Configure User and Group Policy
![]() For supported software information, click here.
For supported software information, click here.
You create user and user group security policies to detect the users and user groups who are using applications on your network. The security policies help to identify who may have transferred files or transmitted threats. User and user group policies identify users based on their name or role rather than their IP address.
Creating user group policies simplifies firewall administration, because you do not have to update the rules whenever a group's membership changes.
For Releases 21.2.2 and earlier, next-generation firewall (NGFW) supports LDAP and SAML authentication. For Releases 22.1.3 and later, NGFW can use certificate, LDAP, local profile, Kerberos, RADIUS, and SAML for user and group authentication.
Configure an LDAP Server Profile
You configure an LDAP server profile to define how NGFW connects to and authenticates the Active Directory server and how it searches the Active Directory and retrieves the group list and associated list members.
Before you begin the configuration process, ensure that you have the bind distinguished name (DN) authentication credentials and the bind password. You can get this information from the LDAP administrator.
To configure an LDAP server for Active Directory authentication:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > LDAP in the left menu bar.
- Select the LDAP Server Profile tab, and then click the
 Add icon.
Add icon.

- In the Add LDAP Server Profile popup window, select the General tab and enter information for the following fields.

Field Description Name (Required) Enter a name for the LDAP server profile. NGFW uses this name to connect to the LDAP directory to retrieve group mapping information and to select the usernames and group names for the profile. Description Enter a text description for the LDAP server profile. Tags Enter a keyword or phrase that allows you to filter the profile name. This is useful when you have many profiles and want to view those that are tagged with a particular keyword. Server Type (Required) Select Active Directory as the location of the LDAP server. NGFW populates the LDAP attributes in the group mapping settings on this server. Domain Base Enter the domain base of the LDAP directory to fetch domain attributes. Domain Name (Required) Enter the domain name in which the LDAP server resides. Base DN (Required) Enter the base distinguished name (DN) of the LDAP directory location. NGFW initiates a search for user and group information at this location. Bind DN (Required) Enter the bind DN authentication credentials to authenticate and bind the LDAP server for access. Bind DN is used to search and request for authentication. Bind Password (Required) Enter the bind password for the service account. Bind Timeout (Required) Enter the period, in seconds, that the firewall waits for an LDAP connection to establish before timing out.
Value: 1 through 255
Default: 30 seconds
Search Timeout (Required) Enter the period, in seconds, for the LDAP server to complete a search request before timing out.
Value: 1 through 255
Default: 30 seconds
Use SSL (Group of Fields) Click enable to use SSL for the LDAP session. When you click Enable, SSL Mode and CA Certificate fields are enabled.
Click disable not to use SSL for the LDAP session.
- SSL Mode
Select the SSL mode for the LDAP session:
- LDAPS—Use secure LDAP (LDAP over SSL).
- Start TLS—Use LDAP over TLS.
- CA Certificate
Select the Certificate Authority (CA) to use for the secure LDAP connection. State Click enable to use the LDAP server.
Click disable not to use the LDAP server.
- Select the Servers tab and then click the
 Add icon.
Add icon.

- In the Add Servers popup window, enter information for the following fields.
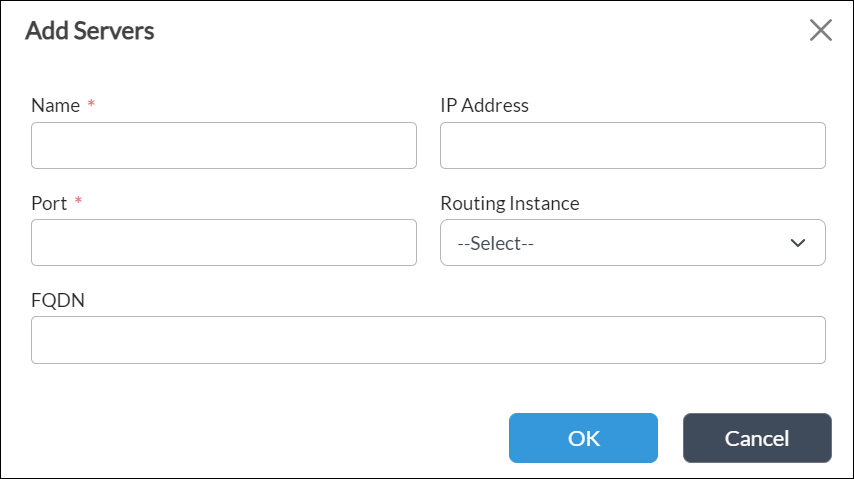
Field Description Name (Required) Enter the hostname of the device hosting the LDAP directory service. IP Address
Enter the IP address of the LDAP server. Port (Required)
Enter the number of the listening port on the LDAP server. This is the port that communicates with the LDAP directory service. Routing Instance
Select the routing instance to use to reach the LDAP server.
FQDN
Enter the full domain name of the LDAP server. - Click OK.
Configure Appliance Proxy To Fetch the LDAP User and Group Profile
If a Director node is directly connected to the LDAP server, the Director node can fetch the user and group profile. If the Director node is not connected to the LDAP server, you can configure appliance proxy, which allows a Versa Operating SystemTM (VOSTM) device to act as an LDAP proxy.
To configure an appliance proxy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Organizations in the left menu bar.
- Select an organization In the main pane, and then click the Appliance Proxy icon.

- In the Edit Appliance Proxy popup window, enter information for the following fields.

Field Description Organization (Required) Displays the organization. Appliances (Required) Select the VOS device. The drop-down list lists all VOS devices associated with the organization. LDAP Server Profile (Required) Select the LDAP server profile. Deconfigure Appliance Proxy Click to disable the appliance proxy. - Click OK.
Configure a User and Group Mapping Profile
To configure a user and group mapping profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors> Users/Groups > LDAP in the left menu bar.
- Select the User/Group Profile tab, and then click the
 Add icon.
Add icon.

