Manage Organization Settings
This article describes how to manage secure access configuration setting for an organization. Note that the secure access configuration is common for across an organization and all devices in the organization. You cannot configure it for individual devices.
Management Profile
Add Custom Logs Profile
Versa Portal sends syslog messages when the following match conditions are met:
- Firewall—Add security rules and select custom logs. For more information, see Manage Firewall Policies.
- Decryption—Add rule and select custom logs. For more information, see Configure TLS Decryption.
To add a customer flow log profile in the Versa Portal Inventory:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Select Custom Logs Profile and then enter information for the following fields.
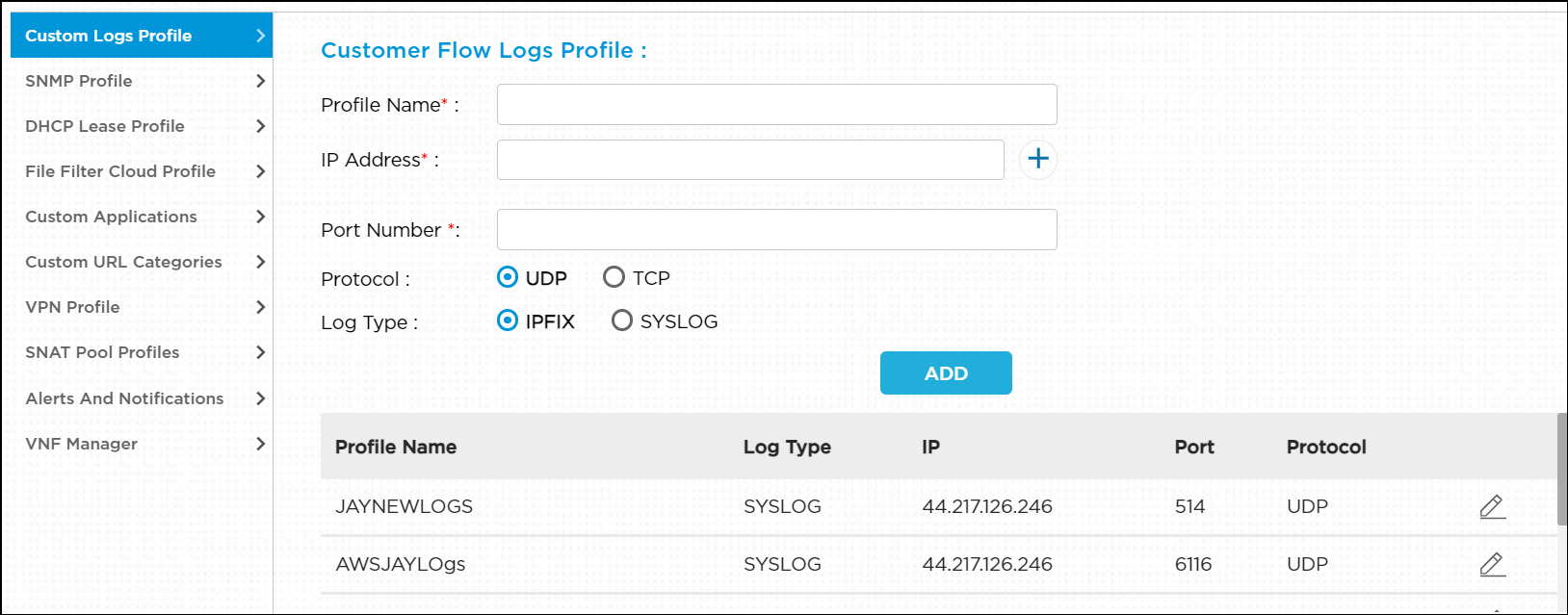
Field Description Profile Name (Required) Enter a name for the profile. IP Address (Required) Enter the IP address of the syslog server. Click the  icon to add multiple IP addresses.
icon to add multiple IP addresses.Port Number (Required) Enter the port number. Protocol Select the protocol:
- TCP
- UDP
Log Type Select the log message format:
- IPFIX
- Syslog
Region Select a region. - Click Add. The flow log profile is displayed.
- Click the
 icon to edit the profile.
icon to edit the profile.
Add an SNMP Profile
You can configure SNMP at the branch level. You specify the SNMP version that the Versa Portal instance supports and the SNMP server to which the Versa Portal instance connects. You must configure an SNMP on at least one device to which the SNMP server is attached. For more information, see Configure Miscellaneous Parameters.
If you want to modify an SNMP profile configuration, you must lock the device, make the changes, and then deploy the device for the changes to take effect.
To add SNMP profile in the Versa Portal Inventory:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click SNMP Profile and then enter information for the following fields.

