Configure Single Sign-On Using Director
![]() For supported software information, click here.
For supported software information, click here.
This article describes how to configure single sign-on (SSO) on Director nodes.
SSO is a session and user authentication service that allows a user to use a single set of login credentials to access multiple applications. The service authenticates all the applications for which the user has the required rights and eliminates further prompts when you switch applications during the same session. On the backend, SSO logs user activities and monitors user accounts. In the context of Versa Director, the service provider offers SSO as a login mechanism to different integrators and clients.
For SSO, Versa Director supports the following:
- Security Assertion Markup Language—SAML is an XML-based, open standard data format for exchanging authentication data and authorization data between an identity provider and a service provider.
- OpenID connect SSO methods
Versa Director enables identity provider (IdP)-based and local user authentication.
Versa Director supports two types of SSO:
- Service provider (SP)-initiated SSO—Allows you to access the Versa Director when you click on the Login with Single Sign-On link on the Director login page. This redirects you to the IdP page for authentication and then redirects you to the Director node.
- IdP-initiated SSO— Allows you to access Versa Director after authenticating on the customer's portal and redirects you directly to the Director node.
Director and Analytics SSO have been tested tested with the ADFS, Okta, OneLogin, and Ping Identity IdPs.
To configure SSO on a Director node, you do the following:
- Configure Director SP-initiated SSO, or configure Director IdP-initiated SSO.
- Configure an IdP.
- Access the Director node using SSO.
For SSO to work properly, you must enable clock synchronization on the Director node. For more information, see Configure an NTP Server and Configure the Time Zone in Configure Systemwide Functions.
Configure SAML-Based SSO
A service provider–initiated SSO flow operation is started from the service provider and is performed in the following sequence:
- The service provider creates an authentication request and redirects you to the IdP.
- The IdP requests your credentials, validates you, and redirects you to service provider with the login response.
- The service provider validates the login response and, if the validation is successful, logs you in.
An IdP-initiated SSO flow operation is started from the IdP and is performed in the following sequence:
- The IdP creates an SSO response.
- The IdP redirects you to the service provider with the login response.
- The service provider validates the login response and, if the validation is successful, provides access to the requested resource.
Configure Service Provider–Initiated SSO
- In Director view, select the Administration tab in the top menu bar.
- Select System > SSO in the left menu bar. The main pane displays the SSO details.
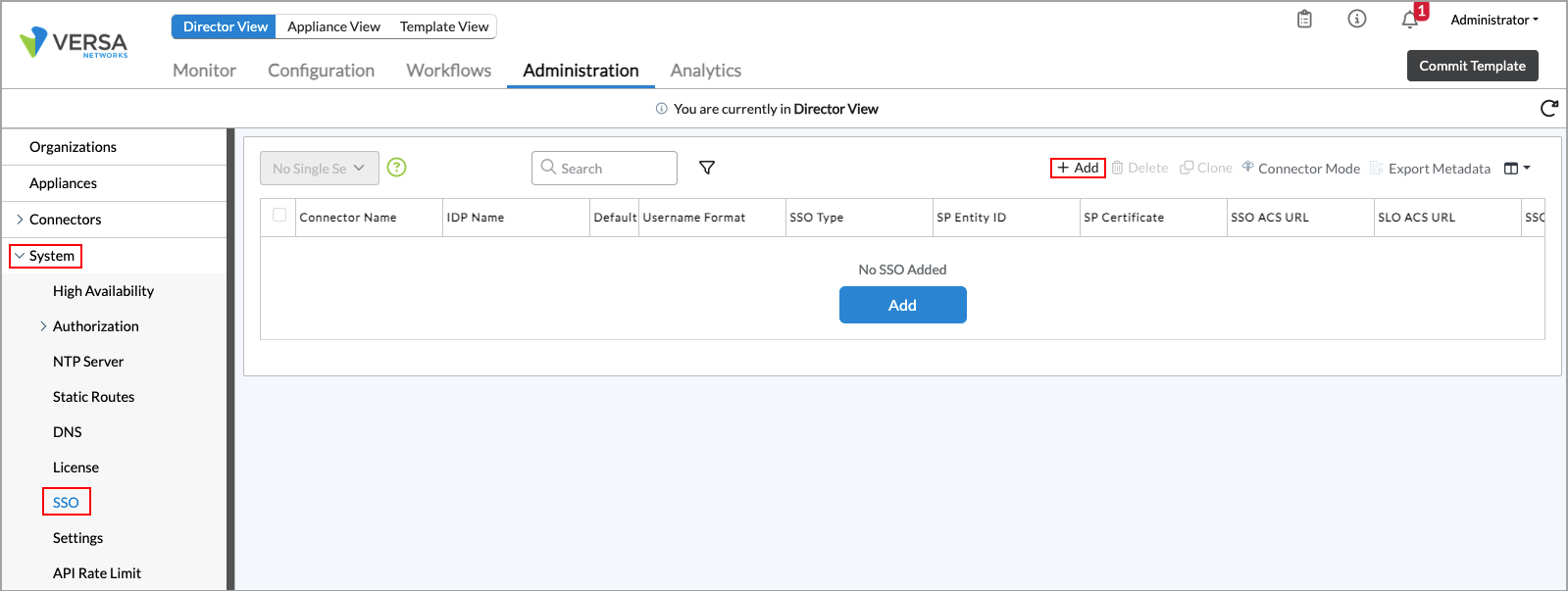
- Click the
 Add icon to modify the SSO configuration and add IdP metadata and other configurations required to configure the SSO. In the Add SSO popup window, enter information for the following fields.
Add icon to modify the SSO configuration and add IdP metadata and other configurations required to configure the SSO. In the Add SSO popup window, enter information for the following fields.

