Configure HTTP/HTTPS Proxy
![]() For supported software information, click here.
For supported software information, click here.
Versa Operating SystemTM (VOSTM) devices inspect HTTPS traffic without decrypting the connections. While the HTTP content of an HTTPS session is encrypted, the SSL certificate is transmitted without encryption. You can configure VOS devices to inspect the various attributes of the SSL certificate and enforce policy based on the inspection.
Note that the VOS software does not support decryption of the QUIC protocol. For the VOS security software modules to work, you must block QUIC traffic.
Configure SSL Inspection and Decryption
For SSL inspection, you configure a decryption policy, which includes one or more rules, and you configure one or more decryption profiles. You associate a decryption profile with a decryption policy, and in this way the profile is applied to traffic that matches a rule in the decryption policy. You can configure one or more decryption profiles for each tenant.
As an example of a decryption policy, you can apply a decryption profile that enforces decrypt and do not decrypt actions, as illustrated in the following figure.

To define traffic decryption for security policies on VOS devices, you configure a decryption policy on the VOS device. In the decryption policy, you specify the URL categories for the traffic that you want to decrypt. Currently, VOS devices support only HTTPS.
Normally, encrypted traffic is not blocked, and it is shaped according to the security settings. Decryption enforces security policies on encrypted traffic to help prevent malicious content from entering the network and to protect sensitive data disguised as encrypted traffic from leaving the network.
You can configure a decryption profile that contains SSL inspection and policy enforcement information.
Applying a decryption policy requires a certificate.
You can configure the policy action for SSL certificates based on the following:
- Restricted certificate extensions
- Sites with expired SSL certificates
- Sites with untrusted issuers
- Unsupported ciphers
- Unsupported key lengths
- Unsupported versions
You can configure the following policy actions to apply to the inspection results:
- Alert
- Allow
- Drop packet
- Drop session
- Reject
To configure SSL inspection and decryption, you do the following:
- Create a CA certificate key.
- Create a certificate on a VOS device.
- Configure an SSL decryption and inspection profile.
- Configure an SSL decryption policy.
- Configure an SSL decryption policy rule.
- Upload a trusted CA database.
- Upload a CA certificate.
You can also export a CA certificate to a file.
Create a CA Certificate Key
On a VOS device, a key is required to access secured traffic using a certificate. To secure the traffic on a VOS device, you can use either a self-signed CA certificate or a trusted CA certificate.
To create a key for a CA certificate:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors > Objects > Custom Objects > Keys in the left menu bar.

- Select the Appliance tab, and then click the
 Add icon in the main pane. In the Generate Key on Appliance popup window, enter information for the following fields.
Add icon in the main pane. In the Generate Key on Appliance popup window, enter information for the following fields.

Field Description Name Enter a name for the certificate key. Type Select the encryption type to use to securely encode and decode the information:
- ECDSA
- RSA
Size Select the RSA key size:
- 2048 bits
- 4096 bits
Pass Phrase Enter the pass-phrase key, or password, to use to encrypt the file that contains the RSA key. - Click OK.
Create a Certificate on a VOS Device
To create a certificate on a VOS device and associate it with a certificate key:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors > Objects > Custom Objects > Certificates in the left menu bar.

- Select the Appliance tab, and then click the
 Add icon in the main pane. In the Generate Certificate on Appliance popup window, enter information for the following fields.
Add icon in the main pane. In the Generate Certificate on Appliance popup window, enter information for the following fields.

Field Description Certificate Name Enter a name for the certificate. Validity Enter how long the certificate is valid, in days
Default: 365 daysCertificate Attributes (Group of Fields) Configure properties of the certificate. - CA Certificate
Click true to have the certificate be a trusted CA certificate. - Serial Number
Enter the serial number of the certificate. - Signature Algorithm
Select the signature algorithm to use with the certificate:
- SHA-1
- SHA-256
- SHA-384
- Common Name
Enter a common name for the certificate. - Email ID
Enter the email address to which to send the certificate. - Country Name
Enter the country where the VOS device is located. - State or Province
Enter the state or province where the VOS device is located. - Locality
Enter additional information about the location of the VOS device. - Organization
Enter the name of the organization or entity to which the VOS device belongs. - Organization Unit
Enter the name of the organizational unit to which the VOS belongs. Private Key Name Select the name of the key to associate with the certificate. + Private Key Click to add a private key. - Click OK.
Configure an SSL Decryption Profile
To decrypt or inspect traffic properties, you create an SSL decryption profile and then associate it with a decryption policy rule. The decryption profile is applied to traffic that matches the decryption rule.
To configure an SSL decryption profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Next-Gen Firewall > Decryption > Proxy Profiles in the left menu bar.

- Click the
 Add icon. The Add Decryption Profile popup window displays. For Releases 22.1.1 and later, the Add Decryption Profile window has four tabs, for Releases 21.2, the Add Decryption Profile window has three tabs, and for earlier releases, it is a single window.
Add icon. The Add Decryption Profile popup window displays. For Releases 22.1.1 and later, the Add Decryption Profile window has four tabs, for Releases 21.2, the Add Decryption Profile window has three tabs, and for earlier releases, it is a single window. - Select the General tab, and then enter information for the following fields.

Field Description Name Enter a name for the decryption profile. Description Enter a text description for the decryption profile. Tags Enter a keyword or phrase that allows you to filter the profile name. Tags are useful when you have many profiles and want to view particular ones. Enable Profile Click to enable the decryption profile. Support Session Ticket Click to enable a session that was created earlier. Use Extended Master Secret Click to use the TLS extended master secret extension. This TLS option helps prevent man-in-the-middle attacks. Type Select the decryption type to use with the profile, either SSL Forward Proxy or SSL Full Proxy.
- SSL Forward Proxy
SSL forward proxy is a transparent proxy that can decrypt and encrypt the SSL/TLS traffic between the client and the server. With a transparent proxy, neither the client nor the server knows about the proxy’s presence. Rather, the proxy acts as a server towards the client and as a client towards the server.
Whether to decrypt can be controlled through the decryption policy. When the client initiates an SSL/TLS handshake towards the server, the proxy applies the decryption policy to determine whether the traffic needs to be decrypted. If the policy action is to decrypt, the proxy uses the matching SSL profile to initiate the SSL handshake towards the server, and the policy inspects the server certificate and other SSL attributes from the SSL handshake stream. If the inspection is successful, the proxy completes the SSL handshake with the server and generates a server certificate signed with the public key specified in the SSL proxy profile, and it resumes the SSL handshake towards the client. After the SSL handshake between the client and the proxy completes, the proxy is able to decrypt application traffic sent by the client. After the traffic is decrypted, it can be examined by the other services in the firewall service chain before before it is encrypted and sent to the server.
When you select SSL Forward Proxy mode, the Start TLS fields display. Choose one or more of the following options:
- IMAP
- POP3
- SMTP

- SSL Full Proxy
When you select SSL Full Proxy mode, the Mode field display. Click to select the proxy mode:
- Explicit
- Transparent

