Configure a Secure Access Service (Remote Access VPN) Template
The Versa Secure Access (VSA) service allows you to configure an organization's Versa Portal instances to be secure access portals or secure access gateways so that a VSA client can connect to the instances. The VSA service provides SD-WAN or secure VPN tunnel connectivity to enterprise networks and access to the internet through secure web gateway (SWG) services. The VSA service can authenticate clients using either Microsoft Active Directory (AD) or the local database on the Versa Operating SystemTM (VOSTM) instance.
During the initial configuration, a reseller or an MSP provisions the license in the Versa MSP portal using Versa Cloud Gateway and provides details about VSA services. Depending on whether you select AD or local database authentication, the VSA configuration is done from the Versa Portal.
After you configure the secure access portal and gateway, you can configure a remote access server (RAS), which allows remote access clients to access resources behind the RAS using IPsec. You can also configure a Versa SASE client to provide VPN access to corporate resources using secure access.
When you use a secure access template, you can attach a VRF to terminate an IPsec tunnel. If you have SASE gateway and remote access VPN services in the same organization, when you publish the VRF configuration, it publishes only to the remote access VPN, because SASE gateways always take the enterprise virtual router by default. When creating a new customer, an operator, store administrator, MSP, or reseller can enable multi-VRF for organization. Then, a user has the option to add a VRF when configuring the Versa secure access service. After the VRF option is enabled for an organization, an administrator cannot disable it using the create or edit organization window. By default, one VRF is created with the name of the organization, and all the initial LAN ports are associated with that VRF. You cannot delete the default LAN-VRF after it is created.
Versa secure access performs the following functions:
- Authenticate Versa secure access client users.
- Push configurations to the Versa secure access client.
- Control the behavior of the client based on users, groups, regions, and license type.
- Generate and share the one-time secret password used for the VPN tunnel.
Use a Remote Access VPN
With a remote access VPN, you can enable a secure access VPN in branch, which allows remote users to connect to enterprise networks. You can configure a remote access VPN for a license when you add or upgrade the license. You can enable or disable remote access VPN only when the instance is in undeploy or lock mode.
To use a remote access VPN, one port on the instance must be configured with a static IP address. This IP address is used to terminate connections to remote clients.
To use a remote access VPN, configure the following:
- For a new instance:
- Configure the remote access VPN template with a local, a Security Assertion Markup Language (SAML), or an LDAP authentication profile. See Configure a Secure Access Client, below.
- Configure a captive portal port for all WAN networks with HTTP port 80 and HTTPS port 443. See Configure Miscellaneous Parameters.
- Add the instance fully qualified domain name (FQDN) and static IP address on the WAN interface. See Configure WAN Connections.
- Deploy and activate the license. Wait until the instance is completely up and the monitor shows that the instance has an IP address.
- Upload all required certificate files for Versa secure access. See Upload a Certificate.
- For an instance that is being updated:
- The enterprise administrator can then enable remote access VPN for the WAN network.
- Configure the remote access VPN template with a local, a SAML, or an LDAP authentication profile. See Configure a Secure Access Client, below.
- If the license is deployed or activated, lock it in the instance honeycomb in the Configure Dashboard.
- Configure a captive portal port for all WAN networks with HTTP port 80 and HTTPS port 443. See Configure Miscellaneous Parameters.
- Upload all required certificate files for VSA. See Upload a Certificate.
Note: If you are upgrading the license from a previous release and the remote access VPN option is not enabled, you can enable it from the license upgrade option in the Inventory menu. For more information, see Upgrade a Device.
Configure a Secure Access Client
- Click Templates in the left menu bar to open the Templates dashboard.
- Select Versa Secure Access Template and then click on the secure access default template name.

- In the Secure Access Default Configuration screen, click Secure Access Profiles > Secure Access Client tab, and then enter information for the following fields.

