Configure Forensic Profiles in Concerto
![]() For supported software information, click here.
For supported software information, click here.
Data forensics is a methodology for collecting and analyzing data, such as user activity and system data, on computing devices, network devices, phones, or tablets. The results are often used in legal procedures, regulatory and company investigations, investigations of criminal activity, and other types of investigations that involve digital evidence.
The Versa Networks implementation of data forensics involves creating a forensic profile that you can then use when you configure the match conditions in a policy or rule that supports the forensic action. In the forensic profile, you specify the application instance that will process the file in question and the location in the cloud where a copy of the file is sent and examined. The original file is retained unchanged. A forensic report is generated and copied to the location specified in the forensics profile. The original file is also copied based on the configuration specified in the profile.
Before you configure a forensic profile, you must create one or more application connectors. For more information, see Configure Cloud Applications To Use with API-Based Data Protection.
To configure forensic profiles:
- Go to Configure > Security Service Edge > Profiles and Connectors > Forensic Profile.

The following screen displays any configured profiles.
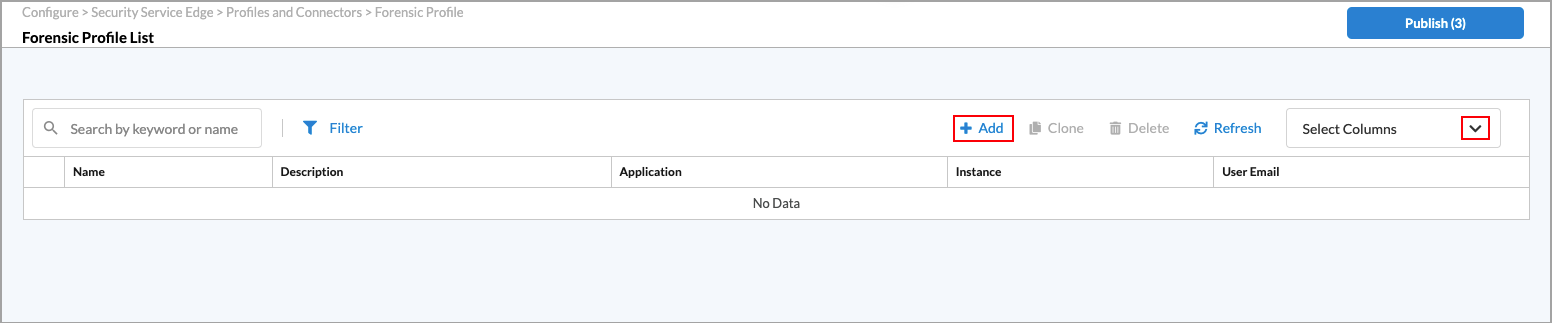
- To customize which columns display, click Select Columns, and then click the columns to select or deselect the ones you want to display. Click Reset to return to the default columns settings. The available columns are:
- Name
- Description
- Application
- Instance
- User Email
- Click the
 Add icon to create a new forensic profile. In the Create Forensic Profile screen, enter information for the following fields.
Add icon to create a new forensic profile. In the Create Forensic Profile screen, enter information for the following fields.