Explicit mode processes SSL/TLS traffic destined to a specific IP address and a specific port. On the client, you configure the proxy IP address and the port. The explicit SSL full proxy works as follows:
- The client connects to the configured proxy IP address and port and sends an HTTP Connect request.
- The SSL full proxy parses the HTTP Connect request and extracts the domain that the client wants to connect to. The proxy uses the domain and other Layer 3 and Layer 4 parameters to locate a decryption policy. If the proxy finds a decryption policy, it decrypts or bypasses the SSL connection based on the action in the policy. If there is no policy, decryption is bypassed.
- The SSL full proxy responds with a 200 OK message. When the proxy receives a client Hello message, if the policy decision was to decrypt, the SSL proxy responds with a server Hello message and the remainder of the handshake message between the client and the proxy is exchanged.
- After the handshake completes, the client does a GET or a POST on the connection.
- The proxy parses the HTTP request and extracts the domain name and port from the URL. The proxy then performs a DNS resolution of that domain and opens a connection towards the resolved IP address using the source IP address and port from the configured SNAT pool referenced in the HTTP proxy profile.
- When the connection is successful, the proxy initiates the SSL handshake with the server and then forwards the HTTP request to the server.
- All the other services in the service chain, such as PS/IDS and antivirus, examine the decrypted stream to look for any threats, and they may drop the packet based on the outcome of their examination.
Transparent mode processes SSL/TLS traffic destined to any IP address but to a specific port. The transparent process works the same was as the explicit process, except for the DNS resolution process. Because the destination IP address is the actual address of the server, the proxy skips DNS resolution, DNS resolution is done on the client, and the client opens the connection to the server IP address. The proxy uses the SNAT pool configured in the HTTPS proxy profile to perform source NATing.
In the Match Rule table, select the rule containing the match conditions. To add a match condition rule, click the + Add icon. In the Add Match Rule popup window, enter information for the following fields.
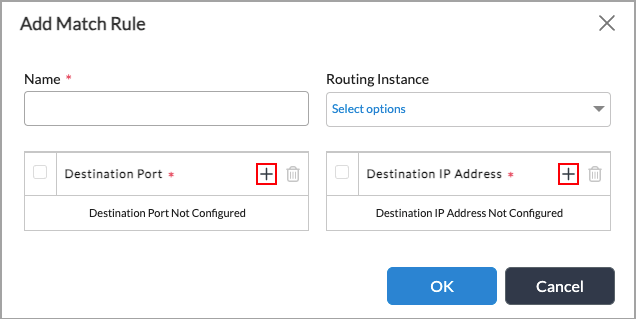
- Name—Enter a name for the match rule.
- Routing Instance—Select the routing instance in which to apply the rule.
- Destination Port—Click the + Add icon, and enter the destination port to match.
- Destination IP Prefix—Click the + Add icon, and enter the destination IP prefix to match.
Trusted Certificate Database Select the trusted certificate database to use to verify and confirm the authority of the server certificate. CA Certificate Select the certificate authority (CA) that issues the decryption server certificate. A CA is an entity that issues digital certificates to verify the ownership of a public key.
LEF Profile Select a log export functionality (LEF) profile to use to capture SSL logs for the decryption profile. For information, see Configure Log Export Functionality. - Default Profile
Click to use the default LEF profile instead of the LEF profile selected in the previous field. - LEF Log Level
If you select Default Profile, select the LEF log level. - Select the SSL Inspection tab, and then enter information for the following fields. For Releases 21.2.1 and earlier, these fields are on the main Add Decryption Profile popup window.

Field Description OCSP (Group of Fields) For Releases 21.2.1 and later. - Enabled
Click to enable server certificate verification using the Online Certificate Status Protocol (OCSP). - Block Unknown Certificate
Click to block SSL sessions whose certificate status is unknown. - Response Timeout
Enter the timeout for an OCSP request.
Default: 5 seconds
Value: 0 through 255 seconds
Verify Select the type of verification:
- Client
- Server
- Server and Client
CRL Check Click to enable checking of the certificate revocation list (CRL). If enabled, the received server certificates are matched against the CRL. For more information, see Upload CRL Files. Fetch Issuer Using AIA Issuers (For Releases 22.1.2 and later.) Click to fetch intermediate certificates from the issuing certification authority. Authority Information Access (AIA) is an SSL certificate extension that contains information about the issuer of the certificate. If a server does not provide intermediate certificates, the certificates can be downloaded from the link contained in the AIA field.
For this option to work, you must select a pool in the SNAT Pool field or you must click SNAT Pool Default.
Server Certificate Checks (Group of Fields) - Action for Expired Certificate
Select the predefined or user-defined action to take when the server certificate expires. The following are the predefined actions:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Action for Untrusted Issuers
Select the predefined or user-defined action to imply when the certificate is from an untrusted issuer. The following are the predefined actions:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Restrict Certificate Extension
Click to restrict certificate extensions.
Unsupported Mode Checks (Group of Fields)
- Action for Unsupported Cipher
Select the predefined or user-defined action to take when the decryption encounters an unsupported cipher:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Minimum Supported Key Length
Enter the minimum RSA key length, in bits.
Default: 512 bits- Action for Unsupported Key Length
Select the action to take when the decryption encounters an unsupported key length:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Action for Unsupported Version
Select the action to take when the decryption encounters an unsupported CA version:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
SNAT Pool Select an SNAT pool. SNAT Pool Default Click to have the selected SNAT pool be the default pool. + SNAT Pool Click to create a new SNAT pool. For more information, see Configure SNAT Pools. - (For Releases 21.2.1 and later.) Select the SSL Protocol tab, and enter information for the following fields. Note that if you do not select key exchange, encryption, and authentication algorithms, all algorithm are considered to be enabled for the selected cipher suites.

Field Description Minimum Version Select the minimum version of Transport Layer Security (TLS) that is supported. The minimum version must be the same as or earlier than the maximum version.
- TLS 1.0
- TLS 1.1
- TLS 1.2
- TLS 1.3
Maximum Version Select the maximum version of TLS that is supported. The maximum version must be the same as or later than the minimum version. The options displayed depend on the version you select in the Minimum Version field. For example, if the minimum version is are TLS 1.0, the options TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3 are displayed. If the minimum version is TLS 1.2, the options TLS 1.2 and TLS 1.3 are displayed.
Key Exchange Algorithms When you select minimum and maximum TLS versions and the version is not TLS 1.3, select one or more key exchange algorithms for the SSL connection:
- ECDHE—Elliptic-curve Diffie–Hellman Key Exchange
- RSA—Rivest–Shamir–Adleman algorithm
Encryption Algorithms Select an encryption algorithm to use:
- AES-128-CBC—AES CBC encryption algorithm with 128-bit key
- AES-128-GCM—AES GCM encryption algorithm with 128-bit key
- AES-256-CBC—AES CBC encryption algorithm with 256-bit key
- AES-256-GCM—AES GCM encryption algorithm with 256-bit key
- Camellia-256-CBC—Camellia encryption algorithm with 256-bit key
- Chacha20-Poly1305—ChaCha stream cipher and Poly1305 authenticator
- Seed CBC—TLS RSA with seed CBC
Authentication Algorithms Click to have the selected LEF profile be the default LEF profile. Cipher Suites Select a TLS cipher suite. If you select a cipher suite, it must be consistent with the selected key exchange, encryption, and authentication algorithms. If you do not configure cipher suites, all cipher suites matching the selected the key exchange, encryption, and authentication algorithms are selected by default.
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SH
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA25
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA384
- TLS-ECDHE-ECDSA-WITH-AES-256-GCM-SHA384
- TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256
- TLS-ECDHE-RSA-WlTH-AES-128-CBC-SHA
- TLS-ECDHE-RSA-WlTH-AES-128-CBC-SHA25
- TLS-ECDHE-RSA-WlTH-AES-128-GCM-SHA256
- TLS-ECDHE-RSA-WlTH-AES-256-CBC-SHA
- TLS-ECDHE-RSA-WlTH-AES-256-CBC-SHA384
- TLS-ECDHE-RSA-WlTH-AES-256-GCM-SHA384
- TLS-ECDHE-RSA-WlTH-CHACHA20 POLY1305-SHA256
- TLS-RSA-WlTH-AES-128-CBC-SH
- TLS-RSA-WITH-AES-128-CBC-SHA256
- TLS-RSA-WlTH-AES-128-GCM-SHA256
- TLS-RSA-WlTH-AES-256-CBC-SHA
- TLS-RSA-WlTH-AES-256-CBC-SHA256
- TLS-RSA-WlTH-AES-256-GCM-SHA384
- TLS-RSA-WITH-CAMELLIA-256-CBC-SHA
- TLS-RSA-WITH-SEED-CBC-SHA
- (For Releases 22.1.2 and later). Select the Advanced tab. The following screen displays.