Field Description Profile Select an OS profile:
- Default (Windows)
- Linux
- MAC
- Android
- IOS
To add a new OS profile, click the + Add icon and enter a profile name and OS type.
General - Secure Access Tunnel Selection (Required)
Select the type of tunnel:
- Full Tunnel—For remote access VPN, full tunnel is the only applicable option.
Secure Access Profile - Client Control (Required)
Configure client settings. - Two-Factor
Click the toggle button to enable or disable two-factor authentication. VSA local users can use two-factor authentication to receive a one-time password (OTP) and time-based one-time password (TOTP) through email. For AD users, you can enable two-factor authentication and receive a TOTP. - Two-Factor Type
Select the two-factor authentication type:
- Authenticator App TOTP—Click to send the QR code to the email address that was used to register the VPN client. You can scan the QR code using any third-party authenticator application and generate an OTP. The secure access client displays an OTP text box in which you enter the OTP displayed in the TOTP authenticator application. To log in manually, copy and paste the code included in the QR code notification email into the authenticator application.
If you configure secure access template with LDAP authenticator and enable TOTP two-factor authentication, you need to configure a security rule with the user group for the system to fetch the email address from the LDAP server to send the QR code. - Email OTP—Click to receive an OTP through email, to enter for two-factor authentication. Email OTP is not supported with external LDAP.
- Remember Credentials
Click to have the VSA client remember the user login credentials. - Edit Gateway
Click to allow VSA client users to enable or disable a gateway. - Tamper Protection
If you enable tamper protection from the server side, you cannot uninstall the client, delete the client account, or delete any files from the installation directory.
To disable, click the toggle button in the Account Details window, and then enter the tamper protection authentication key.
- Tamper Protection Override Key
If you enable tamper protection from the server side, you cannot uninstall the client, delete the client account, or delete any files from the installation directory.
To disable, click the toggle button in the Account Details window, and then enter the tamper protection authentication key.
- Auto Disconnect
Automatically disconnect tunnel after the configured auto disconnection interval. - Password Expiry Warn Before
For active directory users, enter the number of days before the password expiration to display a notification message to the secure access client user. This field is not applicable for VSPA users.
Default: 10 days
- Trusted Network Hostname
Enter the name of the trusted accessible network hostname. The name can be a maximum of 255 characters. - Certificate Issuer
Enter the name of the certificate issuer. Tunnel Monitoring (Tab) - Tunnel Monitoring
Click the toggle button to enable tunnel monitoring. When enabled, the SASE client checks whether the configured host is reachable using the tunnel. If the SASE client cannot reach the host through the tunnel, the client considers the tunnel to be down and tries to reestablish the tunnel. It is recommended that you configure multiple hosts so that the client considers the tunnel as down only if none of the hosts are reachable.
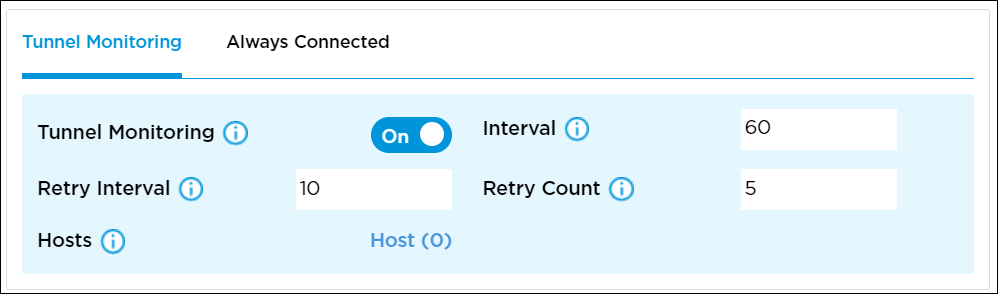
- Interval
Enter the tunnel monitoring interval, in seconds.
Default: 60 seconds- Retry Interval
Enter the time, in seconds, between each retry for monitoring.
Default: 10 seconds- Retry Count
Enter the number of connection retry attempts before concluding the tunnel is down.
Default: 5- Hosts
Select the list of hosts for tunnel monitoring. In the Add IP or Hostname window, enter the IP address or hostname.

Always Connected (Tab) - Always Connected
Click the toggle button to allow the VPN connection to always be on for the secure access client. This connection is called an always-on connection. This is valid only for cloud-based VSPA clients, and is not available on remote access VPN. - Disconnect
Select how to handle a temporary disconnection for an always-on connection, and whether to allow connection to a different gateway:
- Interval—The connection can disconnect for the amount of time specified in the Disconnect Interval. The default interval is 120 seconds. If no connection is made to a different gateway, the original connection automatically restores after the disconnect interval expires.
- Never—Disconnection is not allowed, and an always-on connection cannot change its gateway connection.
- Disconnect Interval
Enter the interval, in seconds, to automatically disconnect the tunnel after the configured auto disconnect interval.
Default: 120 seconds
- Fail Mode
Select whether traffic is allowed when an always-on connection fails:
- Close—Do not allow traffic
- Open—Allow traffic
- Override Interval
If you select fail mode override, enter how long to wait, in seconds, before overriding the fail mode.
Default: 120 seconds- Private Prefix Access (Required)
Enter an IP prefix that can be reached over the remote access VPN, and then click the  icon. If you do not enter a value, the IP subnet is automatically allocated.
icon. If you do not enter a value, the IP subnet is automatically allocated.- Domain (FQDN) and DNS Resolver (Required)
Select the domains to which the FQDN and DNS resolver IP address apply. - All Domains
Apply the name server for all domains that are not explicitly defined. In the Name Server field, enter the name of the DNS name server, and then click the  icon.
icon.- Specific Domains
Apply the name server to the specified domains. Enter the following information for private domains, and then click the
 icon.
icon.
- Domain Name (Required)—Enter the name of the domain in which the DNS resolver is located.
- Name Server Addresses (Required)—Enter the IP addresses of the DNS name servers. You can configure up to two DNS server IP addresses.
- Authenticator
Select an authentication profile:

- Enterprise LDAP Profile—If you select LDAP authentication in the Select Authentication Profile field, select an LDAP profile to associate with the authentication profile. Click + Authenticator Profile to add a new LDAP profile. For more information, see Configure LDAP Profiles.
- Enterprise SAML Profile—If you select SAML authentication in the Select Authentication Profile field, select a SAML profile to associate with the authentication profile. Click + Authenticator Profile to add a new SAML profile. For more information, see Configure SAML Profiles.
- Versa IDP—Use the authentication and user credentials that are stored on the local device.
VRF (Required) Click, and then select the VRF in which the secure access client terminates on the SASE gateway or remote access branch device.
- Select the Secure Access Profiles > Steering tab, and then enter information for the following fields. Note that steering is available on SASE gateway and multitenant RAC/RAS devices only; it is not available for remote access VPN devices.

Field Description Profile Select an OS profile:
- Android
- Default (The default profile is Windows)
- IOS
- Linux
- MAC
To add a new OS profile, click the + Add icon and enter a profile name and OS type.
Application Steering - Exclude Applications
Click and then select an application from the Application List popup window to add an application that you do not want to send to the client. Then click Continue. When full tunnel mode is enabled, these applications are excluded from the VPN tunnel to the SWG (SASE gateway), and they are steered through DIA (local internet) instead.

- Predefined Exclude Applications—Select a predefined application. and then click the + Add icon to add the application.
- User-Defined Exclude Applications—Select a user-defined application. and then click the + Add icon to add the application. To add a new user-defined application to exclude, click the
 icon.
icon.
- Exclude Domain
Click and then select a domain from the Application List popup window to add a domain that you do not want to send to the client. Then click Continue. When full tunnel mode is enabled, these domains are excluded from the VPN tunnel to the SASE gateway, and the domain is steered through DIA (local internet) instead.

- User-Defined Exclude Domains—Select a user-defined domain. and then click the + Add icon to add the domain. To add a new user-defined domain to exclude, click the
 icon.
icon.
- Include Applications
Click and then select an application from the Application List popup window to add an application that you want to send to the client. Then click Continue. When split tunnel mode is enabled, these applications are excluded from DIA (local internet), and they are steered to the SWG (SASE gateway) instead. Use this option when you purchase secure access and SWG licenses.
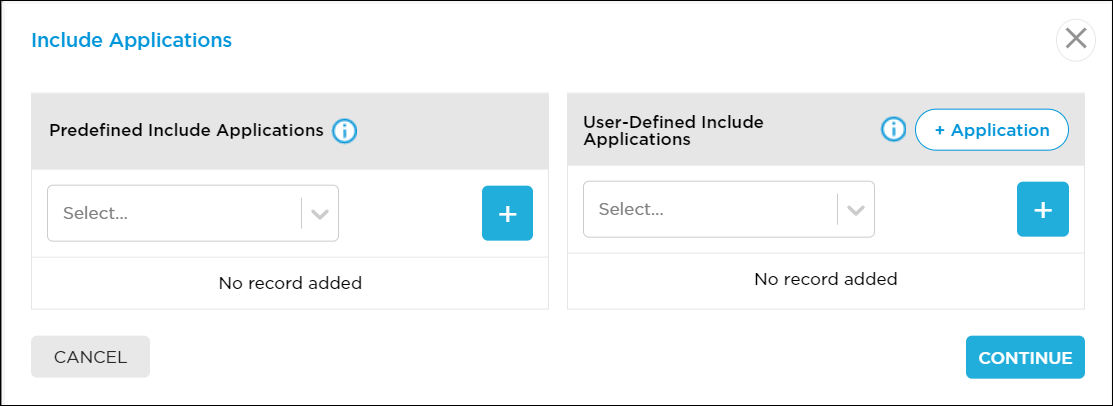
- Predefined Include Applications—Select a predefined application. and then click the + Add icon to add the application.
- User-Defined Include Applications—Select a user-defined application. and then click the + Add icon to add the application. To add a new user-defined application to include, click the
 icon.
icon.
- Include Domains
Click and then select a domain from the Application List popup window to add a domain that you want to send to the client. Then click Continue. When split tunnel mode is enabled, these domains are excluded from DIA (local internet), and they are steered to SWG (SASE gateway) instead. Use this option when you purchase secure access and SWG licenses.

