Upgrade Software on Headend and Branch
![]() For supported software information, click here.
For supported software information, click here.
This article describes how to upgrade the software on the headend components—the Director, the Analytics, and the Controller nodes—and on Versa Operating SystemTM (VOSTM) branch devices.
When you upgrade the software on the headend components, you must ensure that at the end of the upgrade process, the same software version is running on all the headend components. The software running on VOS branch devices can be the same version as that running on the headend components, or it can be a lower (earlier) version.
To ensure that the software upgrade proceeds smoothly and to ensure minimum disruption to an operational network, perform a software upgrade in the following order. If you are upgrading the software on the headend components only and not on any of the VOS hub or branch devices, you can ignore the steps that apply to hub or branch VOS devices.
If you are upgrading to Release 22.1.4, you must upgrade the Analytics node first, then upgrade the Director node. If you are upgrading to an earlier release (22.1.3 or earlier), upgrade the Director node first, then upgrade the Analytics node.
- Upgrade the Analytics node—Upgrade the Analytics node. Note that the Analytics log files are automatically archived.
- Upgrade the Director node—Make a full backup of the Director node. Then upgrade the standalone node or the HA-enabled nodes.
- Upgrade the Controller node—A Controller node is simply a VOS device acting as a Controller, so the Controller software upgrade procedure is the same as for upgrading a VOS device. In a multicontroller environment, start by upgrading only one of the Controller nodes.
- For a hub-and-spoke topology, upgrade the active hub, following the VOS upgrade procedure.
- For branch sites that have redundant (HA) VOS devices, upgrade the active VOS device at each site.
- Upgrade the remaining Controller nodes.
- For a hub-and-spoke topology, upgrade the remaining hubs.
- Upgrade the remaining branch VOS devices.
- Check that the upgrade Director node can connect to and manage branches that are running the same software version as the Director node.
- Check that the upgraded Director node can connect to and manage existing branches that are running a software version that is older than the software running on the Director node.
- Check that VOS devices whose software you have upgraded can communicate with the branches whose software has not been upgraded.
Before you begin a software upgrade, check the release notes for the software release to which you are upgrading to determine whether you need to perform any additional steps before or during the upgrade. For example, for some upgrades you may need to install OS SPacks before beginning the upgrade.
To find the link to the latest software, go to the Versa Networks Customer Support website and then select the General > SD-WAN Software folder.
Note that to upgrade the software on headend components, you can upgrade from and to the same Ubuntu base operating system. That is, you can upgrade components running Ubuntu 18.04 (Bionic) to another Bionic image, and you can upgrade components running Ubuntu 14.04 (Trusty) to another Trusty image.
Note that if a power interruption occurs during the software upgrade process, the affected device may end up in an inconsistent state, and manual intervention would likely be required to recover. For assistance, you can contact Versa Networks Customer Support.
Upgrade a Standalone Director Node
This section describes how to upgrade the software on a standalone Director node. Before you upgrade the software, you must do the following:
- Perform a full backup of the Director node.
- Download the latest OS security packages (OS SPacks) to the Director node.
- Run an upgrade validation script to identify all the configuration discrepancies and fix them before the upgrade.
Then you upload the software image to the Director node and you upgrade the software.
To install or upgrade to the Director software for Releases 21.2 and later, the Director node, whether a virtual machine (VM) or a bare-metal server, must have a minimum of 150 GB of disk space.
Back Up the Director Node
Before you upgrade the Director software, make a full backup of the Director node:
admin@Director$ cli admin@Director> request system recovery backup admin@Director> exit admin@Director$
Download the Latest OS SPacks
Before you upgrade to Release 21.2 or later, you must upgrade the OS security package (OS SPack) on the Director node to the latest version. You can find the latest OS SPacks at https://versanetworks.app.box.com/v/osspack or https://upload.versa-networks.com/index.php/s/nEkF9xOO3e7BA9Z. If you do not upgrade the OS SPack, the software upgrade may fail.
To install the OS SPack:
admin@Director$ chmod +x ./versa-director-osspack-date.bin admin@Director$ sudo ./versa-director-osspack-date.bin
Validate the Director Node Configuration
Before you upgrade, you must install a validation script on the Director node to identify all configuration discrepancies and fix them before you upgrade the Director node. To create the validation script, you download and run the versa-director-pre-upgrade-check.bin file, which creates the validation script, validate.py. Then, you run the validation script from the active Director node.
Upgrading to Release 22.1
To install and run the upgrade validation script:
- Download the versa-director-pre-upgrade-check.bin script from the Versa Director software release folder.
- Run the script from the Director Linux shell. This script creates the validation script, validate.py, and places it in the /opt/versa/vnms/upgrade/scripts directory.
admin@Director$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director$ sudo ./versa-director-pre-upgrade-check.bin
- To run the validation script from the Director node, use either one of the following methods:
-
Place the target Director image to which you want to upgrade in the /var/versa/packages/vnms directory. Then, execute the validate.py script using the bin file name as the argument for the -n flag.
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -n target-director-image.bin
For example:
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -n versa-director-20250501-043503-baf2125-22.1.4-B.bin
-
Execute the validate.py script using the current major version as the argument for the -f flag, and the target major version to which you want to upgrade as the argument for the -t flag.
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -f current-major-version -t target-major-version
For example, to upgrade from Release 21.2 to Release 22.1:
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -f 21.2 -t 22.1
-
Upgrading to Release 21.2 or earlier
To install and run the upgrade validation script:
- Download the versa-director-pre-upgrade-check.bin script from the Versa Director software release folder.
- Run the script from the Director Linux shell. This script creates the validation script, validate.py, and places it in the /opt/versa/vnms/upgrade/scripts directory.
admin@Director$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director$ sudo ./versa-director-pre-upgrade-check.bin
- To run the validation script from the Director node, issue the following command:
admin@Director$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f current-release -t new-release
For example, to upgrade from Release 21.1 to Release 21.2:
admin@Director$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f 21.1 -t 21.2
Verification
If the validation script is successful, the console shows the following output:
INFO - Pre-Upgrade Validation Initiated INFO - Executing validation script: ha-pair-config-validation.py ... INFO - Successfully executed ha-pair-config-validation.py INFO - Executing validation script: auth-connector-validation.lua ... INFO - Successfully executed auth-connector-validation.lua INFO - Executing validation script: org-validation.py ... INFO - Successfully executed org-validation.py INFO - Executing validation script: ip-address-config-validation.py ... INFO - Successfully executed ip-address-config-validation.py
If the validation script identifies incorrect configurations, the script displays error messages on the console and logs details to the /var/log/vnms/upgrade.log file. Fix all the incorrect configurations before you upgrade the software on the Director node.
The following sample console output shows error messages display because of a validation failure:
admin@Director$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f 20.2 -t 21.2 INFO - Pre-Upgrade Validation Initiated Pre-Upgrade Validation Initiated INFO - Executing validation script: auth-connector-validation.lua ... Executing validation script: auth-connector-validation.lua ... ERROR - Errors encountered during execution of auth-connector-validation.lua Errors encountered during execution of auth-connector-validation.lua INFO - Executing validation script: ha-pair-config-validation.py ... Executing validation script: ha-pair-config-validation.py ... INFO - Successfully executed ha-pair-config-validation.py Successfully executed ha-pair-config-validation.py INFO - Executing validation script: org-validation.py ... Executing validation script: org-validation.py ... INFO - Successfully executed org-validation.py Successfully executed org-validation.py INFO - Executing validation script: ip-address-config-validation.py ... Executing validation script: ip-address-config-validation.py ... INFO - Successfully executed ip-address-config-validation.py Successfully executed ip-address-config-validation.py ERROR - Validation failed for following scripts: auth-connector-validation.lua Validation failed for following scripts: auth-connector-validation.lua
The following snippet from the /var/log/vnms/upgrade.log file explains the failure reported by the output above:
13-March-2021, 10:05:10 __main__ [INFO] Executing validation script: auth-connector-validation.lua ... 13-March-2021, 10:05:10 __main__ [DEBUG] Executing command su root -c "source /etc/profile.d/versa-profile.sh && /opt/versa/util/runlua -n confd -e confu /opt/versa/vnms/upgrade/validate/scripts/auth-connector-validation.lua" 13-March-2021, 10:05:10 __main__ [DEBUG] Command Output of auth-connector-validation.lua" is 13-March-2021, 10:05:12 __main__ [DEBUG] DEBUG badly formatted or nonexistent path - Bad path element "radius-server-details" after: /nms/provider/auth-connectors/auth-connector 13-March-2021, 10:05:12 __main__ [DEBUG] secret is not configured for authentication connector Name versaAuth Type radius 13-March-2021, 10:05:12 __main__ [DEBUG] Command exit status/return code is 1 13-March-2021, 10:05:12 __main__ [ERROR] Errors encountered during execution of auth-connector-validation.lua
The validation script runs automatically as the first step in the software upgrade. If the validation fails, the upgrade aborts immediately.
If the following error is displayed while upgrading to Release 21.2 using Versa Director CLI, refer to the validation error mitigation guide or contact Versa Networks Customer Support:
admin@Director> request system package upgrade package-name Will restart Versa Director (all processes). Are you sure? [no,yes] yes Pre-Upgrade Validation Initiated Executing validation script: org-validation.py … Successfully executed org-validation.py Executing validation script: ip-address-config-validation.py … Errors encountered during execution of ip-address-config-validation.py Executing validation script: auth-connector-validation.lua … Successfully executed auth-connector-validation.lua Executing validation script: ha-pair-config-validation.py … Successfully executed ha-pair-config-validation.py Validation failed for following scripts: ip-address-config-validation.py Pre-Upgrade-Validation Failed. Please refer to /var/log/vnms/upgrade.log for more details.
Upgrade the Director Software
Note that if you are prompted to provide the username and password for the peer node while disabling or enabling HA, you must provide credentials for a user with either the ProviderDataCenterSystemAdmin role, or any custom role with the HA_MANAGEMENT privilege and Update action. For standby IP address, use 127.0.0.1 when disabling HA on a standalone Director node; otherwise, use the HA management IP address of the standby Director node.
Using Releases 22.1 and Later
To upgrade a software image file on a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select Inventory > Software Images in the left menu bar.
- Select the Software (VOS/Director) tab, and then select the Director Upgrades tab. The Package Version column in the table displays information about the software package that is installed on the Director node.