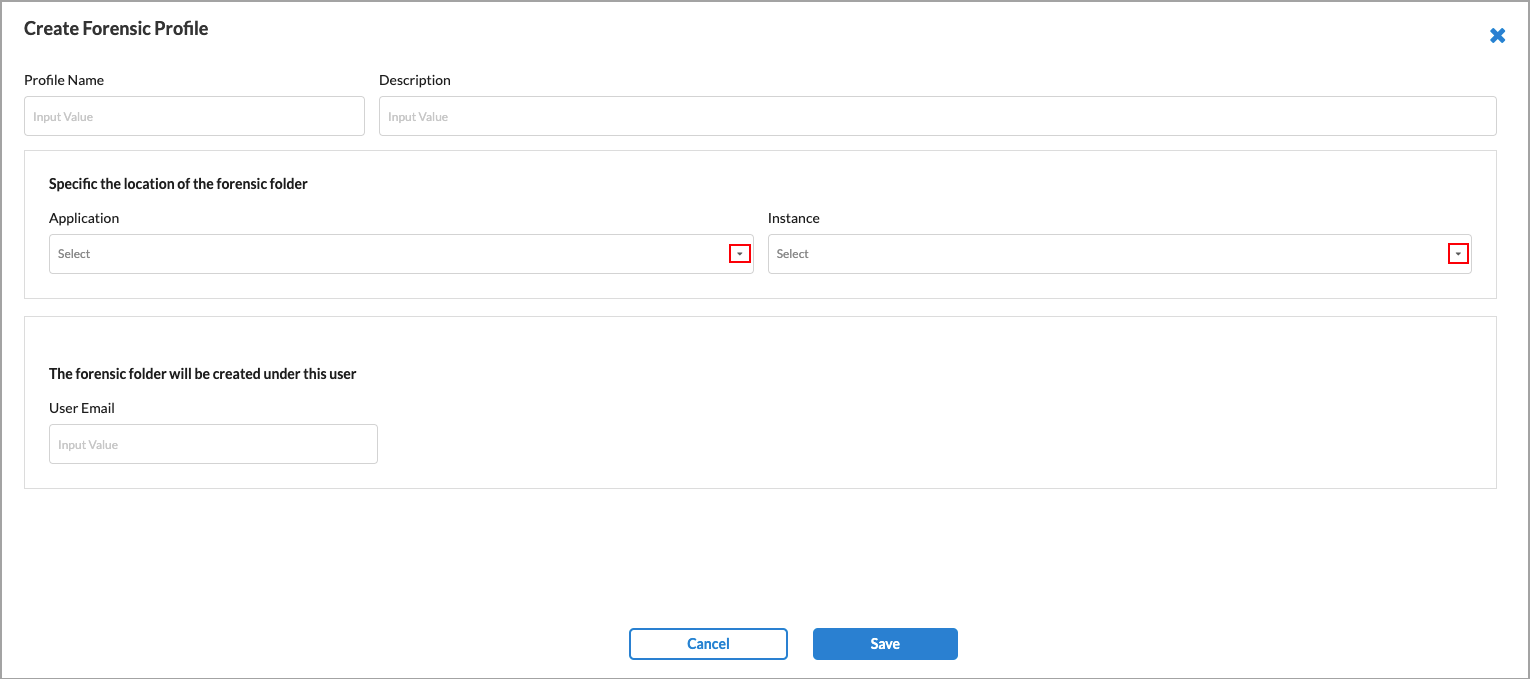
Field Description Profile Name Enter a name for the forensic profile. Description (Optional) Enter a description of the profile. Specific Location of the Forensic Folder (Group of Fields) - Application
Select an application. The options are:
- Box
- Dropbox
- Google Drive
- Microsoft OneDrive
- Microsoft Office 365 SharePoint Sites
- Instance
Select an instance of the chosen application. For information about creating an application instance, see Configure Cloud Applications To Use with API-Based Data Protection. User Email Enter the user email address under which the forensic folder is created. - Click Save.
Quarantine, Forensic, and Legal Hold Instructions
- For all SaaS applications that support Quarantine, Forensic, or Legal Hold as a destination, a folder will be created under the specified user. These folders must not be used or modified for any other purpose.
- For all IaaS applications, access to the designated object (container or bucket) used for Quarantine, Forensic, or Legal Hold purposes should be limited to administrators only. This location must not be used to store any other files or folders.
Applications Supporting Forensic Object Storage
The following applications can be configured as destinations for Forensics profiles.
- IaaS Applications
- Amazon Web Services (AWS)
- Google cloud Platform (GCP)
- Microsoft Azure Cloud
- Oracle Cloud Infrastructure (OCI)
- SaaS Applications
- Box
- Citrix ShareFile
- Dropbox
- Egnyte
- Google Drive
- Microsoft OneDrive
- Microsoft SharePoint
Supported Software Information
Releases 12.2.1 and later support all content described in this article.