Field Description Version Select one or more SNMP versions:
- v2c
- v3
Community Public (Required) For SNMPv2c, enter the SNMP community string to use to access the SNMP server. Username (Required) For SNMPv3, enter the username to use to access the SNMP server. Password (Required) For SNMPv3, enter the password for the username. IP Address (Required) Enter the IP address of the SNMP server. Click the + icon to add multiple SNMP server IP addresses. - Click Save.
Add a DHCP Lease Profile
A DHCP lease profile specifies the duration and properties of the lease profile.
To add a DHCP lease profile:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click DHCP Lease Profile, and then enter information for the following fields.

Field Description Lease Profile Name (Required) Enter a name for the lease profile. The name cannot include any spaces. Description Enter a text description for the lease profile. Life Time Enter how long the lease profile is valid.
Range: 60 through 31536000 seconds
Default: 11600 seconds
Renew Timer Enter the time during which a client can renew the lease profile. You can configure the renew timer to be less than or equal to 50 percent of the valid lifetime.
Range: 60 through 31536000 seconds
Default: 10000 seconds
Rebind Timer Enter the time during which a rebind request can be sent by a client after a period of inactivity. You can configure the rebind timer to be less than or equal to 80 percent of the valid lifetime.
Range: 60 through 31536000 seconds
Default: 20001 seconds
- Click Add. The lease profile is displayed.
- Click the
 icon to delete the profile. You cannot edit a lease profile.
icon to delete the profile. You cannot edit a lease profile.
Add a Cloud Profile for File Filtering
If you enable cloud lookup on Versa Portal, you can configure a cloud profile to look up information about the file on a cloud server. After completing the lookup, the profile marks the file for further action. If you configure a reputation-based action, you must create a cloud profile. See Configure File Filtering.
To configure a cloud profile for file filtering:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click File Filter Cloud Profile, and then enter information for the following fields.

Field Description Name (Required) Enter a name for the cloud profile. Description Enter a text description for the cloud profile. Source NAT List (Required) Select the SNAT pool to configure cloud lookup for file filtering. The SNAT pool is linked to a routing instance that connects to the cloud server. To create an SNAT pool profile, see Add SNAT Pool Profiles. Connection Pool (Required) Enter the number of simultaneous connections to the SSL cloud server.
Range: 1 to 100000
Default: None
Timeout Enter the maximum timeout period to wait for a response from the SSL cloud server, in seconds.
Range: 1 through 4294967295 seconds
Default: 120 seconds
Activation Click the toggle to activate the cloud lookup profile. - Click Add. The cloud profile displays in the list.
- Click the
 Edit icon to update the cloud profile, and then click Update to save the changes.
Edit icon to update the cloud profile, and then click Update to save the changes. - Click the
 icon to delete the cloud profile. You cannot edit a lease profile.
icon to delete the cloud profile. You cannot edit a lease profile.
Add Custom Applications
You can create custom application on a per-tenant basis, and then the custom application objects becomes available to all devices to use for configuration. When you add a custom application, it is added automatically to the custom application list on Versa Director and VOS devices for all active devices. If a device is down, you can publish the custom application after the device is up.
To add custom applications:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click Custom Applications, and then enter information for the following fields.

Field Description Name (Required) Enter a name for the application. Description (Required) Enter a text description for the application. Precedence (Required) Enter a unique priority number to use when multiple applications match the traffic. The application with a higher precedence value is matched first.
Range: 0 through 65535
Application Timeout Enter how long to wait, in seconds, for the application to timeout because of inactivity.
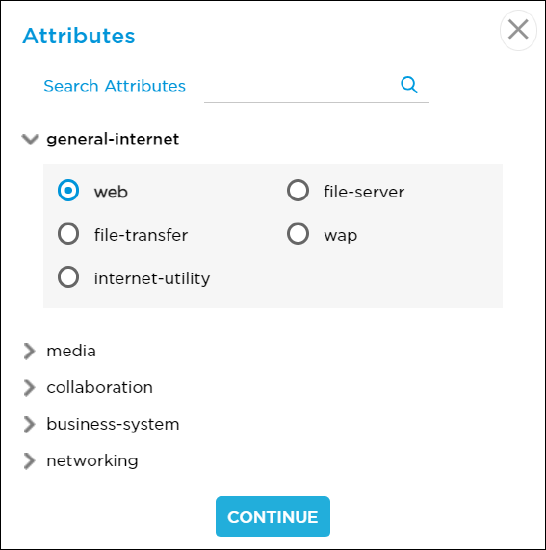
Attributes (Required) Click
 Select. In the Attribute popup window, select an attribute and then click Continue.
Select. In the Attribute popup window, select an attribute and then click Continue.
Match Information (Group of Fields) - Name (Required)
Enter a name for the match rule name for the custom application. - Host Pattern
Enter the host pattern to detect. - Protocol Value
Enter the applications protocol value to detect. - Source IP Address
Enter the source IP address of the application on which the rule is applicable. - Destination IP Address
Enter the destination IP address of the application on which the application rule is applicable. - Source Port
Click
 to enable and assign a custom source port for the application.
to enable and assign a custom source port for the application.