-
Enter information for the following fields.
Field Description HTTP Header Profile Select an HTTP header profile or click + Add New to create a new HTTP header profile. For more information, see Configure HTTP Header Profiles.
Client Authentication (Group of Fields) - Trusted Certificate Database for Client Certificate
Select the trusted certificate database to use to verify and confirm the authority of the server certificate. - Delegate Client Certificate
Select a delegate client certificate. - Certificate Info Header Profile (Group of Fields)
Configure a profile for the certificate information header. - Header
Enter a name for the header profile. - Value
Select a value:
- Common Name
- Issuer Distinguished Name
- Subject Distinguished Name
- Validity Not After
- Validity Not Before
- Name Option
If you select the values Issuer Distinguished Name or Subject Distinguished Name, enter a name for the header value. - Click OK.
Configure an SSL Decryption Policy
You configure an SSL decryption policy to specify traffic that you want to decrypt.
To configure an SSL decryption policy:
- In Director view:
- Select the Administration tab in the top menubar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Next-Gen Firewall > Decryption > Policies in the left menu bar.
- Select the Decryption Policies tab and then click the
 Add icon in the main pane. In the Add Decryption Policy popup window, enter information for the following fields.
Add icon in the main pane. In the Add Decryption Policy popup window, enter information for the following fields.
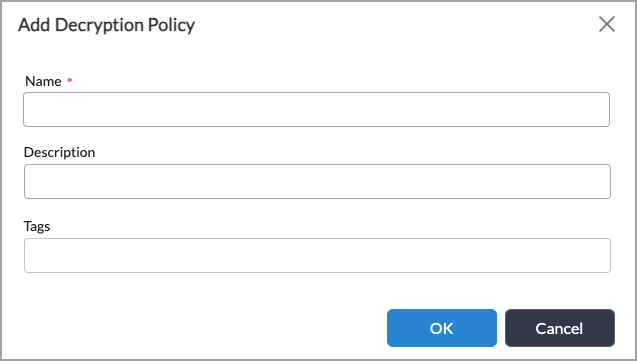
Field Description Name Enter a name for the decryption policy. Description Enter a text description for the decryption policy. Tags Enter a keyword or phrase that allows you to filter the policy name. Tags are useful when you have many policies and want to view those that are tagged with a particular keyword. - Click OK.
Configure an SSL Decryption Policy Rule
In an SSL decryption policy rule, you define the traffic of interest, and for matching traffic you define whether to decrypt the traffic, inspect the traffic, or both decrypt and inspect it.
When you configure SSL decryption for a tenant, the VOS device behaves as an SSL proxy, and it generates a TLS/SSL certificate for each HTTPS URL that the tenant tries to access (for example, https://example.com). The certificate allows the VOS device to inspect the data flow and take any necessary actions. To optimize the SSL proxy behavior, the VOS device uses the same generated public–private key pair for certificates issued across domains. This key pair is generated for each configured decryption profile, and hence is unique for each tenant.
To create the policy rule:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Next-Gen Firewall > Decryption > Policies in the left menu bar.

- Select the Rules tab and click the
 Add icon in the main pane. The Add Decryption Rule popup window displays.
Add icon in the main pane. The Add Decryption Rule popup window displays. - (For Releases 21.2.1 and later.) If you have already added one or more rules, the Configure Rule Order popup window displays.
- Select where you want to insert the policy rule, either at the beginning or end of the existing rules.

- If you select a rule and then click the Add icon, the Configure Rule Order popup window displays the following options:

- Select the order to insert the rule (at the beginning or end bottom of the existing rules, or before or after the selected rule).
- Click OK. The Add Decryption Rule popup window displays.
- Select where you want to insert the policy rule, either at the beginning or end of the existing rules.
- In the Add Decryption Rule screen, select the General tab and then enter information for the following fields.

Field Description Name Enter a name for the decryption policy rule Description Enter a text description for the decryption policy rule. Tags Enter a keyword or phrase that allows you to filter the rule name. This is useful when you have many rules and want to view those that are tagged with a particular keyword. Disable Rule Click to disable the decryption rule. - Select the Source tab to define the source zone and the source address of the incoming (source) traffic to which the decryption policy rule applies. Enter information for the following fields.

Note that in Releases 21.2 and earlier, the Source and Destination information was on the same tab.Field Description Source Zone Select the source zone to which to apply the rule to traffic coming from any interface in the specified zone. Click the
 Add icon to add more security zones.
Add icon to add more security zones.Source Address Select one or more source addresses to which to apply the decryption policy rule. Click the
 Add icon to add more source addresses.
Add icon to add more source addresses.Custom Geographic Circle (For Releases 22.1.2 and later.) Click the  Add icon, and then select a custom geographic circle. A geographic circle consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. To configure a custom geographic circle, see Configure Custom Geographic Circles.
Add icon, and then select a custom geographic circle. A geographic circle consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. To configure a custom geographic circle, see Configure Custom Geographic Circles.Region (For Releases 22.1.2 and later.) Click the  Add icon, and then select a region. To create a region, see Create a Region.
Add icon, and then select a region. To create a region, see Create a Region.EIP Profiles (For Releases 22.1.2 and later.) Click the  Add icon, and then select an endpoint information profile (EIP). To configure an EIP, click + Add EIP Profile. For more information, see Configure EIP Profiles.
Add icon, and then select an endpoint information profile (EIP). To configure an EIP, click + Add EIP Profile. For more information, see Configure EIP Profiles.State (For Releases 22.1.2 and later.) Click the  Add icon, and then select a state.
Add icon, and then select a state.City (For Releases 22.1.2 and later.) Click the  Add icon, and then select a city.
Add icon, and then select a city.Source Address Negate Click to select any source addresses except the configured source addresses. Source Location Negate Click to select any source locations except the configured source locations.
- Select the Destination tab to define the destination zone and the destination address ;of the outgoing (destination) traffic to which the decryption policy rule applies. Enter information for the following fields.

Field Description Destination Zone Select the destination zone to which to apply the decryption policy to traffic coming from all interfaces into a given zone. Click the
 Add icon to add more security zones.
Add icon to add more security zones.Destination Address Select one or more destination addresses to which to apply the decryption policy rule. Click the
 Add icon to add more destination addresses.
Add icon to add more destination addresses.Note that for an explicit proxy, the destination address is the address on which the explicit proxy is configured. This means that configuring destination addresses for an explicit proxy is not effective.
Custom Geographic Circle (For Releases 22.1.2 and later.) Click the  Add icon, and then select a custom geographic circle. ;A geographic circle consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. To configure a custom geographic circle, see Configure Custom Geographic Circles.
Add icon, and then select a custom geographic circle. ;A geographic circle consists of a point and the area enclosed by a circle drawn around that point. You specify the point by its latitude and longitude coordinates, and you specify the size of the circle by a distance. To configure a custom geographic circle, see Configure Custom Geographic Circles.Region (For Releases 22.1.2 and later.) Click the  Add icon, and then select a region. To create a region, see Create a Region.
Add icon, and then select a region. To create a region, see Create a Region.State (For Releases 22.1.2 and later.) Click the  Add icon, and then select a state.
Add icon, and then select a state.City (For Releases 22.1.2 and later.) Click the  Add icon, and then select a city.
Add icon, and then select a city.Destination Address Negate Click to select any destination addresses except the configured destination addresses.
Note that for an explicit proxy, the destination address is the address on which the explicit proxy is configured. This means that configuring destination addresses for an explicit proxy is not effective.
Destination Location Negate Click to select any destination locations except the configured destination locations. - Select the Header/Schedule tab to define the IP header, services and schedule to which the decryption rule applies. Enter information for the following fields.

Field Description IP Version Enter the IP version for which the decryption rule applies. IP Flag For IPv4, select how to fragment packets:
- Don’t Fragment
- More Fragment
DSCP Enter a differentiated service code point (DSCP) value to classify an IP packet is queued for forwarding. TTL (Group of Fields) - Condition
Select the TTL condition to use for the match. The TTL is the number of hops that a packet can travel before it is discarded and indicates the lifespan of a packet. The condition can be one of the following boolean values:
- Greater than or equal to—TTL value must be greater than or equal to the specified value to trigger the security access rule
- Less than or equal to—TTL value must be less than or equal to the specified value to trigger the security access rule
- Equal to—TTL value must be equal to the specified value to trigger the security access rule
- Value (Max 255)
Enter the value for the TTL.
Range: 1 through 255
Default: None
Others (Group of Fields) - Schedules
Select a schedule to set the time and frequency at which the rule is in effect. - + Schedule
Click to create a schedule. Services (Group of Fields) - Service List
Click the  Add icon to select one or more services to apply the decryption rule to the configured services.
Add icon to select one or more services to apply the decryption rule to the configured services.- + Service
Click to create a service. - Select the URL tab to configure match criteria for URL categories. Enter information for the following fields.

