Configure Kerberos Authentication
![]() For supported software information, click here.
For supported software information, click here.
You can configure Kerberos authentication on Versa Operating SystemTM (VOSTM) devices. Kerberos provides strong authentication for users and groups, and its authentication is stronger than LDAP. Kerberos uses secret key cryptography, so it never transmits user credentials over the network.
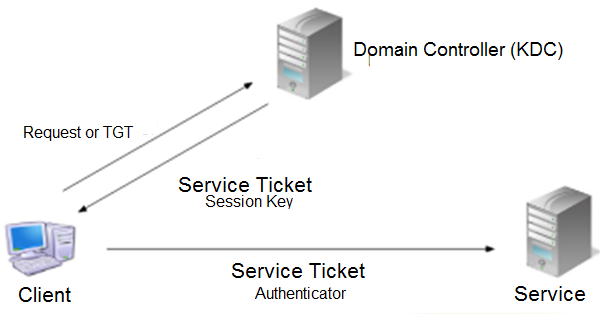
The following figure illustrates how Kerberos authentication works. The client, here, the VOS device, authenticates itself using the authentication server, and the authentication server forwards the username to the key distribution center (KDC). The KDC issues a ticket-granting ticket (TGT), which includes a timestamp, encrypts the TGT using the ticket-granting service (TGS) secret key, and returns the encrypted TGT to the user. The user verifies the validity of the TGT and is then granted access to the requested service. The TGS issues a service ticket and a session key to the client. The client then sends the service ticket, along with its service request, to the service server.
To configure Kerberos authentication, you do the following:
- Generate and upload the keytab file.
- Configure a Kerberos profile.
- Configure an authentication profile for Kerberos.
- Create an authentication rule for Kerberos.
- Configure captive portal.
- Configure a decryption profile with full proxy (transparent or explicit proxy).
- Configure a decryption rule.
- Configure secure web proxy (transparent or explicit proxy)
- Configure browser settings for Kerberos.
Configure Kerberos Keytabs
To use Kerberos, you generate a keytab file and then upload it to one or more VOS devices. You use the Kerberos keytab file to authenticate systems and services that use Kerberos without having to enter a password.
Note that because the keytabs are derived from the Kerberos password, if you change the Kerberos password, you must re-create all keytabs and import the keytab files to the device again.
Generate a Keytab File on an Active Directory Server
- Create a domain user on the Active Directory (AD) server:
- On the Active Directory server, log in to Windows PowerShell (command-line shell) and generate the keytab file.
ktpass.exe -princ spn L -mapuser username -mapOp set -pass password -crypto all -ptype KRB5_NT_PRINCIPAL -out filename.keytab
In this command:
- princ HTTP/john.versaqa999.local@VERSAQA999.LOCAL—Enter the service principal name, in the format of user@realm.
- mapuser username—Enter the username.
- –pass password—Enter the user password.
- –out filename.keytab—Enter the name of the file in which to save the keytabs.
For example:
ktpass.exe -princ HTTP/john.versaqa999.local@VERSAQA999.LOCAL -mapuser john -mapOp set -pass Versa@123 -crypto all -ptype KRB5_NT_PRINCIPAL -out Sample.keytab
Use a Keytab File on Multiple Devices
To use the same keytab file on multiple VOS devices and to configure different virtual URLs in captive portal, you must configure multiple service principal names (SPN) in the user account. The user account is the domain user account that is used to generate the keytab file.
Note: Use this procedure only if you are configuring the same keytab file on multiple devices.
To configure multiple SPNs:
- Log in to Windows PowerShell.
- Configure the SPN directory property for the AD service account:
setspn.exe -S HTTP/spn-name username setspn.exe -S HTTP/spn-name2 username
For example:PS C:\Users\Administrator.WINSERVER> setspn -S HTTP/br1.versaqa999.local john Checking domain DC=spn999,DC=local Registering ServicePrincipalNames for CN=john,CN=Users,DC=versaqa999,DC=local HTTP/br1.versaqa999.local Updated object PS C:\Users\Administrator.WINSERVER> setspn -S HTTP/br2.versaqa999.local john Checking domain DC=versaqa999,DC=local Registering ServicePrincipalNames for CN=john,CN=Users,DC=versaqa999,DC=local HTTP/br2.versaqa999.local Updated object - Verify the SPN by issuing the setspn –l username command. For example:
PS C:\Users\Administrator.WINSERVER> setspn -l john Registered ServicePrincipalNames for CN=john,CN=Users,DC=versaqa999,DC=local: HTTP/br2.versaqa999.local HTTP/br1.versaqa999.local HTTP/john.versaqa999.local
Upload the Kerberos Keytab File
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors
 > Connectors
> Connectors > Users/Groups
> Kerberos Keytab
in the left menu bar.