- Value—Select to enable the Source Port Value field, and then enter the application port on which the security policy is applicable.
- Range—Select to enable the Low and High fields, and then enter the lowest and highest source port numbers on which the security policy is applicable.
- Destination Port
Click
 to enable, and assign a custom destination port for the application.
to enable, and assign a custom destination port for the application.- Value—Select to enable the Source Port Value field, and then enter the application port on which the security policy is applicable.
- Range—Select to enable the Low and High fields, and then enter the lowest and highest destination port numbers on which the security policy is applicable.
- Click
 Add. The match information is added to the list.
Add. The match information is added to the list. - Click
 Add Application. The custom application profile is added to the list.
Add Application. The custom application profile is added to the list. - Click the
 Edit icon to update the custom application profile, and then click
Edit icon to update the custom application profile, and then click  Update Application to save the changes.
Update Application to save the changes. - Click the
 icon to delete the custom application profile.
icon to delete the custom application profile. - Click the
 icon, select a device from the Device List popup window, and then click Publish to publish the profile to the device.
icon, select a device from the Device List popup window, and then click Publish to publish the profile to the device.
Add Custom URL Categories
You can create custom URL category objects on a per-tenant basis. Each custom URL category has a unique name. For a custom URL category, you configure a string or pattern match to define the URLs to match. You can associate a reputation value with the URL category. You can use a custom URL category in SD-WAN policy rules to specify match criteria for a Layer 7 URL category.
A custom URL category is added automatically to the user-defined URL category list on the Director and VOS devices for all active devices. If a device is down, you can publish the custom URL category after the device comes up.
To add custom URL categories:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click Custom URL Categories and enter information for the following fields.

Field Description Name (Required) Enter a name for the custom URL category profile. The name cannot include any spaces. Description (Required) Enter a text description of the URL category. Confidence (Required) Enter a confidence value for the URL category. The confidence value is used to break a tie when multiple URL categories match a single URL. A higher confidence value takes precedence.
Range: 1 through 100
URL Pattern Click to configure a URL pattern.
- Pattern (Required)
Enter the URL pattern to match. You can include regex patterns. If you include a backslash (\) or an open curly brace ({) in the regex pattern, you must escape it by preceding it with a backslash. For example:
- www.versa-networks.com
- www.example.*
- www.*.example.com
- URL Reputation (Required)
Select a predefined reputation from the list to assign it to the URL match pattern.  Add icon
Add iconClick the  Add icon to add additional patterns.
Add icon to add additional patterns.URL String Click to configure a URL string. - String (Required)
Enter a URL string. For example:
- https://example.com/profile
- http://example.com/profile
- example.com
- https://.*example.com
- https://example.*
- *.example.com
- URL Reputation (Required)
Select a predefined reputation from the list to assign it to the URL string.  Add icon
Add iconClick the  Add icon to add additional strings.
Add icon to add additional strings. - Click
 Add. The custom URL category is added to the list.
Add. The custom URL category is added to the list. - Click the
 Edit icon to update the custom URL category profile, and then click
Edit icon to update the custom URL category profile, and then click  Update to save the changes.
Update to save the changes. - Click the
 icon to delete the custom URL category profile.
icon to delete the custom URL category profile. - Click the
 icon, select a device from the Device List popup window, and then click Publish to publish the profile to the device. You can publish the failed devices again.
icon, select a device from the Device List popup window, and then click Publish to publish the profile to the device. You can publish the failed devices again.
Add VPN Profiles
VPN profile is not supported on AWS instances.
Add SNAT Pool Profiles
You can create SNAT pools and associate them with DNS proxy and ;file-filtering profiles.
To create SNAT pool profiles:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click SNAT Pool Profiles, and enter information for the following fields.