Field Description URL Category Click the
 Add icon to select one or more predefined/custom URL categories and apply the security access rule to the URL. For information, see Configure URL Files.
Add icon to select one or more predefined/custom URL categories and apply the security access rule to the URL. For information, see Configure URL Files.Reputations Click the  Add icon to select one or more predefined URL reputations and apply the security access rule to the URL. For more information, see View a Predefined URL Reputation.
Add icon to select one or more predefined URL reputations and apply the security access rule to the URL. For more information, see View a Predefined URL Reputation. - Select the Users/Groups tab to define the users and user groups to which the rule applies. Enter information for the following fields.

Field Description Match Users Select the users to match:
- Any—If you select to match any users, you cannot configure any other fields on this tab.
- Known—If you select to match known users, you cannot configure any other fields on this tab.
- Selected—If you select to match selected users, you can configure the other fields on this tab.
- Unknown—If you select to match unknown users, you cannot configure any other fields on this tab.
User Group Profile If you match selected users, select a user group profile to match users in a group. Local Database If you match selected users, click to create a local database to match users and user groups. Select these users and user groups in the Users and Groups fields. External Database If you match selected users, click to use an external database to match users and user groups. Select these users in the Users and Groups fields. Users If you match selected users, click the  Add icon and select a user. Select + New Custom User to add a user.
Add icon and select a user. Select + New Custom User to add a user.Groups If you match selected users, click the  Add icon and select a user group. Select + New Custom Group to add a user group.
Add icon and select a user group. Select + New Custom Group to add a user group. - Select the Enforce tab to select the applications and URLs to which the decryption rule applies. Enter information for the following fields.

Field Description Action (Required) Select the action to take on the traffic:
- decrypt—Decrypt the traffic.
- no-decrypt—Do not decrypt the traffic.
Action Override If the action selected is decrypt, override the decryption action in a URL filtering profile. This URL filtering must be one in which decrypt bypass is enabled. With the action override, the decryption policy bypasses the URL filtering profile after the captive portal takes an Ask or Justify action before redirecting the user to the domain, and the profile is not decrypted.
- URL Filtering
Select the URL filtering profile to which to apply the action override. Select + Add New to add a new URL filtering action override.
Decryption Profile (Required) If the action you select is decrypt, select the decryption profile. Select + Add New to add a new decryption profile. - Click OK.
Upload a Trusted CA Database
To upload a trusted CA database that verifies and confirms authority of the server certificate and to map it to a decryption profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors > Objects > Custom Objects > CA Chains in the left menu bar.
- Select the Director tab in the main pane.

- Click the
 Upload icon. The Upload CA Chain to Director popup window displays.
Upload icon. The Upload CA Chain to Director popup window displays.

- In the Chain Name field, enter a name for the CA chain.
- Click Browse and select the CA chain file to upload to Versa Director.
- Click OK.
- In the main CA Chain screen, select the Appliance tab.
- Click the
 Upload icon. The Upload CA Chain File to Appliance popup window displays.
Upload icon. The Upload CA Chain File to Appliance popup window displays.

- In the Name field, select the name of the CA chain file.
- In the Appliance field, select a VOS device.
- Click OK to upload the CA chain file to the VOS device.
Upload a CA Certificate
A certificate authority (CA) is an entity that issues digital certificates that are used to verify the ownership of a public key. The digital certificates allow a party to trust the signature that is made by a private key that corresponds to the certified public key.
After a VOS device requests a certificate from a CA server, the CA server issues the certificate. You then need to upload the certificate to the CA database so that it can be used for verification.
You can upload the CA certificate as a bundle of two files (zipped certificate and key), you can upload an existing CA file directly to a VOS device, or you can generate a new CA certificate on the VOS device. If you upload files, they must be in .zip format, and the key file must have the .key extension. The certificate file can have any file extension.
To upload a CA certificate:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors > Objects > Custom Objects > CA Certificate in the left menu bar.
- Select the Director tab in the main pane.

- Click the
 Upload File icon. The Upload CA Certificate to Director popup window displays.
Upload File icon. The Upload CA Certificate to Director popup window displays.

- Click Browse, and the select the name of the CA database file to upload.
- In the CA Chain field, select a CA chain. In Releases 22.1 and later, you must select a CA chain.
- Click OK.
- In the main CA Certificate screen, select the Appliance tab.
- Click the
 Upload icon. The Upload CA Certificate to Appliance popup window displays.
Upload icon. The Upload CA Certificate to Appliance popup window displays.

- In the Filename field, select the name of the CA certificate file.
- In the Appliance field, select an appliance .
- In the CA Chain field, select a CA chain. In Releases 22.1 and later, you must select a CA chain.
- Click OK.
Export a CA Certificate to a File
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Objects & Connectors > Objects > Custom Objects > CA Certificate in the left menu bar.
- Select the Appliance tab in the main pane.

- Select a Certificate from the list in the main pane.
- Click the
 Export icon.
Export icon. - Click OK.
Upload CRL Files
A certificate revocation list (CRL) is a cryptographically signed list of certificates that are revoked by a CA before their scheduled expiration date and should no longer be trusted. To validate the certificates in a CRL, you can upload a CRL file to a VOS device and enable CRL checking in an HTTP/HTTPS decryption profile. Enabling the CRL check ensures that a VOS device validates the server certificates received from SSL/TLS sessions against the CRL database.
You first upload the CRL file to the Director node, and then you upload it to the VOS device. To enable CRL checking in an HTTP/HTTPS decryption profile, see the section Configure an SSL Decryption Profile, above.
To upload a CRL file to a Director node:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects> Custom Object> CRL in the left menu bar.

- Select the Director tab in the horizontal menu bar.
- Click the
 Upload File icon, and in the Upload CRL to Director popup window, enter information for the following fields.
Upload File icon, and in the Upload CRL to Director popup window, enter information for the following fields.
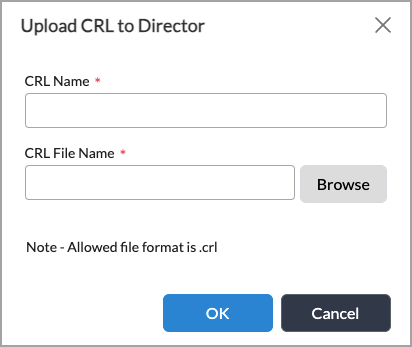
Field Description CRL Name Enter a name for the CRL. CRL Filename Click Browse to select the CRL file to upload to the Director node. The file must be in .crl format. - Click OK.
To upload a CRL file to a VOS device:
- If you are continuing from the previous section, skip to Step 4. Otherwise, in Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Custom Objects > CRL in the left menu bar.
- Select the Appliance tab in the horizontal menu bar.

- Click the
 Upload File icon, and in the Upload CRL to Appliance popup window, enter information for the following fields.
Upload File icon, and in the Upload CRL to Appliance popup window, enter information for the following fields.

Field Description Name Select the name of a CRL file. Appliance Select the name of the VOS device to which to upload the CRL file. - Click OK.
Configure SSL Server Profiles
For Releases 21.2.1 and later.
You can configure SSL server profiles that are used for decryption by captive portal and Versa secure access. Server profiles are used to validate client certificates during certificate-based authentication. Server profiles are based on decryption profiles and use server certification instead of a CA certificate. Note that decryption policy evaluation is not performed for an SSL server profile.
In an SSL server profile, you can configure servers and import server certificates, and you can select a default server certificate. A default server certificate is used for authentication during the TLS handshake when the VOS device is establishing a connection if the first client message (the client Hello) does not contain a Server Name Indication (SNI). If you do not configure a default server certificate, and if the client Hello message does not contain an SNI, the session is closed. When an SNI is present in the initial client message, all the configured servers are evaluated in order, and the first match is used. A server matches when its hostname matches the domain pattern of the server. That server's server certificate is then used to establish connection.
To configure an SSL server profile:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Next-Gen Firewall > Decryption > Server Profiles in the left menu bar.

