Configure IEEE 802.1X Device Authentication
![]() For supported software information, click here.
For supported software information, click here.
IEEE 802.1X is a port-based network access control (PNAC) protocol that authenticates devices before they can connect to the network and gain access to network resources. You can configure IEEE 802.1X to prevent unauthorized network devices from accessing the network and to allow known devices to connect to the network without requiring authentication. You configure IEEE 802.1X on a VNI interface.
IEEE 802.1X has three required components:
- Supplicant—A client that runs on the endpoint and submits credentials for authentication. A Versa Operating SystemTM (VOSTM) interface always acts as an authenticator. If you configure a RADIUS server as the authenticating server, the VOS interface acts only as an authenticator and sends information about the supplicant to the authenticating server. If you use local authentication (that is, you do not use a RADIUS server or an identity provider server), the VOS interface acts as both the authenticator and the authenticating server.
- Authenticator—A network access device that facilitates the authentication process by relaying the credentials of the supplicant to the authentication server. The authenticator enforces both the locally configured network access policy and the dynamically assigned network access policy returned by the authentication server. If you configure a VOS interface with the authenticator role, the VOS interface acts as the authenticator.
- Authentication server—A server that validates the credentials sent by the supplicant and determines what level of network access the end user or device should receive. You can use a RADIUS server as the authentication server, or you can use local authentication so that the VOS device acts as the authentication server.
When you configure a VOS VNI interface to be an authenticator, a RADIUS server can authenticate each user or device connected to a port before that user or device can access any network services.
For Releases 22.1.3 and later, the VOS IEEE 802.1X software uses Extensible Authentication Protocol over LAN (EAPOL) for communication between a client device and a LAN switch. If a client does not use EAPOL (known as a non-EAPOL client), the MAC Authentication Bypass (MAB) protocol authenticates the client by sending their MAC address information to a RADIUS server. A non-EAPOL client is learned initially on a guest VLAN, and its MAC address is sent to a RADIUS server for authentication. You can send the MAC addresses with or without the colon (:) delimiter. The RADIUS server uses the MAC address as the username and password. After a non-EAPOL client has been authenticated, it is moved from the guest VLAN to the RADIUS-assigned VLAN or to the default VLAN.
The following table lists the RADIUS attributes that VOS devices support.
| Value | Attribute Name | Data Type | Description |
|---|---|---|---|
| 1 | User-Name | Text | Name of user to authenticate |
| 2 | User-Password | String | Password of user to authenticate |
| 4 | NAS-IP-Address | IPv4 address | IP address of the network access server (NAS) that is requesting authentication of the user |
| 5 | NAS-Port | Integer | Physical port number of the NAS that is authenticating the user |
| 6 | Service-Type | Enumerated data type | Type of service that the user is requesting, or type of service to provide |
| 8 | Framed-IP-Address | IPv4 address | IP address to configure for the user |
| 12 | Framed-MTU | Integer | Maximum transmission unit size to configure for the user if the MTU is not negotiated some other way |
| 24 | State | String | String to use to maintain state information between the device and the RADIUS server |
| 31 | Calling-Station-Id | Text | Phone number from which the call originated |
| 44 | Acct-Session-Id | Text | Accounting identifier |
| 49 | Acct-Terminate-Cause | Enumerated data type | Reason that the service terminated |
| 55 | Event-Timestamp | Time | Time that the event occurred on the NAS, in seconds, since January 1, 1970 00:00 UTC. |
| 61 | NAS-Port-Type | Enumerated data type | Type of physical port that the NAS is using to authenticate the user. |
| 80 | Message-Authenticator | String | Authentication checksum of Access-Request packet |
To configure IEEE 802.1X device authentication, you do the following:
- If you are using RADIUS as the 802.1X authentication server, configure the RADIUS server.
- Configure an 802.1X authentication profile for one of the following cases:
- If you are using external RADIUS authentication, define the information that the authenticator (that is, the authenticating VOS device) uses to communicate with the RADIUS server.
- If you are using local authentication, define the credentials of the authenticator so that it can communicate with the supplicant.
- To enable authentication on a specific interface, configure the interfaces for 802.1X authentication to control.
Configure a RADIUS Server
If you are using RADIUS as the 802.1X authentication server, configure the RADIUS server:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select the Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > Organization > RADIUS Servers in the left menu bar.

- Click the
 Add icon. In the Add RADIUS Servers popup window, enter information for the following fields.
Add icon. In the Add RADIUS Servers popup window, enter information for the following fields.