- In the Add User/Group Profile popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the user and user group profile. Description Enter a text description for the user and user group profile. Tags Enter a keyword or phrase that allows you to filter the profile name. This is useful when you have many profiles and want to view those that are tagged with a particular keyword. Group Object Class (Required) Enter the group object class provided by your administrator. Group Name (Required) Enter the group name provided by your administrator. Group Member (Required) Enter the group member provided by your administrator. User Object Class (Required) Enter the user object class provided by your administrator. Username (Required) Enter the format of the username. An example is User Principal Name. Refresh Interval (Required) Enter the time period to refresh the profile.
Range: 60 through 86400 seconds
Default: 60 seconds
Password Max Age Enter the password maximum age provided by your administrator. An example is maxPwdAge. Password Last Set Enter the password last set provided by your administrator. An example is pwdLastSet. Email Enter the email address provided by your administrator. Mobile Enter the mobile provided by your administrator. Custom Filter (Group of Fields) - User
Enter the custom filter to query LDAP server for a user belonging to a group. An example is (o=ORG1). - Group
Enter the custom filter to query LDAP server for a group. An example is (o=ORG1). State Select to either enable or disable the user/group profile. - Click OK.
Search User and Group Information
The Director node periodically retrieves the entire listing for users and user groups from the LDAP server, either directly or through an LDAP proxy, and it stores the information in an internal cache. Updating the cache in this way ensures that the listing remains current.
By default, the Director periodically fetches the LDAP user and user group information every 60 minutes, updating the cache after it successfully retrieves the information.
The Director nodes lists the users and and user groups that are in the cache. If, at any time, the Director node is unable to fetch the user and user group information from the LDAP server, it lists the information from the previously cached data.
To configure an LDAP proxy, see Configure Appliance Proxy To Fetch the LDAP User and Group Profile, above. For information about configuring security policy, see Configure NGFW.
Define Kerberos for User and Group Authentication
Kerberos provides strong authentication for users and groups, an authentication that is stronger than LDAP. Kerberos uses secret key cryptography, so it never transmits the actual user credentials over the network. The following figure illustrates how Kerberos authentication works.

The client, here, the VOS device, authenticates itself to the authentication server, which forwards the username to the key distribution center (KDC). The KDC issues a ticket-granting ticket (TGT) with a timestamp, encrypts it using the ticket-granting service (TGS) secret key, and returns the encrypted result to the user. After the user verifies the validity of the TGT, the user is granted access to the requested service. The TGS issues a service ticket and a session key to the client. The client then sends the ticket to the service server along with its service request.
To configure Kerberos for user and group authentication, you upload a Kerberos keytab file to the Director node and then you define a Kerberos profile for authenticating users and groups.
Upload the Kerberos Keytab File
The Kerberos keytab file contains pairs of Kerberos principals and encrypted keys, which are derived from the Kerberos password. You use the Kerberos keytab file to authenticate the systems that use Kerberos without entering the password.
Note: If you change the Kerberos password, you must recreate all the keytabs.
To upload a Kerberos keytab file to the Director node:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > Kerberos Keytab in the left menu bar.
- Select the Director tab, and then click the
 Upload File icon to upload the keytab file to the Director node.
Upload File icon to upload the keytab file to the Director node.

- The Upload Kerberos Keytab Files to Director popup window displays.
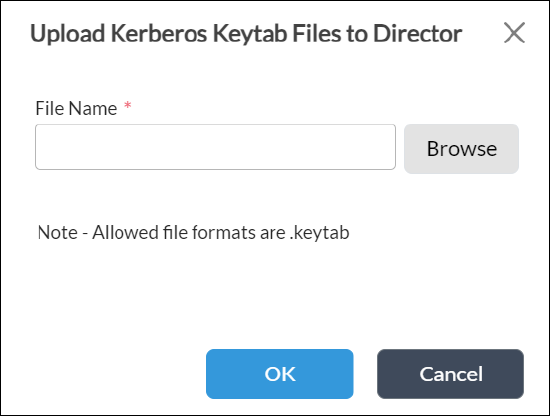
- Click the Browse button, and then select the keytab file.
- Click OK to upload the keytab file to the Director node.
- Select the Appliance tab, and then click the
 Upload File icon to map the Kerberos keytab file to the VOS device. The Upload Kerberos Keytab Files to Appliance popup window displays.
Upload File icon to map the Kerberos keytab file to the VOS device. The Upload Kerberos Keytab Files to Appliance popup window displays.

- In the Filename field, select the Kerberos keytab file. The Appliance field is populated by default.
- Click OK.
Configure a Kerberos Profile
To define a Kerberos profile for authenticating a user and group:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > Kerberos Profile in the left menu bar.