- Click the
 Add icon. The Add Server Profile popup window displays.
Add icon. The Add Server Profile popup window displays. - Select the General tab, and then enter information for the following fields.


Field Description Name Enter a name for the server profile. Description Enter a text description for the server profile. Enable Profile Click to enable the server profile. Support Session Ticket Click to enable a session that was created earlier. Server (Group of Fields) Displays the names of the servers that are already configured. To add a server, click the  Add icon and in the Server Details popup window, enter information for the following fields.
Add icon and in the Server Details popup window, enter information for the following fields.

- Name
Enter a name for the server. - Certificate
Select a certificate to use to authenticate the server. - Domain Pattern
Click the  Add icon to add a domain pattern for the server. When the hostname and domain pattern match, this server's server certificate is used for client connection.
Add icon to add a domain pattern for the server. When the hostname and domain pattern match, this server's server certificate is used for client connection.Match Rule (Group of Fields) Displays the names of the match rules that are already configured. To add a rule, click the
 Add icon and in the Match Rule popup window, enter information for the following fields.
Add icon and in the Match Rule popup window, enter information for the following fields.

- Name
Enter a name for the match rule. - Port List
Click the  Add icon to add a TCP port on which to listen for connections for the server profile.
Add icon to add a TCP port on which to listen for connections for the server profile.- Routing Instance List
Click the  Add icon to add a routing instance for the server profile.
Add icon to add a routing instance for the server profile.- Address List
Click the  Add icon to add an IP address on which to listen for connections for the server profile.
Add icon to add an IP address on which to listen for connections for the server profile.LEF Profile Select a log export functionality (LEF) profile to use to capture logs for the server profile. LEF Log Level Select the log level to associate with the LEF profile Default Profile Click to use the default LEF profile instead of the LEF profile selected in the previous field. For more information, see Configure Log Export Functionality. SNAT Pool Select the source NAT (SNAT) pool to use for OCSP requests. For more information, see Configure SNAT Pools. SNAT Pool Default Click to make the selected SNAT pool the default pool. Client Authentication (Group of Fields) - Trusted Certificate Database for Client Certification
Select a Trusted Certificate Database for Client Certification. - Default Server Certificate
Select the default certificate to use when the client message does not contain an SNI. - CA Chain
Select the certificate authority (CA) chain for the server certificate. For more information, see Configure CA Certificates, Key File, and CA Chains.
OCSP (Group of Fields) - Enabled
Click to enable server certificate verification using the Online Certificate Status Protocol (OCSP). - Block Unknown Certificate
Click to block SSL sessions whose certificate status is unknown. - Response Timeout
Enter the timeout for an OCSP request.
Default: 5 seconds
Value: 0 through 255 seconds
- Verify
Fetch Issuer Using AIA Issuers (For Releases 22.1.2 and later.) Click to fetch intermediate certificates from the issuing certification authority. Authority Information Access (AIA) is an extension in SSL certificates that contains information about the issuer of the certificate. If a server does not provide intermediate certificates, you can download the certificates from the link contained in the AIA field. - Select the SSL Protocol tab, and enter information for the following fields. Note that if you do not select key exchange algorithms, encryption algorithms, and authentication algorithms, all algorithm are considered to be enabled for the selected cipher suites.

Field Description Minimum Version Select the minimum version of the Transport Layer Security (TLS) protocol that is supported. The minimum version must be the same as or earlier than the maximum version.
- TLS 1.0
- TLS 1.1
- TLS 1.2
- TLS 1.3
Maximum Version Select the maximum version of the TLS protocol that is supported. The maximum version must be the same as or later than the minimum version. The options displayed depend on the version you select in the Minimum Version field. For example, if the minimum version is are TLS 1.0, the options TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3 are displayed. If the minimum version is TLS 1.2, the options TLS 1.2 and TLS 1.3 are displayed.
Key Exchange Algorithms When you select minimum and maximum TLS protocol versions and the version is not TLS 1.3, select one or more key exchange algorithms for the SSL connection:
- ECDHE—Elliptic-Curve Diffie–Hellman Key Exchange
- RSA—Rivest–Shamir–Adleman algorithm
Encryption Algorithms Select an encryption algorithm to use:
- AES-128-CBC—AES CBC encryption algorithm with 128-bit key
- AES-128-GCM—AES GCM encryption algorithm with 128-bit key
- AES-256-CBC—AES CBC encryption algorithm with 256-bit key
- AES-256-GCM—AES GCM encryption algorithm with 256-bit key
- Camellia-256-CBC—Camellia encryption algorithm with 256-bit key
- Chacha20-Poly1305—ChaCha stream cipher and Poly1305 authenticator
- Seed CBC—TLS RSA with seed CBC
Authentication Algorithms Click to have the selected LEF profile be the default LEF profile. Cipher Suites Select a TLS cipher suite. If you select a cipher suite, it must be consistent with the selected key exchange, encryption, and authentication algorithms. If you do not configure cipher suites, all cipher suites matching the selected the key exchange, encryption, and authentication algorithms are selected by default.
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SHA
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA384
- TLS-ECDHE-ECDSA-WITH-AES-256-GCM-SHA384
- TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256
- TLS-ECDHE-RSA-WlTH-AES-128-CBC-SHA
- TLS-ECDHE-RSA-WlTH-AES-128-CBC-SHA256
- TLS-ECDHE-RSA-WlTH-AES-128-GCM-SHA256
- TLS-ECDHE-RSA-WlTH-AES-256-CBC-SHA
- TLS-ECDHE-RSA-WlTH-AES-256-CBC-SHA384
- TLS-ECDHE-RSA-WlTH-AES-256-GCM-SHA384
- TLS-ECDHE-RSA-WlTH-CHACHA20 POLY1305-SHA256
- TLS-RSA-WlTH-AES-128-CBC-SHA
- TLS-RSA-WITH-AES-128-CBC-SHA256
- TLS-RSA-WlTH-AES-128-GCM-SHA256
- TLS-RSA-WlTH-AES-256-CBC-SHA
- TLS-RSA-WlTH-AES-256-CBC-SHA256
- TLS-RSA-WlTH-AES-256-GCM-SHA384
- TLS-RSA-WITH-CAMELLIA-256-CBC-SHA
- TLS-RSA-WITH-SEED-CBC-SHA
- Select the HTTP Header Profile tab.

Note that in Releases 22.1.1 and earlier, the Add Server Profile screen did not contain the HTTP Header Profile tab.
- Click in the HTTP Header Profile field, then select an HTTP header profile or click + Add New to create a new HTTP header profile. If you click + Add New, the Add HTTP Header Profile screen displays. For more information, see Configure HTTP Header Profiles.
- Click OK to add the SSL server profile.
View SSL Decryption History
You can view brief and detailed history of SSL decryption profiles from the Monitoring tab.
To view information about SSL decryption profiles sessions:
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the horizontal menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select a provider organization in the top submenu bar.
- Select the Services tab, and then select NGFW > Decryption > History.
- To display a brief history of SSL sessions, select Brief.

- To display a detailed history of SSL sessions, select Detail.

