Configure Security
![]() For supported software information, click here.
For supported software information, click here.
This article describes how you can configure firewall policies, secure traffic flow based on URL, set antivirus strength, tune the intrusion prevention system (IPS), and TLS decryption from the Security tab. You can customize security settings before or after you activate the device. TLS decryption is supported only when you enable advanced security settings. That is, you must enable firewall, security profile, antivirus, and intrusion prevention system to configure TLS decryption.
Configure Security Settings
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.

- Click Security Policy to open the Security settings screen.

You customize the following settings on the Configure > Security screen:
- Firewall Policies—Set firewall rules
- Security Profile Definition—Categorize URLs, configure reputation, antivirus, and intrusion prevention
Manage Firewall Policies
The Titan portal is preconfigured with default firewall rules. You cannot modify the default rules, but you can add new rules. When you create a rule for port-forwarding and IPsec route-based profiles, by default, Titan Portal creates a security rule that allows NAT and IPsec traffic, and the rule is displayed in the security rule list. For port forwarding, the security rule has a name in the format port_forwarding_rule_name_frd, and for an IPsec profile, the rule name is the same as the IPsec route-based profile name. You cannot edit or delete a system-generated default rule for port forwarding or for an IPsec profile. However, you can disable or reorder a default rule to change its priority.
To configure firewall settings:
- In the Firewall Policies section, click Firewall Rules to open the Configuration > Security > Firewall Rules screen.

Each rule displays a numbered circle indicating its position in the rule set. The circle color indicates whether a rule denies (red) or allows (green) traffic, or whether it applies one of the profiles listed in the Security Profile Definition section (purple). By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. The Block icon in the rule name indicates the rule is disabled.
Block icon in the rule name indicates the rule is disabled.
- To remove a rule, click the X icon in the rule name, then click Publish.
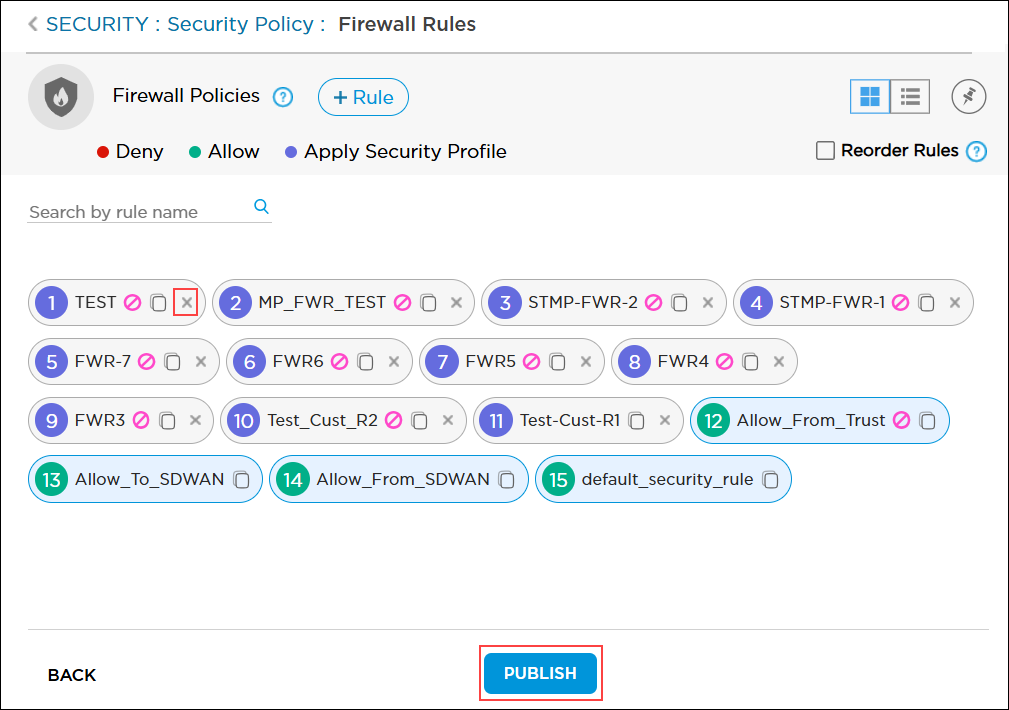
- To copy a rule and modify it as a new rule, click the
 Copy icon in the rule name, make the required changes to the rule, and then click Publish.
Copy icon in the rule name, make the required changes to the rule, and then click Publish.

- To remove a rule, click the X icon in the rule name, then click Publish.
- If needed, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- If needed, click + Rule to add a firewall rule.

- Enter information for the following fields.
Field Description Rule Name Enter a name for the rule, and then slide the toggle to enable the rule. Description Enter a text description for the rule. It can be a maximum of 63 characters. Match Criteria Select the Protocol, Address, Hostname, Application, URL, DSCP, or User and Group tab to add information about that criteria type. For more information, see Apply Match Criteria for Firewall Rules, below.
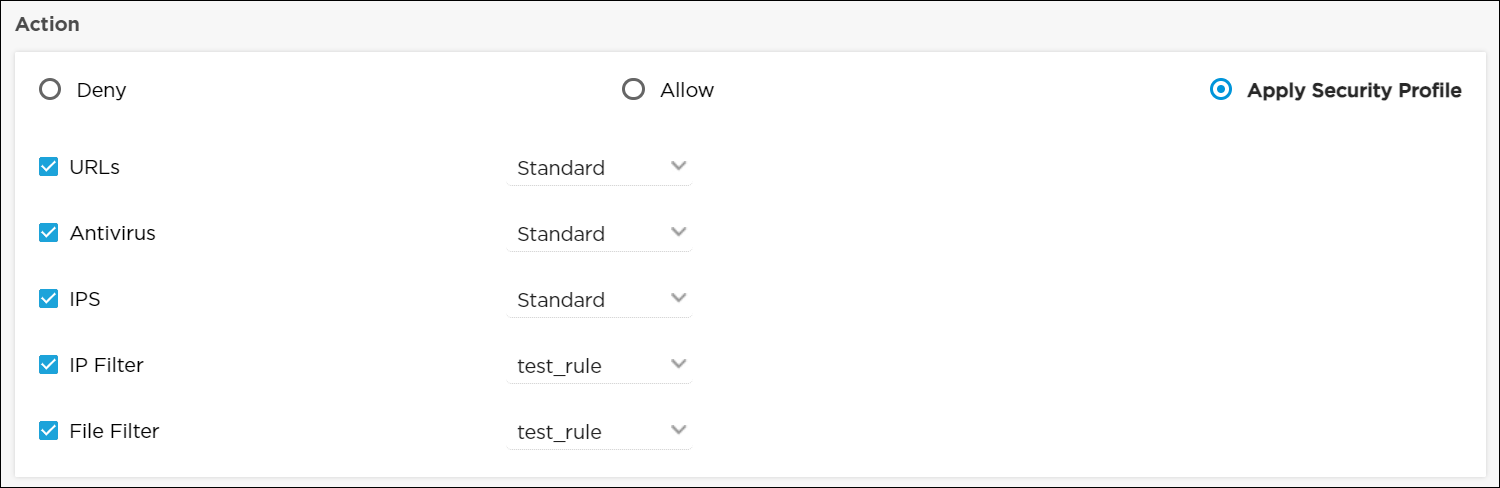
Scope (Group of Fields) - Source Zone
Click the down arrow in the Please Select field. A popup window displays the configured interfaces and tunnels. Choose a source zone, and then click Continue. To create a tunnel, see Configure IPsec VPN Settings.

- Arrow
Choose the type of connection:
 One-way
One-way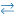 Two-way
Two-way
- Destination Zone
Click the down arrow in the Please Select field. A popup window displays the configured interfaces and tunnels. Choose a destination zone, and then click Continue. To create a tunnel, see Configure IPsec VPN Settings.

Action Choose the Deny, Allow, or Apply Security Profile action. When you click Apply Security Profile, a popup window displays.
Choose a level of security for each of the following:
- URLs
- Antivirus
- IPS
- IP Filter
- File Filter
The security level can be Low, Standard, or Advanced. For IP filter and file filter, IP filter and file filter profiles.
Logging Configure log settings:
- None—Click to perform no logging.
- Default—Click to use default logging.
- Custom—Click to configure logging to a customer log server. Based on the rule match, the device may sent a large number of log messages.

-
Please Select—If you select Custom, click the down arrow to select a log profile.
-
Event—Select an option to log the data.
-
Start—Log data at the start of each session.
-
End—Log data at the end of each session.
-
Both—Log data at the start and end of each session.
-
Never—Never log data.
-
-
To create a new custom flow logs profile, click
 . For more information, see Add Custom Logs Profile.
. For more information, see Add Custom Logs Profile. - Click Add to save the changes. The new rule appears on the Firewall Rules screen.
- Click Publish to save all firewall policies.
Click the following rules on the Security > Firewall Rules screen to view default firewall rules:
- Allow_From_SDWAN
- Allow_To_SDWAN
- Default_Security_Rule
- Default_security_wifi (if the device supports WiFi)
Note that you cannot edit a default rule.

The following video describes how to manage next-generation firewall policies.
Create a Firewall Rule for SASE Gateway
To create a firewall rule for Secure Access Service Edge (SASE) gateway:
- In the Firewall Policies section, click Firewall Rules to open the Configuration > Security > Firewall Rules screen.

Each rule displays a numbered circle indicating its position in the rule set. The color of the circle indicates whether a rule denies traffic (red), allows traffic (green), or whether a rule applies one of the profiles listed in the Security Profile Definition section (purple). By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. The Block icon in the rule name indicates the rule is disabled.
Block icon in the rule name indicates the rule is disabled.
- To remove a rule, click the X icon in the rule name, then click Publish.

- To copy a rule and modify as a new rule, click the
 Copy icon in the rule name, make required changes to the rule, and then click Publish.
Copy icon in the rule name, make required changes to the rule, and then click Publish.

- To remove a rule, click the X icon in the rule name, then click Publish.
- If needed, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- Click +Rule to add a new firewall rule, and then enter information for the following fields.

Field Description Rule Name Enter a name for the rule, and then slide the toggle to enable the rule. Description Enter a text description for the rule. It can be a maximum of 63 characters. Match Criteria Click Protocol, Address, Hostname, Application, URL, DSCP, or User and Group to add details for that criteria type. For more information, see Apply Match Criteria for Firewall Rules, below. Click the down arrow in the Please Select list to select the protocol.