Field Description Connector Name (Required) Enter a name for the connector. IDP Name (Required) Enter a name for the IdP service. Organization Select an organization. SSO-Initiated Type Select the single sign-on initiator:
- All
- IdP Initiated
- SP Initiated
SSO Type Select the SSO markup language:
- SAML-based SSO
SSO Signout Type Enter the SSO signout type:
- IdP
- Local
Username Format (For Releases 22.1.2 and later.) Enter the format for the username:
- String
Versa Director FQDN/IP Address (Required) Enter the FQDN or IP address of the Director host. SP EntityID Enter the URL that identifies the authentication request, for example, http://versa-networks.com/sp. Force Auth Required (For Release 22.1.4 (Service Release dated 2026-02-24.)) Select to force the user to authenticate on every login. Auth Context Required (Group of Fields) (For Releases 22.1.3 and later.) Click to enable authentication context details such as authentication type and comparison method.
Note: If you require stronger authentication methods, such as FIDO multi-factor authentication, disable the Auth Context Required option. For more information, see Enable SSO for FIDO Multi-Factor Authentication.
- Authentication Type
Enter the type of authentication that the IdP is using. The PasswordProtectedTransport class applies when a principal authenticates to an authentication authority through the presentation of a password over a protected session.
Default: urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
- Auth Context Comparison
Enter Exact for the authentication context comparison. Logout Success Redirect URL Enter the URL to be redirected to when the logout is success successful. IDP Metadata XML Click Browse, and then select the IdP metadata, in this case, Okta. For more information, see Configure an IdP, below. IDP Metadata XML Click Browse, and then select the IdP metadata, in this case, Okta. For more information, see Configure an IdP, below. SSO Enabled Click to enable SSO. Analytics Client (Tab) 
- Versa Analytics IP/FQDN
Enter the IP address of the Analytics node, and then click the  Add icon.
Add icon.- Versa Analytics Application ID
Enter the Analytics application ID, and then click the
 Add icon. To determine the Analytics application ID, select the Analytics tab in the top menu bar, and then select Administration > Version in the left menu bar.
Add icon. To determine the Analytics application ID, select the Analytics tab in the top menu bar, and then select Administration > Version in the left menu bar.