Field Description Name (Required) Enter a name for the SNAT pool. By default, the cpsp_ prefix is added to the name of the SNAT profile. Egress Network (Required) Select an egress network to associate with the SNAT pool. - Click Add.
- Click the
 icon to delete the SNAT pool profile.
icon to delete the SNAT pool profile.
Add Alerts and Notifications
When Versa Portal generates an alarm, the alarm goes to the Director and Analytics nodes. On the Director node, you can configure alerts and notifications for alarms. To do this, you configure policies and webhooks that send an email or an SMS text message when an alarm is received.
To configure email notifications for alarms:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click Alerts and Notifications, and enter information for the following fields.

Field Description Rule Name (Required) Enter a name for the rule. Alert on Clear Click to send an email notification when an alarm clears. Email (Required) For email notifications, enter one or more email recipients, and then click the  icon.
icon.CC For email notifications, enter one or more recipients to copy on the email, and then click the  icon.
icon.Message For email notifications, enter the text of the email message. Custom Condition Set Displays the name for the match conditions set. The name is automatically generated and is based on the name of the notification rule.
- To add a condition, click the
 icon. In the Add Conditions popup window, select one or more conditions to match. If you select more than one, all conditions must match for the rule to take effect. That is, the conditions are an AND operation. Note that in a single condition, you can specify only one of each attribute type.
icon. In the Add Conditions popup window, select one or more conditions to match. If you select more than one, all conditions must match for the rule to take effect. That is, the conditions are an AND operation. Note that in a single condition, you can specify only one of each attribute type.
- Condition Set (Required)—Displays the name for the match conditions set. The name is automatically generated and is based on the name of the notification rule.
- Attributes (Required)—Select the criteria to use to determine when to send an email notification:
- Alarm Text—Send a notification based on the text in an alarm message.
- Alarm Type—Send a notification based on the alarm type.
- Count, Wait—Send a notification based on the number of alarms that occur within a wait time window. You must define values for both the Count and Wait parameters. If you configure the Count and Wait parameters, you cannot also configure a value in the Soak Time fields. These fields are mutually exclusive.
- In the Count field, specify the number of alarms that occur in the wait time window, in minutes.
- In the Wait field, specify the length of the time window in which to count alarms, in minutes. The window is a sliding window, not a fixed period of time. As it slides, alarms that are too old fall out of the window and are no longer counted. If the number of alarms does not reach the configured count value within the wait window, no email is sent.
- Device Name—Send a notification based on the device name that appears in an alarm.
- Severity—Send a notification based on the alarm message severity. The alarm severity can be one of the following:
- Cleared
- Critical
- Indeterminate
- Major
- Minor
- Warning
- Soak Time—Do not send a notification unless the conditions that trigger the rule are still present after the specified amount of time, in seconds. Configure a soak time to damp the sending of repetitive notifications. If you configure the Soak Time parameter, you cannot also configure Count and Wait parameters. These fields are mutually exclusive.
- Operator (Required)—Select the operator to use to match the attribute. Note that not all operators are available for all attributes.
- Contains—String that you specify in the Value field is present in the attribute type.
- Equals—String that you specify in the Value field exactly matches the string in the attribute type. Note that for the Soak Time and Wait attributes, Equals is the only operator that is available.
- Like—String that you specify in the Value field is contained in the attribute type. Use an asterisk (*) as the wildcard character. For example, for a value of a*, the Like operator matches all strings that begin with "a", and for a value of *a*, it matches all strings that contain "a".
- Not Like—String that you specify in the Value field is not contained in the attribute type. Use an asterisk (*) as the wildcard character. For example, for a value of a*, the Not Like operator matches all strings that do not begin with "a", and for a value of *a*, it matches all strings that do not contain "a".
- Not Equals—String that you specify in the Value field exactly matches any string except the string in the attribute type.
- Value (Required)—Enter a value for the type of attribute that you selected in the Attributes field:
- Alarm Text—Enter a text string.
- Alarm Type—Select a VOS alarm type.
- Count—Enter a number.
- Device Name—Select a device from the list of those being managed by the Director node.
- Severity—Select an alarm severity.
- Soak Time—(For Releases 22.1.1 and later.) Enter a time, in seconds.
- Wait—Enter the time to wait, in minutes.
- Click the
icon to add a condition.
- Click the
 icon to delete a condition.
icon to delete a condition. - Click Continue.
- To add a condition, click the
- Click Add.
Create VNF Manager
The Virtual Network Functions (VNF) manager IP is the IP address assigned to the Versa VNF manager, which is used to manage and monitor VNFs within a Versa SD-WAN environment.
To create a VNF manager:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Management Profiles.