- In the Target Version box, in the Select Package to Upgrade field, select the package to which to upgrade the Director node.
- Click Upgrade.
Using Releases 21.2 and Earlier
To upgrade a software image file on a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select System > Director Upgrade in the left menu bar. The main pane display the Director Upgrade pane.

- Click the
 Edit icon. In the Upgrade popup window, select the software package name:
Edit icon. In the Upgrade popup window, select the software package name:

- Click OK.
- Click Upgrade.
Upgrade from the Director CLI
-
Upload the software image to the Director repository. You can do this from the Director CLI or manually.
-
To use the Director CLI, issue the following command.
admin@Director> request system package fetch uri url
For example:
admin@Director> request system package fetch uri http://10.167.57.1/Builds/VOAE/21.2.2/versa-director-20151126-094545-a532d5d-21.2.2.bin status Package Saved
-
To upgrade manually:
-
Upload the Director image using the scp (ssh) command from your Linux or Mac device.
scp versa-director-20xxxxxxxxx.bin Administrator@
director-ip-address: For example:
scp versa-director-2020240208-092811-0583692-22.1.3-B.bin Administrator@1.2.3.4:
-
Move the image to the directory that contains the Versa Director images. For example:
mv versa-director-20240208-092811-0583692-22.1.3-B.bin /var/versa/packages/vnms/
-
-
-
Verify that the software image has been uploaded:
admin@Director> request system package list
For example:
admin@Director> request system package list
packages
{
name versa-director-20151126-002132-0ebe99d-21.2.2.bin
}
packages
{
name versa-director-20151126-094545-a532d5d-21.2.2.bin
}
-
Upgrade the software:
admin@Director> request system upgrade package image-filename Will restart Director (all processes). Are you sure? [no,yes] yes
For example:
admin@Director> request system upgrade package versa-director-20151126-094545-a532d5d-21.2.2.bin Will restart Director (all processes). Are you sure? [no,yes] yes
To monitor the progress of the software upgrade, issue the following command:
admin@Director$ tail -f /var/log/vnms/upgrade.log
Note: While the upgrade is in progress, you may see a message that a system reboot is required. You must wait until the upgrade process is completed before you reboot the system. When the upgrade is completed, the screen output displays a message that the upgrade was successful, as shown in the following sample output:
27–April-2024, 10:05:12 __main__ [INFO] Upgrade to director-director-201210910-171209.bin successful!
When the upgrade is completed, reboot the standalone Director node.
Upgrade HA-Enabled Director Nodes
This section describes how to upgrade HA-enabled Director nodes.
Before you update the Versa Director software on HA-enabled nodes, you must perform the following tasks:
- Disable HA. You must do this before upgrading the Director software from any version to any other minor or major version, and then re-enable it after the upgrade of both the active and standby Director nodes.
- Perform a full backup of the Director software.
- Verify that the active and standby Director nodes are operating in standalone mode (HA is disabled on both nodes).
- (For Releases 22.1.4 and later.) Check status of secure-mode on both nodes using the CLI command request system secure-mode status.
- If secure-mode is enabled on any node, disable secure-mode before starting the upgrade from Release 22.x to Release 23.x using the CLI command request system secure-mode disable.
- After the upgrade completes, re-enable secure-mode using the CLI command request system secure-mode enable.
- Download the latest OS security packages (OS SPacks) on the primary and standby Director nodes.
- Run an upgrade validation script to identify all the configuration discrepancies and fix them before the upgrade.
- (For Releases 22.1.4 and later.) Ensure that port 9182 is open and accessible from the HA management IP address of the peer Director node.
To install or upgrade to the Director software for Releases 21.2 and later, each Director node, whether a virtual machine (VM) or a bare-metal server, must have a minimum of 150 GB of disk space.
Disable HA
Before you upgrade, you must disable HA on both the primary and standby Director nodes.
To disable HA:
- In Director view, go to the Administration tab in the top menu.
- Select System > High Availability in the left navigation bar.

- Click the Disable HA button in the High Availability Configuration pane.
- In the Disable High Availability popup window, enter information for the following fields.

Field Description IP Address (Required) Enter the API end point IP address of the standby Director node. Username (Required) Enter the username for the standby Director. The user must have the ProviderDataCenterSystemAdmin role or a custom role with the 'HA_MANAGEMENT' privilege and Update action configured. Password (Required) Enter the password for the standby Director.
The High Availability pane shows that High Availability is disabled.