For example, here, the application ID is 7c530b:

SSO User Attributes (Tab) 
Enter the attribute name, which is configured in the IdP. - Organization
Enter the organization name, which is configured in the IdP. - Roles
Enter the role, which is configured in the IdP. - Idle Timeout
Enter the idle timeout, which is configured in the IdP. - Concerto Role
(For Releases 22.1.2 and later.) Enter the name of the Concerto role, which is configured in the IdP. Director Client (Tab) 
- Director IP/FQDN
Enter the IP address of the FQDN of the Director client. - Hostname
Enter the hostname of the Director client (for central authorization only). Concerto Client (Tab) 
- Concerto IP/FQDN
Enter the IP address of the FQDN of the Concerto client. - Concerto Application ID
Enter Concerto. Metadata (Tab) 
- Click OK. The main pane displays the IdP details that the service provider requires for SSO.
For service provider–initiated SSO, configure the IdP with the service provider–related details, as described in Configure an IDP, below.
For IdP-initiated SSO, you are redirected to the Director login page. The login page does not display the login with the SSO link on it.
Configure an IdP
To generate the IdP metadata, you must first configure, or partially configure, basic details about the IdP. The following procedure shows an example of how to configure an IdP using Okta:
- Configure the IdP using the details generated in the previous section. Check for the following four values in the certificate: SSO ACS URL, SLO ACS URL, SP Entity ID, and SP Certificate.

Note: When you use an IdP-initiated authentication flow, RelayState mapping is required to complete the IdP-initiated configuration. The default relay state for enabling SSO in the parent organization is vd-ui::system, and for enabling SSO in any tenant organization it is vd-ui::TENANT1.
- To add users in the IdP, enter information for the following fields in the Edit User Assignment window. A user is classified as either a Provider User or a Tenant User.
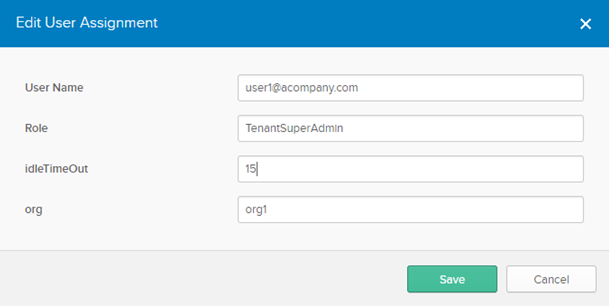
Field Description Username Enter a name for the provider or tenant user. Role Enter the role for the provider or tenant user. The screenshot above show a tenant user with the TenantSuperAdmin role. Idle Timeout Enter the session idle timeout limit for the provider or tenant user. Org For a tenant user only, enter the organization name.
- Click Save to commit the IdP configuration. You can now access the Versa Director page with the single sign-on option in it. For more information, see Access a Director Using Service Provider-Initiated SSO, below.
Access a Director Node Using Service Provider–Initiated SSO
If you enable the SSO Enabled option in the Edit SSO popup window, the Director login page displays the Login with Single Sign-On link.
To access a Director node using SSO:
- On the Director login page, click Login with Single Sign-On. The IdP (Okta) login page displays.

- On the IdP (Okta) login page, enter your credentials and then click Sign In.

IdP validates your credentials and then displays the Director home page.

If a certificate issue occurs while the SAML login request is being verified, and if the certificate has expired, regenerate the SSO certificate on the Director node:
- Regenerate the SSO certificate. Note that you should type this command on a single line.
# sudo openssl req -newkey rsa:2048 -nodes -keyout vnms_sso_private.key -x509 -days 365 -out vnms_sso_public.crt -subj "/CN=director-hostname/O=organization-name/OU=organizational-unit-name/C=country/ST=state or province/L=location"
For example:
# sudo openssl req -newkey rsa:2048 -nodes -keyout vnms_sso_private.key -x509 -days 365 -out vnms_sso_public.crt -subj "/CN=vm/O=versa-networks/OU=VersaDirector/C=US/ST=California/L=Santa Clara"
- Copy the generated vnms_sso_public.crt certificate to the /var/versa/vnms/data/certs directory.
- Upload the vnms_sso_public.crt certificate to the IdP, as described in Configure an IDP, above.
Configure Role Mapping
When the customer portal roles are different from the Director roles, you can map the customer portal roles to the Director roles.
To configure role mapping:
- In Director view, select the Administration tab in the top menu bar.
- Select Director User Management > Roles Mapping in the left menu bar. The main pane displays the existing roles of the provider and tenant users.