Scope (Group of Fields) - Source Zone
Click the down arrow in the Please Select list. A popup window displays the zones that classify the traffic flows coming to the gateway from various sources.
Select a source zone, and then click Continue.
- Host—Click to match the traffic that originates from device itself (that is, non-transient traffic).
- Remote Client—Click to use as the ingress zone for the traffic coming from VSA clients.
- SD-WAN—Click for traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Trust (LAN)—Click to use LAN interfaces that are controlled by enterprises.
- Untrust (Internet)—Click to use for internet-facing WAN interfaces.
- Arrow
Choose a
 one-way or
one-way or 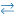 two-way connection.
two-way connection.- Destination Zone
Click the down arrow in the Please Select list. A popup window displays the zones that classify the traffic flows coming to the gateway from various sources.
Select a destination zone, and then click Continue.

- Host—Click to match the traffic that originates from device itself (that is, non-transient traffic).
- Remote Client—Click to use as the egress zone for the traffic coming from VSA clients.
- SD-WAN—Click for traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Trust (LAN)—Click to use LAN interfaces that are controlled by enterprises.
- Untrust (Internet)—Click to use for internet-facing WAN interfaces.
Action Choose Deny, Allow, or Apply Security Profile.
When you click Apply Security Profile, a popup window displays.

Choose a level of security for each of the following:
- URLs
- Antivirus
- IPS
- IP Filter
- File Filter
The security level can be Low, Standard, or Advanced. For IP filter and file filter, IP filter and file filter profiles.
Logging Click to configure logging:
- None—Click to perform no logging.
- Default—Click to use default logging.
- Custom—Click to configure logging to a customer log server. Based on the rule match, the device may sent a large number of log messages.

- Please Select—If you select Custom, click the down arrow to select a log profile.
- Event—Select an option to log the data.
-
Start—Log data at the start of each session.
-
End—Log data at the end of each session.
-
Both—Log data at the start and end of each session.
-
Never—Never log data.
-
To create a new custom flow logs profile, click
 . For more information, see Add Custom Logs Profile.
. For more information, see Add Custom Logs Profile. - Click Add to save the changes. The new rule appears in the Firewall Rules screen.
- Click Publish to save all firewall policies.
Click X in the icon to remove a rule, and then click Publish.
Default Firewall Rules for SASE Gateways
Titan Portal is preconfigured with default firewall rules for SASE gateways. You cannot edit or delete a system-generated default rule. However, you can disable a default rule and reorder a default rule to change its priority. You can also add a new rule.
When you upgrade a SASE gateway license, new default rules are not created, and the default rules present in the previous version are not deleted.
If you use Easy Quick Picks with the SASE gateway default security rule, the default security rules are lost.
The following are system-generated default firewall rule for SASE gateway, which you view by clicking Security > Security Policy > Firewall Rules:
- Allow From Hostbound On LAN
- Allow From SD-WAN
- Allow To SD-WAN
- Allow VSA Authentication
- Default Security Rule
- Default Security WiFi (for devices that support WiFi)
- Deny Remote Users To SD-WAN
- Remote User To Internet Block
- SWG (secure web gateway) Rule
- Versa Endpoint Client Rule
- VSA SWG Rule
For provider organizations, Titan Portal creates the default firewall rule Allow VSA Authentication to allow captive portal traffic.

For a tenant user, the following default firewall rules are provided depending on the license type:
| License Type | Default Rule Name | Description |
|---|---|---|
|
SWG Essential |
Deny Remote Users To SD-WAN | Block remote client from accessing an SD-WAN. |
| SWG Rule |
Allow remote client and SD-WAN to access untrusted internet sites. |
|
| SWG Professional | Deny Remote Users To SD-WAN |
Block remote client from accessing SD-WAN traffic. |
| SWG Rule | Allow remote client and SD-WAN to access untrusted internet sites. | |
| VSA Essential | Allow From Hostbound On LAN | Allow LDAP traffic to access an SD-WAN. This rule is created if you purchase VSA with Active Directory as the authentication method. |
| Remote User To Internet Block |
Block remote client from accessing the internet. |
|
| VSA Rule |
Allow remote client to access SD-WAN traffic. |
|
| VSA Professional | Allow From Hostbound On LAN | Allow LDAP traffic to an SD-WAN. This rule is created if you purchase VSA with Active Directory as the authentication method. |
| VSA Rule |
Allow remote client to access an SD-WAN and untrusted traffic. |
|
| SWG and VSA Essential | Allow From Hostbound On LAN |
Allow LDAP traffic to access an SD-WAN. This rule is created if you purchase VSA with Active Directory as the authentication method. |
| VSA SWG Rule | Allow remote client and SD-WAN traffic to access an SD-WAN and untrusted traffic. | |
| SWG and VSA Professional |
Allow From Hostbound On LAN
|
Allow LDAP traffic to access an SD-WAN. This rule is created if you purchase VSA with Active Directory as the authentication method. |
| VSA SWG Rule | Allow remote client and SD-WAN traffic to access SD-WAN and untrusted traffic. |
Apply Match Criteria for Firewall Rules
You can apply the following match criteria types in a security rule:
- Address
- Application
- DSCP
- Hostname
- Protocol
- URL
- User and Group
To specify the match criteria for a security rule:
- To specify protocol criteria for a security rule:
- Select the Protocol tab to display the protocol window.

- In the Please Select field, select a protocol. Titan Portal automatically populates the next field with common port numbers.
- If needed, click the port number field and edit the port number range.
- Select the Protocol tab to display the protocol window.
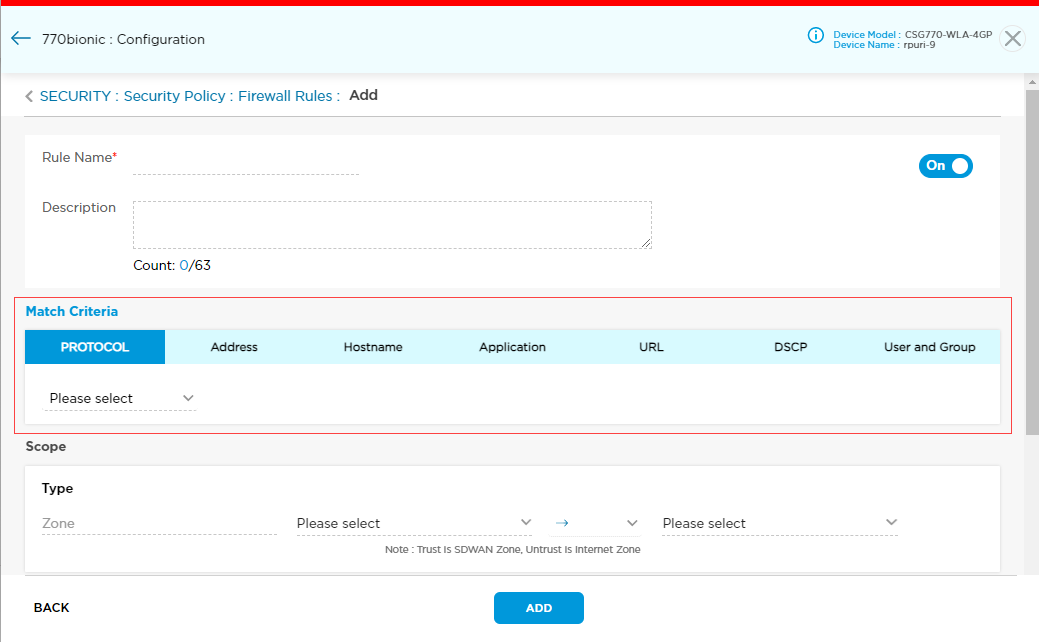
- To specify address criteria for a security rule:
- Select the Address tab to display the address window.

- Click the toggle switch to enter the source or destination IP address. Then click Source.
- Enter a source IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Enter a destination IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Select the Address tab to display the address window.
- To specify hostname criteria for a security rule:
- Select the Hostname tab to display the Hostname window.

- Click the toggle switch to enter the source or destination hostname. Then click Source.

- Enter a source hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue
- Enter a destination hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue.
- Select the Hostname tab to display the Hostname window.
- To specify application and application groups criteria for a security rule:
- Select the Application tab, and then click Click Here To Add or Modify Applications.

- The Firewall Rules > Add Application popup window displays. Select the Applications tab, then select the application to include in the match list, or type the name of the application in the search box and then select it from the search results. Then, click Add.

- Click + Custom Applications to create a new custom application object. For more information, see Add Custom Applications.
- Select the Application Groups tab, and then select predefined application groups to include in the match list, or type the name of the application group in the search box and then select it from the search results. Then, click Add.

- Select the Application tab, and then click Click Here To Add or Modify Applications.
- To specify URL criteria for a security rule:
- Select the URL tab to display the URL window.

- In the URL Category section, click Click Here To Add or Modify URLs to select URL categories.

- To add a new custom URL category object, click the
 icon. For more information, see Add Custom URL Categories.
icon. For more information, see Add Custom URL Categories. - Click the
 icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
- To add a new custom URL category object, click the
- Click Add.
- In the URL Reputation section, click Click Here To Add or Modify to select URL reputations.

- Click Continue. In the Customize option, modify the URL reputation.
- Select the URL tab to display the URL window.
- To specify DSCP criteria for a security rule, select the DSCP tab and then enter a DSCP value. DSCP allows you to classify and manage network traffic and to provide quality of service (QoS) in Layer 3 networks. It uses the 6-bit differentiated services code point (DSCP) field in the IP header to classify packets.

- By default, security enforcement is applied to all users and user groups. To change these settings, select the User and Group tab and do the following:

- Select a user to bind with the security policy:
• Any
• Known
• Selected
• Unknown - To select specific user and group, click Selected and do the following:
- Select an LDAP user group profile in the Select LDAP list.
- Use the search box to search for the user and group, or click the checkbox next to the user and group name.