- Select the Director tab, and then click the
 Upload icon to upload the keytab file to the Director node. The Upload Kerberos Keytab Files to Director popup window displays.
Upload icon to upload the keytab file to the Director node. The Upload Kerberos Keytab Files to Director popup window displays.
- In the Filename field, enter the name of the keytab file, or click the Browse button and then select the file.
- Click OK to upload the keytab file to the Director node.
- Select the Appliance tab, and then click the
 Upload icon to upload the Kerberos keytab file to a VOS device. The Upload Kerberos Keytab Files to Appliance popup window displays.
Upload icon to upload the Kerberos keytab file to a VOS device. The Upload Kerberos Keytab Files to Appliance popup window displays.
- In the Filename field, select the Kerberos keytab file. The Appliance field is populated by default.
- Click OK.
Configure a Kerberos Profile
To define a Kerberos profile for authenticating a user and group:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors
 > Connectors > Users/Groups
> Connectors > Users/Groups > Kerberos Profile
in the left menu bar
- Click the
 Add icon. In Add Kerberos Profile popup window, enter information for the following fields.
Add icon. In Add Kerberos Profile popup window, enter information for the following fields.
Field Description Name Enter a name for the Kerberos profile. Description Enter a text description for the Kerberos profile. Tags Enter a keyword or phrase that allows you to filter the Kerberos profile. This is useful when you have many profiles and want to view those that are tagged with a particular keyword. Keytab File Select the keytab file that you uploaded in Upload the Kerberos Keytab File, above. SPN Enter the value for the service principal name.
- Click OK.
Configure a Kerberos Authentication Profile and Rule
To define a Kerberos authentication profile that is used in the user and group authentication policy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects and Connectors
 > Connectors > Users/Groups
> Connectors > Users/Groups > Authentication Profiles in the left menu bar.
- Click the
 Add icon. The Add Authentication Profile popup window displays.
Add icon. The Add Authentication Profile popup window displays. - In the Kerberos Profile field, select the Kerberos profile you configured in Configure a Kerberos Profile. For information about the other fields in the popup window, see Configure an Authentication Profile.
- Click OK.
Configure an Authentication Policy Rule To Bypass DNS Traffic
If you are using DNS server on the internet side, you configure an authentication policy rule to bypass DNS traffic.
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services
 > Next Gen Firewall > Authentication > Policies in the left menu bar.
> Next Gen Firewall > Authentication > Policies in the left menu bar. - Select Rules tab and click the
 Add icon to add a new authentication policy.
Add icon to add a new authentication policy. - Select the Header/Schedule tab, and in the Services table, select DNS.
- Select the Enforce tab.
- Select Do not Authenticate to bypass DNS traffic. Configure other fields in the popup window, as needed. For more information, see Configure Rules for Authentication Policies.
- Click OK.
Associate an Authentication Profile with an Authentication Policy Rule
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services
 > Next Gen Firewall > Authentication > Policies.
> Next Gen Firewall > Authentication > Policies. - Select Rules tab and click the
 Add icon in the dashboard to add a new authentication policy.
Add icon in the dashboard to add a new authentication policy. - Select the Enforce tab. In the Action group of fields, select Authenticate Using Profile and then select the Kerberos profile you configured in Configure a Kerberos Profile.
- Configure other fields in the popup window, as needed. For more information, see Configure Rules for Authentication Policies.
- Click OK.
Create a Private Key for a CA Certificate
On a VOS device, a key is required to access secured traffic using a certificate. To secure the traffic on a VOS device, you can use either a self-signed CA certificate or a trusted CA certificate.
To create a key for a CA certificate:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors
> Objects
> Custom Objects
> Keys
in the left menu bar.
- Select the Appliance tab and click the
Add icon. In the Generate Key on Appliance popup window, enter information for the following fields. For more information, see Create a CA Certificate Key.
- Click OK.
Create a CA Certificate
To create a certificate on a VOS device and associate it with a certificate key:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors
> Objects
> Custom Objects
> Certificates
in the left menu bar.