- In the Provider User Roles pane, click the
 Edit icon to map Director roles with provider roles. The Edit Provider User Roles popup window displays. Select the customer custom role defined in the IdP, select the Director role to map to, and then click the
Edit icon to map Director roles with provider roles. The Edit Provider User Roles popup window displays. Select the customer custom role defined in the IdP, select the Director role to map to, and then click the  Add icon.
Add icon.
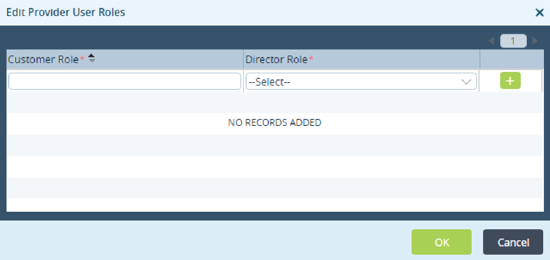
- Click OK.
- In the Tenant User Roles pane, click the
 Edit icon to map Director roles with tenant roles. The Edit Tenant User Roles popup window displays. Select the customer custom role defined in the IdP, select the Director role to map to, and then click the
Edit icon to map Director roles with tenant roles. The Edit Tenant User Roles popup window displays. Select the customer custom role defined in the IdP, select the Director role to map to, and then click the  Add icon.
Add icon.

- Click OK.
Configure OpenID-Based SSO Using Okta
- Create an account at www.okta.com.
- Log in to Okta with your credentials.
- Select the Applications tab in the top menu bar, and then click Add Application to create a new OpenID Connect application.

- Click Create New App to create a new OpenID application. The Create New Application Integration page displays.

- Select OpenID Connect, and then click Create. The Create OpenID Connect Integration page displays.

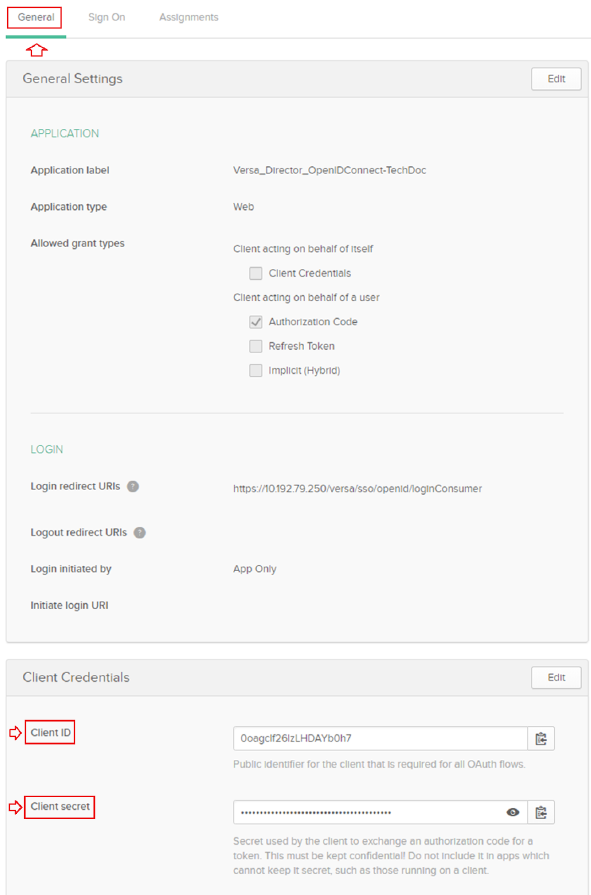
- On the Create OpenID Connect Integration page, enter information for the following fields.
Field Description General Setting (Group of Fields) - Application Name
Enter a name for the OpenID Connect application. - Application Logo
Browse and select a logo to represent the OpenID Connect. Configure OpenID Connect (Group of Fields) - Login Redirect URIs
Enter the URI to which Okta sends OAuth responses. - Logout Redirect URIs
Enter the URI to which Okta sends relying party-initiated logouts. - Click Save.
- Select General tab on the new OpenID Connect preview page, and then copy the Client ID and Client Secret keys from the Client Credentials section.
- Select Directory > Profile Editor in the top menu bar, and then select the newly created OpenID Connect to add custom attributes.
- Select Apps > Newly Created OpenID Connect > Profile on the Profile Editor page.