- Click Add.
- Select a user to bind with the security policy:
To edit or delete a rule:
- In the Security > Rules tab, click a rule name to edit a rule.
- In the Security > Rules tab, click the X to delete a rule.
- Click Save to save the changes to the Titan cloud.
Configure Look Up URL Settings
- In the Configuration > Security Policy > Firewall Rules > Add Rules screen, select the URL tab in the Match Criteria section.
- In the URL Category section, click Click Here To Add or Modify URLs to select URL categories, and then click Look Up URL.

- In the Look Up URL search bar, enter a URL to look up the mappings to predefined or custom URL reputation and category. For example, enter www.google.com. The Look Up URL Result section displays information about the URL, including its category and reputation.

- Click Clear to clear the look up URL result.
- Click Back to return to the Add Rules screen.
Manage Security Profile Definitions
Security profile definitions contain three components:
- Antivirus settings
- Intrusion Prevention System (IPS) settings
- URL settings, including a deny URL and allow URL
You can manage individual components from the Security screen. You can enable or disable all components with one click from the Inventory menu. See Manage Device License Inventory.
To manage the security profile components:
- From the Configuration > Security tab, click the Security Policy to open the Security settings screen.

- Slide the toggle to turn individual security components on or off.
Configure a URL Deny List
Add websites to be blocked on the network so that users cannot access the sites. Add multiple websites by separating them with a comma.
To add URLs to a deny list:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- In the Security Profile Definition section, click Deny URLs to open the Configuration > Security > Deny URLs screen.

- Enter a single URL or enter multiple URLs separated by a comma.
- Click + Add URL to add URLs to the Deny URL list.
- Click Publish to save the settings.
To delete URLs from the list, click the X next to the URL.
Configure a URL Accept List
Add websites allowed on the network, even if blocked by other settings. Add multiple websites by separating them with a comma.
To add URLs to the accept list:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- In the Security Profile Definition section, click Allow URLs to open the Configuration > Security > Allow URLs screen.

- In the Security Profile Definition section, click Allow URLs to open the Configuration > Security > Allow URLs screen.
- Enter a single URL or enter multiple URLs separated by a comma.
- Click + Add URL to add URLs to the Allow URLs list.
- Click Publish to save the settings.
To delete URLs from the list, click the X next to the URL.
Configure URL Categories
To set a category filter for types of URLs to allow or block:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- Click a Category level to open the configuration screen for that level:
- Low
- Standard
- Advanced

- To add a new custom URL category object, click the
 icon. For more information, see Add Custom URL Categories.
icon. For more information, see Add Custom URL Categories. - Click the
 icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
- To add a new custom URL category object, click the
- Click to select the categories to Block or Alert & Confirm.
- Click Publish to save the settings.
Configure IP Reputation Filtering
To set a reputation filter for types of URLs to allow or block:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- Click a Reputation level to open the configuration screen for that level:
- Low
- Standard
- Advanced

- Click the
 icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
icon to enter a URL and to look up the mappings to predefined and custom URL reputations and categories. For more information, see Configure Look Up URL Settings.
- Click the
- Click to select the reputation level.
Field Description Red
Blocked Amber Ask Blue Allowed High-Risk IP Addresses IP addresses with a higher than average predictive risk for delivering attacks to infrastructure or endpoints.
Range: 1 through 20
Suspicious IP Addresses
IP addresses with a higher than average predictive risk for delivering attacks to infrastructure or endpoints.
Range: 21 through 40Moderate Risk Generally benign IP addresses that have exhibited some potential risk characteristics. There is some predictive risk that these IP addresses may deliver attacks to infrastructure or endpoints.
Range: 41 through 60Low Risk Benign IP addresses that rarely exhibit some characteristics that may expose infrastructure and endpoints to security risks. There is a low predictive risk of attack.
Range: 61 through 80Trustworthy Clean IP addresses that have not been tied to a security risk. There is a low predictive risk that infrastructure and endpoints may be exposed to attack.
Range: 81 through 100 - Click Publish to save the settings.
Configure Antivirus Protection
To choose where to apply antivirus protection:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- Click an Antivirus level to complete the configuration:
- Low—Web Traffic
- Standard—Email Attachment
- Advanced—Web and Email Attachment
- Click Publish to save the settings.
Configure Intrusion Prevention System
To configure IPS:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab.
- Click to choose an Intrusion Detection Protection level to open the configuration screen for that level:
- Low
- Standard
- Advanced
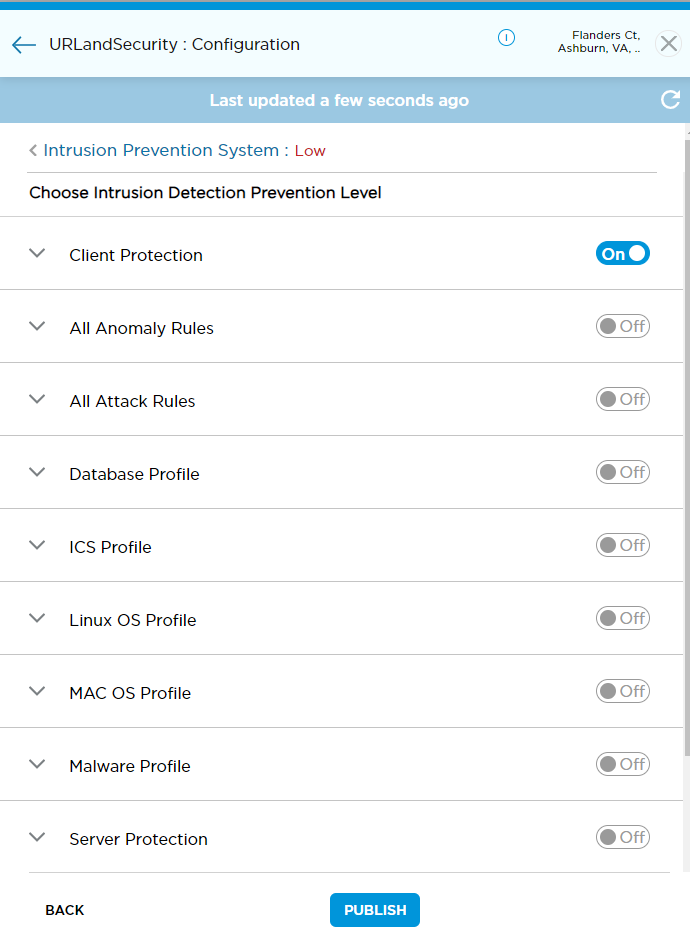
- Enter information for the following fields.
Field Description Choose Intrusion Detection Prevention Level Click the toggle to set attack detection level. The following values are the default settings for the selected Intrusion Detection Protection level:
- Low—Client Protection. Loads all client-side attack detection.
- Standard—Standard Recommended Profile. Recommended profile for adequate security and performance.
- Advanced—All attack rules. Loads all attack signatures.
All Anomaly Rules Load all the anomaly signatures. All Attack Rules Load all attack signatures. This is the default protection in the Advanced setting. Client Protection This profile loads all client-side attack detection. Database Profile Load the Oracle database server vulnerability signatures. ICS Profile Load the Industrial Control System (ICS) vulnerability signatures. Linux OS Profile Detect all attacks related to Linux OS. MAC OS Profile Detect all attacks related to MAC OS. Malware Profile Detect all antivirus attacks. Server Protection Detect server-side attacks. Standard Recommended Profile This profile is the one recommended by Versa for adequate security and performance. Windows OS Profile Detect attacks specific to Windows OS. - Click Publish to save the settings.
Configure Geolocation IP Filtering
Traffic passing through the network may have IP addresses that are associated with a bad reputation and that may cause security risk to your network. To block IP addresses based on IP address reputation and IP address metadata such as geolocation, you can configure IP address–filtering profiles and then associate them with security rules under apply security profile. Versa Networks provides a list of predefined regions that you can use to create IP-filtering profiles based on geolocation.
After a user creates geolocation IP-filtering profiles, you can associate the profile with any security firewall rule.
You can match the IP address based on the following match criteria:
- Destination IP address
- Source IP address
- Source and destination IP address
- Source or destination IP address
When a session's IP address matches the conditions in an IP-filtering profile, you can enforce the following actions:
- Allow
- Alert
- Drop packet
- Drop session
- Reject
To configure a geolocation IP filter:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab and then click Security Policy.
- In the Security Profile Definition section, click Geo IP Filter to open the Configuration > Security > Security Policy > Geo IP Filter screen.

To display the action color code, click the action color code icon.
action color code icon.