- Click the
 Add icon. In the Add Kerberos Profile popup window, enter information for the following fields.
Add icon. In the Add Kerberos Profile popup window, enter information for the following fields.
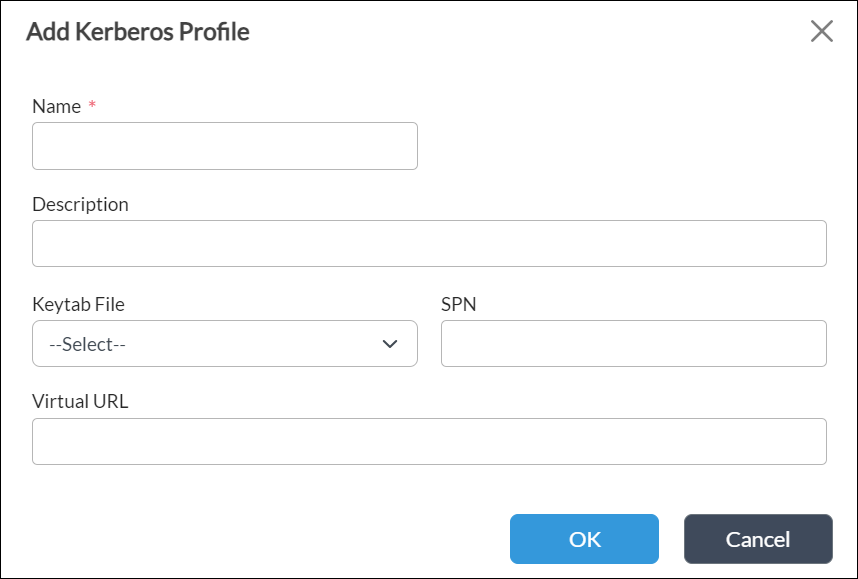
Field Description Name (Required) Enter a name for the Kerberos profile. Description Enter a text description for the Kerberos profile. Keytab File Select the keytab file that you uploaded in Upload the Kerberos Keytab File, above. SPN Enter the value for the service principal name.
Virtual URL Enter the Kerberos virtual URL. - Click OK.
Configure a Local Database
You can store user and group information in a local database on a VOS device, and the VOS device then uses the local database to authenticate, search for, and retrieve users and group membership information. This section describes how to configure local database users and groups.
Note: Configure and use a local database only for small set of users and groups, up to a maximum of 50 to 100. For a larger set of users and groups, it is recommended that you use a third-party user authentication solution, such as LDAP or Kerberos.
Configure Local Database Groups
To configure groups in the local authentication database:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > Local Database in the left menu bar.
- Select the Groups tab, and then click the
 Add icon.
Add icon.

- In the Add Group popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the local database group. Description Enter a text description for the group. - Click OK.
Configure Local Database Users
To configure users in the local authentication database:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > Local Database in the left menu bar.
- Select the Users tab in the horizontal menu bar, and then click the
 Add icon.
Add icon.

- In the Add User popup window, enter information for the following fields.

Field Description Username (Required) Enter a username for the local user. Password (Required) Enter the password to authenticate the user. First Name Enter the first name of the user. Last Name Enter the last name of the user. Email ID Enter an email address that can be used for two-factor authentication and to register the user with the system. Phone Number Enter a phone number that can be used for two-factor authentication and to register the user with the system. Description Enter a text description for the user. Group Name Select the group to which the user belongs. - Click OK.
Add External Database Users
VOS devices do not load the full database of users into its RAM because it may be too large. Therefore, when you use external authentication, through Kerberos, LDAP, SAML, or TACACS+, you may want to match a specific user or group in the policy. To do this, you define external users that you use in the match condition for CoS (QoS), NGFW, SD-WAN, and UTM policy rules.
To add an external database user:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors > Connectors > Users/Groups > External Database in the left menu bar.
- Select the Users tab in the horizontal menu bar, and then click the
 Add icon.
Add icon.

- In the Add User popup window, enter information for the following fields.

Field Description Name (Required) Enter the name of the external user. This is usually the user's email address. Description Enter a text description for the user. First Name Enter the first name of the user. Last Name Enter the last name of the user. Email ID Enter an email address that can be used for two-factor authentication and to register the user with the system. Phone Number Enter a phone number that can be used for two-factor authentication and to register the user with the system. - Click OK.
Configure SAML Profiles
Security Assertion Markup Language (SAML) authenticates users so that they can access multiple services and applications. SAML is useful when you want to access multiple services or applications when each service or application requires that you authenticate yourself, for example, Google and its related services. SAML is a standard for exchanging authentication between parties, and it is most commonly used for web browser–based single sign-on (SSO).
You can configure SAML SSO to log in using a single sign-on and and then access multiple services and applications. Similarly, you can configure SAML single sign-out to end sessions for multiple services and applications and then log out from only one session. You can use SAML authentication for services and applications that are external or internal to your organization.
VOS devices use SAML to support user-identification from external identity providers (IdP). You can use any third-party IdP to authenticate users, and you then apply the users, groups, roles, and location security policies on these users. Multiple VOS branch devices can use use SAML to authenticate users from a single centrally located authentication server. User authentication is done by the IdP, and the VOS device is aware only of the users. A captive portal is used to send redirections.
To configure SAML, you configure a SAML profile, which contains information about the third-party SAML IDP and other protocol information.
To configure a SAML profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > SAML Profile in the left menu bar.

