded directly to the internet from the user's device. This procedure ensures that full tunnel is used.
-
Select Configure > Security Service Edge > Secure Access > Client-Based Access > Policy Rules.

- Click + Add in the Create Client-Based Access Rule screen.
- Set your match criteria in step 1, Operating System, and step 2, Users and Groups. For example, the screenshot below shows the match criteria for operating system is All Windows Operating Systems.
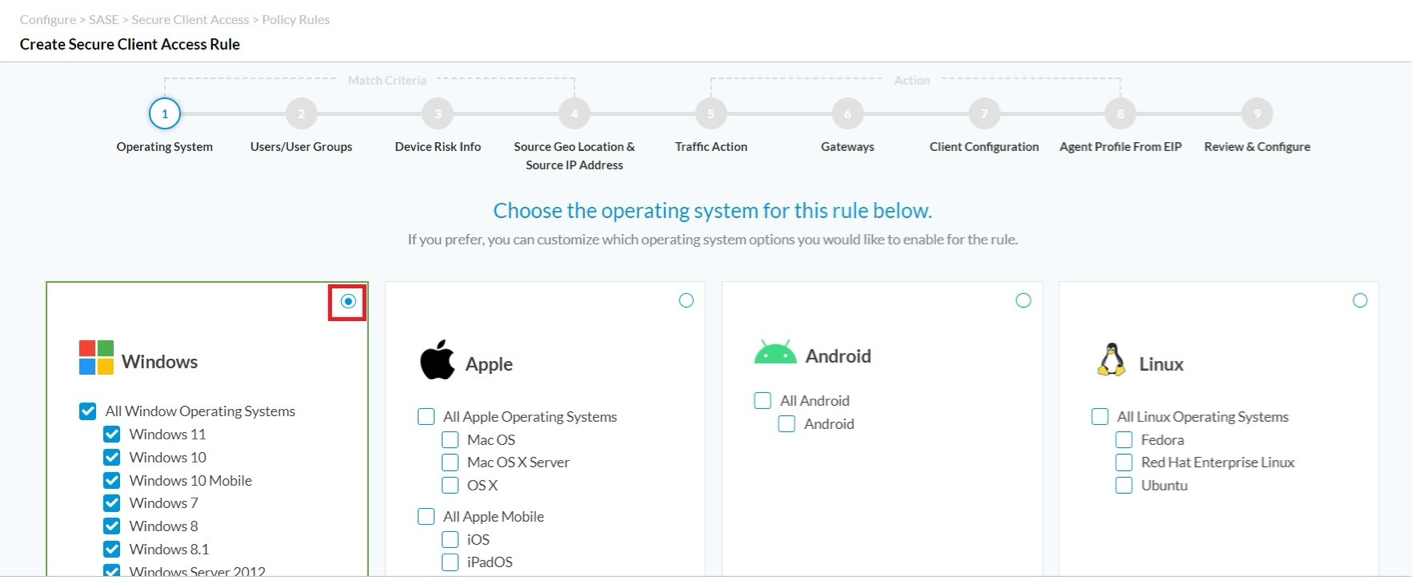
In the example below, the match criteria for user group is Engineering. The Enable Rule for the following matched users and user groups is automatically filled in.

- Select step 5, Traffic Action.

- To configure traffic action to send all traffic from the user device to the VCG and only selected applications to bypass directly to the internet:
- Select your subscription type (here, VSPA and VSIA).
- Select the Sends Apps to Versa Cloud Gateway option in the Allow section.
Note: The available traffic-action options depend on the subscription type assigned to the tenant and the type of operating system. For more information, see the Configure SASE Traffic Action Rules for Secure Client-Based Access section in Configure SASE Secure Client-Based Access Rules.
- Enter a message to display after a user successfully logs into the VCG in the Display Message after Successful Connection field. In this example, the message is Welcome to Your Company Internet.
- To select applications to not send to the VCG, use the search bar to type an application name or select from the Pre-Defined Applications section by clicking the icons. You can also click +Add New to create a user-defined application.
In this example, the Zoom and OpenDrive applications are selected to bypass the Versa Gateway. All other applications are sent to the tunnel and will be sent directly to the VCG from the user device. - Configure the remaining steps in the workflow (step 6 through step 8), as needed.
- Go to step 9, Review and Submit, and add a name to the rule.
- Set the rule order for this rule based on your requirements.
- Click Save.
- Once the changes are published, you can verify the configuration was successful.
Verify Applications Are Not Sent to SASE Using the Versa Client
The following procedure explains how to verify that an application is excluded.
To verify the changes are published to the gateway:
- Log into the Versa client, click the
 Settings icon, then click Reregister. The client displays the welcome message highlighted in green at the bottom of the window.
Settings icon, then click Reregister. The client displays the welcome message highlighted in green at the bottom of the window. - In the Enterprise section, select the enterprise, and then select the gateway.
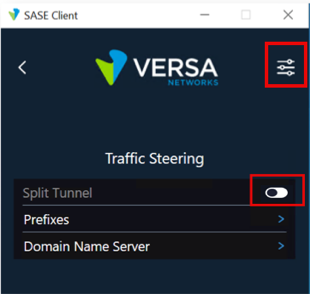
- In the Gateway Details screen, click Advanced Settings > Traffic Steering.
- To verify split tunnel is not active, confirm the Split Tunnel option is disabled with the toggle in the off position, as highlighted in the following image.
- To view the routing table, open a command prompt in Windows and enter route print after you connect to the gateway.
A routing table displays. The following example routing table output shows only one default route pointing to the local Interface IP address, 10.200.1.28, highlighted in green. The Versa Secure Private Access (VSPA) private routes also point to the VCG tunnel Interface IP address, 10.163.104.25; an example of a route is highlighted in yellow in the following image.

- To view the routing table to confirm that client is receiving the default route from the VCG, open a command prompt in Windows and enter route print after you connect to the gateway. Note the highlighted row with metric=5 is preferred over local default route. This means that all traffic (except Zoom and OpenDrive) is sent to the VCG.
Note that as soon as you start browsing Zoom/OpenDrive, the client routing table starts populating with respective IP network entries (used to browse Zoom and OpenDrive) as shown in following image.

Supported Software Information
Releases 12.1.1 and later support all content described in this article.
Releases 7.8.9 of Versa SASE client and later support all content described in this article.
