Update and View Shadow IT Discovery Applications
![]() For supported software information, click here.
For supported software information, click here.
Shadow IT refers to IT devices, software, and services that operate within an organization's network without explicit management, control, or approval of the IT department. Shadow IT discovery proactively identifies and categorizes such IT assets within the organization's network, and categorizes them according to their risk level, which is based on security vulnerabilities, compliance risks, and business impact.
From Versa Concerto, you can change the state of shadow IT applications according to your organization's requirements. The states are sanctioned, unsanctioned, or unknown. If an application is sanctioned, that means it has been officially approved by your organization's IT department. You can also view application traffic logs and security information of an application.
Update the State of a Shadow IT Application
- Go to View > Security > Risk Score.

- Click Shadow IT Discovery. The following screen displays.

- Click View Details for the application for which you want to update the state. The following screen displays with the application state in the top right corner (Unsactioned in the following screenshot).

- To update the application state click the
 Edit icon next to the application state. The Edit State popup window displays.
Edit icon next to the application state. The Edit State popup window displays.
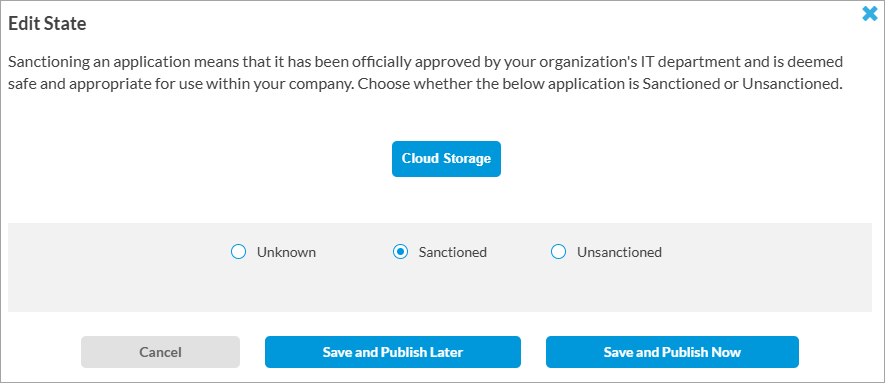
- Select one of the options (Unknown, Sanctioned, or Unsanctioned). You can use sanction or unsanctioned application categories for SASE application and URL filtering match criteria for internet protection rules. For more information, see Configure SASE Application and URL Filtering for Internet Protection Rules.
- Click Save and Publish Later or Save and Publish Now, as needed.
View Shadow IT Application Details
- Go to View > Security > Risk Score > Shadow IT Discovery.

- Click View Details for the application.

- To view traffic logs for the application, check the Application Traffic Logs section.

- To view security details of an application, select from the following tabs on the Application Details screen:
- Select the Certification and Standards tab to view the compliance and datacenter certifications. The following screen displays.

- Select the Data Protection tab to view the data protection standards details. The following screen displays.

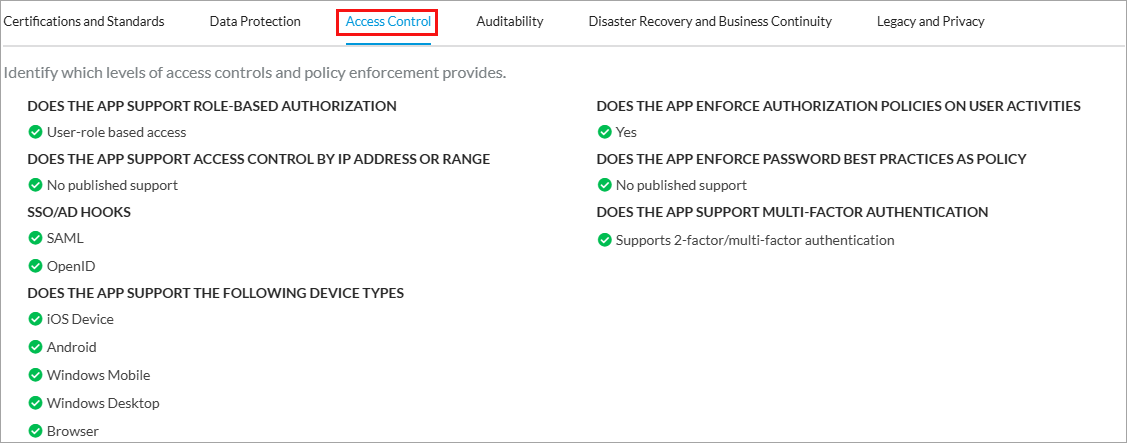
- Select the Access Control tab to view the levels of access controls and policy enforcement. The following screen displays.
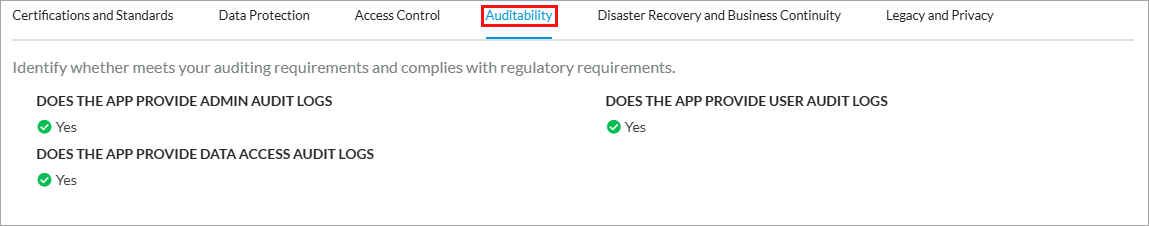
- Select the Auditability tab to view the status of auditing and regulatory requirements. The following screen displays.
- Select the Disaster Recovery and Business Continuity tab to view the details of business continuity data access in case of a system failure or disaster. The following screen displays.

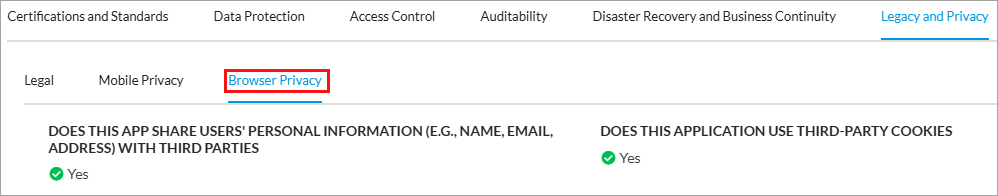
- Select the Legacy and Privacy tab to view legal, mobile privacy, and browser privacy information. The following tabs display:
- Legal tab:

- Mobile Privacy tab:

- Browser Privacy tab:
- Legal tab:
- Select the Certification and Standards tab to view the compliance and datacenter certifications. The following screen displays.
Supported Software Information
Releases 12.2.1 and later support all content described in this article.
Additional Information
Configure SASE Internet Protection Rules
View Concerto Security Dashboards