- Click the
 Add icon. In the Add SAML Profile popup window, enter information for the following fields.
Add icon. In the Add SAML Profile popup window, enter information for the following fields.
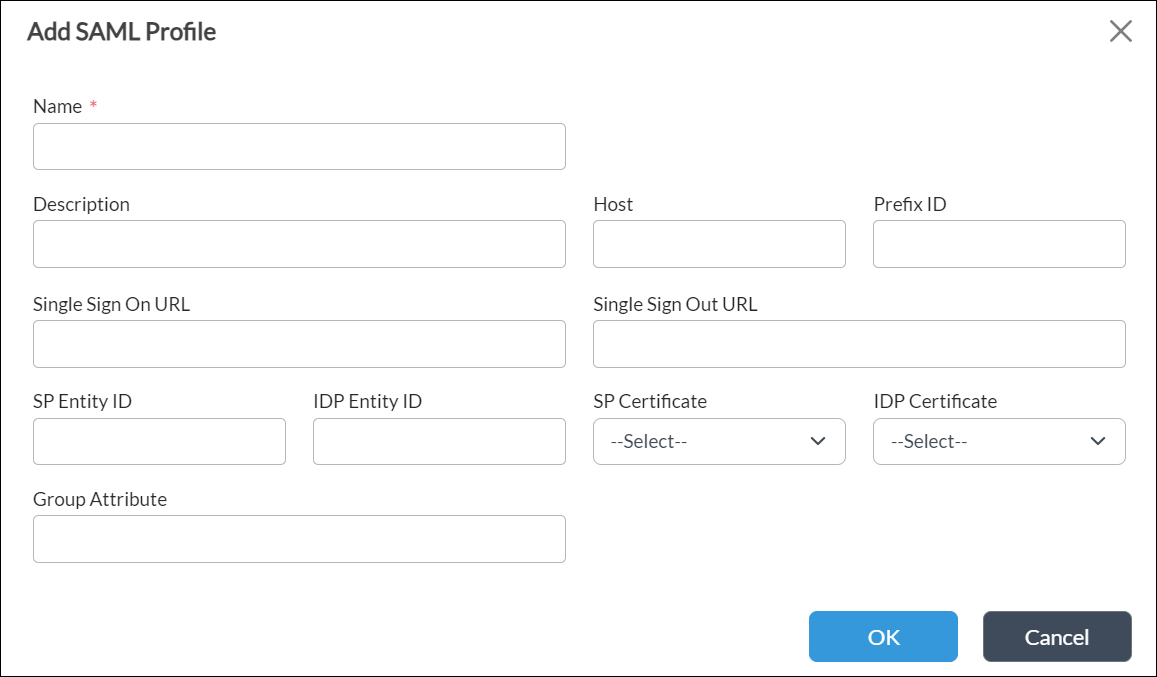
Field Description Name (Required) Enter a name for the SAML profile. Description Enter a text description for the SAML profile.
Host Enter the name of the host to which to apply the SAML profile. Prefix ID Enter the name of the external IdP. Single Sign-on URL Enter the URL of the IdP to use for single sign-on. Single Sign-out URL Enter the URL to point to for single sign-out. SP Entity ID Enter the entity ID of the service provider (that is, the VOS device). IdP Entity ID Enter the entity ID that uniquely identifies the SAML identity provider. SP Certificate Select the certificate that the service provider uses to authenticate and send a message to NGFW. NGFW uses this authentication information and provides access to the applications and services. IdP Certificate Select the authentication certificate issued by the identity provider. The IdP and NGFW use this certificate to sign SAML messages.
Group Attribute Enter the SAML group attribute to identify group value from the SAML response. - Click OK.
Configure a Certificate Authentication Profile
You configure a certificate authentication profile to use when you configure an authentication profile. For more information, see Configure an Authentication Method, below.
To define a certificate authentication profile:
- In Director view:
a. Select the Administration tab in the top menu bar.
b. Select Appliances in the left menu bar.
c. Select a device name in the main pane. The view changes to Appliance view. - Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > Certificate Authentication Profile in the left menu bar.

- Click the
 Add icon. In the Add Certificate Authentication Profile popup window, enter information for the following fields.
Add icon. In the Add Certificate Authentication Profile popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the certificate authentication profile. Description Enter a description for the certificate authentication profile. Server Certificate (Required) Select the server certificate for certificate authentication. Server Hostname (Required) Enter a hostname to start certificate authentication service. Server Address (Required) Enter the server address to start certificate authentication service. Server Port (Required) Enter the port number to start certificate authentication service.
Client CA Chain (Required) Select the CA chain to authenticate client certificate. Username Field Select the field that the VOS software uses to validate a name match in the client certificate:
- Alternative-name Email
- Subject Alternative-name Principal Name
- Subject Common-nameSubject
SNAT Pool Select an SNAT pool. To create an SNAT pool, click +SNAT Pool. For more information, see Configure SNAT Pools. Routing Instances (Required) Click the
 Add icon and select the routing instances to reach the certificate authentication server.
Add icon and select the routing instances to reach the certificate authentication server.Server Addresses Enter the WAN-VR IP address to start certificate authentication service. Verify OCSP Click to use the Online Certificate Status Protocol (OCSP) to verify a certificate authentication. - Click OK.
Configure SMTP Server Settings
For Releases 21.2.1 and later.
For Versa secure access (VSA), you configure SMTP server settings to support two-factor authentication (2FA). For more information about VSA, see Configure the Versa Secure Access Service and Use the Versa SASE Client Application.
With VSA, you can generate a one-time password (OTP) that is shared using SMS or email. When the OTP is shared by email, it is sent using the SMTP server details that you set in the SMTP server settings. The dynamically generated authentication code that a user enters allows you to verify the user's enterprise credentials and to determine whether they are using a cell phone or email.
By default, SMTP server settings are enabled and they use the default SMTP server. You can customize the SMTP server configuration.
To configure SMTP server settings:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > Settings > in the left menu bar. The main pane displays the SMTP settings pane.

- Click the
 Edit icon. The Add SMTP popup window displays.
Edit icon. The Add SMTP popup window displays.
- Clear the Default SMTP Server checkbox, and then enter information for the following fields.

Field Description Routing Instance Select the routing instance to use for the SMTP server. Timeout Enter the time, in seconds, after which the connection request to the SMTP server times out.
Default: 10 seconds
Host Enter the FQDN or IP address of the SMTP server. Port Enter the port number to use on the SMTP server.
Range: 0 to 65353
Username Enter the username to use to connect to the SMTP server.
Password Enter the password of the user to connect to the SMTP server. Security Level Select the security level to use to connect to the SMTP server:
- Plain text
- SMTPS
- StartTLS
CA Chain Select the CA chain to use to validate the x509 certificate. - Click OK.
Configure Active User Distribution for VMS
For Releases 22.1 and later.
You use active user distribution to apply uniform user or group-based policies for user traffic across gateways. When you enable active user distribution, when a user connects to a gateway or branch, the user login or logout information is shared across all branches or gateways using a Versa Messaging Server (VMS).
To configure active user distribution:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > Settings in the left menu bar.
- In the main pane, click the Edit icon in the Active User Distribution section. In the Manage Active User Distribution popup window, enter information for the following fields.