Enable HA
To enable HA:
- In the High Availability Configuration pane, click the Enable HA button.
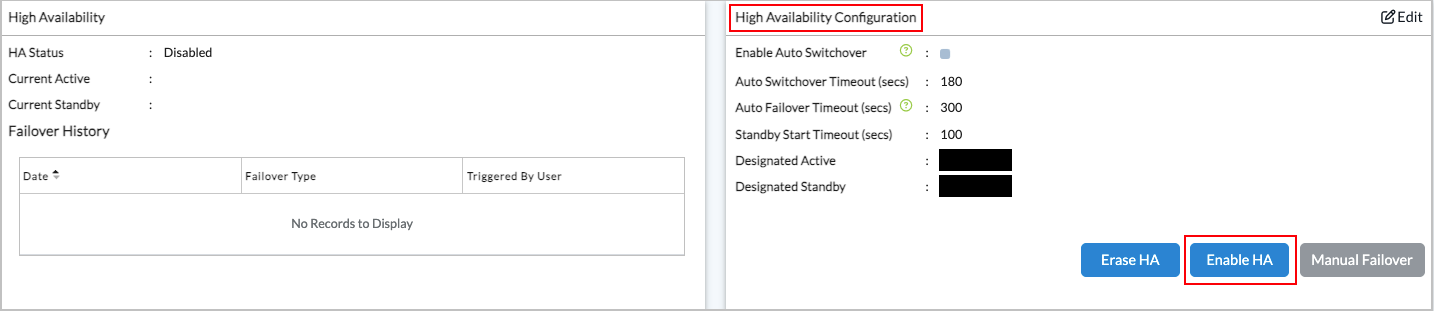
The Enable High Availability popup window displays.

- Enter the Standby Director UI credentials in the following fields.
Field Description IP Address (Required) Enter the API end point IP address of the standby Director node. Username (Required) Enter the username for the standby Director. The user must have the ProviderDataCenterSystemAdmin role or a custom role with the 'HA_MANAGEMENT' privilege and Update action configured. Password (Required) Enter the password for the standby Director.
- Click OK. A progress bar displays the progress of the enable operation.

Back Up the Director Node
Before you upgrade the Director software, make a full backup of the Director node:
admin@Director1> request system recovery backup
Verify the Director Node Operating Mode
To verify that the primary (active) and standby Director nodes are operating in the proper modes and that HA is enabled:
-
Ensure that the same software version is running on the primary and standby Director nodes:
admin@Director1> show system package-info admin@Director2> show system package-info
-
Check that the primary Director node is in master mode. In the following example, the line "mode master" under "vnmsha-details" indicates that the primary Director is in master mode. (The "mode slave" line under "peer-vnmsha-details" shows the mode for the peer Director node, which is the standby.)
admin@Director1> request vnmsha actions get-vnmsha-details fetch-peer-vnmsha-details true status SUCCESS vnmsha-details { mgmt-ip-address 10.192.36.170 enabled true designated-master true mode master peer-vnmsha-details { peer-vnmsha-detail { mgmt-ip-address 10.192.36.171 enabled true designated-master false mode slave } } }
You can also check the Director mode by issuing the following command:
admin@Director1> request vnmsha actions get-vnmsha-postgres-status
The Role column in the command output shows "primary" for the primary Director node. For example:
admin@Director1> request vnmsha actions get-vnmsha-postgres-status status ID | Name | Role | Status | Upstream | Location | Connection string ----------+-------------------+-----------+-------------+-----------------+----------+--------------------------------------------- 1 | director-node1 | primary | * running | | default | host=10.192.36.170 user=repmgr dbname=repmgr 2 | director-node2 | standby | running | director-node1 | default | host=10.192.36.171 user=repmgr dbname=repmgr
-
Check that the standby Director node is in slave mode. In the following example, the line "mode slave" under "vnmsha-details" indicates that the standby Director node is in slave mode. (The "mode master" line under "peer-vnmsha-details" shows the mode for the peer Director node, which is the primary.)
admin@Director2> request vnmsha actions get-vnmsha-details fetch-peer-vnmsha-details true status SUCCESS vnmsha-details { mgmt-ip-address 10.192.36.171 enabled true designated-master false mode slave peer-vnmsha-details { peer-vnmsha-detail { mgmt-ip-address 10.192.36.170 enabled true designated-master true mode master } } }
You can also check the Director mode by issuing the following command:
admin@Director2> request vnmsha actions get-vnmsha-postgres-status
The Role column in the command output shows "standby" for the standby Director node. For example:
admin@Director2> request vnmsha actions get-vnmsha-postgres-status status ID | Name | Role | Status | Upstream | Location | Connection string ----------+----------------+---------+-----------+----------------+----------+---------------------------------------------- 1 | director-node1 | primary | * running | | default | host=10.192.36.170 user=repmgr dbname=repmgr 2 | director-node2 | standby | running | director-node1 | default | host=10.192.36.171 user=repmgr dbname=repmgr
-
Verify that the primary and standby Director nodes are synchronized:
admin@Director1> request vnmsha actions check-sync-status postgres-status IN_SYNC ncs-status IN_SYNC admin@Director2> request vnmsha actions check-sync-status postgres-status IN_SYNC ncs-status IN_SYNC
Download the Latest OS SPacks
Before you upgrade to Release 21.2 or later, you must upgrade the OS security packages (OS SPacks) on all Director nodes to the latest version. You can find the latest OS SPacks at https://versanetworks.app.box.com/v/osspack or https://upload.versa-networks.com/index.php/s/nEkF9xOO3e7BA9Z. If you do not upgrade the OS SPacks, the software upgrade may fail.
To install the OS SPack:
admin@Director1$ chmod +x ./versa-director-osspack-date.bin admin@Director1$ sudo ./versa-director-osspack-date.bin
For more information about OS Spacks, see Use OS Security Packages.
Validate the Director Node Configuration
Before you upgrade, you must install a validation script on both the active and standby Director nodes to identify all configuration discrepancies and fix them before you upgrade the Director nodes. To create the validation script, you download and run the versa-director-pre-upgrade-check.bin file, which creates the validation script, validate.py. Then, you run the validation script from the active Director node.
Upgrading to Release 22.1
To install and run the upgrade validation script:
- Download the versa-director-pre-upgrade-check.bin script from the Versa Director software release folder.
- Run the script from the Director Linux shell. This script creates the validation script, validate.py, and places it in the /opt/versa/vnms/upgrade/scripts directory.
admin@Director1$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director1$ sudo ./versa-director-pre-upgrade-check.bin admin@Director2$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director2$ sudo ./versa-director-pre-upgrade-check.bin
- To run the validation script from the Director node, use either one of the following methods:
-
Place the target Director image to which you want to upgrade in the /var/versa/packages/vnms directory. Then, execute the validate.py script using the bin file name as the argument for the -n flag.
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -n target-director-image.bin
For example:
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -n versa-director-20250501-043503-baf2125-22.1.4-B.bin
-
Execute the validate.py script using the current major version as the argument for the -f flag, and the target major version to which you want to upgrade as the argument for the -t flag.
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -f current-major-version -t target-major-version
For example, to upgrade from Release 21.2 to Release 22.1:
admin@Director$ sudo -E /opt/versa/vnms/upgrade/scripts/validate.py -f 21.2 -t 22.1
-
Upgrading to Release 21.2 and Earlier
To install and run the upgrade validation script:
- Download the versa-director-pre-upgrade-check.bin script from the Versa Director software release folder.
- Run the script from the Director Linux shell. This script creates the validation script, validate.py, and places it in the /opt/versa/vnms/upgrade/scripts directory.
admin@Director1$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director1$ sudo ./versa-director-pre-upgrade-check.bin admin@Director2$ chmod +x ./versa-director-pre-upgrade-check.bin admin@Director2$ sudo ./versa-director-pre-upgrade-check.bin
- To run the validation script from the active Director node (here, Director1), issue the following command:
admin@Director$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f current-release -t new-release
For example, to upgrade from Release 21.1 to Release 21.2:
admin@Director1$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f 21.1 -t 21.2
Verification
If the validation script is successful, the console shows the following output:
INFO - Pre-Upgrade Validation Initiated INFO - Executing validation script: ha-pair-config-validation.py ... INFO - Successfully executed ha-pair-config-validation.py INFO - Executing validation script: auth-connector-validation.lua ... INFO - Successfully executed auth-connector-validation.lua INFO - Executing validation script: org-validation.py ... INFO - Successfully executed org-validation.py INFO - Executing validation script: ip-address-config-validation.py ... INFO - Successfully executed ip-address-config-validation.py
If the validation script identifies incorrect configurations, the script displays error messages on the console and logs details to the /var/log/vnms/upgrade.log file. Fix all the incorrect configurations before you upgrade the software on the Director nodes.
The following sample console output shows error messages display because of a validation failure:
admin@Director2$ sudo /opt/versa/vnms/upgrade/scripts/validate.py -f 20.2 -t 21.2 INFO - Pre-Upgrade Validation Initiated Pre-Upgrade Validation Initiated INFO - Executing validation script: auth-connector-validation.lua ... Executing validation script: auth-connector-validation.lua ... ERROR - Errors encountered during execution of auth-connector-validation.lua Errors encountered during execution of auth-connector-validation.lua INFO - Executing validation script: ha-pair-config-validation.py ... Executing validation script: ha-pair-config-validation.py ... INFO - Successfully executed ha-pair-config-validation.py Successfully executed ha-pair-config-validation.py INFO - Executing validation script: org-validation.py ... Executing validation script: org-validation.py ... INFO - Successfully executed org-validation.py Successfully executed org-validation.py INFO - Executing validation script: ip-address-config-validation.py ... Executing validation script: ip-address-config-validation.py ... INFO - Successfully executed ip-address-config-validation.py Successfully executed ip-address-config-validation.py ERROR - Validation failed for following scripts: auth-connector-validation.lua Validation failed for following scripts: auth-connector-validation.lua
The following snippet from the /var/log/vnms/upgrade.log file explains the failure reported by the output above:
13-March-2021, 10:05:10 __main__ [INFO] Executing validation script: auth-connector-validation.lua ... 13-March-2021, 10:05:10 __main__ [DEBUG] Executing command su root -c "source /etc/profile.d/versa-profile.sh && /opt/versa/util/runlua -n confd -e confu /opt/versa/vnms/upgrade/validate/scripts/auth-connector-validation.lua" 13-March-2021, 10:05:10 __main__ [DEBUG] Command Output of auth-connector-validation.lua" is 13-March-2021, 10:05:12 __main__ [DEBUG] DEBUG badly formatted or nonexistent path - Bad path element "radius-server-details" after: /nms/provider/auth-connectors/auth-connector 13-March-2021, 10:05:12 __main__ [DEBUG] secret is not configured for authentication connector Name versaAuth Type radius 13-March-2021, 10:05:12 __main__ [DEBUG] Command exit status/return code is 1 13-March-2021, 10:05:12 __main__ [ERROR] Errors encountered during execution of auth-connector-validation.lua
The validation script runs automatically as the first step in the software upgrade. If the validation fails, the upgrade aborts immediately.
If the following error is displayed while upgrading to Release 21.2 using Versa Director CLI, refer to the validation error mitigation guide or contact Versa Networks Customer Support:
admin@Director> request system package upgrade package-name Will restart Versa Director (all processes). Are you sure? [no,yes] yes Pre-Upgrade Validation Initiated Executing validation script: org-validation.py … Successfully executed org-validation.py Executing validation script: ip-address-config-validation.py … Errors encountered during execution of ip-address-config-validation.py Executing validation script: auth-connector-validation.lua … Successfully executed auth-connector-validation.lua Executing validation script: ha-pair-config-validation.py … Successfully executed ha-pair-config-validation.py Validation failed for following scripts: ip-address-config-validation.py Pre-Upgrade-Validation Failed. Please refer to /var/log/vnms/upgrade.log for more details.
Upgrade the Director Software
Upgrade both standalone Director nodes. See Upgrade the Director Software, above.
Upgrade Analytics Clusters
You can upgrade the software for an Analytics cluster using the following methods:
- Director UI workflow—(Releases 23.1.1 and later.) You upgrade the cluster through a workflow in the Director UI.
- Analytics nodes—You upgrade each node in the cluster individually from the Versa CLI on the node.
Before you upgrade the Analytics software, archive the Analytics log files on every node that collects logs. By default, archiving of log files is enabled when you install the Analytics software.
If you have disabled the automatic log file archiving, or if you want to manually archive the log files, run the following script to archive the log files at the specified time interval:
admin@Analytics$ /opt/versa/scripts/van-scripts/log-archive-start source-directory destination-directory (hourly | daily | weekly)
The archive debug logs are in the file /var/log/versa/versa-log-archive.log.
To disable the manual archiving of log files:
admin@Analytics$ /opt/versa/scripts/van-scripts/log-archive-stop
Upgrade an Analytics Cluster from the Director UI
For Releases 23.1.1 and later.
To upgrade an Analytics cluster from the Director UI:
- In Director view, select Administration in the top menu bar.
- Select Inventory > Software Images in the left menu bar.