- Click +Profiles to add a new geolocation IP filter profile, and then enter information for the following fields.
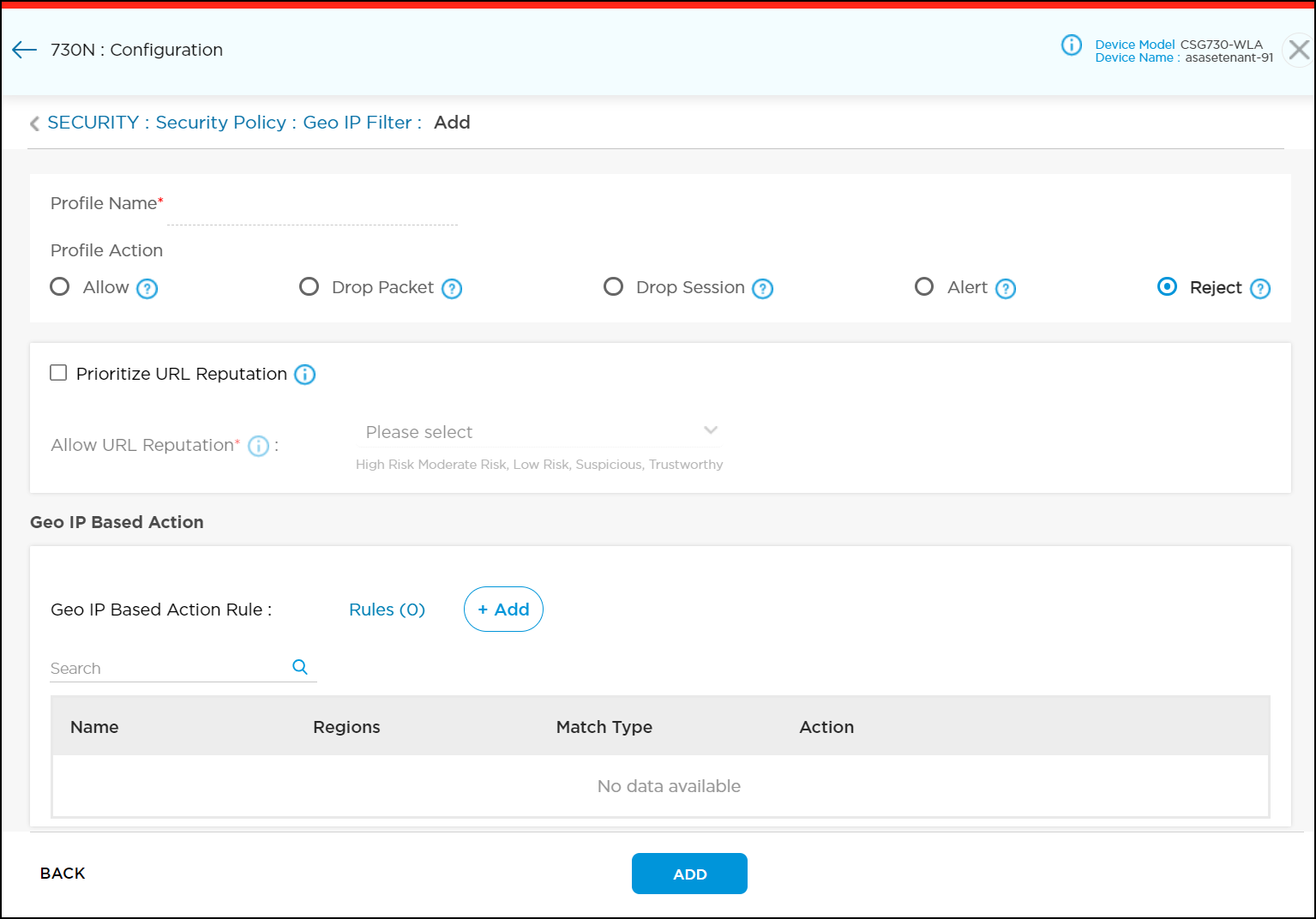
Field Description Profile Name (Required) Enter a name for the geolocation IP-filtering profile. Profile Action Select an action for geolocation reputation-based IP filtering.
- Alert —Allow the IP address, and generate an entry in the IP-filtering log.
- Allow —Allow the IP address, and do not generate an entry in the IP-filtering log.
- Drop packet —The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session —The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject —Send an ICMP unreachable message back to the client and resets the connection to the server.
Prioritize URL Reputation Click to prioritize the URL reputation over the IP reputation. When you select this option, instead of blocking the traffic in IP filtering based on reputation, traffic is further evaluated with URL filtering. The URL reputation correlates with an actual website. When you configure an IP-filtering profile that blocks traffic based on IP reputation, some legitimate websites may be blocked. When the URL reputation meets the threshold you select in the Allow URL Reputation field, prioritizing the URL reputation overrides the IP Reputation Action. - Allow URL Reputation (Required)
When you use Prioritize URL Reputation, select the priority to assign to the URL reputation when traffic is evaluated:
- High risk (Priority 4)
- Moderate risk (Priority 3)
- Low risk (Priority 2)
- Suspicious (Priority 1)
- Trustworthy (Priority 0)—Ignore a website that is labeled as one with a bad reputation, or ignore an HTTP/SSL URL reputation check that indicates a bad IP reputation.
Geo IP Based Action (Group of Fields) - Geo IP Based Action Rule
Click the
 icon to add actions for geographical reputation-based IP filtering. You can add multiple action rules.
icon to add actions for geographical reputation-based IP filtering. You can add multiple action rules.
- Name (Required)
Enter a name for the geo IP-based action rule. - Regions (Required)
Select the Geo IP-filtering region and then click Continue.

- Match Type
Select the match criteria for the IP address:
- Match only source IP address
- Match only destination IP address
- Match source and destination IP address
- Match source or destination IP address
- Action
Select an action for file-based action rule and click Add.
- Alert —Allow the IP address, and generate an entry in the IP-filtering log.
- Allow —Allow the IP address, and do not generate an entry in the IP-filtering log.
- Drop packet —The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session —The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject —Send an ICMP unreachable message back to the client and resets the connection to the server.
- Click Add.
Configure File Filtering
You can use file filtering to reduce the risk of attacks from virus and vulnerabilities that are associated with various types of files, thus decreasing an attacker's ability to attack your organization by sending unwanted or malicious files. File filtering is performed based on the file type and the hash of the file.
You can configure file filtering to block the transfer of potentially dangerous files and types of files (that is, files associated with specific applications), files of specific sizes, files associated with specific protocols, and files being sent in a particular direction. You can configure file filtering to perform reputation-based file hash lookups on a cloud server.
The file-filtering process is performed in the following sequence:
- Scan the early bytes of an incoming file, and identify the file type.
- Search the configured rules to check whether the file type, file size, protocol, and direction match one of the rules.
- If a match occurs, take the appropriate rule action.
- If no match occurs, perform a cloud lookup.
- Perform a cloud lookup, sending the hash of the file, to check the file's reputation.
- If the hash of the file is found, take the configure action. A hash can indicate that the file is clean, malicious, or suspicious.
- If the file matches none of these, take the default action defined in the file-filtering profile.
To configure file filtering:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb, and then click Configure to open the site information window.
- Click Next to open the Configuration > Network screen.
- Click the Security tab and then click Security Policy.
- In the Security Profile Definition section, click File Filters to open the Configuration > Security > Security Policy > File Filter ;screen.

To display the action color code, click the action color code icon.
action color code icon.

- Click +Profiles to add a new file-filtering profile, and then enter information for the following fields.

Field Description Profile Name (Required) Enter a name for the file-filtering profile. Description Enter a text description for the file-filtering profile. Protocol (Required) Select one or more protocols to filter the files:
- FTP
- HTTP
- IMAP
- MAPI
- POP3
- SMTP
Default Action Select the default action to take on a file that enters the network. The default action is taken when a file matches no entries in a deny list, an allow list, or a cloud lookup.
- Alert—Allow the file to pass and, if a LEF profile is configured, log the action.
- Allow—Allow the file to pass and log the action.
- Block—Do not allow the file to pass and, if a LEF profile is configured, log the action.
- Reject—Reset the connection to the server and client and, if a LEF profile is configured, log the action.
Logging Click to configure logging:
- None—Click to perform no logging.
- Default—Click to use the default logging.
- Custom—Click to configure logging to a customer log server. Based on the rule match, the device sends many log messages.

- Please Select—If you select Custom, click the down arrow to select a log profile. To create a new custom flow logs profile, click
. For more information, see Add Custom Logs Profile.
- Select the File-Based Action tab to configure file-filtering rules for file properties, such as file type, file size, protocol, and direction.

- Click the
 Add icon. In the Add File-Based Actions popup window, and then enter information for the following fields.
Add icon. In the Add File-Based Actions popup window, and then enter information for the following fields.

Field Description Name (Required) Enter a name for the file action. Description Enter a text description for the file action. File Size Enter a file size, in bytes. The file filter is applied to any file larger than this size.
Range: 0 through 4294967295 bytes
Default: None
File Type (Required) Click the Selected link to add the file type for which to apply the file filter. In the Selected File Type popup window, select the file types, and then click Continue. You can select multiple file types.

Protocol (Required) Click the Selected link to add the protocols to associate with the file transfer. In the Selected Protocol popup window, select the protocol, and then click Continue. You can select multiple protocols.

Direction (Required) Select the direction in which to apply the file filter:
- Download
- Upload
- Both
Action Select the default action to take on a file:
- Alert—Allow the file to pass and, if a LEF profile is configured, log the action.
- Allow—Allow the file to pass without logging the action.
- Block—Do not allow the file to pass and, if a LEF profile is configured, log the action.
- Reject—Reset the connection to the server and client and, if a LEF profile is configured, log the action.
- Select the Reputation-Based Action tab to configure file-filtering rules for cloud-based hash lookups, and enter information for the following fields.

Field Description Cloud Lookup Click to enable cloud lookup of a file for its reputation and select a file filter cloud profile. To add a new file filter cloud profile, see step 9a. Enable Logging Click to store logs. Action Select the default action to take on a file:
- Alert—Allow the file to pass and, if a LEF profile is configured, log the action.
- Allow—Allow the file to pass without logging the action.
- Block—Do not allow the file to pass and, if a LEF profile is configured, log the action.
- Reject—Reset the connection to the server and client and, if a LEF profile is configured, log the action.
- To add a new file filter cloud profile, click + File Filter Cloud Profile and enter information for the following fields.

Field Description Name (Required) Enter a name for the cloud profile. Description Enter a text description for the cloud profile. Source NAT List (Required) Select the SNAT pool to configure cloud lookup for file filtering. The SNAT pool is linked to a routing instance that connects to the cloud server.
To create an SNAT pool profile, click
 and enter information for the following fields.
and enter information for the following fields.