Field Description Send - Disable—Click to disable the sending of user login and logout events to VMS. This is the default.
- Enable—Click to enable the sending of user login and logout events to VMS.
Receive - Disable—Click to disable the receiving of user traffic information. This is the default.
- Enable—Click to enable the receiving of user traffic information.
Messaging Server (Group of Fields) Configure the VMS messaging server. - Profile
Configure a VMS profile. Enter information for the following fields.
- Key—Enter the authentication key for the VMS that shares user information.
- Profile Name—Enter the name of the profile VMS profile to share user information.
- Provider
Configure a VMS provider. Enter information for the following fields.
- Key—Enter the authentication key for the VMS server that shares user information.
- Provider Profile—Enter the name of VMS profile for which to share user information.
- Provider Tenant Name—Enter the provider tenant name for which to share user information.
- Click OK.
Configure an Authenticator Profile
Before you configure an authenticator profile, ensure that SMTP server settings are enabled, to support two-factor authentication using OTP. For more information about receiving an OTP through email, see Configure SMTP Server Settings, above.
To define an authenticator profile to use in the authentication profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Connectors > Users/Groups > Authenticator Profiles in the left menu bar.

- Click the
 Add icon. In the Add Authenticator Profiles popup window, enter information for the following fields.
Add icon. In the Add Authenticator Profiles popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the authenticator profile. Description Enter a text description for the authenticator profile.
Authenticator Type Select an authenticator type:
- REST-based Authenticator Service—Select to configure a one-time password in the One-Time Password group of fields.
- Time-based OTP Authenticator Service
One-Time Password (Group of Fields) - Mobile
Click to send a one-time password (OTP) to a mobile device. - Mobile Message Format
Enter the format for the mobile message. - Email Address
Click to send the one-time password using email and to share a QR code to use to register the SASE client to the user's email address. Note that if the email address of the user is not configured or if the user is not available through LDAP or SAML, the authentication fails and the user cannot register the client. For more information, see Enable a Time-Based One-Time Password. - Mail Message Format
Enter the format for the email. - OTP Format
Select the format for the one-time password:
- Alphabetic
- Alphanumeric
- Numeric—Note that for Release 21.2.1, only Numeric is supported.
- Cloud Profile
Select a cloud profile to use for one-time password–based authentication. For more information, see Configure a Cloud Profile. - Length
Enter the length of the one-time password.
- Time To Live
Enter how long the one-time password is valid. - Click OK.
Configure an Authentication Method
For Releases 22.1.3 and later.
You configure the authentication method to use for certificate authentication, Kerberos, LDAP, local, RADIUS, or SAML profiles, and you then use this method when you configure an authentication profile for user authentication.
To configure an authentication method:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > Authentication Methods in the left menu bar.

- Click the
 Add icon. In the Add Authentication Methods popup window, enter information for the following fields.
Add icon. In the Add Authentication Methods popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the authentication method. Description Enter a text description for the authentication method. Authentication Method (Group of Fields) - Methods
Select the authentication method, and then, in the field on the right, select a configured profile to associate with the authentication method:
- Certificate Authentication Profile—Select, and then select a certificate authentication profile. For more information, see Configure Certificate Authentication Profile, above.
- Kerberos Profile—Select, and then select a Kerberos profile. For more information, see Define Kerberos for User and Group Authentication, above.
- LDAP Profile—Select, and then select an LDAP profile. For more information, see Configure an LDAP Server Profile, above
- Local Profile—Select to use the local database on the VOS device for user authentication. Do not enter any informaiton in the field on the right.
- RADIUS Profile—Select, and then select a RADIUS server. For more information, see Configure RADIUS Servers, below.
- SAML Profile—Select, and then select a SAML profile. For more information, see Configure SAML Profiles, above.
- Click OK.
To associate an authentication method with an authentication profile, see Configure an Authentication Profile, below.
Configure an Authentication Profile
To define an authentication profile to use in the user and group authentication policy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > Authentication Profiles in the left menu bar.

- Click the
 Add icon. The Add Authentication Profile popup window displays. For Releases 21.2.1 and earlier, the popup window has one tab, General. For Releases 22.1.3 and later, the popup window has two tabs, General and Rules.
Add icon. The Add Authentication Profile popup window displays. For Releases 21.2.1 and earlier, the popup window has one tab, General. For Releases 22.1.3 and later, the popup window has two tabs, General and Rules.

