Configure Systemwide Functions
![]() For supported software information, click here.
For supported software information, click here.
This article describes how to configure a number of systemwide functions on Director nodes.
Configure High Availability
High availability (HA) provides a fallback option in case the active Director node goes down. HA ensures a seamless bringup of the standby Director node, thus allowing network services to continue with no disruptions.
The Director node supports the following flows for HA:
- Netconf
- Fault module supports UDP and TCP channels
For a UDP channel, syslog messages are sent to the active and standby Director nodes, but only the active node processes the alarms. You configure a remote collector for the active-standby pair. For a TCP channel, only the active Director node accepts a connection, and you configure a log collector group for the active-standby pair. Data between the active and standby Director nodes is synchronized by Postgres replication.
Any settings that you configure on the active Director node automatically extend to the standby Director node. The standby node cannot perform any action until it activates.
View HA Settings
For Releases 22.1.1 and later.
To view the Director HA settings:
- In Director view, select the Administration tab in the top menu bar.
- Select System > High Availability in the left menu bar. The following screen displays.

The High Availability pane displays the following read-only information about the HA components:

Configure HA for Director Nodes in Releases 21.2.1 and Earlier
For Releases 21.2.1 and earlier.
- Install Versa Director on two hosts (virtual machines, or VMs).
- Log in to one of the Director nodes.
- In Director view, select the Administration tab in the top menu bar.
- Select System > High Availability in the left menu bar.

- In the High Availability pane, click the
 Edit icon. In the High Availability popup window, enter information for the following fields.
Edit icon. In the High Availability popup window, enter information for the following fields.

Field Description Master IP Address Enter the IP address of the active Director node. Slave IP Address Enter the IP address of the standby Director node. Designated Master IP Address Enter the IP address of the designated active Director node. Enable Auto Switchover Click to enable automatic switchover to the backup Director node if the active Director node goes down. - Click OK.
Configure Revertive Behavior
By default, the Director HA implementation is non-revertive, which means that if the designated master is up and running after a recovery, it is not promoted to master. To change the behavior to be revertive, so that the designated master is promoted to active after a recovery, you enable automatic switchover. The designated master is then promoted to active after the automatic switchover timeout value expires.
It is recommended that you not change the HA configuration values in production deployments.
To enable revertive behavior in Releases 22.1.1 and later:
- In the Director view, select the Administration tab in the top menu bar.
- Select System > High Availability in the left menu bar.

- In the High Availability Configuration pane, click the
Edit icon. In the Edit Configure HA popup window, enter information for the following fields.

Field Description Enable Auto Switchover Click to enable the designated active Director node to promote itself to the active state after a recovery. Auto Switchover Timeout Enter the timeout period, in seconds, before the designated active Director node promotes itself to the active state after a recovery.
Range: 180 through 3600 seconds (60 minutes)
Default: 180 seconds (3 minutes)Failover Timeout Enter the timeout period, in seconds, before the standby Director node can promote itself to be the active Director node.
Range: 180 through 3600 seconds (60 minutes)
Default: 300 seconds (5 minutes)Standby Start Timeout
Enter how long, in seconds, a non-designated standby node waits before it promotes itself to the active state.
Range: 0 through 3600 seconds (60 minutes)
Default: 100 secondsActive IP Address
Enter the IP address of the active Director node. This field is disabled if HA is enabled for the Director node. Standby IP Address
Enter the IP address of the standby Director node. This field is disabled if HA is enabled for the Director node. - Click OK.
To enable revertive behavior in Releases 21.2 and earlier:
- In the Director view, select the Administration tab in the top menu bar.
- Select System > High Availability in the left menu bar.

- In the HA Configuration pane, click the
Edit icon. In the Edit Configure HA popup window, enter information for the following fields.

Field Description Enable Auto Switchover Select to enable the designated active Director node to promote itself to the active state after a recovery. Auto Switchover Timeout Enter the timeout period, in seconds, before the designated active Director node promotes itself to the active state after a recovery.
Range: 0 through 3600 seconds (60 minutes)
Default: 120 seconds (2 minutes)Failover Timeout Enter the timeout period, in seconds, before the standby Director node can promote itself to be the active Director node.
Range: 0 through 3600 seconds (60 minutes)
Default: 300 seconds (5 minutes)Standby Start Timeout
Enter how long, in seconds, a non-designated standby node waits before it promotes itself to the active state.
Range: 0 through 3600 seconds (60 minutes)
Default: 100 secondsActive IP Address
Enter the IP address of the active Director node. This field is disabled if HA is enabled for the Director node. Standby IP Address
Enter the IP address of the standby Director node. This field is disabled if HA is enabled for the Director node. - Click OK.
Configure HA Failover
You can manually cause the Director active node to fail over. Doing this causes the active Director node to become the standby, and the standby node to become the active Director node.
For Release 22.1.1 and later, click Failover in the High Availability Configuration pane.