- Click VNF Manager, and then enter the IP address/prefix of the SNMP server that you want to be able to poll the Versa Portal and receive its SNMP traps. Click the + Add icon to add an address.

- Click Add.
- Click the
 icon to delete the VNF manager.
icon to delete the VNF manager.
Create a Spoke Group
You can create spoke groups to help control direct traffic flow between the hubs, hub controllers, and specific branch spoke groups. You can create spoke groups templates on the Versa Portal dashboard and bind them to specific spoke device templates to allow the devices to participate in a spoke group topology.
A spoke group network configuration can be one of the following types:
- Spoke to Hub—Set up a connection between a spoke and a hub. There is no communication between spokes, either directly or through a hub. This type of configuration is preferred when the hub is used as a gateway to go out from the spoke site.
- Spoke to Spoke via Hub—Set up a connection between two spokes through a hub. There is no communication between the spokes directly. The spokes have a default route towards the hub. Spokes are blocked from importing routes directly from other spoke sites. The hub receives the routes from the spoke and exports them to other spokes.
- Spoke to Spoke Direct—Set up a direct connection between two spokes within a spoke group, bypassing a hub. One spoke can receive LAN routes directly from the other spoke. For this spoke group type, you need to add a community value.
The spoke devices that are a part of the same spoke group inherit the properties of the group.
To create a spoke group:
- Click Org Settings in the left menu bar to open the organization settings dashboard.
- Select Spoke Group, and then enter information for the following fields.

Field Description Name (Required) Enter a name for the spoke group. Spoke Group Type (Required) Select the type of spoke group:
- Spoke to Hub Only
- Spoke to Spoke via Hub
- Spoke to Spoke Direct
Community (Required) For the Spoke to Spoke Direct spoke group type, enter a community value. Region Select the region in which to place hub and hub controller devices that facilitate spoke-to-hub to hub-to-spoke communication. Hub or Hub Controller Select hub or hub controller. Priority Select the priority of the hub. - Click Add.
User Authentication Profiles
On Versa Portal, you can configure a number of authentication methods to authenticate end users, including using a Lightweight Directory Access Protocol (LDAP) server, Security Assertion Markup Language (SAML), a RADIUS profile, and Kerberos. This section describes how to configure LDAP, SAML, RADIUS, and Kerberos profiles to use for end user authentication.

You configure authentication profiles at the tenant (organization) level, and the same profile is available to be used for all devices in that organization. Versa Portal saves the profiles locally in the Versa Portal database. You can select the profiles when you configure a device, so you do not need to define same profile in multiple places on a device.
Configure LDAP Profiles
You configure an LDAP server profile to define how NGFW connects to and authenticates the Active Directory (AD) server, how it searches the Active Directory, and how it retrieves the group list and list of associated members. Before you begin the configuration process, ensure that you have the bind distinguished name (DN) authentication credentials and the bind password. You can get this information from the LDAP administrator.
For LDAP authentication to work, you must enable or disable SSL mode. If SSL mode is enabled, the LDAP session supports secure LDAP (LDAP over SSL) and start TLS (LDAP over TLS) modes. The LDAP server profile configuration accepts all the parameters needed to communicate with an external LDAP server.
You associate the LDAP authentication profile created when you create an authentication profile and authentication rule. Before you create an authentication profile, you must create an LDAP authentication profile.
User and group authentication provides a mechanism for verifying the identities of users so that only genuine users have access to applications. For each organization, you can configure one user or group profile in an LDAP server profile.
You can add custom filters for LDAP users or groups with the users and groups available in an LDAP server. Only the users or groups that are added using the custom filter can connect to the Versa SASE client, multitenant gateway, and remote access VPN devices. Note that you must enable appliance proxy for the SASE gateway, multitenant gateway, or remote access VPN to use the custom filter. To enable appliance proxy, see Enable Appliance Proxy for a Tenant.
To configure an LDAP server for Active Directory authentication and to configure a user and group mapping profile:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Authenticator.

- In the LDAP Server Profile page, enter information for the following fields.
Field Description LDAP Name (Required) Enter a name for the LDAP server profile. NGFW uses this name to connect to the LDAP directory to retrieve group mapping information and to select the usernames and group names for the profile. LDAP Server (Required) Click the
 icon. In the Server popup window, enter the following information for LDAP server, and then click Add.
icon. In the Server popup window, enter the following information for LDAP server, and then click Add.