- In the main pane, select Software > Package Downloads.
- Click + Add. The Add Software Package popup window displays.

- Enter information for the following fields.
Field Description Package Name (Required) Enter a name for the software package. Description Enter a description for the software package. Product Type (Required) Select Analytics.
Signature Upload Click Browse File and select the signature file to upload.
Bin Package Location Identify the package (.bin file) location using one of the following methods:
- URL—Click URL, and then enter the URL where the package files are located.
- Upload—Click Upload, and then do the following:
- Click Choose File to display a dialog window that is specific to your local system.
- Follow the dialog to select the file to be uploaded.
- Click Upload to copy the software package to the Director inventory.
- In Director view, select Workflows > Infrastructure > Analytics Clusters. The Analytics Clusters table displays.

- Select the Menu icon in the upper right corner of the table.
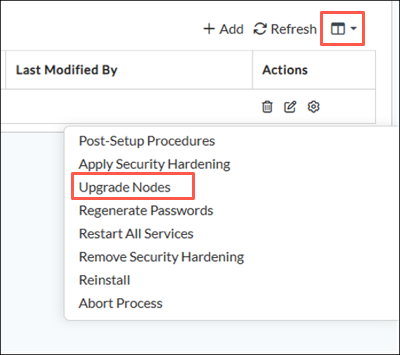
- Select Upgrade Nodes. The Upgrade Nodes window displays.