For 21.2 and earlier, click Failover in the High Availability pane.

For automatic failover, if the active Director node is down because of network issues or if the vnms process has stopped, the standby Director node checks the status of the active node for a maximum of 15 minutes (checking at the default interval of 300 seconds for a maximum of three times) before assuming the role as the active Director node. This behavior is not specific to the SSL certificate installation process.
In Releases 22.1.1 and later, to configure the failover timeout,click the Edit icon in the High Availability pane, enter a value in the Failover Timeout field, and then click OK.
In Releases 21.2 and earlier, you configure the failover timeout using REST API calls or the following Director CLI commands.
To display the failover timeout, issue the following CLI command:
Administrator@VOAEHA2> show vnmsha ha-config failover-timeout failover-timeout 300;
To set the failover timeout, issue the following CLI command:
Administrator @VOAEHA2% set vnmsha ha-config failover-timeout seconds
For example, to set the failover timeout to 60 seconds:
Administrator @VOAEHA2% set vnmsha ha-config failover-timeout 60 Administrator @VOAEHA2% commit
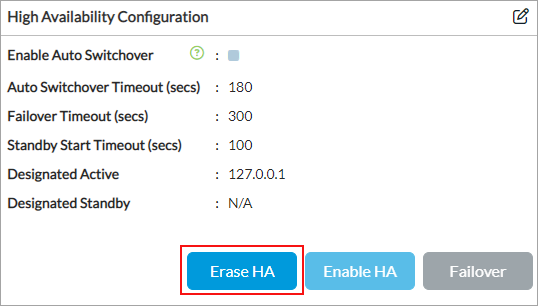
Delete the HA Configuration
For Releases 22.1.1 and later.
To reconfigure the Director nodes in an HA implementation, you can delete the HA configuration.
To delete the HA configuration on a Director node on which HA is enabled:
- In the High Availability Configuration section, click Disable HA.

- Click Erase HA.
- To reconfigure the HA node, click the
Edit icon. The Edit Configure HA screen displays. For more information, see Configure Revertive Behavior above.
To remove the HA configuration on a Director node on which HA is not enabled, click Erase HA in the High Availability Configuration pane.
Configure OAuth
The Versa Director UI and Versa Analytics use the Open Authorization (OAuth) login protocol to communicate with the Director node. OAuth has two mechanisms for logging in:
- Client registration—The Director administrator registers the application client and shares the client ID and client secret with the user, who uses the information to access the application and refresh the tokens.
- Token registration—An administrator creates a client registration token and shares with the user, who uses the token to invoke a REST API call. As a result, the application self-registers and generates the client ID and secret ID to access the application and refresh the tokens.
This section describes how to register clients and tokens.
Register Clients
- In Director view, select the Administration tab in the top menu bar.
- Select System > Authorization > Clients in the left menu bar.

- Click the
 Add icon. In the Add Client popup window, enter information for the following fields.
Add icon. In the Add Client popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the client. Description (Required) Enter a text description for the client. Disable Click to deactivate the client after you commit the configuration. - Select the Credential tab, and enter information for the following fields.
Field Description URL (Group of Fields) - Client URL
Enter the URL to invoke. - Redirect URL
Enter the URL to which to redirect the user. Address (Group of Fields) Configure how to grant access authorization to the OAuth client. - Any
Click to grant access to all IP addresses. - Source Address
Click to grant access only to specific IP addresses. Click the  Add icon to add the addresses in the table.
Add icon to add the addresses in the table.Grant Types (Group of Fields) Select one or more types of access to grant to an application. - Client Credentials
Click to issue a client ID and secret ID. - Password
Click to issue a password for access. - Refresh Token
Click to issue a refresh token to generate a new token for access. - Select the Expiry tab, and enter information for the following fields.