- IP Address (Required)—Enter the IP address of the LDAP server.
- Port (Required)—Enter the number of the listening port on the LDAP server. This is the port that communicates with the LDAP directory service.
- Routing Instance—Select the routing instance to use to reach the LDAP server.
- FQDN—Enter the full domain name of the LDAP server.
SSL Mode Enabled (Required) Click to enable or disable SSL mode:
- Click Yes to use SSL for the LDAP session.
- Click No to not use SSL for the LDAP session.
SSL Mode (Required) Select the SSL mode for the LDAP session:
- LDAPS—Use secure LDAP (LDAP over SSL).
- Start TLS—Use LDAP over TLS.
CA Chain (Required) Select the Certificate Authority (CA) to use for the secure LDAP connection.
-
Custom—Click custom to upload a .crt file, and then click Browse file to upload your CA chain certificate.
-
Default—Click default to use the default CA chain certificate.
Bind-DN Name (Required) Enter the bind distinguished name (DN) authentication credentials for binding to the LDAP tree. Domain Name (Required) Enter the domain name in which the LDAP server resides. Bind-DN Password (Required) Enter the bind password. Base-DN (Required) Enter the base DN of the LDAP directory location. NGFW initiates a search for user and group information at this location. Bind Timeout (Required)
Enter the bind timeout period, in seconds.
Default: 30 seconds
Search Timeout Enter the search timeout period, in seconds.
Default: 30 seconds
User/Group (Group of Fields) - Name (Required)
Enter a name for the user and user group profile. - Group Object Class (Required)
Enter the group object class provided by your administrator. - Group Name (Required)
Enter the group name provided by your administrator. - Group Member (Required)
Enter the group member provided by your administrator. - User Object Class (Required)
Enter the user object class provided by your administrator. - User Name (Required)
Enter the format of the username. An example is User Principal Name. - Refresh Interval (Required)
Enter how often to refresh the profile, in seconds.
Range: 60 through 86400 seconds
Default: 60 seconds
Custom Filter (Group of Fields) - User
Enter the user details to filter from the LDAP profile user or group. - Group
Enter the group details to filter. - Region (Required)
Select a Versa Portal region. - Click Save.
Enable Appliance Proxy for a Tenant
You must enable appliance proxy from the tenant that uses the LDAP authenticator for the secure access client and associate with an LDAP profile.
To enable appliance proxy for SASE gateway or multitenant gateway:
- Click the Inventory icon in the left menu bar to open the Inventory dashboard.
- In the Device Type field, select SASE Gateway or Multitenant Gateway, and then click the Appliance Proxy toggle.

- In the Select LDAP Profile popup window, select the LDAP profile to associate, and then click Continue. The LDAP profile you choose must be the same as the LDAP profile used in the secure access template.

To enable appliance proxy for remote access VPN devices:
- Click the Inventory icon in the left menu bar to open the Inventory dashboard.
- In the Device Type field, select Active Licenses, and then click the Appliance Proxy toggle.

- In the Select LDAP Profile popup window, select the LDAP profile to associate, and then click Continue. The LDAP profile you choose must be the same as the LDAP profile used in the secure access template.

To view the devices associated with the LDAP profile, edit, or delete a LDAP profile from the profile list:
- Click the
 Device List icon to view the devices associated with the LDAP profile.
Device List icon to view the devices associated with the LDAP profile. - Click the
 Edit Profile icon to update the LDAP profile.
Edit Profile icon to update the LDAP profile. - Click the
 Delete icon to delete a LDAP profile.
Delete icon to delete a LDAP profile.
Configure SAML Profiles
Security Assertion Markup Language (SAML) authenticates users so that they can access multiple services and applications. SAML is useful when you want to access multiple services or applications when each service or application requires that you authenticate yourself. SAML is a standard for exchanging authentication between parties, and it is most commonly used for web browser–based single sign-on (SSO).
You can configure SAML SSO to log in using a single sign-on and then access multiple services and applications. Similarly, you can configure SAML single sign-out to end sessions for multiple services and applications and then log out from only one session. You can use SAML authentication for services and applications that are external or internal to your organization. A user can update their SAML profile and publish the updated configuration to all devices. You can attach a SAML profile to a secure access template for SASE or remote access server for authentication, and you can associate a SAML profile while creating an authentication rule.
To configure SAML, you configure a SAML profile, which contains information about the third-party SAML IDP and other protocol information.
To configure a SAML profile:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Authenticator.
- In the Select Authentication Method field, select Enterprise SAML Profile, and then enter information for the following fields.

