Use LDAP for End User Authentication
![]() For supported software information, click here.
For supported software information, click here.
Authentication is a mechanism for verifying the identities of users so that only genuine users have access to applications. You can choose from various authentication methods to authenticate end-use s through a captive portal and an authenticate firewall. You can configure either a user-based or group-based policy to set whether to allow or deny traffic.
On Versa Operating SystemTM (VOSTM) devices, you can configure a number of authentication methods to authenticate end users, including using a local database, using a Lightweight Directory Access Protocol (LDAP) server, Security Assertion Markup Language (SAML), and Kerberos. This article describes how to configure an LDAP server to use for end user authentication.
LDAP is a client-server protocol that enables a network device to access an LDAP server, which provides directory services that store descriptive attribute-based information. When an end user sends a request to access a webpage, the VOS device accesses the LDAP server to validate the user. Based on the authentication result, the user is either authentication or their authentication request is denied. You can configure either a user-based or group-based policy to allow or deny traffic.
For LDAP authentication to work, you must enable the NGFW service on the VOS device. For more information, see Configure NGFW.
Configure LDAP for End User Authentication
To authenticate users using LDAP and an LDAP server:
- Configure an LDAP server profile. Currently, the LDAP server type can only be Active Directory. For configuration information, see Configure an LDAP Server Profile.
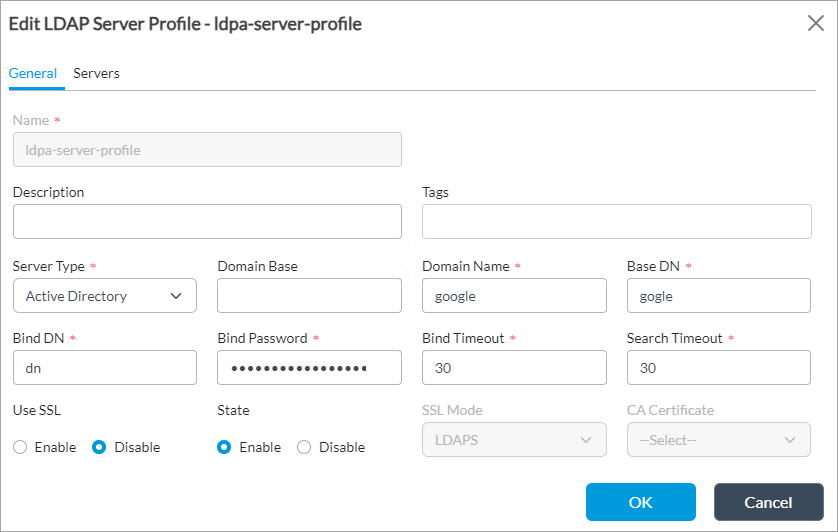
- Configure an LDAP user group profile. For configuration information, see Configure a User and Group Mapping Profile.

- Create an authentication profile in which you associate the LDAP authentication profile you created in Step 1. For configuration information, see Configure an Authentication Profile. If you create an authentication profile without creating an LDAP profile, you must create an LDAP profile here.

- Create an authentication rule in which you select the authentication profile you created in Step 3 to use for the enforcement action. For more information, see Configure Rules for Authentication Policies.
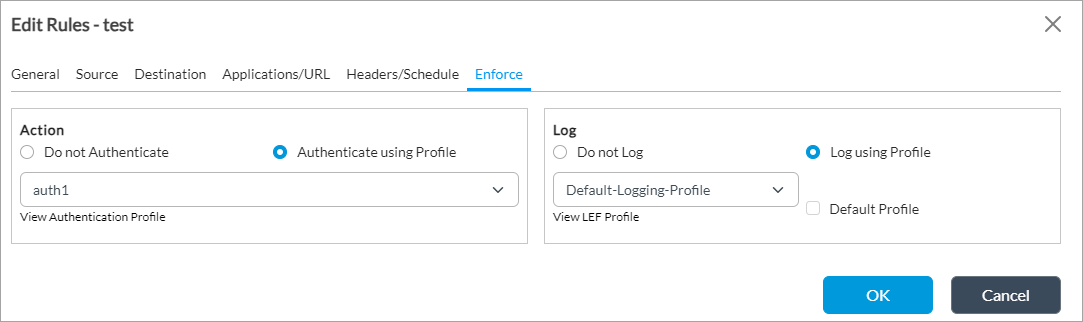
- Configure the captive portal:
- Create a private key for the certificate. This is required because the captive portal uses a self-signed certificate. For more information, see Create a CA Certificate Key.
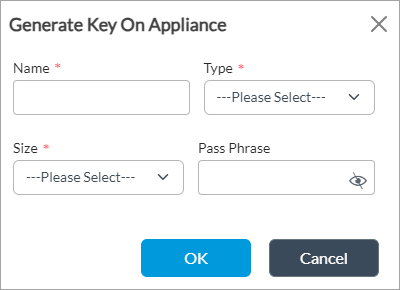
- Create the certificate and assign the private key you generated in Step 5a. For more information, see Create a Certificate on a VOS Device.