- User-Defined Include Domains—Select a user-defined domain. and then click the + Add icon to add the domain. To add a new user-defined domain to include, click the
 icon.
icon.
- Exclude Routes
Click and then select a route from the Exclude Routes popup window to add a route that you do not want to send to the client.

- User-Defined Exclude Routes—Select a user-defined route. and then click the + Add icon to add the route.
- Select the Client Security tab to configure secure access rules. A numbered circle next to the rule name indicates its position in the rule set. The color of the circle indicates whether the rule denies (red) or allows (green) traffic. By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon.
Note that client security is available on SASE gateway and multitenant RAC/RAS devices only; it is not available for remote access VPN devices.

- If necessary, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers update automatically.
- Click Publish Reordered Rules to save the changes to the Versa cloud.
- Click the Add Rule icon, and the enter information for the following fields.

Field Description Rule Name (Required) Enter a name for the rule. Click the toggle button to enable the rule. Description Enter a text description for the rule. The description can be a maximum of 63 characters. Match Criteria Select the Location, Address, EIP Profile, Device, or User and Group tab to add information about that criteria type.
For more information, see Apply Match Criteria for Client Security Rules, below.
Action Select Allow or Deny. Secure Access Profile Select a secure access profile to associate with the client security rule. EIP Agent Profiles Select an EIP agent profile to associate with the client security rule. - Select the Miscellaneous tab and enter information for the following fields.

Field Description Grouping and Registration Portal Configure a registration portal and group. The registration portion is the device to use to register and configure the VSA clients on first contact. The welcome email for SASE contains the link and information for the registration portal settings.
- Registration Portal (Required)
Click to select a registration portal. - Group
Group a set of SASE gateway and remote access devices to let the system determine the best gateway for the VSA client to connect. Click Please select to select a group. To add a new group, click the + Add icon and enter information for the following fields.
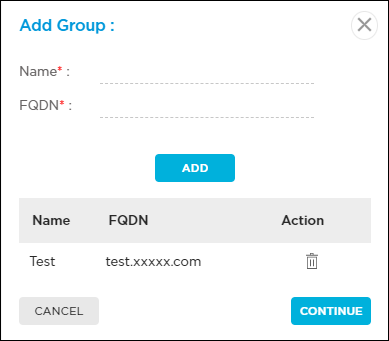
- Name (Required)—Enter a name for the group.
- FQDN (Required)—Enter a fully qualified domain name. The FQDN must resolve to one gateway.
Click Add, and then click Continue. The VSA client then displays the group, and the customer can select the group instead of a specific gateway.
- Click Publish to publish the configuration to all remote access VPN-enabled devices and SASE gateways that have secure access services.
Apply Match Criteria for Client Security Rules
You can use the following match criteria types in a client security rule:
- Address
- Device
- EIP Profile
- Location
- User and Group
To specify match criteria for a client security rule:
- To specify location criteria for a client security rule:
- Select the Location tab to display the location window.

- Click Source Address Regions.
- In the Select Regions for Location popup window, select the regions, and then click Continue.

- Select the Location tab to display the location window.
- To specify an address criteria for a client security rule:
- Select the Address tab to display the address window.

- Click the toggle button to enter the source or destination IP address. Then click Source.

- Enter a source IP address in CIDR format, and then click the
icon. To remove an IP address from the list, click the
icon.

- Click Continue
- Select the Address tab to display the address window.
- To specify EIP profile criteria for a client security rule:
- Select the EIP Profile tab to display the EIP profile window.

- Click the toggle button to enter the EIP profile. Then click EIP Profile.

- In the EIP Profile window, select a predefined EIP profile, and then click the Add icon to add the profile.

- Click Continue.
- Select the EIP Profile tab to display the EIP profile window.
- To specify device criteria for a client security rule:
- Select the Device tab to display the device window, and then click Endpoint Protections to select the predefined endpoint protections.

- In the Endpoint Protections window, select a predefined endpoint protections profile, and then click the Add icon to add the profile.

- Click Continue.
- Click Operating System to select the predefined operating systems, and then click Add icon to add the operating system.

- Click Continue.
- Select the compliance state.

- Select the Device tab to display the device window, and then click Endpoint Protections to select the predefined endpoint protections.
- To specify user and group criteria for a client security rule:
- Select the User and Group tab and enter information for the following fields.

- Known—Click to select known user and group.
- Selected—Click to select an LDAP profile.
- User Group Profile (Required)—Select an LDAP authentication profile, and in the Select User Group Profile window, select the users and groups, and then click Add.

Ensure you add an authentication rule with authenticator as LDAP profile with the user and group name you want to choose. The LDAP user and group name is not displayed until you add an authenticator rule with the LDAP profile.
- User Group Profile (Required)—Select an LDAP authentication profile, and in the Select User Group Profile window, select the users and groups, and then click Add.
- Select the User and Group tab and enter information for the following fields.
- Click Add.