- Name (Required)—Enter a name for the SNAT pool.
- Egress Network (Required)—Select an egress network to associate with the SNAT pool.
Click Add, and then click Continue.
Connection Pool (Required) Enter the number of simultaneous connections to the SSL cloud server.
Range: 1 to 100000
Default: None
Timeout Enter the maximum timeout period to wait for a response from the SSL cloud server, in seconds.
Range: 1 through 4294967295 seconds
Default: 120 seconds
Activation Click the toggle to activate the cloud lookup profile. - Click Add. The cloud profile displays in the list.
- Click Add.
The following video describes how to manage security profile definitions.
Configure TLS Decryption
Transport Layer Security (TLS) decryption enforces security policies on encrypted traffic to prevent malicious content from entering the network and to protect sensitive data disguised as encrypted traffic from leaving the network. TLS decryption is supported only when you enable advanced firewall security settings and the professional license type. That is, you must enable a firewall, security profile, antivirus, and IPS to configure TLS decryption. This feature is available only when the device is activated and running.
The following table describes information about TLS certificate management.
| Certificate Management | MSP Provider Organization | MSP Tenant Organization | Branch or Hub | Notes |
|---|---|---|---|---|
| System-generated TLS decryption certificate | TLS decryption profile configured with default certificate. The certificate name and provider organization name are the same. | TLS decryption profile configured with default certificate. The certificate name and tenant organization name are the same. | TLS decryption profile configured with default certificate. The certificate name and tenant organization name are the same. | System generates TLS decryption certificate with the organization name using Versa root certificate. |
| User-generated TLS decryption certificate | User can upload their own certificate. | User cannot upload their own certificate. | User can upload their own certificate. | Only device owner can upload their own certificate. |
Prerequisites for TLS Decryption
Before you create a TLS decryption rule:
- Create a profile for decryption. To decrypt the TLS traffic to inspect for malware, you upload the certificate and its associated private key. By default, Titan provides a unique Versa-generated certificate and associated private key for every organization that you can download and install on the customer's end devices to connect to gateways. Alternately, you can use your own private key and certificate. To upload or download a certificate, see Upload a Certificate.
- For tenant organizations, you need to create a TLS decryption profile and rule. However, for provider organizations, default security rules are created and applied. You need to enable decryption and configure the URL category.
- Create a firewall rule without source and destination zones. The default destination port must be 44991 and 8080. If you have configured any other ports as part of captive portal, then you have to configure those ports as the destination ports for TLS decryption.
Configure TLS Decryption Profile
To decrypt or inspect traffic properties, you create an SSL decryption profile and associate it with a decryption policy rule. The decryption profile is applied to traffic that matches the decryption rule.
You can use two types of SSL proxies with a TLS decryption profile:
- SSL forward proxy—This is a transparent proxy that can decrypt and encrypt the SSL/TLS traffic between the client and the server. With a transparent proxy, neither the client nor the server knows about the proxy’s presence. Rather, the proxy acts as server towards the client and as a client towards the server.
Whether to decrypt can be controlled through the decryption policy. When the client initiates an SSL/TLS handshake towards the server, the proxy applies the decryption policy to determine whether the traffic needs to be decrypted. If the policy action is to decrypt, the proxy uses the matching SSL profile to initiate the SSL handshake towards the server, and the policy inspects the server certificate and other SSL attributes from the SSL handshake stream. If the inspection is successful, the proxy completes the SSL handshake with server and generates a server certificate signed with the public key specified in the SSL proxy profile, and it resumes the SSL handshake towards the client. After the SSL handshake between the client and the proxy completes, the proxy is able to decrypt application traffic sent by the client, Once decrypted, the traffic can be examined by the other services in the firewall service chain before before it is encrypted and sent to the server. - SSL full proxy—This proxy works in two modes, explicit and transparent:
- Explicit—Processes SSL/TLS traffic destined to a specific IP address and a specific port. On the client, you configure the proxy IP address and the port. The explicit SSL full proxy works as follows:
- The client connects to the configured proxy IP address and port and sends an HTTP Connect request.
- The SSL full proxy parses the HTTP Connect request and extracts the domain that the client wants to connect to. The proxy uses the domain and other Layer 3 and Layer 4 parameters to locate a decryption policy. If the proxy finds a decryption policy, it decrypts or bypasses the SSL connection based on the action in the policy. If there is no policy, decryption is bypassed.
- The SSL full proxy responds with a 200 OK message. When the proxy receives a client Hello message, if the policy decision was to decrypt, the SSL proxy responds with server Hello message and the remainder of the handshake message between the client and the proxy is exchanged.
- After the handshake completes, the client does a GET or a POST on the connection.
- The proxy parses the HTTP request and extracts the domain name and port from the URL. The proxy then performs a DNS resolution of that domain and opens a connection towards the resolved IP address using the source IP address and port from the configured SNAT pool referenced in the HTTP proxy profile.
- After the connection is successful, the proxy initiates the SSL handshake with the server and then forwards the HTTP request to the server.
- All the other services in the service chain, such as PS/IDS and antivirus, examine the decrypted stream to look for any threats, and they may drop the packet based on the outcome of their examination.
- Transparent—Processes SSL/TLS traffic destined to any IP address but to a specific port. The transparent process works the same was as the explicit process, except for the DNS resolution process. Because the destination IP address is the actual address of the server, the proxy skips DNS resolution, and DNS resolution is done on the client, and the client opens the connection to the server IP address. The proxy uses the SNAT pool configured in the HTTPS proxy profile to performs source NATing.
- Explicit—Processes SSL/TLS traffic destined to a specific IP address and a specific port. On the client, you configure the proxy IP address and the port. The explicit SSL full proxy works as follows:
To configure TLS decryption profile:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Decryption.

- Click the
 icon in the Profiles section to create a profile for decryption.
icon in the Profiles section to create a profile for decryption.
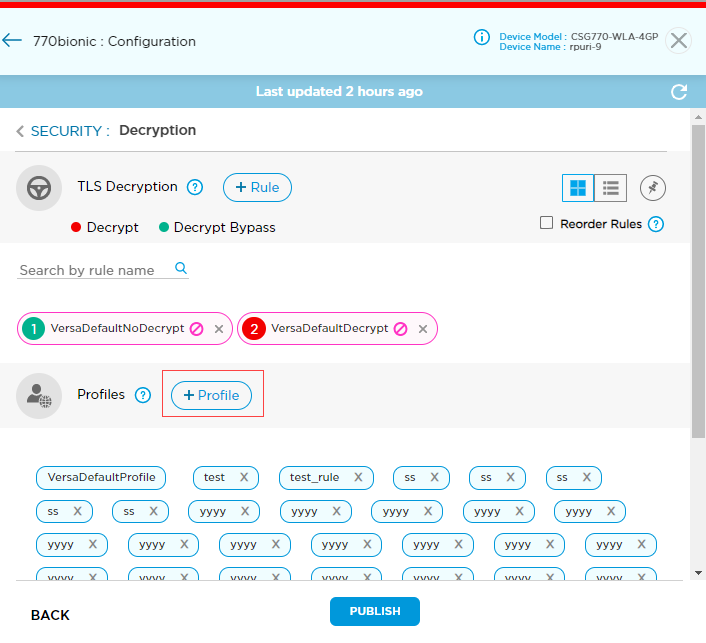
- In the Decryption Add window, enter information for the following fields.

Field Description Profile Name (Required) Enter a name for the decryption profile.
SSL Type Select the decryption type to use with the profile:
- SSL Forward Proxy
- SSL Full Proxy—This proxy works in one of two modes, explicit or transparent.

- Explicit—Click to process SSL/TLS traffic destined to a specific IP address and a specific port.
- Transparent—Click to process SSL/TLS traffic destined to any IP address but to a specific port.
- Match Rules—Displays the names of the configured match rules. To add a rule, click the
 Add Rule icon to enter the following information in the Match Rule window.
Add Rule icon to enter the following information in the Match Rule window.

- Rule Name (Required)—Enter a unique name for the rule.
- Routing Instance—Click the Routing Instance link. In the Routing Instance popup window, select a routing instance to associate with the match rule.

- Destination Ports (Required)—Click the Ports link. In the Destination Ports popup window, enter the port number to explicitly or transparently decrypt traffic originating from that port.

- Destination IP Prefix—For transparent decryption, click the Prefix link. In the Destination IP Prefix popup window, enter destination IP address prefix to match for connections.

- Destination IP Address—For explicit decryption, click the Address link. In the Destination IP Address popup window, enter destination IP address to match for connections.
Start TLS For SSL forward proxy decryption, select how to start the TLS connection:
- IMAP
- POP3
- SMTP
- User Extended Master Secret
Click to use the TLS extended master secret extension, This option helps to prevent man-in-the-middle attacks. CA Certificate Click to upload a certificate and its associated private key. In the Certificate List popup window, select the certificate and then click Continue.

If you need to upload your own certificate, you can add the key and then add the certificate for the provider organization. You cannot upload your own certificate for tenant organizations.
TLS Inspection - Restrict Certificate Extension
Click to restrict certificate extensions. Certificate Checks (Group of Fields) - Expired Certificate
Select the action to take when the server certificate expires:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject session—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Untrusted Issuer
Select the action to imply when the certificate is from an untrusted issuer:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject session—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
Mode Checks (Group of Fields) - Unsupported Cipher
Select the action to take when the decryption encounters an unsupported cipher:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Unsupported Key Length
Select the action to take when the decryption encounters an unsupported key length:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Unsupported Version
Select the action to take when the decryption encounters an unsupported CA version:
- Alert—Allow the decrypt session and generate an entry in the SSL log.
- Allow—Allow the decrypt session without generating an entry in the SSL log.
- Drop packet—The browser waits for a response from the server and then drops the packets. It is not possible to determine whether the packet was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Drop session—The browser waits for a response from the server and drops the session. It is not possible to determine whether the session was dropped because of a delayed response from the server or because a firewall blocked access to the website.
- Reject—The browser displays an alert and resets the connection to the server. It is not possible to determine whether this occurred because of a delayed response from the server or because a firewall blocked access to the website.
- Minimum Supported Key Length
Enter the minimum RSA key length, in bits.
Range: 512 through 65535
Default: 512
TLS Protocol Select the TLS protocol:
- Minimum Version—Select the minimum version of TLS protocol that is supported. The minimum version must be the same as or earlier than the maximum version.
- TLS 1.1
- TLS 1.2
- TLS 1.3
- Maximum Version—Select the maximum version of TLS protocol that is supported. The maximum version must be the same as or later than the minimum version. The options displayed depend on the version you select in the Minimum Version field. For example, if the minimum version is TLS 1.1, the options TLS 1.1, TLS 1.2, and TLS 1.3 are displayed. If the minimum version is TLS 1.2, the options TLS 1.2 and TLS 1.3 are displayed.
Key Exchange Algorithms When you select minimum and maximum TLS versions and the version is not TLS 1.3, select one or more key exchange algorithms for the SSL connection:
- ECDHE—Elliptic-curve Diffie–Hellman Key Exchange
- RSA—Rivest–Shamir–Adleman algorithm
Encryption Algorithms Select an encryption algorithm to use:
- AES-128-CBC—AES CBC encryption algorithm with 128-bit key
- AES-128-GCM—AES GCM encryption algorithm with 128-bit key
- AES-256-CBC—AES CBC encryption algorithm with 256-bit key
- AES-256-GCM—AES GCM encryption algorithm with 256-bit key
- Camellia-256-CBC—Camellia encryption algorithm with 256-bit key
- Chacha20-Poly1305—ChaCha stream cipher and Poly1305 authenticator
- Seed CBC—TLS RSA with seed CBC
Authentication Algorithms Click to have the selected LEF profile be the default LEF profile:
- SHA—Secure Hash Algorithm
- SHA-256—Secure Hash Algorithm 2 with 256-bit digest
- SHA-384—Secure Hash Algorithm 2 with 384-bit digest
Cipher Suites Select a TLS cipher suite. If you select a cipher suite, it must be consistent with the selected key exchange, encryption, and authentication algorithms. If you do not configure cipher suites, all cipher suites matching the selected the key exchange, encryption, and authentication algorithms are selected by default.
- TLS-AES-128-GCM-SHA256
- TLS-AES-256-GCM-SHA384
- TLS-CHACHA20-POLY1305-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SHA
- TLS-ECDHE-ECDSA-WITH-AES-128-CBC-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA
- TLS-ECDHE-ECDSA-WITH-AES-256-CBC-SHA384
- TLS-ECDHE-ECDSA-WITH-AES-256-GCM-SHA384
- TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256
- TLS-ECDHE-RSA-WITH-AES-128-CBC-SHA
- TLS-ECDHE-RSA-WITH-AES-128-CBC-SHA256
- TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
- TLS-ECDHE-RSA-WITH-AES-256-CBC-SHA
- TLS-ECDHE-RSA-WITH-AES-256-CBC-SHA384
- TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384
- TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256
- TLS-RSA-WITH-AES-128-CBC-SHA
- TLS-RSA-WITH-AES-128-CBC-SHA256
- TLS-RSA-WITH-AES-128-GCM-SHA256
- TLS-RSA-WITH-AES-256-CBC-SHA
- TLS-RSA-WITH-AES-256-CBC-SHA256
- TLS-RSA-WITH-AES-256-GCM-SHA384
- TLS-RSA-WITH-CAMELLIA-256-CBC-SHA
- TLS-RSA-WITH-SEED-CBC-SHA
Logging (Group of Fields) - None
Click to perform no logging. - Default
Click to use default logging. - Custom
Click to configure logging to a customer log server. Based on the rule match, the device may send many log messages.