- Configure the captive portal. For more information, see Configure Captive Portal.

- Create a private key for the certificate. This is required because the captive portal uses a self-signed certificate. For more information, see Create a CA Certificate Key.
- Create an access policy rule to allow the traffic you want to authenticate. For more information, see Configure Access Policy Rules.
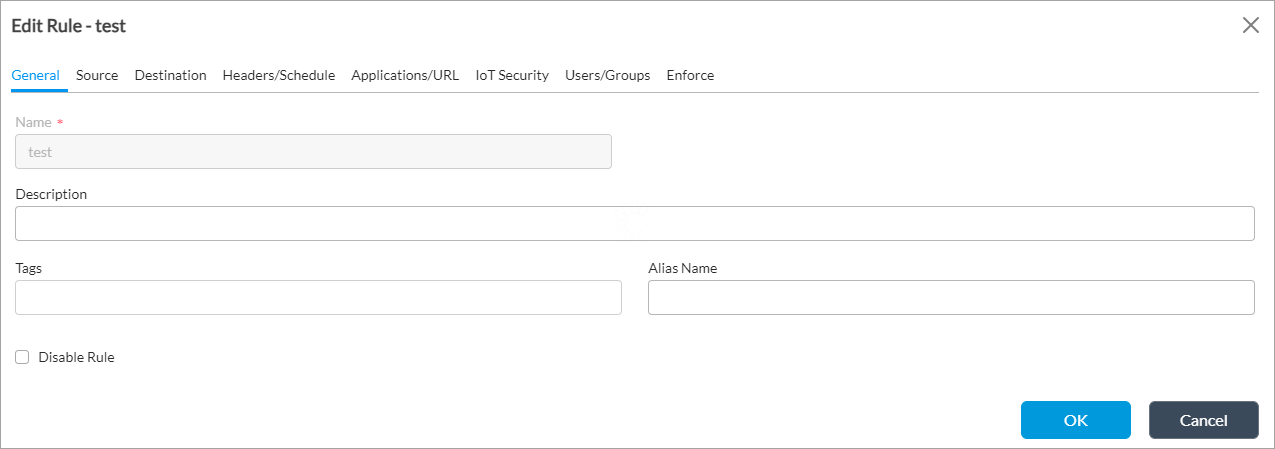
- If you are authenticating HTTPS traffic, configure an SSL decryption profile. For more information, see Configure an SSL Decryption Profile.
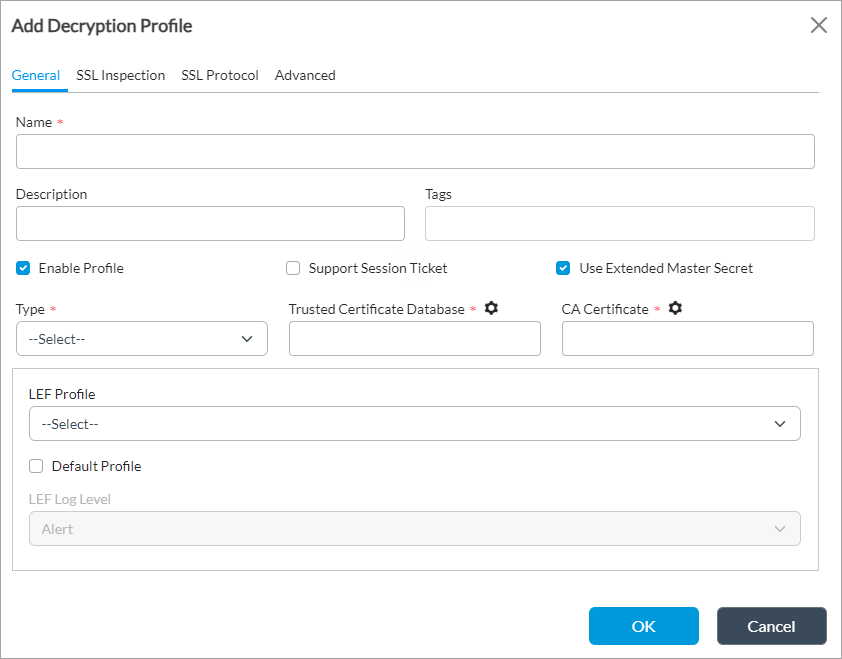
- If you are authenticating HTTPS traffic, configure an SSL decryption policy that sets the decrypt action. For more information, see Configure an SSL Decryption Profile.