Field Description SAML Name (Required) Enter a name for the SAML profile. Host (Required) Enter the name of the host to which to apply the SAML profile. Prefix ID (Required) Enter the name of the external IdP. Single Sign-on URL (Required) Enter the URL of the IdP to use for single sign-on. Single Sign-out URL(Required) Enter the URL to point to for single sign-out. SP Entity ID (Required) Enter the entity ID of the service provider (that is, the Versa Portal instance). IdP Entity (Required) Enter the entity ID that uniquely identifies the SAML identity provider. Upload SP Certificate Select the certificate that the service provider uses to authenticate and send a message to NGFW. NGFW uses this authentication information and provides access to the applications and services. Upload IdP Certificate (Required) Select the authentication certificate issued by the identity provider. The IdP and NGFW use this certificate to sign SAML messages. - Click Save.
To edit or delete a SAML profile from the profile list:
- Click the
 Device List icon to view the devices associated to the SAML profile.
Device List icon to view the devices associated to the SAML profile. - Click the
 Edit icon to update a SAML profile.
Edit icon to update a SAML profile. - Click the
 Delete icon to delete a SAML profile.
Delete icon to delete a SAML profile.
Configure RADIUS Profiles
RADIUS is a distributed client–server system that secures networks against unauthorized access. A RADIUS server provides an external database that authenticates users before allowing them to access a network, a device, or related services. You configure a RADIUS server and RADIUS profile attributes to authenticate a user. If you are using external RADIUS authentication, define the information that the authenticator uses to communicate with the RADIUS server.
You can associate a RADIUS profile while creating an authentication rule.
To configure RADIUS profile for user authentication:
- Click Org Settings in the left menu bar to open the organization settings dashboard, and then select Authenticator.
- In the Select Authentication Method field, select Enterprise RADIUS Profile, and then enter information for the following fields.
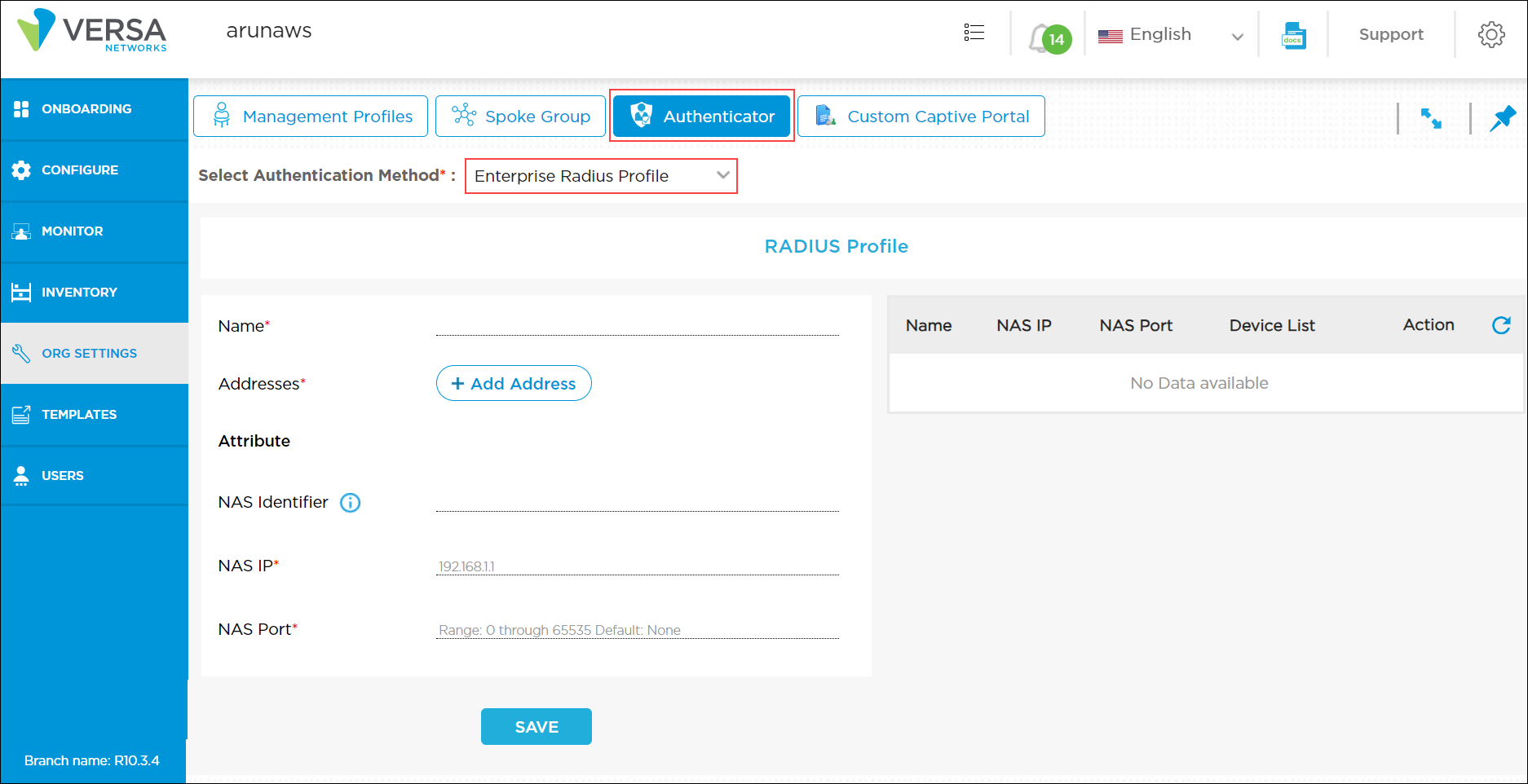
Field Description Name (Required) Enter a name for the RADIUS profile. Addresses (Required) Click the
 icon. In the Addresses popup window, enter the following information for the RADIUS server, and then click Add.
icon. In the Addresses popup window, enter the following information for the RADIUS server, and then click Add.