- Select Add Attribute on the next page that displays.
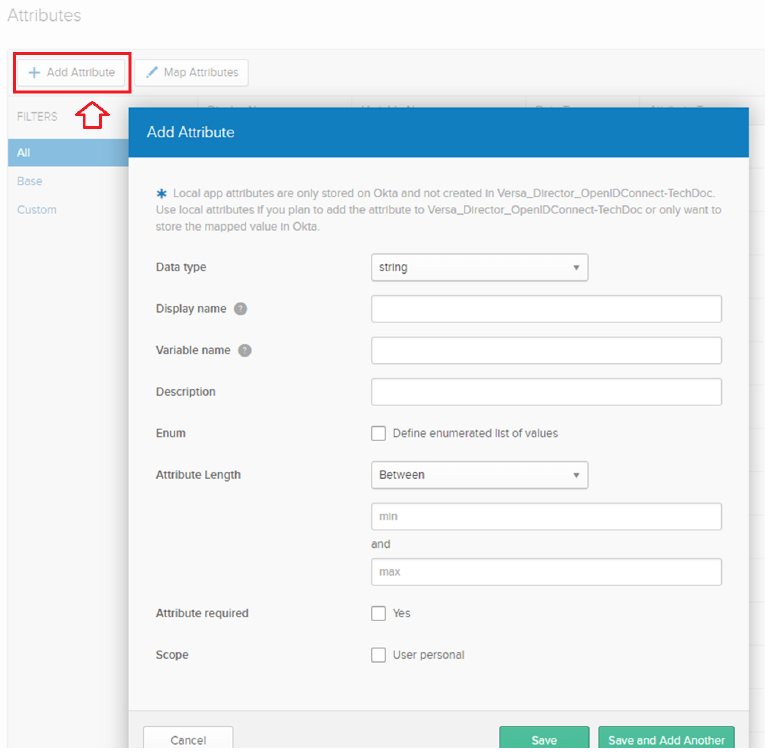
- In the Add Attribute popup window, add roles, organization, and idle timeout attributes. These display in the attribute dashboard.

- Select Apps > Newly Created OpenID Connect > Profile on the Profile Editor page.
- In the top menu bar, select Applications > Applications > Newly Created OpenID Connect to assign users to the Versa Director.

- Select Assign > Assign to People in the next page that displays.

- Select a person, and click Assign.
- In the preview page that displays next, enter the roles, organization, and idle timeout for the assigned user. Then click Save and Go Back.

- Select Assign > Assign to People in the next page that displays.
- On the Director node, select the Administration tab in the top menu bar, and then select System > SSO in the left menu bar. Click the
 Edit icon to modify the SSO configuration.
Edit icon to modify the SSO configuration.

- In the Edit SSO popup window, enter information for the following fields.

Field Description SSO-Initiated Type Select IdP Initiated. SSO Type Select OpenID. Authorize Endpoint Enter your account domain's authorized endpoint. Token Endpoint Enter your account domain's token endpoint. User Information Endpoint Enter your account domain's user information endpoint. Revoke Endpoint Enter your account domain's revocation endpoint. Client ID Enter the client identifier you obtained when you created the OpenID Connect application. Client Secret Enter the client password you obtained when you created the OpenID Connect application. - Click OK.
- Log out from the Director node, and then log in again using SSO.
Export SSO Configuration Metadata
For Releases 21.1 and later.
Some IdP providers need the SSO configuration metadata from the Versa Director so that they can configure their side of the connection. You can export the SSO metadata in XML format. If the IdP provider needs the metadata in JSON format, you can use an XML-to-JSON converter to convert the metadata.
To export the SSO configuration metadata from a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select System > SSO in the left menu bar.
- In the main pane, click to select the IdP provider record.

- Click the
 Export Metadata icon.
Export Metadata icon. - Select the location to which to download the XML file.
- Click OK.
Limitations
The following are the limitations for configuring SSO using Director:
-
A provider user who has the ProviderDataCenterSystemAdmin role and who is logged into the Director node using SSO cannot open a shell-in-a box on the Director node
Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 21.1 add support for exporting SSO configuration metadata.
- Release 22.1.2 supports additional fields in the Add SSO UI screen.
- Release 22.1.4 (Service Release dated 2026-02-24) and later adds a Force Auth Required field to the SAML connector configuration.