- Please Select
If you select Custom, click the down arrow to select a log profile. To create a new custom flow logs profile, click  . For more information, see Add Custom Logs Profile.
. For more information, see Add Custom Logs Profile. - Click Add.
Configure TLS Decryption Rule
In a TLS ecryption rule, you define the traffic of interest, and for matching traffic you define whether to decrypt the traffic, inspect the traffic, or both decrypt and inspect it. Create a TLS decryption rule without source and destination zones, or only configure the destination zone.
To configure TLS decryption rule:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Decryption.

- Click the
 icon in the TLS Decryption section to create a rule for decryption.
icon in the TLS Decryption section to create a rule for decryption.

Each rule displays a numbered circle indicating its position in the rule set. Circle color indicates whether a rule decrypt (red) or decrypt bypass (green) traffic. By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. - If needed, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- In the Decryption Add window, enter information for the following fields.

Field Description Rule Name (Required) Enter a name for the decryption rule. Slide the toggle to enable or disable rules.
Description Enter a text description for the rule. It can be a maximum of 63 characters. Match Criteria Click Protocol, Address, Hostname, URL, or User and Group to add details for that criteria type. For more information, see Apply Match Criteria for TLS Decryption Rules, below.
Scope (Group of Fields) Select the traffic source and destination. - Source
Click the down arrow in the Please Select list. Select the source network security zone to which to apply the decryption policy rule to traffic coming from any interface in the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet-facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces that are on wireless networks.
Arrow Choose a  one-way or
one-way or  two-way connection.
two-way connection.- Destination
Click the down arrow in the Please Select list. Select the destination network security zone to which to apply the decryption policy rule to traffic coming from any interface into the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces that are on wireless networks.
Action Select the action to take on the traffic:
- Decrypt—Click to enable decryption.
- Decrypt Bypass—Click to bypass the decryption of SSL traffic that matches the predefined actions.
Select Profile If the action selected is decrypt, select the decryption profile. - Click Add.
Apply Match Criteria for TLS Decryption Rules
You can use the following match criteria types in a TLS decryption rule:
- Protocol
- Address
- Hostname
- URL
- User and Group

To specify match criteria for a TLS decryption rule:
- To specify protocol criteria for a TLS decryption rule:
- Select the Protocol tab to display the protocol window.

- In the Please Select field, select a protocol. Titan Portal automatically populates the next field with common port numbers.
- If needed, click the port number field and edit the port number range.
- Select the Protocol tab to display the protocol window.
- To specify address criteria for a TLS decryption rule:
- Select the Address tab to display the address window.

- Click the toggle switch to enter the source or destination IP address. Then click Source.

- Enter a source IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Enter a destination IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Select the Address tab to display the address window.
- To specify hostname criteria for a TLS decryption rule:
- Select the Hostname tab to display the Hostname window.

- Click the toggle to enter the source or destination hostname. Then click Source.

- Enter a source hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue
- Enter a destination hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue.
- Select the Hostname tab to display the Hostname window.
- To specify URL criteria for a TLS decryption rule:
- Select the URL tab to display the URL window.

- Enter the URL pattern, for example, https://google.*. You can save the URL patterns in .txt file format and add multiple .txt files separated by a comma. Click Browse File to add te file.
- In the URL Category section, select the URL categories to decrypt. Titan devices support a wide range of predefined URL categories that you can apply in different types of security policies. You can look up URL categories in the database of predefined URL database to determine the URL category. The predefined URL database is updated daily or in real time as part of security package (SPack) updates.

- To add custom URL category, click the
 icon. For more information, see Add Custom URL Categories.
icon. For more information, see Add Custom URL Categories. - To configure look up URL settings, click the
 icon. For more information, see Configure Look Up URL Settings.
icon. For more information, see Configure Look Up URL Settings.
- To add custom URL category, click the
- Click Add.
- In the URL Reputation section, select the URL reputation to decrypt and click Continue.

Use the Customize option to modify the URL reputation.
- Select the URL tab to display the URL window.
- By default, security enforcement is applied to all users and user groups. To change these settings, select the User and Group tab and do the following.

- Select a user to bind with the security policy: Any, Known, Unknown, or Selected.
- To select specific user and group, click Selected and then do the following:
- Select an LDAP user group profile from the Select LDAP list.
- Use the search box to search for the user and group, or click the check box next to the user and group name.

- Click Add.
Configure Authentication Rules
On Titan Portal, you can configure authentication rules to authenticate end users, including using a Lightweight Directory Access Protocol (LDAP) server, Kerberos, and Security Assertion Markup Language (SAML). This section describes how to configure authentication rules and associate LDAP, Kerberos, and SAML authentication profiles to use for end user authentication. To do this, you create an authentication rule in which you select the authenticator profile you created for the enforcement action.
If you create an authentication rule without creating an LDAP, Kerberos, or SAML authenticator profile, you must define an authenticator profile to use in the authentication rule.
If you use Kerberos authentication and you need access to users and user groups, you must add an LDAP authentication profile from the Org Settings menu on Titan Portal before you add a Kerberos authentication profile. To configure an authentication rule for a Kerberos profile authenticator, it is recommended that you have an LDAP authentication profile for the system to fetch users and user groups. When you create an authentication rule with a Kerberos profile, the system also pushes an LDAP profile to the CPE. If an LDAP profile does not exist, the system prompts you to create one when you select a Kerberos profile authenticator.
To configure an authentication rule:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Authentication.

- Click the
 icon in the Authentication section to create a rule for authentication.
icon in the Authentication section to create a rule for authentication.

Each rule displays a numbered circle indicating its position in the rule set. Circle color indicates whether a rule do not authenticate (red) or authenticate using a profile (green). By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. - If needed, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- In the Authentication Add window, enter information for the following fields.
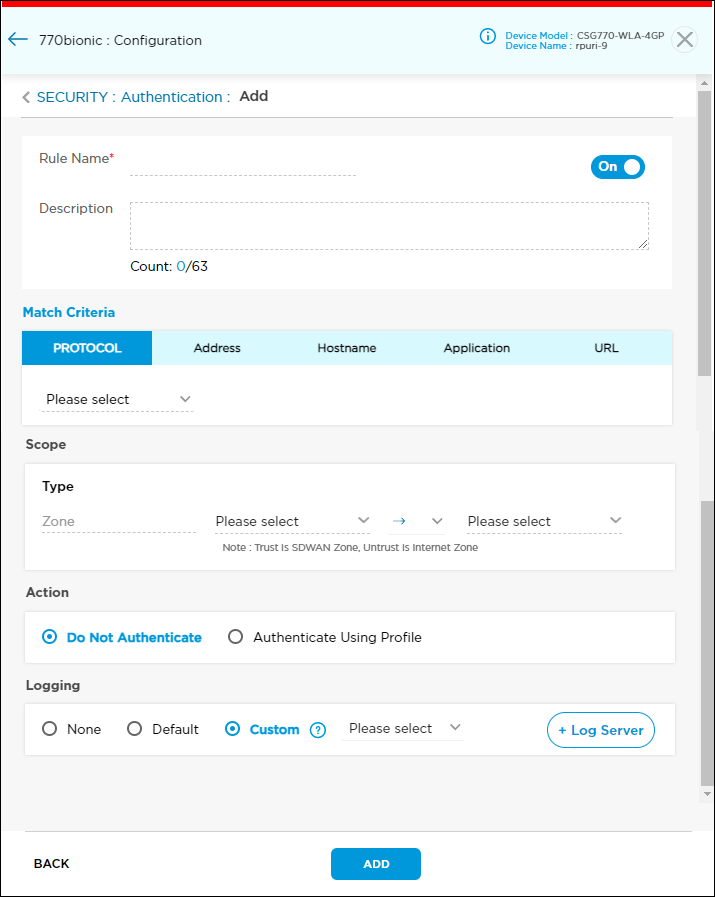
Field Description Rule Name (Required) Enter a name for the decryption rule. Slide the toggle to enable or disable rules.
Description Enter a description for the rule. The maximum characters allowed is 63. Match Criteria Click Protocol, Address, Hostname, Application, or URL to add details for that criteria type. For more information, see Apply Match Criteria for Authentication Rules, below.
Scope (Group of Fields) Select the traffic source and destination. - Source
Click the down arrow in the Please Select list. Select the source network security zone to which to apply the decryption policy rule to traffic coming from any interface in the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet-facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces on wireless networks.
Arrow Choose a  one-way or
one-way or 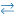 two-way connection.
two-way connection.- Destination
Click the down arrow in the Please Select list. Select the destination network security zone to which to apply the decryption policy rule to traffic coming from any interface into the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces on wireless networks.
Action Select the action to take on the profile:
- Do Not Authenticate—Click to not authenticate the profile.
- Authenticate Using Profile—Click to authenticate using an authentication profile. Enter information for the following fields.
- Cache Expiration—Enter the time, in minutes, after which cache for the authentication profile expires.
Default: 10 minutes - Concurrent Login—Enter the number of concurrent logins a user can perform from different devices.
- Expiration Mode—Select the mode to use to end a session:
- Fixed Interval—Use the time specified in the cache expiration as the time interval to end a session.
- Inactivity—Use the time specified in the cache expiration as the interval of inactivity after which to end a session.
- Authenticator
- Kerberos Profile—If you select Kerberos authentication, in the Select Authentication Profile list, select a Kerberos profile to associate with the authentication profile. Click + Authenticator Profile to add a new Kerberos profile. For more information, see Configure Kerberos Profiles.
- LDAP Profile—If you select LDAP authentication, in the Select Authentication Profile list, select an LDAP profile to associate with this authentication profile. Click + Authenticator Profile to add a new LDAP profile. For more information, see Configure LDAP Profiles.
- SAML Profile—If you select SAML authentication, in the Select Authentication Profile list, select a SAML profile to associate with this authentication profile. Click + Authenticator Profile to add a new SAML profile. For more information, see Configure SAML Profiles.
- Cache Expiration—Enter the time, in minutes, after which cache for the authentication profile expires.
Logging Configure log settings:
- None—Click to perform no logging.
- Default—Click to use default logging.
- Custom—Click to configure logging to a customer log server. Based on the rule match, the device may sent a large number of log messages.