- Select the General tab, and enter information for the following fields.
Field Description Name (Required) Enter a name for the authentication profile name. Description Enter a text description for the authentication profile. Tags Enter a keyword or phrase that allows you to filter the authentication profile. Tagging is useful when you have many profiles and want to view those that are tagged with a particular keyword. Authentication Type (For Releases 22.1.3 and later.) Select the type of authentication to use:
- Active—Use active authentication by using one or more Kerberos, LDAP, and SAML profiles.
- Passive—Use passive authentication using a Versa message service (VMS) profile.
VMS Profile (For Releases 22.1.3 and later.) If you select passive authentication, select a VMS profile to use for passive authentication. For more information, see Install and Configure VMS. Local Database (For Releases 22.1.3 and later.) Click to use the database on the local VOS device for storing the user and group authentication information on the local server. It is recommended that you use the local database only for user groups no larger than 50 to 100 users. Caching Mode Select the caching mode:
- Cookie Based—Set the cookie in the user's browser, and do not store the user information on the device.
- IP Based—Map users using their IP address as the key.
Cache Expiration Enter the time, in minutes, after which cache for the authentication profile expires.
Default: 10 minutes
Cookie Name If you select cookie-based caching, enter the authentication cookie name. Concurrent Login If you select IP-based caching, enter the number of concurrent logins a user can perform from different devices. Routing Instance If you select an LDAP provider, select the routing instance to use to reach the LDAP server. Expiration Mode Select the mode to use to end a session:
- Fixed Interval—Use the time specified in the cache expiration as the time interval to end a session.
- Inactivity—Use the time specified in the cache expiration as the interval of inactivity after which to end a session.
LEF Profile Select a LEF profile to use to register logs for the profile. Default Profile Click to mark the LEF profile as the default profile. Kerberos Profile (For Releases 21.2.2 and earlier.) If you select Kerberos authentication, select a Kerberos profile to associate with the authentication profile. Click + Create Kerberos Profile to add a new Kerberos profile. For more information, see Create a Kerberos Profile, above.
LDAP Profile (For Releases 21.2.2 and earlier.) If you select LDAP authentication, select an LDAP profile to associate with this authentication profile. Click + Create LDAP Profile to add a new LDAP profile. For more information, see Configure an LDAP Server Profile, above.
SAML Profile (For Releases 21.2.2 and earlier.) If you select SAML authentication, select a SAML profile to associate with this authentication profile. Click + Create SAML Profile to add a new SAML profile. For more information, see Configure SAML Profiles, above.
Certificate Authentication Profile (For Releases 21.2.1 and earlier.) Select a certificate authentication profile to associate with this authentication profile. Click + Create Cert Authentication Profile to add a new certificate authentication profile. For more information, see Configure a Certificate Authentication Profile, above.
Proactive Reauthentication If you select a Kerberos profile and set Expiration Mode as Fixed Interval, click to proactively reauthenticate midway through the expiration interval. For example, if the expiration interval is set to 10 minutes, one of the TCP sessions is selected for Kerberos authentication when the expiration time reaches 5 minutes (the halfway point). If the domain client browser follows the redirection for Kerberos, the user session is automatically authenticated. If the response for a TCP session authentication is not received within 30 seconds or if the reauthentication fails, another TCP session is selected for redirection until the reauthentication is successful. After a TCP session is reauthenticated, the expiration interval is reset to the configured interval (in this example, 10 minutes). This mechanism ensures that all the traffic is not redirected and that the user is not logged out at the end of the expiration interval. Default Authenticator Select a default authenticator profile.
Note that for Releases 21.2.1 and earlier, this field is called Authentication Profiles
Default Authentication Method (For Releases 22.1.3 and later.) Select an authentication method to associate with the authentication profile.
Click the
 Add icon to add more authentication methods. For more information, see Configure an Authentication Method, above.
Add icon to add more authentication methods. For more information, see Configure an Authentication Method, above. - For Releases 21.2.1 and earlier, click OK.
- For Releases 22.1.3 and later, select the Rules tab.

- Click the
 Add icon. The Add Rules Popup window displays. Select the General tab, and enter information for the following fields.
Add icon. The Add Rules Popup window displays. Select the General tab, and enter information for the following fields.

Field Description Name (Required) Enter a name for the authentication profile rule. Description Enter a text description for the authentication profile rule. - Select the Match tab, and enter information for the following fields.

Field Description Domains Click the
 Add icon, and then enter a domain name to use as match filter in the rule. Click the
Add icon, and then enter a domain name to use as match filter in the rule. Click the  Add icon to add more domains.
Add icon to add more domains. - Select the Set tab, and enter information for the following fields.

Field Description Authentication Methods Click the  Add icon and select an authentication method to associate with the rule. Click the
Add icon and select an authentication method to associate with the rule. Click the  Add icon to add more authentication methods. For more information, see Configure an Authentication Method, above.
Add icon to add more authentication methods. For more information, see Configure an Authentication Method, above.Authenticator Profiles Click the  Add icon and select an authenticator profile to associate with the rule. Click the
Add icon and select an authenticator profile to associate with the rule. Click the  Add icon to add more authenticator profiles. For more information, see Configure an Authenticator Profile, above.
Add icon to add more authenticator profiles. For more information, see Configure an Authenticator Profile, above. - Click OK.
Configure Authentication Policies
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Authentication > Policies in the left menu bar.
- Select the Authentication Policies tab, and then click the
 Add icon.
Add icon.

- In the Add Policies popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the authentication policy. Description Enter a text description for the policy. Tags Enter a keyword or phrase that allows you to filter the policy name. This is useful when you have many policies and want to view those that are tagged with a particular keyword. - Click OK.
Configure RADIUS Servers
For Releases 22.1.3 and later.
To configure RADIUS servers to use for user authentication:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Object and Connectors > Connectors > Users/Groups > RADIUS Servers in the left menu bar.

- Click the
 Add icon. In the Add RADIUS Servers popup window, enter information for the following fields.
Add icon. In the Add RADIUS Servers popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the RADIUS server.
Description Enter a text description for the RADIUS server. IP Address (Required)
Enter the IP address of the RADIUS server. Port (Required) Enter the port number to use on the RADIUS server. Routing Instance Enter the routing instance to use to reach the RADIUS server. Shared Secret (Required) Enter the RADIUS shared secret (password) string. - Click OK.
Configure Rules for Authentication Policies
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Authentication > Policies in the left menu bar.
- Select Rules tab, and then click the
 Add icon in the dashboard to add a new authentication policy. The Add Rules popup window displays.
Add icon in the dashboard to add a new authentication policy. The Add Rules popup window displays.