- Enter information for the following fields.
Field Description Analytics Package Select the Analytics package name from procedure Steps 3 through 5, above. Nodes to Upgrade In the drop-down list, select the Analytics Nodes to be upgraded. -
Click the Run Action icon to upgrade the nodes.
Upgrade an Analytic Cluster from the Versa CLI
Note: For Releases 22.1.4 and earlier, if you are upgrading the nodes in an Analytics cluster, upgrade the analytics-type nodes before you upgrade the search-type nodes. Some of the Versa services may not come up until all database nodes are completely upgraded. Proceed with upgrade of all database nodes of the cluster before ensuring that services are up.
Download the Software Image to the Analytics Nodes
To download the software image to Analytics nodes:
-
Login to the shell on one of the nodes in the Analytics cluster.
-
Copy the software image file to the /home/versa/packages directory using one of the following methods:
-
Download the software image file from the URL.
admin@Analytics$ cli admin@Analytics> request system package fetch uri url filename.bin
-
Download the software image file to a remote host and then use SCP to copy the file to Analytics nodes.
user@Remote-Host$ scp filename.bin admin@Analytics-IP-address:/home/versa/packages
Note that after you upload the software image file, existing configuration-related files, such as /etc/hosts, /etc/network/interfaces, and vansetup.conf, remain unchanged on the Analytics node.
-
- Confirm that the software image file was uploaded:
admin@Analytics> request system package list
Upgrade a Standalone Analytics Node
If you are using a single Analytics node to perform both analysis and search:
-
Run the software image binary file. Note that upgrading the software image restarts the Analytics node.
admin@Analytics> request system package upgrade filename.bin
- Check that the services on the Analytics node have restarted:
admin@Analytics$ vsh status versa-confd is Running versa-lced is Running versa-analytics-driver is Running versa-analytics-app is Running versa-monit is Running
- If the services are not started, issue the following command from the shell:
admin@Analytics$ vsh start
Upgrade an Analytics Cluster
Upgrade the Analytics cluster nodes one at a time. Upgrade the nodes containing the noSQL database first, and then upgrade nodes containing the Analytics search engine.
To upgrade nodes in an Analytics cluster:
- Upgrade a node whose personality is Analytics. Issue the following command from the CLI:
admin@Analytics> request system package upgrade filename.bin
- Check that the services on the Analytics node have restarted. Issue the following command from the shell:
admin@Analytics$ vsh status versa-confd is Running versa-lced is Running versa-analytics-driver is Running versa-analytics-app is Running versa-monit is Running
Note: If the output of vsh status command recommends a reboot, reboot the nodes only after the entire cluster is upgraded. For more information, see Step 7.
- Repeat Steps 1 and 2 for all Analytics node whose personality is Analytics.
- Upgrade a node whose personality is Search:
admin@Analytics2> request system package upgrade filename.bin
- Check that the services on the Analytics node have restarted:
admin@Analytics2$ vsh status versa-confd is Running versa-lced is Running versa-analytics-driver is Running versa-analytics-app is Running versa-monit is Running
Note: If the output of vsh status command recommends a reboot, reboot the nodes only after the entire cluster is upgraded. For more information, see Step 7.
- Repeat Steps 4 and 5 for all Analytics node whose personality is Search.
- In some cases after an upgrade, the output of the vsh status command recommends a reboot of the node, for example, after a kernel upgrade.
If a reboot is recommended, reboot the nodes only after the entire cluster is upgraded. You can reboot these nodes one by one in the same order that you upgraded them. The reboot command varies, depending on the type of Analytics node.
For Analytics-type nodes, reboot by issuing the following command:admin@Analytics$ sudo nodetool drain && sudo reboot
For nodes with personality other than Analytics, reboot by issuing the following command:
admin@Search$ sudo reboot
- Check that all nodes in the Analytics cluster are connected.
- Identify whether the node is running the DSE or Fusion platform.
admin@Analytics$ dse -v dse: command not found
If the command returns returns a version number, such as 4.5 or 4.8, then the node is running the DSE platform. If the command returns an error message, then the platform is Fusion.
- On the DSE platform, issue the command below and verify that the nodes display status UN (Up and Normal).
admin@Analytics$ nodetool status
For example:
admin@Analytics$ nodetool status [sudo] password for Administrator: Note: Ownership information does not include topology; for complete information, specify a keyspace Datacenter: Search ================================================================================= Status=Up/Down |/ State=Normal/Leaving/Joining/Moving -- Address Load Tokens Owns Host ID Rack UN 10.51.24.34 9.73 GB 256 25.8% d640f8d5-45e3-4152-bd9a-1e280973b22b RAC1 UN 10.51.24.33 9.88 GB 256 22.1% dd79fab5-e480-4e84-b8f6-dda4f631de8e RAC1 Datacenter: Analytics ==================================================================================== Status=Up/Down |/ State=Normal/Leaving/Joining/Moving -- Address Load Tokens Owns Host ID Rack UN 10.51.24.43 25.77 GB 256 24.2% 666f6173-1ffc-41e2-a86d-b64b4058a439 RAC1 UN 10.51.24.44 25.76 GB 256 27.9% 2dfb1545-ddea-4a28-adc6-88ae5d16a4e7 RAC1
- On the Fusion platform, issue the following command to verify that the nodes display status UN (Up and Normal).
admin@Analytics$ vsh dbstatus
- If you are upgrading to Release 22.1.4 (Service Release dated 2025-06-27), or any later release, you must migrate your existing Solr collections (search indexes) to match the newer release. To do this, perform the following steps:
- Upgrade the Director node to Release 22.1.4 (Service Release dated June 27, 2025), or any later release. This step is required to obtain an updated version of the van_cluster_installer.py script on the Director node.
- Login to the shell on the Director node.
- Ensure the Director node has connectivity to all search nodes in the Analytics cluster.
- Issue the following command to migrate Solr collections to the newer release.
admin@Director$ sudo /opt/versa/vnms/scripts/van-cluster-config/van_cluster_install/van_cluster_installer.py --post-upgrade
Checks To Perform after an Analytics Upgrade
In Releases 21.2 and later, you cannot access the Versa Analytics application using port 8080, to avoid any security vulnerabilities. By default, only secure ports 443 and 8443 are enabled in Analytics, and port 8443 is used for communication between the Director and Analytics nodes. When you upgrade to Releases 21.2 and later on Director nodes, the upgrade process automatically changes the northbound interface port number 8080 to 8443, and it automatically synchronizes the certificates required for SSL communication between the Analytics and Director nodes.
If there is no communication between the Versa Director and Versa Analytics nodes, perform the following steps:
- Check whether any firewall rule is blocking Versa Director to Versa Analytics communication on port 8443.
- Connect to Versa Analytics directly using https://analytics-ip-address:8443 to determine whether the portal is accessible. This ensures that the application is reachable using a secure port and that the SSL certificate is valid.
- Log in to the Versa Analytics node using the same username and password as the Versa Director node. If the login is successful, this means that RBAC between the Analytics and Director nodes is working using a secure connection. If the login is not successful, install Versa Director certificates on Versa Analytics nodes as described in https://support.versa-networks.com/a/solutions/articles/23000010418.
- Log in to the Versa Director shell and issue the following commands to check whether the Versa Analytics truststore has been created on Versa Director:
admin@Director$ cd /var/versa/vnms/data/certs admin@Director$ ls -tlr versa_analytics_truststore.ts -rw-rw---- 1 versa versa 1274 Jul 30 05:42 versa_analytics_truststore.ts
- If the truststore file does not exist or if the Versa Analytics certificates were regenerated, resynchronize and import the Versa Analytics certificates by running the vd-van-cert-upgrade.sh script in the active Director shell. This script transfers the Versa Analytics certificates from each of the Analytics nodes configured under the connectors and then imports them. You must restart Versa Director for the certificate to take effect.
admin@Director$ sudo su – versa versa@Director$ /opt/versa/vnms/scripts/vd-van-cert-upgrade.sh --pull
For example:
versa@Director$ /opt/versa/vnms/scripts/vd-van-cert-upgrade.sh --pull Pulling Analytics certificates to Director key store Checking previous version config path Changing port for [Analytics] No modifications to commit. Port Migration completed VAN Clusters IPs: [ 10.48.189.23 ] Removing previous analystics cert store Getting Certificate for : 10.48.189.23 depth=0 C = US, ST = California, L = Santa Clara, O = versa-networks, OU = VersaAnalytics, CN = versa-analytics verify error:num=18:self signed certificate verify return:1 depth=0 C = US, ST = California, L = Santa Clara, O = versa-networks, OU = VersaAnalytics, CN = versa-analytics verify return:1 DONE Importing Certificate for : 10.48.189.23 Certificate was added to keystore Certificates Imported... Requires restart.. Do you want to postpone restart (y/N): N [sudo] password for versa: Stopping VNMS service ------------------------------------ Stopping TOMCAT................[Stopped] Stopping REDIS.................[Stopped] Stopping NETBOX-IPAM...........[Stopped] Stopping POSTGRE...............[Stopped] Stopping SPRING-BOOT...........[Stopped] Stopping SPACKMGR..............[Stopped] Stopping NCS...................[Stopped] * Stopping daemon monitor monit Starting VNMS service ------------------------------------ Starting NCS...................[Started] Starting POSTGRE...............[Started] Starting NETBOX-IPAM...........[Started] Starting SPRING-BOOT.......... [Started] Starting REDIS.................[Started] Starting TOMCAT................[Started]
Download Controller and VOS Software Image to Director Node
Before you can upgrade the VOS software on a Director node, on VOS devices, and on Controller nodes, which are simply VOS devices acting in the role of a controller, you download the VOS software image file to the Director node.
Using Releases 22.1 and Later
To download the VOS software image file from the Director software image repository:
- In Director view, select the Administration tab in the top menu bar.
- Select Inventory > Software Images in the left menu bar.
- Select the Software (VOS/Director) tab, and then select the Package Downloads tab. The following screen displays.