Field Description Client Expires On Enter the expiration date and time for the client ID. Client Secret Expires On Enter the expiration date and time for the secret ID. - Select the Contacts tab, and enter information for the following fields.

Field Description Email (Required) Enter the email address for the client contact. Phone (Required) Enter the telephone number for the client contact.  Add icon
Add iconClick the  Add icon to add the contact information.
Add icon to add the contact information. - Select the Access tab, and enter information for the following fields.

Field Description Maximum Tokens per User (Required) Enter the maximum number of tokens to allocate to each user. Token Validity (Required) Enter how long the token is valid, in seconds. Maximum Access Tokens Enter the maximum number of access tokens to allocate to a client. You can assign any number of tokens to a user to access applications or APIs. For example, for a user to access five applications, allocate five access tokens. Refresh Token Validity (Required) Enter how long the refresh token is valid, in seconds. When a token expires, it has to be refreshed using a refresh token, which generates a new access token for the client. Software Identification Enter the application identifier. Software Version Enter the application version. - Click OK.
View System Uptime
In Director view, select the Monitor tab in the top menu bar to view the system uptime and application uptime in the monitor dashboard.

View System Resources
In Director view, select the Monitor tab in the top menu bar to view the system details usage, including memory usage, CPU load, and disk usage in the monitor dashboard.

Configure an NTP Server
The Network Time Protocol (NTP) synchronizes clock times on the computers in a network. NTP synchronizes computer clock times to within a few milliseconds of Coordinated Universal Time (UTC). To use NTP, you configure an NTP server in a network.
For Releases 22.1.4 and later, you can configure authentication for NTP by creating an authentication key, using either MD5 or SHA1.
Add an NTP Server
- In Director view, select the Administration tab in the top menu bar.
- Select System > NTP > Server in the left menu bar.

- Click the
 Add icon. In the Create NTP Server popup window, enter information for the following fields.
Add icon. In the Create NTP Server popup window, enter information for the following fields.

Field Description Server (Required) Enter a name for the server. iburst Click to enable iburst on the server. Using iburst improves the time required for initial synchronization. With iburst, when the NTP server is unreachable, a burst of eight packets is sent instead of the usual one packet. Key (For Release 22.1.4 and later.) Select an authentication key. For more information, see Create an NTP Authentication Key, below. - Click OK.
Create an NTP Authentication Key
For Releases 22.1.4 and later.
- In Director view, select the Administration tab in the top menu bar.
- Select System > NTP > Key in the left menu bar.

- Click the
 Add icon. In the Add Create NTP Key popup window, enter information for the following fields.
Add icon. In the Add Create NTP Key popup window, enter information for the following fields.

Field Description Key ID (Required) Enter an ID number for the NTP key.
Range: 1 through 65535.
Default: None
Type (Required) Select an authentication type:
- md5
- sha1
- sha256 (Currently not supported.)
- sha384 (Currently not supported.)
- sha512 (Currently not supported.)
Value (Required) Enter a password for the NTP key. - Click OK.
Configure Static Routes
Static routes are fixed and do not change, even if the network is changed or reconfigured. They are useful when dynamic routing fails.
To configure a static route:
- In the Director view, select the Administration tab in the top menu bar.
- Select System > Static Routes in the left menu bar.

- For Releases 22.1.1 and later, when a standby node is available, you can add static routes to the active or standby Director node:

- Click the
 Add icon. In the Add Static Route popup window, enter information for the following fields.
Add icon. In the Add Static Route popup window, enter information for the following fields.
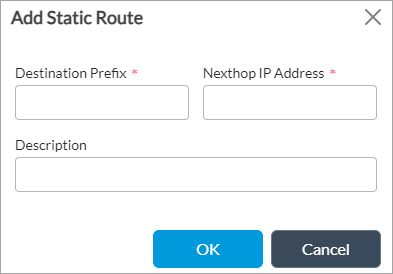
Field Description Destination Prefix Enter the destination IP address of the static route. Next-Hop IP Address (For Releases 21.2 and earlier.) Enter the IP address of the next-hop interface to reach the destination. Description (For Releases 22.1.1 and later.) Enter a text description for the static route. - Click OK.
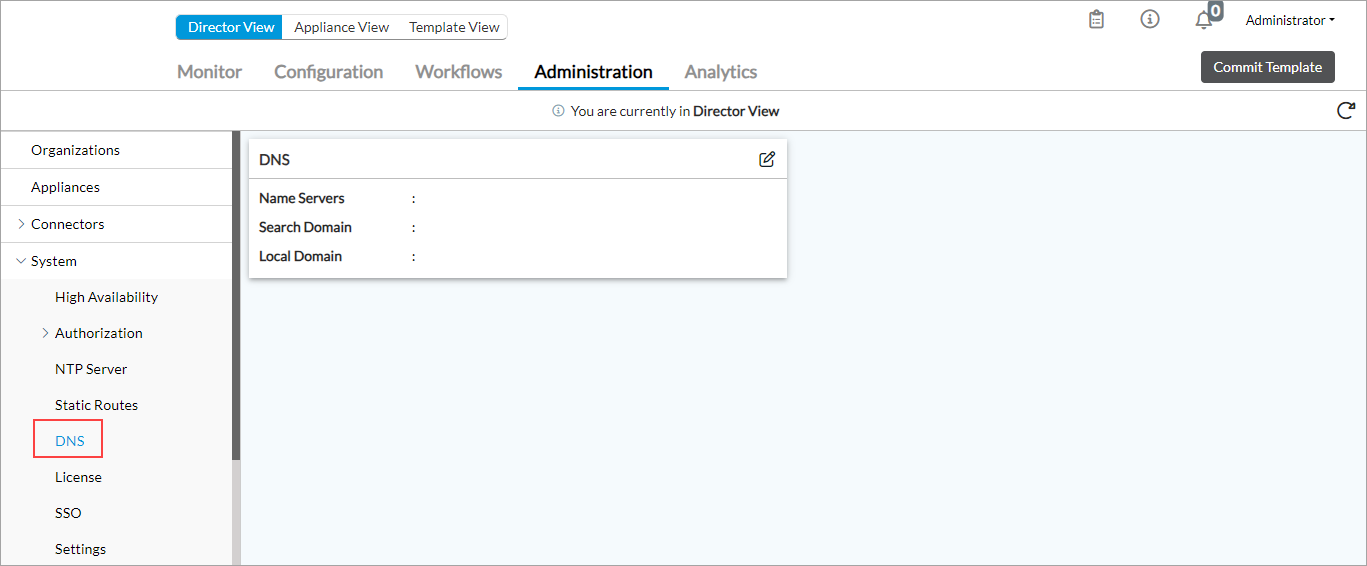
Configure a DNS Server
A Domain Name System (DNS) server maintains a directory of domain names and translates them to Internet Protocol (IP) addresses.
To configure a DNS server:
- In Director view, select the Administration tab in the top menu bar.
- Select System > DNS in the left menu bar.
- Click the
 Edit icon. In the Edit DNS popup window, enter information for the following fields.
Edit icon. In the Edit DNS popup window, enter information for the following fields.
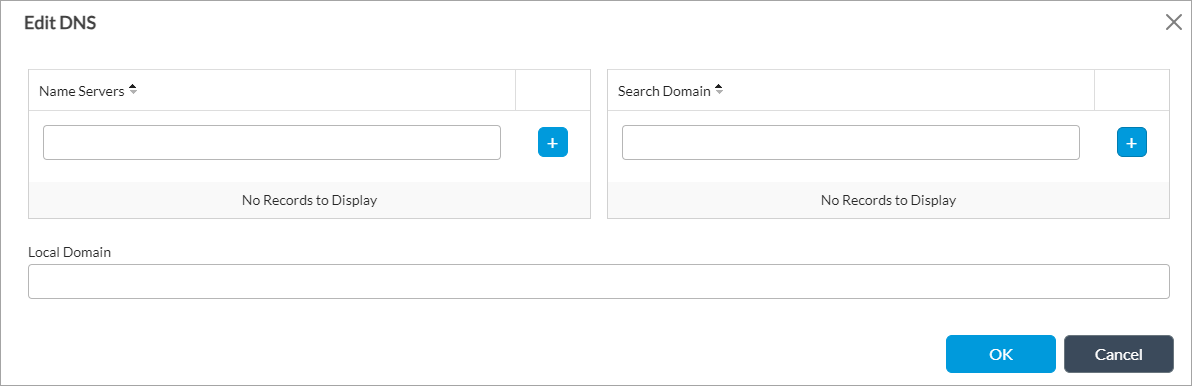
Field Description Name Servers Click the  Add icon, and enter the IP address of the DNS server.
Add icon, and enter the IP address of the DNS server.Search Domain Click the  Add icon, and enter the IP address that the DNS service uses to resolve hostnames that are not fully qualified.
Add icon, and enter the IP address that the DNS service uses to resolve hostnames that are not fully qualified.Local Domain Enter the IP address of the local domain. - Click OK.
Verify the Director System License Status
For Releases 21.2 and earlier.
To verify the license status of a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select System > License in the left menu bar.