- (For Releases 21.2.1 and later.) If you have already added one or more rules, the Configure Rule Order popup window displays.
- Select where you want to insert the policy rule, either at the beginning or end of the existing rules.

- If you select a rule and then click the
 Add icon, the Configure Rule Order popup window displays the following options:
Add icon, the Configure Rule Order popup window displays the following options:
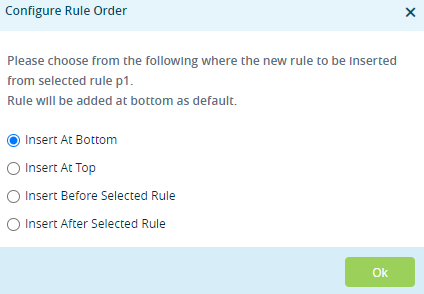
- Select the order to insert the rule (at the beginning or end bottom of the existing rules, or before or after the selected rule).
- Click OK. The Add Rule popup window displays.
- Select where you want to insert the policy rule, either at the beginning or end of the existing rules.
- Select the General tab, and enter information for the following fields.

Field Description Name (Required) Enter a name for the authentication policy rule. Description Enter a text description for the rule. Tags Enter a keyword or phrase that allows you to filter the rule name. This is useful when you have many policies and want to view those that are tagged with a particular keyword. Disable Rule Click to not activate the access policy rule after you configure it. - Select the Source tab to define the source zone and the source address of the incoming (source) traffic to which the authentication policy rule applies. Enter information for the following fields.

Field Description Source Zone Select the source zone to apply the rule to traffic coming from any interface in the specified zone. Click the
 Add icon to add more security zones.
Add icon to add more security zones.Source Address Select and specify one or more source address to which the rule applies. Click the
 Add icon to add more source addresses.
Add icon to add more source addresses.Source Address Negate Enable this to select any address except the configured addresses. Region Click the  Add icon to select a region.
Add icon to select a region.State Click the  Add icon to select a state.
Add icon to select a state.City Click the  Add icon to select a city.
Add icon to select a city.Source Location Negate Click to have the rule select any location except the configured locations. Custom Geo Circle Click the  Add icon to select a custom geographic circle, which consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. For more information, see Configure Geolocation Objects.
Add icon to select a custom geographic circle, which consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. For more information, see Configure Geolocation Objects. - Select the Destination tab to define the destination zone and the destination address of the outgoing (destination) traffic to which the authentication policy rule applies. Enter information for the following fields.

Field Description Destination Zone Select the destination zone to apply the rule to traffic coming from all interfaces into a given zone. Click the
 Add icon to add more security zones.
Add icon to add more security zones.Destination Address Select and specify one or more destination address to apply the rule to the traffic marked to the specific destination. Note that for an explicit proxy, the destination address is the address on which the explicit proxy is configured, so configuring this option with explicit proxy is not effective. Click the
 Add icon to add more destination addresses.
Add icon to add more destination addresses.Destination Address Negate Enable this to specify any address except the configured addresses. For explicit proxy, the destination address is the address on which the explicit proxy is configured. Configuring this option with explicit proxy is not effective.
Region Click the  Add icon to select a region.
Add icon to select a region.City Click the  Add icon to select a city.
Add icon to select a city.State Click the  Add icon to select a state.
Add icon to select a state.Destination Location Negate Click to have the rule select any location except the configured locations. Custom Geo Circle Click the  Add icon to select a custom geographic circle, which consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. For more information, see Configure Geolocation Objects.
Add icon to select a custom geographic circle, which consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. For more information, see Configure Geolocation Objects. - Select the Application/URL tab to select the applications and URLs to which the security access rule applies. Enter information for the following fields.

Field Description Applications Click the
 Add icon and then select one or more predefined or custom application signature and apply the authentication policy rule to the application. For more information, see Configure Custom Application Objects.
Add icon and then select one or more predefined or custom application signature and apply the authentication policy rule to the application. For more information, see Configure Custom Application Objects.URL Categories Click the
 Add icon and then select one or more predefined/custom URL categories and apply the authentication policy rule to the URL. For more information, see Configure URL Category Objects.
Add icon and then select one or more predefined/custom URL categories and apply the authentication policy rule to the URL. For more information, see Configure URL Category Objects.Reputations (For Releases 21.2.1 and later.) Click the  Add icon and then select one or more predefined URL reputations and apply the security access rule to the URL. For more information, see View a Predefined URL Reputation.
Add icon and then select one or more predefined URL reputations and apply the security access rule to the URL. For more information, see View a Predefined URL Reputation. - Select the Header/Schedule tab to define the IP header, services and schedule to which the authentication policy rule applies. Enter information for the following fields.

Field Description IP (Group of Fields) - IP Version
Select the IP version. - IP Flags
For IPv4, select the IP flag:
- Don’t Fragment
- More Fragment
- DSCP
Enter a differentiated service code point value to classify the way the IP packet is queued to get forward, then click the  Add icon.
Add icon.TTL (Group of Fields) - Condition
Select the TTL condition of the IP packet that the security access policy rule verifies:
- Greater than or equal to—TTL value must be greater than or equal to the specified value for the security access rule to trigger.
- Less than or equal to—TTL value must be less than or equal to the specified value for the security access rule to trigger.
- Equal to—TTL value must be equal to the specified value for the security access rule to trigger.
- Value
Enter the TTL value to match with the TTL condition. Others (Group of Fields) - Schedules
Select a schedule to specify when the security access rule is in effect. You can also create and add a new schedule. For more information, see Configure Schedule Objects.
Services table Click the  Add icon then select one or more services to apply the security access rule to the configured services.
Add icon then select one or more services to apply the security access rule to the configured services. - Select the Enforce tab to specify the applications and URLs to which the authentication policy rule applies. Enter information for the following fields.