- Select the Appliance tab and click the
Add icon. In the Generate Certificate on Appliance popup window, enter information for the following fields. For more information, see Create a Certificate on a VOS Device.

- Click OK.
Configure Transparent Proxy for Kerberos
- Configure a decryption profile in transparent mode:
- In Appliance view, select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services
> Next Gen Firewall
> Decryption
> Profiles
in the left menu bar.
- Click the
 Add icon. The Add Decryption Profile popup window displays. For more information, see Configure an SSL Decryption Profile.
Add icon. The Add Decryption Profile popup window displays. For more information, see Configure an SSL Decryption Profile.
- In the Decryption Type field, select SSL Full Proxy.
- Select Transparent.
- Click OK.
- Associate the transparent decryption profile with a decryption policy rule:
- Select Services
> Next Gen Firewall
> Decryption
> Policies
in the left menu bar.
- Select the Rules tab and click the
 Add icon. The Add Decryption Rule popup window displays.
Add icon. The Add Decryption Rule popup window displays. - Select the Enforce tab. In the Action field, select decrypt, and in the Decryption Profile field select the decryption profile you configured in Step 1. For more information, see Configure an SSL Decryption Policy Rule.
- Click OK.
- Select Services
- Configure a transparent secure web proxy:
- In Appliance view, select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services
> Web Proxy
in the left menu bar. The Add HTTP/HTTPS Proxy window displays.
- Select Transparent from the Mode drop-down list and enter other details. For more information, see Configure a Transparent Proxy.
- Enter the port number.
- Click OK.
- Configure a transparent captive portal:
- In Appliance view, select the Configuration tab in the top menu bar.
- Select Services
> Next Gen Firewall
> Security Settings
> Captive Portal
in the left menu bar. The dashboard displays the Captive Portal Settings pane.
- Click the
Edit icon. The Edit Captive Portal Settings popup window displays. For more information, see Modify Captive Portal Settings.
- Select the General tab, and enter information for the following fields:
- In the SSL CA Certificate field, select the CA certificate.
- In the SSL Port field, enter the SSL port number (here, port 44991).
- In the Routing Instance table, select the routing instance.
- Select the Authentication tab, and in the Kerberos Virtual URL field, enter the Kerberos virtual URL. Note that you must resolve the virtual URL with the appliance LAN IP address.
- Click OK.
Configure Kerberos Setting in Client Browser for Transparent Proxy
A transparent proxy processes SSL/TLS traffic that is destined to any IP address but to a particular port. The client (browser) performs DNS resolution and opens the connection to the server's IP address. For more information, see Enable Kerberos Settings in Browsers below.
Configure an Explicit Proxy for Kerberos
An explicit proxy processes SSL/TLS traffic destined to a specific IP address and a port.
- Configure a decryption profile in explicit mode:
- In Appliance view, select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services
> Next Gen Firewall
> Decryption
> Profiles
in the left menu bar.
- Click the
Add icon. The Add Decryption Profile popup window displays. For more information, see Configure an SSL Decryption Profile.
- In the Decryption Type field, select SSL Full Proxy.
- Select Explicit.
- Enter IP address and port number of the proxy, and select the routing instance to use to reach the proxy.
- Click OK.
- Associate the explicit decryption profile with a decryption policy rule:
- Select Services
> Next Gen Firewall
> Decryption
> Policies
in the left menu bar.
- Select the Rules tab and click the
Add ico. The Add Decryption Rule popup window displays.
- Select the Enforce tab. In the Action field, select Decrypt, and in the Decryption Profile field, select the decryption profile you configured in Step 1. For more information, see Configure an SSL Decryption Policy Rule.
- Select Services
- Configure an explicit secure web proxy:
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services
> Web Proxy in the left menu bar. The Add HTTP/HTTPS Proxy window displays.
- In the Mode field, select Explicit, and enter information for other fields. For more information, see Configure an Explicit Proxy.
- Click OK.
- Configure an explicit captive portal:
- In Appliance view, select the Configuration tab in the top menu bar.
- Select Services
> Next Gen Firewall
> Security Settings
> Captive Portal
in the left menu bar. The dashboard displays the Captive Portal Settings pane.
- Click the
Edit icon. The Edit Captive Portal Settings popup window displays. For more information, see Modify Captive Portal Settings.
- Select the General tab, and enter information for the following fields:
- In the SSL CA Certification field, select the CA certificate.
- In the SSL Port field, enter the port number for the captive portal.
- In the Routing Instance table, select the routing instance to use to reach the captive portal.