To view SSL session history from the CLI, use the following commands:
- show orgs org-services tenant-name security profiles decrypt history brief
admin@versa-cli> show orgs org-services versa security profiles decrypt history brief
SRC DST PROXY DECRYPT
TIMESTAMP SRC IP PORT DST IP PORT TYPE RULE PROFILE ACTION STARTTLS HOSTNAME
-------------------------------------------------------------------------------------------------------------------------------
2020-12-17 11:59:07 192.168.10.23 42972 151.101.65.67 443 FORWARD rule1 dp1 decrypt false edition.cnn.com
2020-12-17 11:58:56 192.168.10.23 38983 157.240.2.35 443 FORWARD rule1 dp1 decrypt false facebook.com
2020-12-17 11:58:56 192.168.10.23 38983 157.240.2.35 443 FORWARD rule1 dp1 decrypt false facebook.com
2020-12-17 11:58:36 192.168.10.23 55336 172.217.164.110 443 FORWARD rule1 dp1 decrypt false google.com
2020-12-17 11:58:36 192.168.10.23 55336 172.217.164.110 443 FORWARD rule1 dp1 decrypt false google.com
2020-12-17 11:59:03 192.168.10.23 33837 151.101.1.67 443 FORWARD rule1 dp1 decrypt false www.cnn.com
2020-12-17 11:59:03 192.168.10.23 33837 151.101.1.67 443 FORWARD rule1 dp1 decrypt false www.cnn.com
- show orgs org-services tenant-name security profiles decrypt history detail
admin@versa-cli> show orgs org-services versa security profiles decrypt history detail security profiles decrypt history detail "2020-12-17 11:59:07" src-ip 192.168.10.23 src-port 42972 dst-ip 151.101.65.67 dst-port 443 proxy-type FORWARD rule rule1 profile dp1 decrypt-action decrypt starttls false hostname edition.cnn.com decrypt-bypass false action NA action-reason NA splice-state Handshake pub-key-len 2048 starttls-capability false inward-tls-version TLSv1.2 inward-tls-cipher TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 inward-tls-state "Handshake complete" inward-last-tls-op Decrypt inward-last-tls-op-status "Close notify" inward-last-tls-op-error CLOSE_NOTIFY outward-tls-version TLSv1.2 outward-tls-cipher TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 outward-tls-state "Handshake complete" outward-last-tls-op Decrypt outward-last-tls-op-status Success outward-last-tls-op-error UNUSED security profiles decrypt history detail "2020-12-17 11:58:56" src-ip 192.168.10.23 src-port 38983 dst-ip 157.240.2.35 dst-port 443 proxy-type FORWARD rule rule1 profile dp1 decrypt-action decrypt starttls false hostname facebook.com decrypt-bypass false action NA action-reason NA splice-state Handshake pub-key-len 576 starttls-capability false inward-tls-version TLSv1.2 inward-tls-cipher TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 inward-tls-state "Handshake complete" inward-last-tls-op Decrypt inward-last-tls-op-status "Close notify" inward-last-tls-op-error CLOSE_NOTIFY outward-tls-version TLSv1.2 outward-tls-cipher TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 outward-tls-state "Handshake complete" outward-last-tls-op Decrypt outward-last-tls-op-status Success outward-last-tls-op-error UNUSED
To display the history of specific SSL decryption profiles in the Monitor tab, you configure history settings to select the desired profiles. You can display sessions that are either decrypted or not decrypted, and you can set the maximum number of entries to display.
To select the SSL decryption profiles sessions for which to display history:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Decryption > Settings in the left menu bar. The main pane displays the History pane.

- Click the
 Edit icon. In the Edit History popup window, enter information for the following fields.
Edit icon. In the Edit History popup window, enter information for the following fields.

Field Description Action Select the type of SSL session for which to display history:
- Decrypt—Display only sessions that are decrypted.
- No Decrypt—Display only sessions that are not decrypted.
Profiles Select the SSL decryption profiles for which to display session history. Maximum Entries Enter the maximum number of entries to display in the session history in the Monitor tab.
Value: 1 through 128
Default: 64 - Click OK.
Configure Secure Web Proxy
You can configure a VOS device to be an HTTP/HTTPS proxy, and you can define whether the proxy acts for some or all the HTTP or HTTPS requests that it receives.
You can configure the following types of HTTP/HTTPS proxy:
- Explicit proxy—Process SSL/TLS traffic destined to a specific IP address and a port.
- Web proxy—Type of explicit proxy that acts as an intermediary between the user and websites that they are visiting so that the websites see the IP address of the proxy, not the IP address of the user.
- Transparent proxy—Process the SSL/TLS traffic destined to any IP address but to a specific port.
Configure an Explicit Proxy
An explicit proxy processes SSL/TLS traffic destined to a specific IP address and a specific port. To configure an explicit proxy, you configure the proxy IP address and port information on the client (browser), and then you configure explicit mode when you create an SSL decryption profile on the VOS device.
To configure an explicit HTTP/HTTPS proxy on a VOS device:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Decryption > Proxy Profiles in the left menu bar.
- Click the
 Add icon in the main pane. The Add Decryption Profile popup window displays.
Add icon in the main pane. The Add Decryption Profile popup window displays.

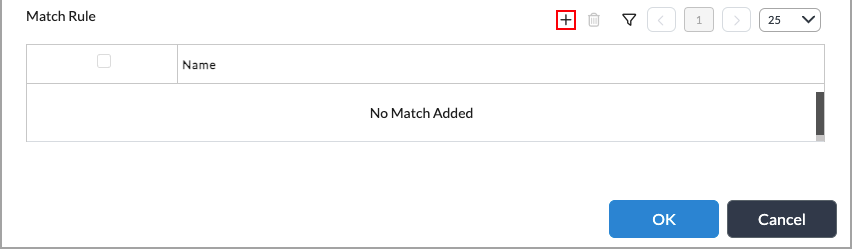
- In the Type field, select SSL Full Proxy.
- Under Mode, click Explicit.
- In the Match Rule table, click the
 Add icon. The Add Match Rule popup window displays.
Add icon. The Add Match Rule popup window displays.

- In the Destination Port table, click the
 Add icon, and then enter the port number to decrypt traffic originating from that port. The most common port number used for an explicit HTTP/HTTPS proxy is 3128.
Add icon, and then enter the port number to decrypt traffic originating from that port. The most common port number used for an explicit HTTP/HTTPS proxy is 3128. - In the Destination IP Address table, click the
 Add icon, and then enter an IP address to decrypt traffic originating from that address.
Add icon, and then enter an IP address to decrypt traffic originating from that address. - Configure other decryption profile parameters. For more information, see Configure an SSL Decryption Profile, above.
- Click OK.
Configure a Web Proxy
You can configure a VOS device to be a web proxy, which is a type of explicit proxy. A web proxy acts as an intermediary between the user and websites that they are visiting so that the websites see and log the IP address of the proxy, not the IP address of the user. In this way, the web proxy allows the user to remain anonymous. A web proxy can also speed up browsing by caching webpage data.
To configure a web proxy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Web Proxy in the left menu bar.

- Click the
 Add icon in the main pane. The Add HTTP/HTTPS Proxy popup window displays
Add icon in the main pane. The Add HTTP/HTTPS Proxy popup window displays - Select the General tab, and then enter information for the following fields.

Field Description Name Enter a name for the HTTP/HTTPS proxy. Description Enter a text description for the HTTP/HTTPS proxy. Mode Select Explicit. For more information about proxy modes, see Configure an SSL Decryption Profile, above.
IP Address Enter the IP address of the HTTP/HTTPS proxy. Port Click the  Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.
Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.Routing Instance Select the routing instance for the proxy to use to route traffic. Source NAT Pool Select the NAT pool for the explicit HTTP/HTTPS proxy to use. LEF Profile Select a LEF profile to use to record the SSL logs for the explicit HTTP/HTTPS proxy. Default Profile Click to use the default LEF profile instead of the LEF profile selected in the previous field. For more information, see Configure Log Export Functionality. Provider Organization Select the organization to which the explicit HTTP/HTTPS proxy belongs. DNS Redirection Policy Select a DNS redirection policy to use for DNS lookup of either the local breakout domain or FQDN of the proxy chain. For more information, see Configure DNS Proxy Profiles.
Note that if the next-generation firewall (NGFW) service is enabled, the redirection access policy must contain one rule with a source zone match condition that matches the host and with the action to allow self-generated DNS traffic. More more information, see Configuration Example: Access Policy Rule To Allow DNS Traffic for NGFW, in Configure File Filtering.
Honor PBF Select whether to honor policy-based forwarding. If you click Yes, when you apply policy-based forwarding in a redirection rule in a DNS profile, proxy forwarding can also check SD-WAN policies to select the path for the DNS query and the onward connection to the application server. For more information, see Configure DNS Redirection Rules. Parse Response Select whether to enable or disable HTTP/HTTPS parsing of the response. If you enable parsing of the response, the parsing responses are available as a counter in the secure web proxy VFP profile statistics. - Select the Cookie-Based User Identification tab, and then enter information for the following fields.