Field Description Actions Select the action to impose on the traffic:
- Do Not Authenticate—Select to not authenticate the profile.
- Authenticate Using Profile—Select, then select an authentication profile.
Log Select how to log the data:
- Do Not Log—Do not log the authentication profile information.
- Log Using Profile—Select, and then select a LEF profile from the list, or click Default Profile to use the default LEF.
- Click OK.
Match Users and Groups in Access Policy
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Security > Policies in the left menu bar.

- Select the Rules tab, and click a security rule in the main pane to make changes to it. The Edit Rule popup window displays.
- Select the Users/Groups tab, and enter information for the following fields.
Field Description Match Users Select the user to match with the access policy:
- Any
- Known
- Unknown
- Selected—Click the
 Add icon and select users from the drop-down list.
Add icon and select users from the drop-down list.
User Group Profile If the match is for selected users, select the user group profile to access the network in the security policy.
Local Database Click to use local database to store the user and group authentication information on the local server. It is recommended that you use a local database only when the number of user sand groups does not exceed 50 to 100.
External Database Click to use an external database to store user authentication information.
- Click OK.
Supported Authentication Protocols
For NGFW, VOS devices support various protocols, including LDAP, SAML, and Kerberos (in both HTTP and HTTPS modes).
End clients use captive portal autodetection to attempt to fetch a preconfigured HTTP URL. If the path includes a captive portal, the client redirects with its own response page. This is different from what the device expects to see from the server. Thus, the device pops up an application to follow the link that the captive portal would have sent in the redirect request. Because the generated traffic is plain text, it does not require an SSL proxy. For a captive portal to redirect a request, the captive portal must understand that it is an HTTP request. In response to that HTTP request, the captive portal must redirect with an appropriate response code. This can be done only if the captive portal sees an HTTP request in clear text. The entire response to an HTTPS request cannot be in clear text, because the SSL layer at the client would discard it as a malformed SSL record. Also, without decryption, the system cannot send an encrypted response to the client.
The following table describes the supported authentication protocols.
| Authentication Protocol | Session Protocol | Session Type | Supported | SSL Decryption Required | Notes |
|---|---|---|---|---|---|
| Kerberos | HTTP | No Proxy | No | Not applicable | None |
| Forward Proxy | No | Not applicable | None | ||
| Transparent Full Proxy | Yes | Not applicable | None | ||
| Explicit Full Proxy | Yes | Not applicable | None | ||
| HTTPS | No Proxy | No | Not applicable | None | |
| Forward Proxy | No | Not applicable | None | ||
| Transparent Full Proxy | Yes | Yes | Decryption required to redirect session to virtual URL to get Kerberos token | ||
| Explicit Full Proxy | Yes | No | Kerberos token is received from CONNECT HTTP method and hence does not require decryption |
||
| LDAP | HTTP | No Proxy | Yes | Not applicable | None |
| Forward Proxy | Yes | Not applicable | None | ||
| Transparent Full Proxy | Yes | Not applicable | None | ||
| Explicit Full Proxy | Yes | Not applicable | None | ||
| HTTPS | No Proxy | Yes | Yes | Decryption required to redirect session to authentication page | |
| Forward Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| Transparent Full Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| Explicit Full Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| Local | HTTP | No Proxy | Yes | Not applicable | None |
| Forward Proxy | Yes | Not applicable | None | ||
| Explicit Full Proxy | Yes | Not applicable | None | ||
| HTTPS | No Proxy | Yes | Yes | Decryption required to redirect session to authentication page | |
| Forward Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| Transparent Full Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| Explicit Full Proxy | Yes | Yes | Decryption required to redirect session to authentication page | ||
| SAML | HTTP | No Proxy | Yes | Not applicable | None |
| Forward Proxy | Yes | Not applicable | None | ||
| Transparent Full Proxy | Yes | Not applicable | None | ||
| Explicit Full Proxy | Yes | Not applicable | None | ||
| HTTPS | No Proxy | Yes | Yes | Decryption required to redirect session to IdP | |
| Forward Proxy | Yes | Yes | Decryption required to redirect session to IdP | ||
| Transparent Full Proxy | Yes | Yes | Decryption required to redirect session to IdP | ||
| Explicit Full Proxy | Yes | Yes | Decryption required to redirect session to IdP |
Monitor User Identification Statistics
You monitor user ID statistics to view the reports for profiles associated with a user ID. For more information, see Monitor Device Services.
To monitor user identification statistics:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select the Provider Organization > Services tab.
- Select NGFW > User Identification, and then select one of the following options from the drop-down list: Authentication Profile, Local Database, LDAP Profile, Kerberos Profile, SAML Profile, or Live Users. The user ID statistics display.

Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 20.2.2 adds support for authenticator profiles.
- Release 21.2.1 adds support for certificate authentication profile and SMTP server settings, and configuring rule order for authentication policy rules.
- Release 22.1 adds support for configuration of active user distribution for VMS.
- Release 22.1.3 adds support for configuration of additional authentication methods, associating authentication profiles with authentication methods, configuring authentication profile rules, and configuring RADIUS servers.
Additional Information
Configure CA Certificates, Key File, and CA Chains
Configure File Filtering
Configure IEEE 802.1X Device Authentication
Configure Kerberos Authentication
Configure Layer 7 Objects
Configure NGFW
Install and Configure VMS
Configure Policy-Based Forwarding
Configure Schedule Objects
Configure SD-WAN Policy
Configure URL Filtering
Configure the Versa Secure Access Service
Configure Versa SASE Clients
Monitor Device Services