- Click the
 Add icon. In the Add Software Package popup window, enter information for the following fields.
Add icon. In the Add Software Package popup window, enter information for the following fields.

Field
Description
Package Name (Required)
Enter the name of the software package.
Description Enter a text description for the software package. Product Type (Required) Select the product type:
- Director—Select for a Director node.
- FlexVNF —Select for a VOS device or Controller node.
Package Location (Group of Fields) Select the location of the software package.
- URL
Click, and then enter the URL in the Path field from which to download the software package. - Upload
Click Browse, and then select the software package file. - Click Upload.
Using Releases 21.2 and Earlier
To download the VOS software image file to the Director software image repository:
- In Director mode, select the Administration tab in the top menu bar.
- Select Inventory > Images in the left menu bar. The following screen displays.

- Click the
 Add icon. In the Add Package popup window, enter information for the following fields:
Add icon. In the Add Package popup window, enter information for the following fields:

Field
Description
Package Name (Required)
Enter the name of the software package.
Description Enter a text description for the software package. CMS Organization
Select the name of the organization to which the Director node belongs.
Image Select Image as the package type. Product Type (Required) Select the product type:
- Director—Select for a Director node.
- FlexVNF —Select for a VOS device or Controller node.
Package Location Click URL to enter the URL from which to download the software package from.
Click Upload to browse for and select the software package file.
Package Location (Group of Fields) Select the location of the software package.
- URL
Click, and then enter the URL in the Path field from which to download the software package. - Upload
Click Browse, and then select the software package file. - Click OK.
Upgrade a Software Image on a VOS Device
For Releases 22.1.1 and later.
You can upgrade the software image on a VOS device from the Inventory > Software Images option as described in this section. You can also upgrade the VOS device software image from the Appliance option, as described in Upgrade the Remaining Controller Nodes, below.
To upgrade a software image on a VOS device:
- In Director view, select the Administration tab in the top menu bar.
- Select Inventory > Software Images in the left menu bar.
- Select the Software (VOS/Director) tab, and then select the Appliance Upgrades tab.

- Select the VOS device or devices on which to upgrade the software, or select the box next to the Appliance Name column to select all devices. The Package Version column in the table displays the current software version installed on the device.
- Click Upgrade Appliances. The Upgrade Appliances Software (Image/Bin) Package popup window displays. Enter information for the following fields.

Field Description OS Type Select Trusty or Bionic CPU Type Select SNB or WSM. Selected Appliances Displays the device or devices you selected to upgrade. Software Package Version (Required) Select the software package from the list of downloaded software packages. Schedule Upgrade (Required) Click to schedule a date and time for the upgrade to occur. Enter the date in the format mm/dd/yyyy (month/date/year), and enter the time in the format hh:mm:ss (hours:minutes:seconds using 12-hour format for the hours), click AM or PM to toggle between the two settings.
Note: If you do not set a schedule for the upgrade, the software package is upgraded immediately.
Upload Only Click to upload the software package without upgrading it. Upgrade App ID Proto Bundle (Release 23.1.1 and later.) Click to upgrade the App ID protocol bundle along with the VOS image, if a newer bundle is included in the image. - Click Upgrade. If you have not set a schedule for upgrade, the software package is upgraded immediately.
Upgrade a Software Image on a Director Node
Using Releases 22.1 and Later
To upgrade a software image file on a Director node:
- In Director view, select the Administration tab in the top menu bar.
- Select Inventory > Software Images in the left menu bar.
- Select the Software (VOS/Director) tab, and then select the Director Upgrades tab. The Package Version column in the table displays information about the software package that is installed on the Director node.

- In the Target Version box, in the Select Package to Upgrade field, select the package to which to upgrade the Director node.
- Click Upgrade.
Using Releases 21.2 and Earlier
To upgrade a software image file on a Director node:
- In Director view, select the Administration tab in the top menu bar
- Select System > Director Upgrade in the left menu bar. The main pane display the Director Upgrade pane.

- Click the
 Edit icon. In the Upgrade popup window, select the software package name.
Edit icon. In the Upgrade popup window, select the software package name.

- Click OK.
- Click Upgrade.
Upgrade the First Controller Node
Using Releases 22.1 and Later
To upgrade the first Controller node:
- Check that the Controller node (or VOS device) status is synchronized and reachable:
- In Director view, select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Check the values in the Status columns in the main pane. Note that you cannot update a device whose state is error or unreachable.

- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a Controller node (or VOS device) from the main pane. The view changes to Appliance view.
- Select Operations in the left menu bar, and click the
 Edit icon in the Upgrade box.
Edit icon in the Upgrade box.

- In the Upgrade popup window, select the software image package name.

- Click OK.
- In the Upgrade box, verify the information about the existing and new VOS software packages.
- Click the
 Upgrade button.
Upgrade button. - Select the name of the software package to which you are upgrading.
- Click OK.
- To track the progress of the software upgrade, click the
 Tasks icon. The Tasks screen displays:
Tasks icon. The Tasks screen displays:

- If you are upgrading a Controller node, wait for services to come up on the node. Then verify that the Controller has connected to the other Controllers, to all branches, and to all hubs if there are any in the network.
Using Releases 21.2 and Earlier
To upgrade the first Controller node:
- Check that the Controller node (or VOS device) status is synchronized and reachable:
- In Director view, select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Check the values in the Status columns in the main pane. Note that you cannot update a device whose state is error or unreachable.

- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the left menu bar.
- Select an organization in the left menu bar.
- Select a Controller node (or VOS device) from the main pane. The view changes to Appliance view.
- Select System > Operations in the left menu bar.

- Click the
 Edit icon in the Upgrade box.
Edit icon in the Upgrade box. - In the Upgrade popup window, select the software image package name.
.png?revision=1)
- Click OK.
- In the Upgrade box, verify the information about the existing and new VOS software packages.
- Click the
 Upgrade button.
Upgrade button. - Select the name of the software package to which you are upgrading.
- Click OK.
- To track the progress of the software upgrade, click the
 Tasks icon. The Tasks screen displays:
Tasks icon. The Tasks screen displays:

- If you are upgrading a Controller node, wait for services to come up on the node. Then verify that the Controller has connected to the other Controllers, to all branches, and to all hubs if there are any in the network.
Upgrade Active Hub Devices
If you are not upgrading the software image on VOS hub devices, you can skip this section.
If you are using a hub-and-spoke topology, and if you have deployed the hub in an active-standby HA pair, upgrade the software on the active hub of the HA pair. Follow the procedure in Upgrade the First Controller Node, above. Then follow the same procedure to upgrade the standby hub.
Upgrade Active HA VOS Branch Devices
If you are not upgrading the software image on VOS devices, you can skip this section.
If any branches have two VOS devices that use an interchassis HA deployment, in which one branch VOS device is the active device and a second is the standby device, upgrade the software on the active VOS devices. Follow the procedure in Upgrade the First Controller Node, above. Then follow the same procedure to upgrade the standby VOS branch device.
Upgrade the Remaining Controller Nodes
To upgrade the remaining Controller nodes (or VOS devices) one at a time, follow the procedure in Upgrade the First Controller Node, above.
If your network has more than two Controller nodes (or more than two VOS devices), you can choose to upgrade them all at once.
Using Releases 22.1 and Later
To upgrade the remaining Controller nodes:
- Check that the Controller or VOS status is synchronized and reachable:
- In Director view, select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Check the values in the Status columns in the main pane. Note that you cannot update a device whose state is error or unreachable.
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select an organization in the left menu bar.
- Select one or more Controller nodes (or VOS devices) in the main pane, and click the
 Upgrade Selected Appliances icon.
Upgrade Selected Appliances icon.