View the Director License and Upload the License Key
For Releases 22.1.1 and later.
- In Director view, select the Administration tab in the top menu bar.
- Select System > License in the left menu bar.
- Select the active or standby Director node to view in the Node ID field. The License screen displays the information about the Director license. For example:

- Click the
Download icon to download the Director node ID binary file that represents the node. You can share this file to Versa Support to request for a new license key.
- Click the
Edit icon to upload a new license key. The license key file must be in .key format. The Upload popup window displays.

- Click Choose File and then select the license key file from your device.
- Click Upload.
Configure Subjugate Addresses
Subjugation allows a Director node to control selected Versa Operating SystemTM (VOSTM) devices exclusively so that all network communication between VOS devices can happen only through that Director node. One reason to subjugate VOS devices to a particular Director node is to streamline the management of branches and network services.
To enable subjugation:
- In Director view, select the Administration tab in the top menu bar.
- Select System > Settings in the left menu bar. In Releases 22.1.1 and earlier, select System > Southbound Addresses in the left menu bar.

- In the Southbound IP Addresses pane, click the
 Edit icon to add IP addresses.
Edit icon to add IP addresses.
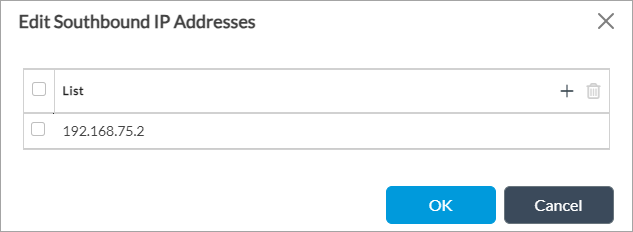
- Click the
 Add icon to add an IP address.
Add icon to add an IP address. - Click OK.
Enable the Secure Upload
To enable signature verification for secure upload, see Configure Signature Verification for Software Package Uploads.
Configure Stolen Branch Settings
To edit the stolen branch settings on a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select System > Settings in the left menu bar. In Release 22.1.1, select System > Settings > Stolen Branch Settings in the left menu bar.
- In the Stolen Branch pane, click the
 Edit icon.
Edit icon.

- In the Edit Stolen Branch Setting popup window, enter information for the following fields.

Field Description Continuous Alarm Interval Enter how often, in minutes, to send a continuous alarm when theft of a device is suspected.
Default: 60 minutes
Detection Interval Enter how often, in minutes, to check for detect suspected stolen devices.
Default: 20 minutesDistance Unit - Miles
Click to use miles for distance-based detection. This is the default.
- Kilometers
Click to use kilometersfor distance-based detection. Enable Click to enable antitheft detection.
- Click OK.
Configure the Timezone
To configure the timezone on a Director node:
- In the Director view, select the Administration tab in the top menu bar.
- Select System > Settings in the left menu bar. In Releases 22.1.1 and earlier, select System > Time Zone in the left menu bar.

- In the Timezone pane, click the
 Edit icon.
Edit icon.
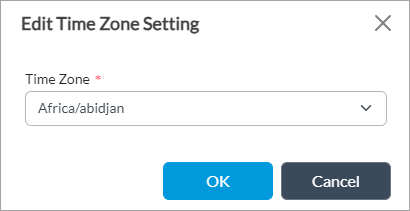
- In the Edit Time Zone Setting popup window, select the timezone in the Time Zone field.
- Click OK.
Configure Proxy Settings
To configure proxy settings for HTTP or HTTPS:
- In the Director view, select the Administration tab in the top menu bar.
- Select System > Settings in the left menu bar. In Releases 22.1.1 and earlier, select System > Proxy Setting in the left menu bar.