- IP Address (Required)—Enter the IP address of the RADIUS server.
- Port (Required)—Enter the number of the listening port on the RADIUS server. This is the port number to communicate with the RADIUS directory service.
Range: 0 through 65535
Default: None
- Shared Secret (Required)—Enter a password that the Versa Portal instance uses to access the RADIUS server.
- Routing Instance—Select the routing instance to use to communicate with the RADIUS server.
You can use the search option to find a RADIUS server from the list and do the following actions:
- Click the
 Edit Profile icon to update the RADIUS server details.
Edit Profile icon to update the RADIUS server details. - Click the
 Delete icon to delete a RADIUS server.
Delete icon to delete a RADIUS server.
Attribute - NAS Identifier
Enter a text string to identify the network access server (NAS) that originates the access request. - NAS IP (Required)
Enter the IP address of the NAS that is requesting authentication. - NAS Port (Required)
Enter the number of the physical port to use to connect to the NAS that is authenticating the user.
Range: 0 through 65535
Default: None
- Region (Required)
Select a Versa Portal region. - Click Save.
To view the devices associated to the RADIUS profile, edit, or delete a RADIUS profile from the profile list:
- Click the
 Device List icon to view the devices associated to the RADIUS profile.
Device List icon to view the devices associated to the RADIUS profile. - Click the
 Edit Profile icon to update the RADIUS profile.
Edit Profile icon to update the RADIUS profile. - Click the
 Delete icon to delete a RADIUS profile.
Delete icon to delete a RADIUS profile.
Configure Kerberos Profiles
Kerberos provides strong authentication for users and groups, an authentication that is stronger than LDAP. Kerberos uses secret key cryptography, so it never transmits user credentials over the network. To configure Kerberos, you must also configure decryption full proxy and web proxy in transparent mode.
To use Kerberos, you upload the keytab file generated from Active Directory. You use the Kerberos keytab file to authenticate systems and services that use Kerberos without having to enter a password. Note that because the keytabs are derived from the Kerberos password, if you change the Kerberos password, you must re-create all keytabs and import the keytab files to the device again.
You can associate a Kerberos profile with an authentication rule when you are creating the rule.
To define a Kerberos profile for authenticating a user and group:
- Click the Org Settings icon in the left menu bar to open the organization settings dashboard, and then select the Authenticator tab.
- In the Select Authentication Method field, select Kerberos Profile, and then enter information for the following fields.

Field Description Name (Required) Enter a name for the Kerberos profile. Keytab File Click the  icon and select the keytab file (.keytab) that you uploaded.
icon and select the keytab file (.keytab) that you uploaded.SPN (Required) Enter the value for the service principal name. Virtual URL (Required) Enter the Kerberos virtual URL. Note that the virtual URL must resolve through the appliance LAN IP address. Region (Required) Select a Versa Portal region. -
Click Save.
To view the devices associated to the Kerberos profile, edit, or delete a Kerberos profile from the profile list:
- Click the
 Device List icon to view the devices associated to the Kerberos profile.
Device List icon to view the devices associated to the Kerberos profile. - Click the
 Edit Profile icon to update a Kerberos profile.
Edit Profile icon to update a Kerberos profile. - Click the
 Delete icon to delete a Kerberos profile.
Delete icon to delete a Kerberos profile.
Configure Custom Captive Portal
Custom captive portal is not supported on AWS instances.