- Click OK.
Configure Kerberos Setting in Client Browser for Explicit Proxy
An explicit proxy processes SSL/TLS traffic destined to a specific IP address and a specific port. On the browser client, you configure the proxy IP address and the port. For more information, see Enable Kerberos Settings in Browsers below.
Enable Kerberos Settings in Browsers
As part of the configuring Kerberos authentication, you must enable Kerberos settings in browsers for transparent and explicit web proxy. This article describes the settings to enable Kerberos for Internet Explorer (IE) and Mozilla Firefox. The settings for IE are applicable for Google Chrome as well.
Enable Kerberos in Internet Explorer for Transparent Proxy
- Open an IE browser window.
- Click the Settings icon in the upper-right corner, or click the Tools menu.
- Select Internet Options, and select the Security tab.
- Select Internet, and click Custom Level. The Security Setting dialog box displays.
- In User Authentication > Log On, click Automatic Log-On with Current Username and Password.
- Select Security tab again, and select Local Intranet and repeat Steps 4 and 5.
- Under Local Intranet, select Sites. The Local Intranet dialog box displays.
- Click Advanced, and in the Websites field, enter the virtual URL that you configured in Step 3 of Configure Transparent Proxy for Kerberos above.
- Click Close.
- Click OK.
Enable Kerberos in Internet Explorer for Explicit Proxy
- Perform Steps 1 through 10 in Enable Kerberos in Internet Explorer for Transparent Proxy above.
- In Internet Options, select the Connections tab.
- Click LAN Settings. The Local Area Network (LAN) Settings dialog box displays.
- Click Use a Proxy Server for Your LAN.
- In the Address field, enter the virtual URL that you configured in Step 3 of Configure Transparent Proxy for Kerberos above.
- In the Port field, enter the proxy port number.
- Click OK.
Enable Kerberos in Firefox for Transparent Proxy
- Open a Firefox browser window, type about:config in the address bar, and press Enter.
- Click Accept the Risk and Continue.
- In the search bar, enter the string "negotiate", and press Enter.
- Select network.negotiate-auth.trusted-uris, and enter the domain name.
Enable Kerberos in Firefox for Explicit Proxy
- Perform Steps 1 through 4 in Enable Kerberos in Firefox for Transparent Proxy above.
- In the main menu, select Options.
- Navigate to General > Network Setting and click Settings. The Connection Settings dialog box displays.
- In Configure Proxy Access to the Internet, select Manual Proxy Configurationn.
- In the HTTP and HTTPS Proxy fields, enter the virtual URL that you configured in Step 3 of Configure Transparent Proxy for Kerberos above.
- Click OK.
Match Authenticated Users
To configure match criteria for the specific user authenticated by Kerberos in a CoS (QoS), NGFW, SD-WAN, or UTM policy rule, see Add External Database Users in Configure User and Group Policy.
View Active Users
To view currently active users:
- Import the SSL CA certificate to the browser.
- Log in using the domain user name in the domain client system and browse the internet. User login is automatic in a device with the domain username.
- Verify the list of active users by issuing the show orgs org-services organization-name user-identification live-users list detail CLI command.
For example:admin@BR1-cli> show orgs org-services ORG1 user-identification live-users list detail TIME SESSION TO EXPIRATION SEQUENCE INFORMATION INTERNAL IP ADDRESS NAME STATUS HITS EXPIRY MODE NUMBER SOURCE AUTHENTICATION PROFILE ID INTERNAL GROUP ID TIME STAMP ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 192.168.10.254 user1@versaqa999.local Live 72 119 inactivity - n/a Test-Kerberos-Auth-Profile - [ 1048 ] 2020-11-06 11:16:24
Monitor Kerberos User Identification Statistics
To view the reports for Kerberos authentication profiles (in this case, Kerberos authentication profile) associated with a user ID, you monitor user identification statistics. For more information, see Monitor Device Services.
To monitor active user statistics:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select the Provider Organization > Services tab.
- Select NGFW
> User Identification, and select Live Users from the drop-down list. The user ID statistics displays.
Display Kerberos Authentication Logs
To display the authentication events logs for a Kerberos authentication profile:
- In Director view, select the Analytics tab from the top menu bar. The view changes to Analytics view.
- Select Home
> Logs > Authentication in the left menu bar to view the authentication logs.
- Select the Events tab to display information about the authentication logs.
Supported Software Information
Releases 20.2 and later support all content described in this article.