-
In the Upgrade Appliance popup window, enter information for the following fields:

Field Description Package Name (Required) Select the name of the software image package. Schedule Upgrade at Select the date and time to run the automatic appliance upgrade. Upload Only To upload the software image package only but not upgrade the software, select this box.
Leave the box unchecked to upgrade the software image.
- To view the progress of the upgrade process, click the
 Tasks icon.
Tasks icon. - If you are upgrading Controller nodes, wait for services to come up on the nodes. Then verify that each Controller has connected to the other Controllers, to all branches, and to all hubs if there are any in the network.
Using Releases 21.2 and Earlier
To upgrade the remaining Controller nodes:
- Check that the Controller or VOS status is synchronized and reachable:
- In Director view, select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Check the values in the Status columns in the main pane. Note that you cannot update a device whose state is error or unreachable.
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select an organization in the left menu bar.
- Select one or more Controller nodes (or VOS devices) in the main pane, and click the Upgrade Selected Appliances icon.

- Click the
 Upgrade Selected Appliances icon.
Upgrade Selected Appliances icon. -
In the Upgrade Appliance popup window, enter information for the following fields:

Field Description Package Name (Required) Select the name of the software image package. Upload Only To upload the software image package only but not upgrade the software, select this box. To upgrade the software image, leave the box unchecked.
- Click OK.
- To view the progress of the upgrade process, click the
 Tasks icon.
Tasks icon. - If you are upgrading Controller nodes, wait for services to come up on the nodes. Then verify that each Controller node has connected to the other Controller nodes, to all branches, and to all hubs if there are any in the network.
Upgrade the Remaining Hub Devices
If you are not upgrading the software image on VOS hub devices, you can skip this section.
If you are using a hub-and-spoke topology, and if you have deployed the hub in an active-standby HA pair, upgrade the software on the standby hub of the HA pair.
To upgrade the standby hub of the HA pair, or to upgrade hubs one at a time if you have more than two hubs, follow the procedure in Upgrade the First Controller Node, above.
To upgrade the hubs all at once if you have more than two hubs, follow the procedure in Upgrade the Remaining Controller Nodes, above.
Upgrade the Remaining VOS Branch Devices
If you are not upgrading the software image on VOS devices, you can skip this section.
If any branches have two VOS devices that use an interchassis HA deployment, where one branch VOS device is the active device and a second is the standby device, upgrade the software on the standby VOS device.
To upgrate the standby VOS device in an interchassis HA deployment, or to upgrade VOS branch devices one at a time if you have more than two VOS devices. follow the procedure in Upgrade the First Controller Node, above.
To upgrade the VOS branch devices all at once if you have more than two VOS devices, follow the procedure in Upgrade the Remaining Controller Nodes, above.
Check Connectivity Between the Director Nodes and VOS Devices
Check that the upgrade Director node can connect to and manage branches that are running the same software version as the Director node.
Check that the upgraded Director node can connect to and manage existing branches that are running a software version that is older than the software running on the Director node.
Check that VOS devices whose software you have upgraded can communicate with the branches whose software has not been upgraded.
To check communication between the Director node and VOS devices, start by selecting the Monitor tab in the Director top menu bar and selecting a VOS device in the left menu bar.
Change VNMS and Postgres Database Passwords
You can change the VNMS and Postgres database passwords on Versa Director. Before changing the passwords, ensure that HA is disabled and all services on the standalone (designated-active) node are up and running. Note that only the following special characters are allowed in the passwords:
- - (hyphen)
- @ (at sign)
- _ (underscore)
- + (plus sign)
- ^ (circumflex or caret)
- * (asterisk or star)
- . (period)
- , (comma)
To change the password for VNMS and Postgres databases:
- Change the VNMS and Postgres passwords using the following CLI command:
Administrator@versa-director% set nms provider defaults database-credentials password "<password>"
Administrator@versa-director% commit
For example:
Administrator@versa-director% set nms provider defaults database-credentials password "bxXzyHkhgDt8z6SFa37anPeNZzy9lFLQ"
Administrator@versa-director% commit
- Change the Postgres password using the following CLI commands:
Administrator@versa-director$ sudo -u postgres psql -c "ALTER USER vnms WITH PASSWORD '<new_vnms_password>';"
Administrator@versa-director$ sudo -u postgres psql -c "ALTER USER postgres WITH PASSWORD '<new_postgres_password>';"
For example:
Administrator@versa-director$ sudo -u postgres psql -c "ALTER USER vnms WITH PASSWORD 'bxXzyHkhgDt8z6SFa37anPeNZzy9lFLQ';"
Administrator@versa-director$ sudo -u postgres psql -c "ALTER USER postgres WITH PASSWORD 'bxXzyHkhgDt8z6SFa37anPeNZzy9lFLQ';"
- (For Releases 22.1.4 and later.) Restart the Netbox-IPAM service using the following CLI commands:
Administrator@versa-director$ sudo /opt/versa/vnms/scripts/initvnmshelper.sh -a stop-netbox
Administrator@versa-director$ sudo /opt/versa/vnms/scripts/initvnmshelper.sh -a start-netbox
Note that if you are running Release 22.1.4 hotfix image released on or after February 2025, you have the option to use the commands above, or the commands for Releases 22.1.3 and earlier, below.
(For Releases 22.1.3 and earlier.) Delete the Netbox-IPAM docker container using the following CLI commands:
Administrator@versa-director$ sudo docker ps | grep netbox | cut -d " " -f1
Administrator@versa-director$ sudo docker stop <container_id>
For example:
Administrator@versa-director$ sudo docker ps | grep netbox | cut -d " " -f1 [sudo] password for admin: a06ed8025d69
Administrator@versa-director$ sudo docker stop a06ed8025d69
- Start the Netbox-IPAM and spring boot services:
- Start the Netbox-IPAM service using the following CLI command:
Administrator@versa-director$ sudo systemctl restart versa-netbox.service
- Start the spring boot service using the following CLI command:
Administrator@versa-director$ sudo systemctl restart versa-spring-boot.service
Or, restart all Director services using the following CLI command:
Administrator@versa-director$ vsh restart
To check the PostgreSQL password, issue the following CLI command:
Administrator@versa-director$ sudo -u postgres psql -h localhost -d vnms -U vnms
For example:
Administrator@versa-director$ sudo -u postgres psql -h localhost -d vnms -U vnms Password for user vnms: psql (15.3 (Ubuntu 15.3.1.pgdg18.04+1)) Type "help" for help.
Schedule Automatic Software Upgrade
On a Director node, you can schedule software upgrade tasks to occur automatically. In a software upgrade tasks, you can download or upload software to one or more VOS devices at the same time, and you can commit tenant-specific templates. In a single scheduled upgrade task, you can have multiple appliances for an individual job type.
You can edit or cancel an automatic software upgrade at any time. When you edit the task, the changes apply to all the VOS devices in the list of tasks that are in the queue.
The ability to schedule automatic software upgrades uses role-based access control (RBAC), so only users with the authorized role can configure schedule modification. If a scheduling job affects multiple devices and if each device owner tenant is in a different organization, the task is visible only to the owner who has RBAC access to all the devices.
You typically schedule automatic software upgrades during a maintenance window. If a VOS device is not reachable at that time, you can configure pending tasks to resume when the device becomes reachable. If you apply (commit) a template to multiple devices, the prevalidation for the schedule job can take a few minutes to several hours.
If a scheduled software upgrade is in process and a Director HA failover occurs, the scheduled software upgrade fails.
To schedule automatic software upgrade:
- In Director view, select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select one or more Controller nodes or VOS devices in the main pane. Note that you can schedule a software upgrade on multiple Controller nodes or multiple VOS devices in a single job, but you cannot upgrade Controller and VOS devices in the same job.
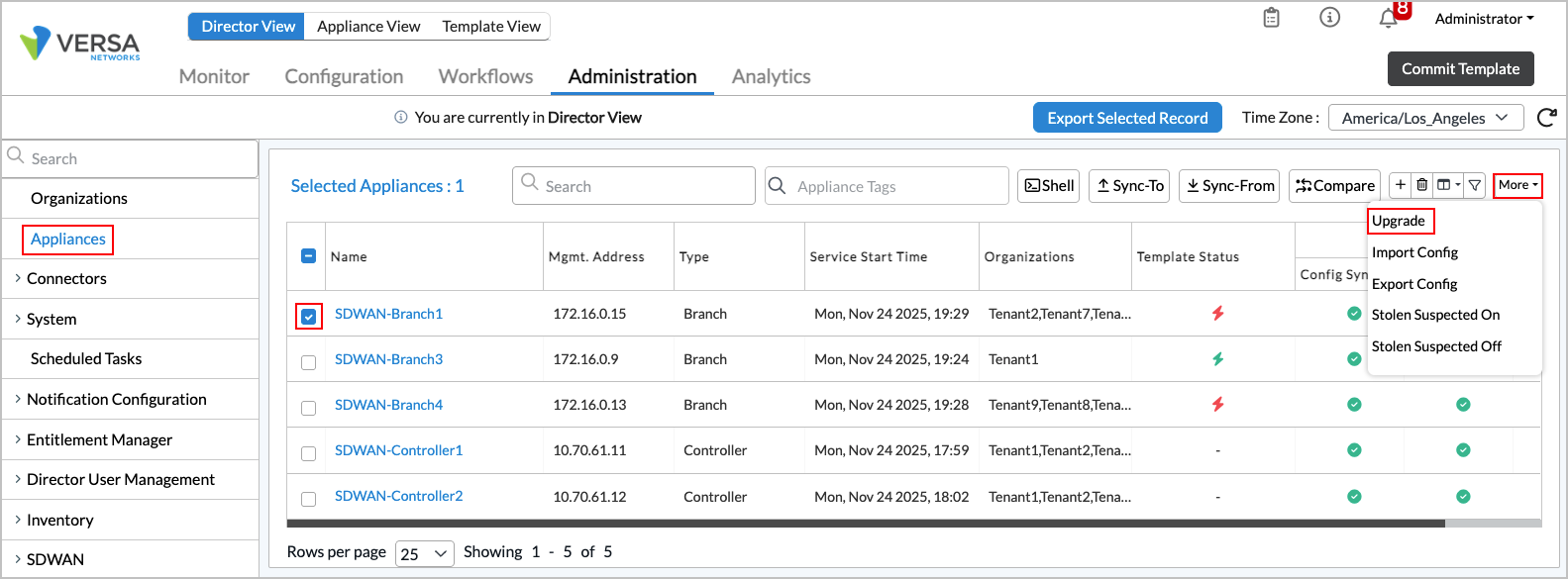
- Click More at the right side of the horizontal submenu, then click Upgrade.
- In the Upgrade Appliance popup window, enter information for the following fields.