Field Description Name (Required) Enter the name of the RADIUS server.
Value: Text string from 1 through 255 characters long
Default: NoneDescription Enter a text description for the RADIUS server.
Value: Text string from 1 through 255 characters
Default: NoneIP Address (Required) Enter the IP address of the RADIUS server. Port (Required)
Enter the number of the listening port on the RADIUS server. For UDP, port 1812 is commonly used.
Range: 0 through 65535
Default: None
Routing Instance Select the routing instance to use to communicate with the RADIUS server. Shared Secret (Required)
Enter a password that the VOS device uses to access the RADIUS server. Priority Enter the order of priority to use the RADIUS server when when multiple servers are configured for authentication. - Click OK.
Configure an 802.1X Authentication Profile
You can configure an 802.1X authentication profile for one of the following cases:
- If you are using external RADIUS authentication, define the information that the authenticator (that is, the authenticating VOS device) uses to communicate with the RADIUS server.
- If you are using local authentication, define the credentials of the authenticator so that it can communicate with the supplicant.
To configure an 802.1X authentication profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select the Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > Organization > Authentication Profile in the left menu bar.
- Click the
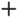 Add icon. In the Add Authentication Profile popup window, enter information for the following fields.
Add icon. In the Add Authentication Profile popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the 802.1X authentication profile
Value: Text string from 1 through 255 characters long
Default: NoneType Select the 802.1X authentication type:
- Local—Perform 802.1X authentication on the local VOS device. VOS devices support certificate authentication based on EAP-TLS.
- RADIUS—Perform 802.1X authentication using a RADIUS server.
Description Enter a text description of the 802.1X authentication profile.
Value: Text string from 1 through 255 characters
Default: NoneTrusted Certificate Database (Required) For the Local 802.1X authentication type, select the trusted certificate database to use to validate the client (supplicant) certificate. Certificate (Required) For the Local 802.1X authentication type, select the certificate to use for local authentication. - If you select RADIUS as the 802.1X authentication type, the Add Authentication Profile popup window displays.
For Releases 22.1.1 and later:

For Releases 21.2 and earlier:
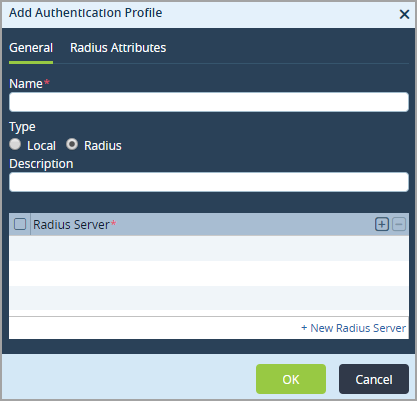
- In the Name field, enter a name for the authentication profile.
- Click the
 Add icon in the RADIUS Server table, and then select the RADIUS server to associate with the authentication profile.
Add icon in the RADIUS Server table, and then select the RADIUS server to associate with the authentication profile. - If the server is not listed, click +New RADIUS Server, and then configure a RADIUS server. For redundancy, you can configure multiple RADIUS servers. For more information, see Configure a RADIUS Server, above.
- Select the RADIUS Attributes tab to configure the RADIUS attributes to use to communicate AAA information between the authenticator and the RADIUS server. Enter information for the following fields.
For Releases 22.1.1 and later:
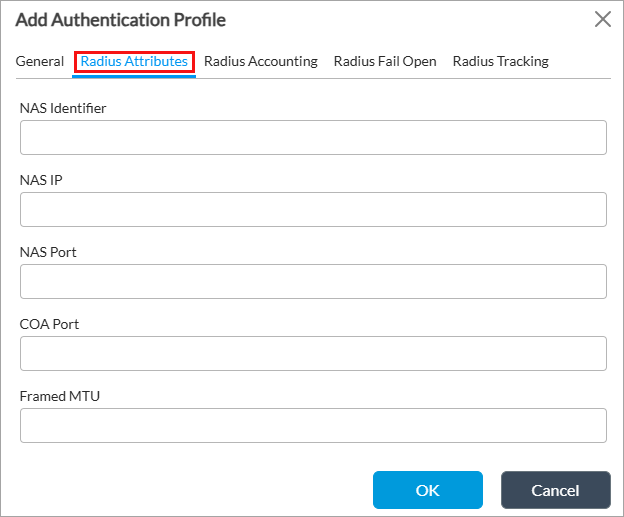
For Releases 21.2 and earlier:

Field Description NAS Identifier Enter a text string to identify the network access server (NAS) that originates the access request. NAS IP Enter the IP address of the NAS that is requesting authentication.
Default: None
NAS Port Enter the number of the physical port to use to connect to the NAS that is authenticating the user.
Range: 0 through 65535
Default: None
COA Port (For Releases 22.1.4 and later.) Enter the number of the port on the RADIUS server that handles change of authorization (CoA) requests. CoA allows you to dynamically change the attributes or state of an authenticated session without client reauthentication.
Default: NoneFramed MTU (For Releases 22.1.4 and later.) Enter the Maximum Transmission Unit (MTU) for the user when it is not negotiated through methods like Point-to-Point Protocol (PPP). This value can be included in Access-Accept packets or used as a hint in Access-Request packets to inform the Network Access Server (NAS) of the maximum packet size that can be sent without fragmentation. The RADIUS server is not obligated to enforce this limit.
Default: None - (For Releases 22.1.3 and later.) Select the RADIUS Accounting tab, and then click Enable to enable RADIUS accounting. When you enable IP accounting, the VOS device sends accounting information, including framed IP information, to the RADIUS server.

- (For Releases 22.1.3 and later.) Select the RADIUS Fail Open tab, and then click Enable to enable RADIUS fail open. RADIUS fail open provides network access to EAPOL and non-EAPOL clients when the RADIUS server is not reachable.

- (For Releases 22.1.3 and later.) Select the RADIUS Tracking tab, and then click Enable to enable RADIUS tracking. RADIUS tracking tracks the reachability of RADIUS servers to check for further authentication. Once a RADIUS server is reachable, the authentication is retried. Enter how often, in seconds, to send tracking requests. The interval can be from 30 through 300 seconds, and there is no default value.
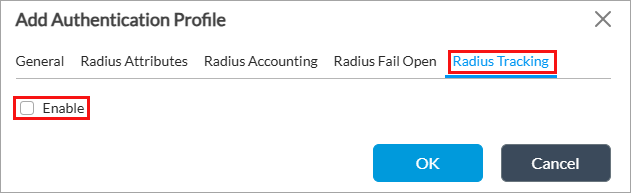
- Click OK.
Configure 802.1X Authentication Control
To enable 802.1X authentication on a specific interface, configure the interface for 802.1X authentication to control:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select the Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > Organization > dot1x > Authentication Control in the left menu bar, and the select the dot1x tab.
For Releases 22.1.1 and later:

For Releases 21.2 and earlier:

- Click the
 Edit icon to configure 802.1X on an interface. In the dot1x popup window, enter information for the following fields.
Edit icon to configure 802.1X on an interface. In the dot1x popup window, enter information for the following fields.
For Releases 22.1.1 and later:


For Releases 21.2 and earlier:

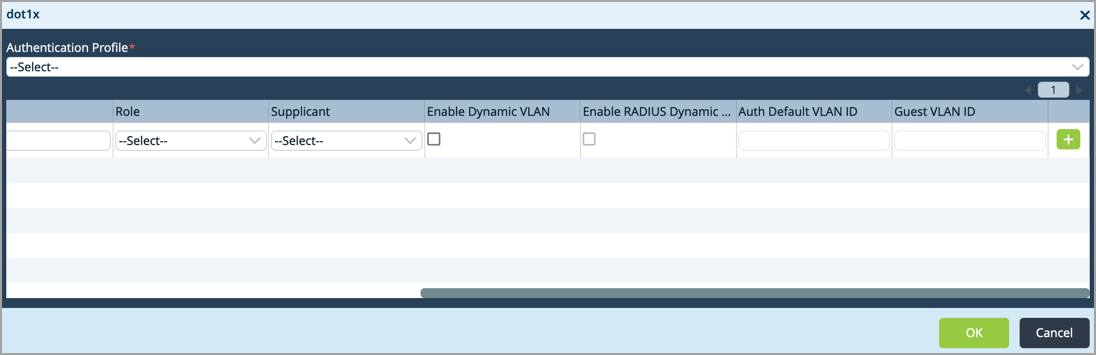
Field Description Authentication Profile (Required)
Select the name of the 802.1X authentication profile. This is a profile that you created in Configure an 802.1X Authentication Profile, above. Interface Name (Required) Select the interface on which to configure 802.1X authentication.
Quiet Period Enter how long the interface waits after a failed authentication attempt before again attempting to authenticate a user.
Range: 0 through 600 seconds
Default: None
No Reauthentication Click to disable periodic reauthentication of users. Reauthentication Interval Enter the interval at which to reauthenticate the user. By default, a user is reauthenticated at each configured interval.
Range: 10 through 86400 seconds
Default: None
Retries Enter how many times to try to authenticate the port after an initial failure. The port remains in a wait state during the quiet period after the authentication attempt.
Range: 1 through 10
Default: 2
Roles Select the interface role:
- Authenticator—Interface acts as the authenticator.
- Supplicant—Interface acts as a supplicant.
Default: None
Supplicant Select the type of supplicant:
- Single—Authenticate only the first end device. All other end devices that connect to the port later are allowed access without any further authentication. The subsequent devices effectively piggyback on the first end device’s authentication.
- Single-secure—Allow only one end device to connect to the port at a time. No other end device can connect until the first device logs out.
- Multiple—Allow multiple end devices to connect to the port. Each end device is authenticated individually.
Default: None
Enable Dynamic VLAN Click to enable dynamic VLANs. Enable RADIUS Dynamic VLAN Click to enable RADIUS dynamic VLANs. Authentication Default VLAN ID Enter the ID of the default VLAN to use for authentication. Authentication Default Voice VLAN (For Releases 22.1.3 and later.) Enter the ID of the default voice VLAN to use for authentication. Guest VLAN ID Enter the ID of the guest VLAN. Enable Multicast Frames (For Releases 22.1.3 and later.) Click to enable multicast frames. - Click the
 Add icon to add the profile.
Add icon to add the profile. - Select the MAC Address Bypass tab in the horizontal menu bar,