- Export the self-signed certificate, and then import it to the Windows computer.
For information about how to match a specific user from LDAP, see Add External Database Users in Configure User and Group Policy.
Use Case Example
This section shows an example of how the LDAP configuration authenticates end users.
- An unauthenticated user enters a webpage address in the URL. A captive portal window similar to the following displays:
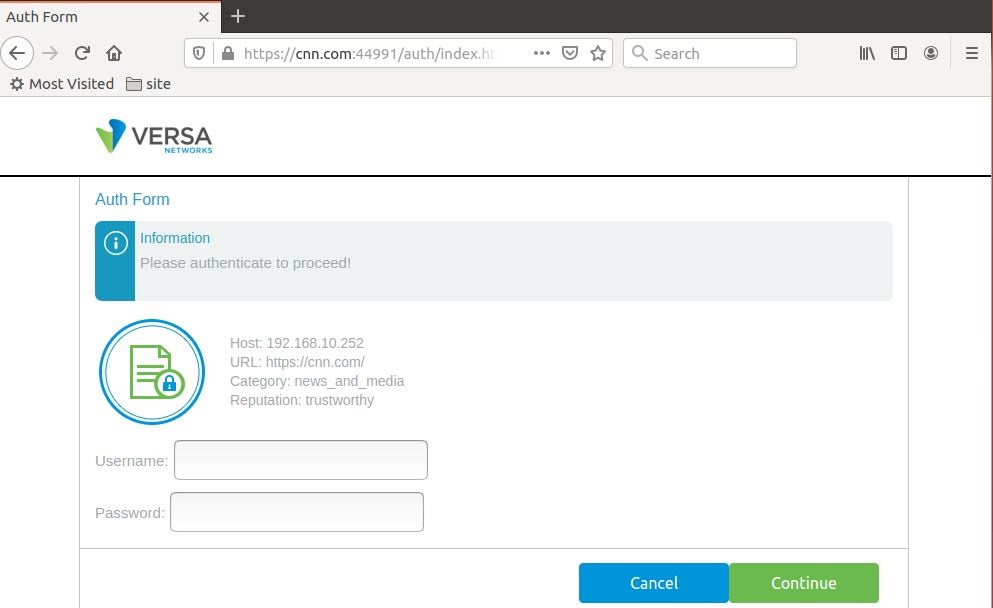
- The user enters their credentials and then clicks Continue.
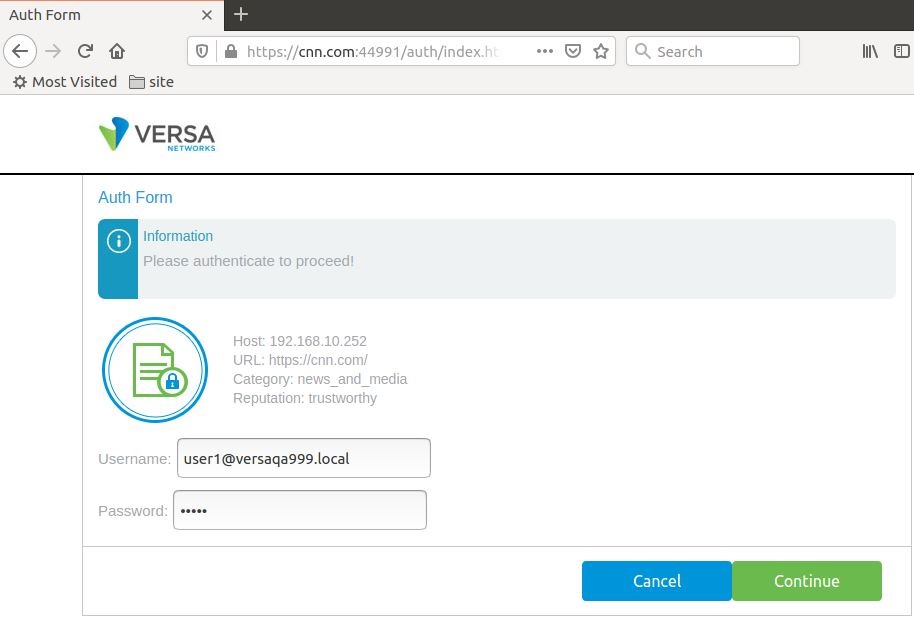
- If the credentials are correct based on the LDAP configuration, the webpage opens successfully.
- If the credentials are incorrect based on the LDAP configuration, a window similar to the following displays:

- To view profile statistics for custom profiles:
- In Appliance view, select the Monitor tab in the top menu bar.
- Select the Services tab in the horizontal menu bar.
- Select NGFW > User Identification.
- Select Live Users in the drop-down menu. The window displays statistics for the currently active users.

- To view the authentication logs on the Analytics node:
- Log in to the Analytics node that is integrated with the Director node.
- Select the Dashboard tab in the top menu bar.
- Select Logs > Authentication in the left navigation bar. The following window displays, showing the logs panes with top data.

Supported Software Information
Releases 20.2 and later support all content described in this article.