- Please Select—If you select Custom, click the down arrow to select a log profile.
To create a new custom flow logs profile, click
 . For more information, see Add Custom Logs Profile.
. For more information, see Add Custom Logs Profile. - Click Add.
Apply Match Criteria for Authentication Rules
You can use the following match criteria types in an authentication rule:
- Address
- Application
- Hostname
- Protocol
- URL

To specify match criteria for an authentication rule:
- To specify protocol criteria for an authentication rule:
- Select the Protocol tab to display the protocol window.

- In the Please Select field, select a protocol. Titan Portal automatically populates the next field with common port numbers.
- If needed, click the port number field and edit the port number range.
- Select the Protocol tab to display the protocol window.
- To specify address criteria for an authentication rule:
- Select the Address tab to display the address window.

- Click the toggle switch to enter the source or destination IP address. Then click Source.
- Enter a source IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Enter a destination IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Select the Address tab to display the address window.
- To specify hostname criteria for an authentication rule:
- Select the Hostname tab to display the Hostname window.

- Click the toggle to enter the source or destination hostname. Then click Source.

- Enter a source hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue
- Enter a destination hostname, and then click the
 icon. To remove a hostname from the list, click the
icon. To remove a hostname from the list, click the  icon.
icon.

- Click Continue.
- Select the Hostname tab to display the Hostname window.
- To specify application and application groups criteria for an authentication rule:
- Select the Application tab, and then click Click Here To Add or Modify Applications.

- The Authentication > Rules > Add Application popup window displays. Select the Applications tab is selected by default. Then, select the application to include in the match list, or type the name of the application in the search box and then select it from the search results, and then click Add.

- Click + Custom Applications to create a new custom application object. For more information, see Add Custom Applications.
- Select the Application Groups tab. Then select predefined application groups to include in the match list, or type the name of the application group in the search box and then select it from the search results, and then click Add.

- Select the Application tab, and then click Click Here To Add or Modify Applications.
- To specify URL criteria for an authentication rule:
- Select the URL tab to display the URL window.

- Enter the URL pattern, for example, https://google.*. You can save the URL patterns in .txt file format and add multiple .txt files separated by a comma. Click Browse File to add te file.
- In the URL Category section, select the URL categories to decrypt. Titan devices support a wide range of predefined URL categories that you can apply in different types of security policies. You can look up URL categories in the database of predefined URL database to determine the URL category. The predefined URL database is updated daily or in real time as part of security package (SPack) updates.

- To add custom URL category, click the
 icon. For more information, see Add Custom URL Categories.
icon. For more information, see Add Custom URL Categories. - To configure look up URL settings, click the
 icon. For more information, see Configure Look Up URL Settings.
icon. For more information, see Configure Look Up URL Settings.
- To add custom URL category, click the
- Click Add.
- In the URL Reputation section, select the URL reputation to decrypt and click Continue.

Use the Customize option to modify the URL reputation.
- Select the URL tab to display the URL window.
- Click Add.
Example: Configure a SAML Authentication Rule
Before you create a SAML authentication rule, you must configure a SAML profile, which contains information about the third-party SAML IdPs and other protocol information. Then, you associate the SAML profile with the SAML authentication rule.
To create a SAML authentication rule, you perform the following tasks:
- Create three authentication rules in the following order:
- Create an authentication rule to allow DNS packets.
- Create an authentication rule to allow IdP packets.
- Create a SAML authentication rule.
- Create a firewall rule without source and destination zones and destination port must be 44991 and 8080.
- Create a TLS decryption rule without source and destination zones.
To create a SAML authentication rule:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Authentication.

- Click the
 icon in the Authentication section to create a rule for authentication.
icon in the Authentication section to create a rule for authentication.

Each rule displays a numbered circle indicating its position in the rule set. Circle color indicates whether a rule do not authenticate (red) or authenticate using a profile (green). By default, the rules are displayed in grid view. To change the view to list, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. - If needed, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- In the Authentication Add window, create an authentication rule to allow DNS packets by entering the following information.

- Enter a firewall rule name.
- Enter the description for the rule.
- In the Protocol tab, select UDP, and enter 53 as the port number.
- In the Action section, click Do Not Authenticate.
- Click Add.
- Click the
 icon in the Authentication section to create a rule for authentication.
icon in the Authentication section to create a rule for authentication. - In the Authentication Add window, create an authentication rule to allow IdP packets by entering the following information.

- Enter an OKTA IdP rule name.
- Enter the description for the rule.
- Click URL tab, enter a URL pattern, an then click the
 Add icon.
Add icon. - In the Action section, click Do Not Authenticate.
- Click Add. The OKTA IdP rule is added to the rules list.
- Click the
 icon in the Authentication section to create a rule for SAML authentication.
icon in the Authentication section to create a rule for SAML authentication. - In the Authentication Add window, create a SAML rule by entering the following information.

- Enter a SAML authentication rule name.
- Enter a rule description.
- Select source and destination zones.
- In the Actions section, click Authenticate Using Profile to authenticate using an authentication profile. Enter information for the following fields.
- Cache Expiration—Enter the time, in minutes, after which cache for the authentication profile expires.
Default: 10 minutes - Concurrent Login—Enter the number of concurrent logins a user can perform from different devices.
- Expiration Mode—Select the mode to use to end a session:
- Fixed Interval—Use the time specified in the cache expiration as the time interval to end a session.
- Inactivity—Use the time specified in the cache expiration as the interval of inactivity after which to end a session.
- In the Authenticator section, click SAML Profile, and in the Select Authentication Profile list, select a SAML profile to associate with this authentication profile. Click + Authenticator Profile to add a new SAML profile. For more information, see Configure SAML Profiles.
- Cache Expiration—Enter the time, in minutes, after which cache for the authentication profile expires.
- Click Add.
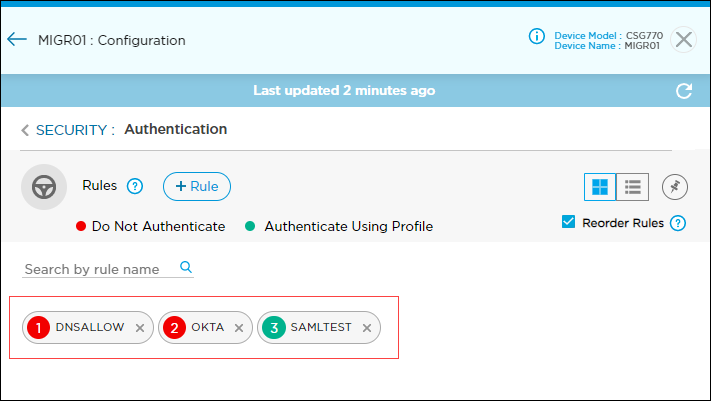
- In the Security tab, click Security Policy.
- In the Firewall Policies section, click Firewall Rules and then click +Rule to create a firewall rule. Enter the following information.

- Enter a firewall rule name.
- Enter a rule description.
- In the Protocol tab, select TCP, and enter 44991 and 8080 as the port numbers.
- Click Add.
- In the Security tab, click Decryption.
- In the TLS Decryption section, click +Rule to create a decryption rule. Enter the following information.