- Click the
 Edit icon to configure a list of MAC address bypasses on an interface. These are MAC addresses that do not need to be authenticated. Enter information for the following fields.
Edit icon to configure a list of MAC address bypasses on an interface. These are MAC addresses that do not need to be authenticated. Enter information for the following fields.

Field Description Address (Required) Enter the MAC address of the device that is allowed to bypass the 802.1X authentication process. Description Enter a text description of the MAC address.
Value: Text string from 1 through 255 characters
Default: NoneInterface Name Select the interface that the MAC address is allowed to connect to without requiring authentication. - (For Releases 22.1.3 and later.) Select the MAB Authentication tab in the horizontal menu bar. Note that before you enable MAB authentication, you must configure the interface to be in trunk mode. For more information, see Configure Trunk Interfaces.

- Click the
 Edit icon. The MAB Authentication popup window displays.
Edit icon. The MAB Authentication popup window displays.

- Click Enable to enable MAB authentication, and then enter information for the following fields.

Field Description Allow Delimiter Click to send MAC addresses with the colon (:) delimiter. All Interfaces (For Releases 22.1.4 and later.) Select Enable to apply the port reset feature globally to all interfaces, or select Disable to turn it off. This global setting applies only if port reset is not configured on an interface. For example, if an interface has its own port reset setting (enabled or disabled), the specific interface setting overrides the global setting.
Port Reset Timer (For Releases 22.1.4 and later.) Enter the time (in seconds) that the port checks for the presence of any active client or supplicant on the 802.1x interface before it resets. If All Interfaces is set to Enable, the port reset timer applies to all interfaces for which the timer is not set.
Range: 30 through 3600 seconds.
- (For Releases 22.1.4 and later.) Click to Diable Fallback MAB to EAP Transition to disable falling back to MAB authentication when an Extensible Authentication Protocol (EAP) session starts in between and fails to authenticate.
- Click OK.
Verify 802.1x Authentication Information
- In Director view:
- Select the Administration tab in the top menu bar.
- Select the Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select an organization in the left menu, and then select the Services tab in the horizontal menu.
- Select dot1x in the Networking section to view the interface details and other statistics. In the drop-down menu, select the level of detail to view.
- Select Brief to view the interface roles as authenticator or supplicant. This view shows the authenticated supplicant count if the interface role is authenticator, and it shows the authentication state of the interface that is configured as a supplicant.

- Select Detail to view details about the authenticator and supplicant for each interface, including configuration parameters, and authentication and EAP packet statistics. The Detail screen also provides information about the connected supplicant state for the interface that is configured as the authenticator.

- Select Statistics to view per-interface packet statistics.

Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 22.1.3 supports MAB authentication bypass, RADIUS accounting, RADIUS failover, and RADIUS tracking.
- Release 22.1.4 supports COA port, framed MTU, all interfaces, and port reset timer.
Additional Information
Configure Dynamic VLANs Using 802.1X Authentication Flows
Configure Layer 2 Forwarding