Field Description Package Name (Required) Select the name of the software image package. Schedule Upgrade at Click the
 Calendar icon, then select the date and time to run the automatic software update.
Calendar icon, then select the date and time to run the automatic software update.
Upload Only Click to upload the software image package only, but not upgrade the software. To upgrade the software image, leave the box unchecked. This option is disabled by default. Click Reset to return to the default setting.
- Click OK. A popup window confirms the user-initiated task.

- Click the Upgrade: Device bar to open the Tasks status window.
- To view scheduled software upgrade status, select a task.
- To cancel the scheduled software upgrade, click the Delete icon.

To view, edit, or delete a scheduled task:
- In Director view, select the Administration tab in the top menu bar.
- Select Scheduled Tasks in the left menu bar. The table in the main pane displays the scheduled tasks, including job type and job state.
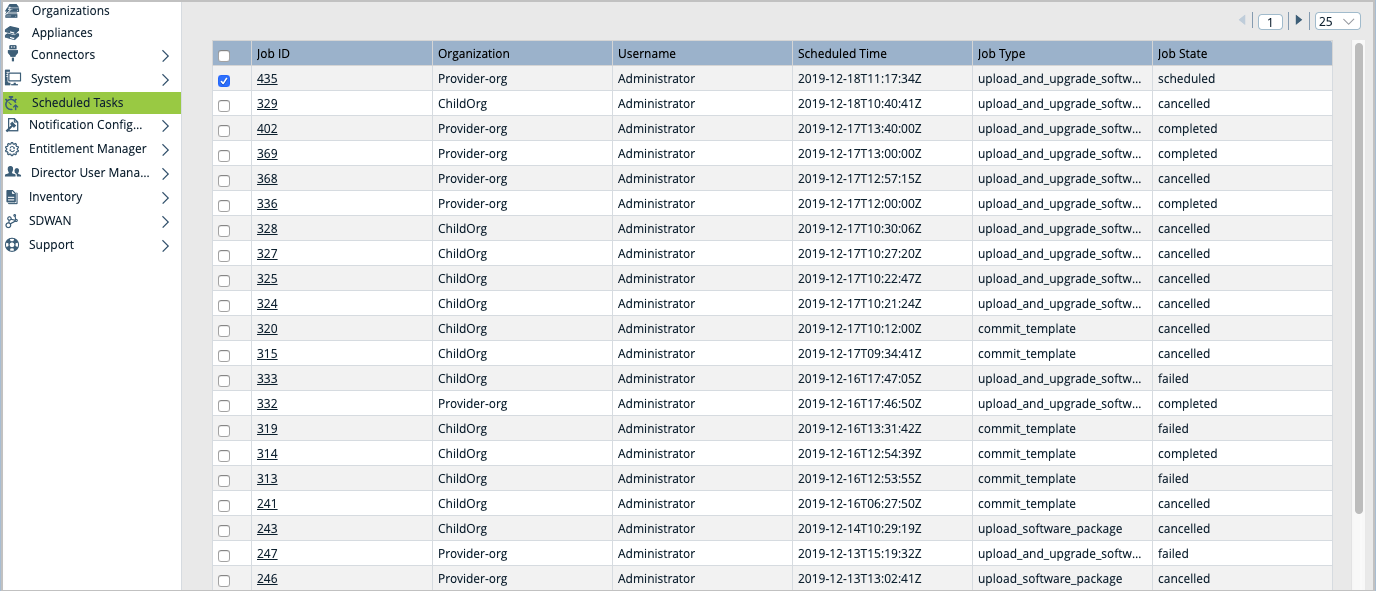
- Select a task from the Job ID column, and then click the task number to open the Edit Task window.
- Edit information in the following fields:
- Job State—Select Cancel to delete the scheduled task.
- Schedule Time—Click the Calendar and Clock icons to reschedule the task.
- Click OK.
- Click Confirm.
Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 21.1.0 adds support for the scheduling automatic software upgrades.
- Release 23.1.1 adds support for upgrading an Analytics cluster from the Director GUI and for upgrading the App ID protocol bundle along with the VOS image.