- Enter a decryption rule name.
- Enter a rule description.
- In the Protocol tab, select TCP, and enter 443 as the port number.
- Select a decryption profile.
- Click Add.
Configure DoS Protection
You can configure Titan devices to detect and mitigate denial-of-service (DoS) attacks. A DoS attack is an attempt to disrupt network services and deny network access by overloading the network with unnecessary traffic using multiple sources. DoS protection is supported only with the secure application optimization and advanced security license types. The enterprise security license users must upgrade the security license to enable the DoS protection feature.
Note: Protection against DoS attacks is resource intensive, so use it only for critical systems and enable it only for the subnet or subset of servers that need protection.
When a malicious entity launches a DoS attack by flooding the network with a high volume of traffic. The intent of the attack is to exhaust the hardware and software resources. As a result, the network becomes unavailable for its intended users. DoS attacks attempt to do the following:
- Divert high-volume traffic from multiple sources to the network
- Create unnecessary TCP sessions
- Flood the network
- Scan ports
- Sweep the host
- Attack the network with packet-based methods
To defend against such attacks, you configure DoS protection policies and profiles to detect and prevent zone-based or endpoint-based DoS attacks.
In a DoS policy, you define match criteria to separate the incoming traffic into fine-grained traffic streams. For example, you can specify criteria to match all traffic originating from the internet and destined to a specific web server. As another example, you can specify criteria to match all traffic originating from within an enterprise that is destined towards a data center resource like a file server. The following criteria can be used to match traffic in a DOS policy:
- Source zone
- Destination zone
- Source address
- Destination address
- IP headers
- TCP and UDP services
To apply DoS protection, you define DoS protection profiles, and then you reference the profile in a DoS protection policy. DoS protection profiles monitor thresholds for various protocols based on an endpoint-classified or aggregate basis. The Versa security appliance monitors the traffic rate for the various traffic protocols that matches the above match criteria and enforces the mitigation actions when the configured thresholds exceed. For TCP SYN flood, the enforcement actions allow for allow, alert, random early drop or TCP SYN cookies.
The DoS protection profile specifies:
- Maximum number of sessions.
- Profile type—Type of DoS protection profile:
- Aggregate profile—Applies the thresholds in the DoS protection profile to all the packets that match the rule criteria with which this profile is associated.
- Classified Profile—Applies the threshold configured in the profile to all the packets that match the classification criteria.
- Classification key—For a classified profile, the classification key allows you to classify the attack based on the source IP address, the destination IP address, or both the source and destination IP addresses.
An aggregate DoS protection profile monitors the thresholds configured for various protocols for all the traffic that matches the rule in the DoS policy. The aggregate DoS profile is useful to defend against DoS attacks targeted across an entire subnet (instead of endpoints based on specific IP addresses) and the source of the DoS traffic spans a wide range of IP addresses.
In a classified DoS profile, you set the classification key to source and destination IP address to monitor the thresholds based on a per-source and destination IP address basis. The rate at which packets are received is tracked per-protocol, per-source-and-destination-IP-address. You use classified DoS profiles to defend against DoS attacks targeted against specific endpoint hosts, based on the destination IP address or to narrow down the source of the DoS traffic to a few source IP addresses.
- If the DoS profile is configured as classified type then the thresholds configured for the various protocols are monitored based on the classification key for the traffic that matches the rule in the DoS policy.
- If the classification key is set to source IP address then the thresholds are monitored based on a per-source-IP-address. The rate at which packets are received is tracked per-protocol, per-source-IP-address.
- If the classification key is set to destination IP address then the thresholds are monitored based on a per-destination-IP-address basis. The rate at which packets are received is tracked per-protocol, per-destination-IP-address.
A DoS policy allows you to control the number of sessions between interfaces, zones, addresses and region. You can configure the DoS protection profile to define the flood thresholds for these protocols:
- ICMP
- ICMPv6
- Other IP
- SCTP
- TCP
- UDP
Configure a DoS Protection Profile
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Denial of Service (DoS) Policy.

- Click the
 icon in the DoS Profiles section to create a profile for DoS.
icon in the DoS Profiles section to create a profile for DoS.

- In the DoS Profile Add window, enter information for the following fields.

Field Description Name (Required) Enter a name for the DoS protection profile. Description Enter a text description for the profile. Type Select the type of profile:
- Aggregate Profile—Applies the thresholds in the DoS protection profile to all the packets that match the rule criteria with which this profile is associated.
- Classified Profile—Applies the threshold configured in the profile to all the packets that match the classification criteria.
- Classification Key (Required)
For a classified profile, select the key to classify the attack:
- Destination IP Only—Apply the DoS profile on the destination IP address of the attack.
- Source IP Only—Apply the DoS profile on the source IP of the attack.
- Source and Destination IP—Apply the DoS profile on both the source and destination of the attack.
- Maximum Sessions
Enter the maximum number of sessions to allow for traffic that meets the DoS protection rule to which this DoS profile is applied.
Range: 1 through 4194304
Flood Protection (Group of Fields) Enter the following information for each protocol for which you want to enable flood protection. - Enable
Click the checkbox in the Enable column to enable flood protection for a protocol. - Alarm Rate
Enter the threshold rate at which to generate a DoS alarm, in packets per second (pps).
Range: 1 through 20000000 pps
Default: 100000 pps
- Activate Rate
Enter the threshold rate at which to activate a DoS response, in pps.
Range: 1 through 20000000 pps
Default: 100000 pps
- Maximum Rate
Enter the threshold rate of incoming packets, in pps. When this threshold is exceeded, all packets are dropped.
- For aggregate DoS protection profile, this limit applies to all the traffic processed by the DoS protection rule with which this DoS protection profile is associated.
- For classified DoS protection profile, this limit applies to the traffic on a classified basis (based on the source IP address, destination IP address, or both), for the traffic processed by the DoS protection rule with which this DoS protection profile is associated.
Range: 1 through 20000000 pps
Default: 100000 pps
- Drop Period
Enter the duration, in seconds, when offending packets are dropped. Traffic dropped during this time is not counted when triggering an alert.
Range: 1 through 18000 seconds
Default: 300 seconds
- Action
Select the action to take when the active rate threshold is breached:
- Random Early Drops—Randomly drop packets.
- SYN Cookies—Generate an acknowledgment, and ensure that the connection is not dropped during a SYN flood attack.
Default: SYN Cookies
- Click Add.
Configure a DoS Policy Rule
A DoS policy consists of a set of rules, where each rule specifies the traffic match criteria and the action to take on matching traffic. The rules are evaluated in order, starting with the first rule. When traffic matches a rule, the action for that rule is applied, and none of the remaining rules are evaluated.
To create a DoS protection policy rule:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb and click Configure to open the site information window.
- Click the Security tab, and then click Denial of Service (DoS) Policy.

- Click the
 icon in the TLS Decryption section to create a rule for decryption.
icon in the TLS Decryption section to create a rule for decryption.

Each rule displays a numbered circle indicating its position in the rule set. The circle color indicates whether a rule is to deny (red), bypass (green), or protect (blue) traffic. By default, the rules are displayed in grid view. To change to list view, click the list view icon. To pin the view to grid or list for the login session, use the pin icon. The Block icon in the rule name indicates the rule is disabled.
Block icon in the rule name indicates the rule is disabled. - To reorder the rules, click Reorder Rules.
- To change the position of a rule in the order, click the colored circle for the rule and drag it to a different position in the rule set. The rule numbers update automatically.
- Click Publish Reordered Rules to save the changes to the Titan cloud.
- In the Decryption Add window, enter information for the following fields.

Field Description Name (Required) Enter a name for the DoS rule. Slide the toggle to enable or disable rules.
Description Enter a text description for the DoS rule. Match Criteria Click Protocol, Address, Region, or Header/Service to add details for that criteria type. For more information, see Apply Match Criteria for DoS Rules, below.
Scope (Group of Fields) Select the traffic for source and destination zones. - Source
Click the down arrow in the Please Select list. Select the source network security zone to which to apply the DoS policy rule to traffic coming from any interface in the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet-facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces that are on wireless networks.
- Arrow
Choose a
 one-way or
one-way or  two-way connection:
two-way connection:- Single arrow shows the traffic direction that checks match conditions from source to destination in one direction.
- Dual arrow shows the traffic direction that checks match conditions on both directions source to destination and destination to source.
- Destination
Click the down arrow in the Please Select list. Select the destination network security zone to which to apply the DoS policy rule to traffic coming from any interface into the zone, and then click Continue.

- SD-WAN—Select for the traffic coming to the gateway over overlay tunnels from remote SD-WAN branches.
- Untrust (Internet)—Select for internet facing WAN interfaces.
- Wired LAN—Select for LAN interfaces that are controlled by enterprises.
- Wireless LAN—Select for LAN interfaces that are on wireless networks.
DoS Profile Select the DoS profile:
- Aggregate Profile
- Classified Profile
Action Select an action to take for packets that match the DoS protection policy rule:
- Allow—Permit the packets.
- Deny—Drop the packets.
- Protect—Enforce protection on the packets defined in the DoS protection profile that match the rule. These packets are compared with the configured threshold rates to determine whether to trigger an alarm, activate another action, or drop a packet when the threshold rate is exceeded.
Logging (Group of Fields) - None
Click to perform no logging. - Default
Click to use default logging. - Custom
Click to configure logging to a customer log server. Based on the rule match, the device may send many log messages.

- Please Select
If you select Custom, click the down arrow to select a log profile. To create a new custom flow logs profile, click  . For more information, see Add Custom Logs Profile.
. For more information, see Add Custom Logs Profile. - Click Add.
Apply Match Criteria for DoS Rules
You can use the following match criteria types in a DoS policy rule:
- Protocol
- Address
- Region
- Header/Service

To specify match criteria for a DoS rule:
- To specify protocol criteria:
- Select the Protocol tab to display the protocol window.

- In the Please Select field, select a protocol. Titan Portal automatically populates the next field with common port numbers.
- If needed, click the port number field and edit the port number range.
- Select the Protocol tab to display the protocol window.
- To specify address criteria:
- Select the Address tab to display the address window.

- Click the source or destination toggle switch to enter the source or destination IP address.

- Click Source, and enter a source IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue.
- Click Destination, and enter a destination IP address in CIDR format, and then click the
 icon. To remove an IP address from the list, click the
icon. To remove an IP address from the list, click the  icon.
icon.

- Click the Negate toggle switch to select any addresses except the configured addresses.
- Click the Import icon to enter multiple IP addresses separated by commas, and then click Update. Note that this overwrites any existing IP addresses.

- Click Continue
- Select the Address tab to display the address window.
- To specify region criteria:
- Select the Region tab to display the source and destination region window.

- Click the source or destination toggle switch to enter the source or destination location.

- In the Select Regions for Location window, select one or more regions. If you want to select all regions, click Select All.

- Click Continue.
- Select the Region tab to display the source and destination region window.
- To specify match criteria based on the contents of the IP packet header and to set a time at which to apply the policy for a DoS rule:
- Select the Header/Service tab.

- Enter a differentiated services code point (DSCP) value.
- Select whether data packets can be fragmented:
- Don't Fragment
- More Fragments
- Click Service to select services to allow or block. In the window below, select one or more services. A service is defined based on the destination address and port.

- Click Continue.
- Select the Header/Service tab.
Supported Software Information
Releases 11.2 and later support all content described in this article.
Additional Information
Manage Device Inventory
Manage Organization Settings
Configure WAN Connections