Field Description Enabled Click to enable cookie-based identification, which collects user information from cookies. Authentication URL Enter the URL of the central authentication server. Users are redirected to this server for authentication. Domain Cookie Name Enter the name of the cookie to use for storing user information for each domain.
Domain Cookie Validity Enter how long the domain cookie is valid, in seconds.
Default: 86400 seconds (24 hours)Validation Cookie Name Enter the name of the short-lived validation cookie to use to check the cookie status (whether it is enabled or disabled) on the user agent. Validation Cookie Validity Enter how long the validation cookie is valid, in seconds.
Default: 60 secondsBlock Session with No Cookie Click to block all sessions that do not have a cookie. If you do not click this field, all the sessions whose cookie is not set are allowed even without user identification. Allow Cross-Origin Requests Click to allow cross-origin requests. This option allows a user to request restricted resources on a webpage from a domain that is outside the domain that serves the resource. Whitelist (Group of Fields)
Configure allow list information. - Pattern
Click the  Add icon to add domains that the user is allowed to access without user identification. Enter the pattern to use to match domain name; for example, *+, *.google*.
Add icon to add domains that the user is allowed to access without user identification. Enter the pattern to use to match domain name; for example, *+, *.google*.- URL Category
Click the  Add icon to add a specific URL category to the allow list.
Add icon to add a specific URL category to the allow list. - Select the Rules tab to configure proxy rules.

- Click the
 Add icon. The Add Rules popup window displays.
Add icon. The Add Rules popup window displays.

- Select the General tab, and then enter information for the following fields.
Field Description Name
Enter a name for the rule.
Monitor Select the monitor object for an IP address to associate with the rule. For more information, see Configure IP SLA Monitor Objects. Rule Status Select the rule status:
- Disabled
- Enabled
- Select the Match tab, and then enter information for the following fields.
Field Description Domain Pattern (Tab) - Domain Pattern
Click the
 Add icon to specify a pattern to use to match the domain name; for example, *.example.com. Requests are forwarded to the next proxy address and proxy port through the proxy routing instance only when the domain name of the proxy request matches the domain pattern.
Add icon to specify a pattern to use to match the domain name; for example, *.example.com. Requests are forwarded to the next proxy address and proxy port through the proxy routing instance only when the domain name of the proxy request matches the domain pattern.If you do not specify a pattern, proxy chaining is applied to all sessions.
Negate Match Result Select to negate the final match results. Any rule that matches the criteria is considered as a no-match. Applications/URL (Tab) 
- Applications
Click the  Add icon to select a predefined or a custom application.
Add icon to select a predefined or a custom application.- URL Categories
Click the  Add icon to select a predefined or a custom URL category.
Add icon to select a predefined or a custom URL category. - Select the Enforce tab, and then enter information for the following fields.

Field Description Rule Mode (Group of Fields) Click to select the proxy rule mode:
- Local Breakout
- Proxy Chaining
Proxy Chaining (Group of Fields)
Click to configure the proxy forwarding and match criteria and forward selected sessions to an external proxy. The VOS device acts as an intermediate proxy, and it supports virtual wire mode.
- Proxy IP Address
Enter the address of the next proxy to which to send the forwarding request. - Proxy Port
Enter the port on the next proxy to which to send the forwarding request. - SNAT Pool
Select the SNAT pool for the explicit HTTP/HTTPS proxy to use. - Honor PBF
Click Enabled to honor policy-based forwarding. When honor policy-based forwarding is enabled, and when you apply policy-based forwarding in a redirection rule in a DNS profile, proxy forwarding can also check SD-WAN policies to select the path for the DNS query and the onward connection to the application server. For more information, see Configure DNS Redirection Rules. Local Breakout
Click to route internet traffic from the site directly to the internet.
- Skip Local Breakout on DNS Failure
Click Enabled to not perform local breakout of traffic when DNS fails and instead route traffic to the proxy server. - SNAT Pool
Select the SNAT pool for the explicit HTTP/HTTPS proxy to use. - Negate Match
Select to negate the match results. - Click OK.
Configure a Transparent Proxy
A transparent proxy processes SSL/TLS traffic that is destined to any IP address but to a particular port. The client (browser) performs DNS resolution and opens the connection to the server's IP address. To configure a transparent proxy, you configure explicit mode when you create an SSL decryption profile on a VOS device.
To configure a transparent explicit HTTP/HTTPS proxy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Decryption > Profiles in the left menu bar.
- Click the
 Add icon in the main pane. Select the General tab in the Add Decryption Profile popup window.
Add icon in the main pane. Select the General tab in the Add Decryption Profile popup window.


- In the Type field, select SSL Full Proxy.
- Under Mode, click Transparent.
- In the Match Rule table, click the
 Add icon. The Add Match Rule popup window displays.
Add icon. The Add Match Rule popup window displays.

- In the Destination Port table, click the
 Add icon, and then enter the port number to use for the HTTP proxy. Common port numbers are 80 for an HTTP proxy and 443 for an HTTPS proxy.
Add icon, and then enter the port number to use for the HTTP proxy. Common port numbers are 80 for an HTTP proxy and 443 for an HTTPS proxy. - In the Destination IP Prefix table, click the
 Add icon, and then enter the IP address prefix to decrypt traffic originating from that address.
Add icon, and then enter the IP address prefix to decrypt traffic originating from that address. - Configure other decryption profile parameters, as desired. For more information, see Configure an SSL Decryption Profile, above.
- Click OK.
To associate the decryption profile with a decryption rule:
- Select the Configuration tab in the top menu bar of the Proxy Profiles dashboard screen.
- Select Services > Next-Gen Firewall > Decryption > Policies in the left menu bar, and then select the Rules tab to associate the decryption profile with a decryption rule. For more information, see Step 13 in Configure an SSL Decryption Policy Rule, above.
To configure a transparent proxy for the web proxy service:
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Web Proxy in the left menu bar.

- Click the
 Add icon in the main pane. The Add HTTP/HTTPS Proxy popup window displays.
Add icon in the main pane. The Add HTTP/HTTPS Proxy popup window displays. - Select the General tab, and then enter information for the following fields.


Field Description Name Enter a name for the HTTP/HTTP proxy. Description Enter a text description for the HTTP/HTTPS proxy. Mode Select Transparent. For more information, see Configure an SSL Decryption Profile, above.
IP Prefix Enter the IP address ot the HTTP/HTTPS proxy. Port Click the
 Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.
Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.Routing Instance Select the routing instance for the proxy to use to route traffic. Provider Organization Select the organization to which the transparent HTTP/HTTPS proxy belongs. DNS Redirection Policy Select a DNS redirection policy to use for DNS lookup of either the local breakout domain or FQDN of the proxy chain. For more information, see Configure DNS Proxy Profiles. Source NAT Pool Select the NAT pool for the transparent HTTP/HTTPS proxy to use. SNAT Pool Default Click to use the default SNAT pool instead of the SNAT pool selected in the previous field. LEF Profile Select a LEF profile to use to record the SSL logs for the transparent HTTP/HTTPS proxy. Default Profile Click to use the default LEF profile instead of the LEF profile selected in the previous field. For more information, see Configure Log Export Functionality. Honor PBF Select whether to honor policy-based forwarding. If you click Yes, when you apply policy-based forwarding in a redirection rule in a DNS profile, proxy forwarding can also check SD-WAN policies to select the path for the DNS query and the onward connection to the application server. For more information, see Configure DNS Redirection Rules. Parse Response Select whether to enable or disable HTTP/HTTPS parsing of the response. If you enable parsing of theresponse, the parsing responses are available as a counter in the secure web proxy VFP profile statistics. Parser Request Select whether to enable or disable HTTP/HTTPS parsing of the request. - Click OK.
- Configure your browser, setting the HTTP/HTTPS proxy port to the port configured in the decryption profile.
Configure an Application Proxy
An application proxy serves as an intermediary between an application request from a client and the destination application server to obtain a requested service. When an application makes a request, the application proxy intercepts the request to the destination server and initiates its own request to the server. When the destination server responds to the request, the application proxy responds back to the client as if it were the destination server.
To configure an application proxy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliance in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select an organization in the horizontal menu bar.
- Select Services > Web Proxy in the left menu bar.
- Click the
 Add icon in the main pane.
Add icon in the main pane.