- In the Proxy Setting pane, click the
 Edit icon.
Edit icon. - In the Edit Proxy Settings popup window, enter information for the following fields.
Note: For Releases 22.1.1 and later, you must add the HA IP addresses of both the active and standby Directors under Exceptions below.
Note: If you configure Director to use a proxy for operating system security package (OS SPacks) and security package (SPack) updates, you must add an exception for the Versa Messaging Service (VMS) IP address that Director uses to communicates with it, typically the northbound IP address of VMS.

Field Description Enabled Click to enable proxy settings. HTTP Host Enter the HTTP hostname or IP address of the proxy. HTTP Port Enter the HTTP port number of the proxy. HTTPS Host Enter the HTTPS hostname or IP address of the proxy. HTTPS Port Enter the HTTPS port number of the proxy. Username Enter the login name to access the proxy. Password Enter the password to access the proxy. Exceptions Click the
 Add icon to add the hostname or IP address of exceptions for the proxy.
Add icon to add the hostname or IP address of exceptions for the proxy. Note: For Releases 22.1.1 and later, you must add the HA IP addresses of both the active and standby Directors. For example:

- Click OK.
Configure Local Organizations
To configure a local organization and associate it with a network name and VLAN IP address:
- In Director view, select the Administration tab in the top menu bar.
- Select Connectors > Local > Organization in the left menu bar.

- Click the
 Add icon. In the Add Organization popup window, enter information for the following fields.
Add icon. In the Add Organization popup window, enter information for the following fields.

Field Description Name Enter a name for the organization. Description Enter a text description for the organization. - Select the Networks tab, and enter information for the following fields.
Field Description Networks (Group of Fields) Name Name of the network. VLAN
Enter the VLAN IP address. IPv4 Allocation Mode
Select how to allocate IPv4 addresses: - DHCP
- Manual
IPv6 Allocation Mode
Select how to allocate IPv6 addresses: - DHCP
- Manual
- Select the Resources tab, and enter information for the following fields.

Field Description Resource Pool (Group of Fields) Server Name
Enter the names of one or more servers. IP Address/Host Name
Displays the selected server IP address. Click  Add icon to add a server.
Add icon to add a server. - Click OK.
Configure AMQP Connectors
The Advanced Message Queuing Protocol (AMQP) is an open standard application layer protocol for messages. The key features of AMQP are message orientation, queuing, routing, reliability, and security. The AMQP connector defines which credentials to use when connecting, and it defines all the common properties used by the inbound and outbound endpoints that use the connector.
To configure an AMQP connector:
- In Director view, select the Administration tab in the top menu bar.
- Select Connectors > AMQP in the left menu bar.

- Click the
 Add icon. In the Add AMQP Connector popup window, enter information for the following fields.
Add icon. In the Add AMQP Connector popup window, enter information for the following fields.

Field Description Name Enter a name for the AMQP connector. AMQP Host Enter the IP address of the AMQP connector. AMQP Port Enter the port number that the AMQP connector uses. Exchange Enter the address of the exchange server. vHost Enter the name of the vHost server. Username Enter the login name to access the server. Password Enter the password to access the server. Notification Types Click to receive notifications. Email Enter the email ID to send AMQP server connectivity notification.
Director Identifier Name Enter a name for the Director identifier.
- Click OK.
Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- In Release 22.1.1:
- High Availability section in the High Availability screen is view only. Move Designated Active and Designated Standby fields to the High Availability Configuration section. Add ability to delete an HA configuration.
- You can select the active or standby Director node to add static routes when you select Administration > Static Routes. Remove Next-Hop IP Address and Next-Hop Interface fields from the Add Static Route screen.
- The License screen displays additional details such as mode, days elapsed, and days remaining. You can download the node ID binary file and edit the license to upload license key.
- In Release 22.1.2, add System > Settings in the left menu bar and move System > Southbound IP Addresses, System > Stolen Branch Setting, System > Secure Upload Setting, System > Timezone Setting, and System > Proxy Setting items in the left menu bar to System > Settings.
- In Release 22.1.4, you can configure authentication for NTP by creating an authentication key, using either MD5 or SHA1.
- In Releases 22.1.x and later, neutral terms have replaced master, slave, arrived, and died instances in the HA UI. The renamed terms are active, standby, online, and offline; except for "designated master," which will remain in the NCS CLI, REST API responses, as well as other non-UI references.
- Release 23.1.1 adds support for the sha256, sha384, and sha512 NTP authentication key types.
Additional Information
Configure Single Sign-On Using Director
Firewall Requirements