- In the Add HTTP/HTTPS Proxy popup window, select the General tab, and then enter information for the following fields.


Field Description Name Enter a name for the HTTP/HTTPS proxy. Description Enter a text description for the HTTP/HTTPS proxy. Mode Select App Proxy. For more information, see Configure an SSL Decryption Profile, above.
IP Address Enter the IP address of the HTTP/HTTPS application proxy. Port Click the  Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.
Add icon, and then enter the port number to use to connect to the proxy. The most common port number for an explicit HTTP/HTTPS proxy is 3128.Routing Instance Select the routing instance for the proxy to use to route traffic. Provider Organization Select the organization to which the explicit HTTP/HTTPS proxy belongs. DNS Redirection Policy Select a DNS redirection policy to use for DNS lookup of either the local breakout domain or FQDN of the proxy chain. For more information, see Configure DNS Proxy Profiles.
Note that if the next-generation firewall (NGFW) service is enabled, the redirection access policy must contain one rule with a source zone match condition that matches the host and with the action to allow self-generated DNS traffic. More more information, see Configuration Example: Access Policy Rule To Allow DNS Traffic for NGFW, in Configure File Filtering.
Application Domain Enter the domain name of the application proxy. The application domain name is prepended to the replaced URLs in the response. Service Provider Application Domain Enter the service provider application domain name for the application proxy. Source NAT Pool Select the NAT pool for the explicit HTTP/HTTPS proxy to use. LEF Profile Select a LEF profile to use to record the SSL logs for the explicit HTTP/HTTPS proxy. Default Profile Click to use the default LEF profile instead of the LEF profile selected in the previous field. For more information, see Configure Log Export Functionality. Honor PBF Select whether to honor policy-based forwarding. If you click Yes, when you apply policy-based forwarding in a redirection rule in a DNS profile, proxy forwarding can also check SD-WAN policies to select the path for the DNS query and the onward connection to the application server. For more information, see Configure DNS Redirection Rules. Parse Response Select whether to enable or disable HTTP/HTTPS parsing of the response. If you enable parsing of the response, the parsing responses are available as a counter in the secure web proxy VFP profile statistics. Proxy App Certificates (For Releases 22.1.2 and later.) If you select application proxy mode, click the  Add icon, and then select a proxy application server certificate. The server certificates are used to create the implicit SSL server for application proxy.
Add icon, and then select a proxy application server certificate. The server certificates are used to create the implicit SSL server for application proxy.Proxy Apps (For Releases 22.1.2 and later.) If you select application proxy mode, click the  Add icon, and then select a proxy application. You can select multiple proxy applications.
Add icon, and then select a proxy application. You can select multiple proxy applications. - Click OK.
Configuration Example for Decryption Bypass
The decrypt bypass option disables decryption of SSL traffic that matches the predefined captive portal actions for a URL filtering profile after captive portal redirection. The decryption policy decrypts SSL sessions to display only the captive portal response. After the captive portal action is performed, SSL decryption is bypassed, and users can directly access the URL.
The following example shows how to use a URL-filtering profile in which decrypt bypass is enabled in an SSL decryption policy. The configuration here displays a justify form when users try to access a social networking site (here, Facebook).
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Click an appliance in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Security > Profiles > URL Filtering.

- Click the
 Add icon. The Add URL Filter popup window displays.
Add icon. The Add URL Filter popup window displays.

- Add a URL-filtering profile with the following information. For more information, see Configure URL Filtering.
- In the Name field, enter a name for URL filter. In our example, the name is URLF_Profile_Social_Networks.
- Click the Decrypt Bypass checkbox to enable decryption bypass.
- Select the Category-Based Action tab and add an action to justify access to social networking sites.
- Click OK.
- Go to Services > Next-Gen Firewall > Security > Policies, and then select the Rules tab.

- Click the
 Add icon.
Add icon. - In the Add Rule or Edit Rule popup window, add or edit a security access policy rule to apply to the URL-filtering profile. In our example, we update the rule named Justify_Social_Media_Traffic. For more information, see Configure Security Access Policy Rules.

- Select the Applications/URL tab, click the
 Add icon, and then select social_network from the URL Category List.
Add icon, and then select social_network from the URL Category List. - Select the Enforce tab.

- In the Actions field, select Apply Security Profile.
- Click Profiles, and then select URL Filtering. Then select the profile you added, URLF_Profile_Social_Networks, in Step 1. Note that in this profile, Decrypt Bypass is enabled.
- Select the Applications/URL tab, click the
- Click OK.
- Upload a certificate, as described in Upload a CA Certificate, above. When users try to access social networking sites, this certificate displays, along with the justify form.
- Add an SSL decryption profile, as described in Configure an SSL Decryption Profile, above. In our example, the name of the decryption profile is Forward_Proxy.

- Add an SSL decryption policy rule in the Add Decryption popup window, as described in Configure an SSL Decryption Policy Rule, above. In our example, the rule name is Justify_Social_Media_Traffic.

- Click OK.
- Add an SSL decryption policy rule in the Add Decryption popup window, as described in Configure an SSL Decryption Policy Rule, above. In our example, the rule name is Justify_Social_Media_Traffic.
- Apply this rule to the SSL decryption rule that you created in Step 5.
- In the URL tab, select social_network in the URL Category table.
- In the Enforce tab:
- In the Action field, select decrypt.
- In the Decryption Profile field, select the decryption profile you created in Step 5, here Forward_Proxy.
- In the URL Filtering field, select the URL filtering profile you created in Step 1, here URLF_Profile_Social_Networks.
- In the URL tab, select social_network in the URL Category table.
- Click OK.
- When users try to access any social networking site, such as Facebook, the following justify form and CA certificate are displayed. To access Facebook, users must enter a justification and then click Continue.
To display the statistics for the SSL decryption profile called Forward_Proxy, issue the show orgs organization name security profiles decrypt profile-stats decryption-profile-name CLI command. The ssl_pxy_bypass field shows the number of times the decrypt bypass has been used in the decryption profile.
security profiles decrypt profile-stats Forward_Proxy ssl_pxy_client_encrypt 0 ssl_pxy_client_decrypt 0 ssl_pxy_client_ptdata 0 ssl_pxy_server_encrypt 0 ssl_pxy_server_decrypt 0 ssl_pxy_server_ptdata 0 ssl_pxy_create 0 ssl_pxy_strm 0 ssl_pxy_drop 0 ssl_pxy_url_match 0 ssl_pxy_url_decrypt 0 ssl_pxy_url_no_decrypt 0 ssl_pxy_bypass 1 ssl_pxy_splice_failed 0 ssl_pxy_noprof_err 0 ssl_pxy_err 0 ssl_alert_pxy_client_unexpected_message 0 ssl_alert_pxy_client_bad_record_mac 2 ssl_alert_pxy_client_decryption_failed 0 ssl_alert_pxy_client_record_overflow 0 ssl_alert_pxy_client_decompression_failure 0 ssl_alert_pxy_client_handshake_failure 0 ssl_alert_pxy_client_no_certificate 0 ssl_alert_pxy_client_bad_certificate 0 ssl_alert_pxy_client_unsupported_certificate 0 ssl_alert_pxy_client_certificate_revoked 0 ssl_alert_pxy_client_certificate_expired 0
Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 21.2.1 adds support for CRL file uploading, SSL server profile configuration, setting the SSL encryption profile session cache history, displaying session history, validating a server certificate using OCSP, and configuring rule order for SSL decryption policy rules.
- Releases 22.1.2 renames the HTTP Header Insertion tab Advanced tab; adds support for proxy application certificates and proxy applications for web proxy.
