Configure Routing
![]() For supported software information, click here.
For supported software information, click here.
From the Routing tab, you can configure static routing and the OSPF and EBGP routing protocols. You can customize route redistribution for each routing protocol.
Configure Static IP Routes
Static routes are used to manually specify the path that data packets take to reach a destination. Note that if you create static routes to use to leak routes between VRFs, you must also create a firewall rule that allows this traffic to pass through. You do this by selecting match criteria and the correct zone scope interface VRF names for both VRFs.
Note: For SASE or multitenant gateway tenants, you must configure an allow firewall rule at the provider level with no source zone so that router-generated traffic, including traffic generated by ICMP, TCP, and UDP, can be transmitted.
Note: You can configure IP SLA monitor objects and monitor groups for SASE gateway and multitenant gateway tenants using the Monitor option in the Advance Configuration window in this section.
To configure a static IP route to a destination:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb, and then click Configure to open the site information window.

- Click the Routing tab, and then click the Static tab. Enter information for the following fields.

Field Description LAN Direct Redistribute Slide the toggle to enable redistribute to advertise the LAN Direct route to SD-WAN. Interface Select the interface on which to enable static routing. Redistribute Click Redistribute to advertise the static IP route added to WAN interface to redistribute to SD-WAN. If not selected, the static IP route is redistributed to LAN-VR. Destination (IPv4/Mask) Enter the destination IP address and subnet mask. Next Hop Select the next hop:
- Address—Click, and then enter the next-hop IP address. To configure static route with discard or reject option on a LAN virtual router, next- hop IP address must be 0.0.0.0.
- Discard—For LAN virtual router, select to silently drop packets that match the route without sending an ICMP unreachable message. The default option is discard.
- Reject—For LAN virtual router, select to drop packets that match the route and send an ICMP unreachable message.
- IPsec—Click, and then select an IPsec tunnel. To configure IPsec in routing, you must add IPsec from the WAN network. To create an IPsec tunnel, see Configure IPsec VPN Settings.
- Routing Instance (VRF)—Click, and then select a routing instance to resolve the static route next hop to the same or to a different routing instance.
Name Enter the name of the static route for route redistribution. - Address—Click, and then enter the next-hop IP address. To configure static route with discard or reject option on a LAN virtual router, next- hop IP address must be 0.0.0.0.
- Click Advance Configurations (Customized) to configure advanced static routing settings, and then enter information for the following fields.

Field Description Metric Enter the cost to reach the destination network. The metric is used to choose between multiple paths learned with the same routing protocol.
Range: 1 through 4294967295
Preference Enter the administrative distance (AD) or route preference value of the static route. You can assign a preference for each route. The preference is used to choose between multiple paths learned from different routing protocols.
Range: 1 through 255
Monitor Select the name of a liveness detection monitor or monitor group that must be up for the static route to become active.
To select a monitor object or monitor group:
- Click the Monitor drop-down list.

- Select a monitor object or monitor group, and then click Continue.

To add a new monitor object or monitor group, click + Monitor:
- To add a monitor object, select the Monitor tab, and then enter information for the following fields.

- Name (Required)—Enter a name for the IP service-level agreement (SLA) monitor object.
- Monitor Type (Required)—Select the type of packets to monitor on the IP address:
- DNS
- ICMP
- TCP
- Interval (Required)—Enter the time interval between monitor packets.
Range: 1 through 60 seconds
Default: 3 seconds - Threshold (Required)—Enter the the number of monitor packets transmission to be missed before setting the state of the node as down and withdrawing the static route.
Range: 1 through 60
Default: 5 - IP Address (Required)—Enter the IP address to monitor.
- Next Hop—Select the device to use as the next hop.
- Networks—Select the source network on which to send the probe packets.
- Source Interface—Select the source interface on which to send the probe packets.
- Click Add, and then click Continue.
- To add a monitor group, select the Monitor Group tab, and then enter information for the following fields. You can associate up to 8 monitors to a monitor group.

- Name (Required)—Enter a name for the IP SLA monitor group.
- Operations—Select the AND or OR operator:
- And—Monitor state is considered up, if all monitors in the monitor group are up.
- Or—Monitor state is considered up, if at least one of the monitors in the monitor group are up.
- List of Monitors—Select the monitor objects from the Available column to add to a monitor group. The selected objects will be moved to the Added column.
- Click Add, and then click Continue.
To remove a monitor object, or all objects, from a monitor group:
- In the Added column, click the
 icon to remove a single monitor object, or click Remove All to remove all monitor objects in a monitor group.
icon to remove a single monitor object, or click Remove All to remove all monitor objects in a monitor group. - Click the
 Edit icon to update the monitor group information.
Edit icon to update the monitor group information. - Click the
 Delete icon to delete the monitor group.
Delete icon to delete the monitor group.
Enable BFD (Bidirectional Forwarding Detection) (Group of Fields) Click to enable the use of BFD to monitor the next hop that is configured for the static route. If the BFD monitoring fails, the route is withdrawn from the routing table. Note that if you configure one or more of the Enable ICMP, Monitor, or Enable BFD fields simultaneously, and if any one of the monitors fails, the static route is withdrawn from the routing table. You cannot configure both BFD and monitor object for a static route. - Minimum Receive Interval (Required)
Enter the minimum time interval to receive routes, in milliseconds.
Range: 1 through 255000 milliseconds
- Multiplier
Enter the multiplier value to use to calculate the final minimum receive interval and minimum transmit interval.
Range: 1 through 255
- Minimum Transmit Interval (Required)
Enter the time after which routes can be retransmitted, in milliseconds.
Range: 1 through 255000 milliseconds
- Click the Monitor drop-down list.
- Click Continue.
- Click the
 icon.
icon. - Click Save and then Publish.
Whenever the WAN IP address of the IPsec tunnel address pool changes, the previous IP address is not deleted as a static route on the SASE device and Versa Director. To delete the static route entry:
- Configure the static IP route with the IP address that you want to delete. See Configure Static IP Route.
- Click the
 icon, and then click Publish.
icon, and then click Publish.

Configure OSPF
The Open Shortest Path First (OSPF) is an interior gateway routing protocol (IGP) that uses a link-state routing algorithm. OSPFv2 for IPv4 is defined in RFC 2328. You can configure OSPF instances on both LAN and WAN interfaces. On a WAN interface, OSPF applies only to the static WAN.
To configure OSPF:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb, and then click Configure to open the site information window.
- Click the Routing tab, and then click the OSPF tab. Enter information for the following fields.

Field Description Area ID Enter the OSPF area ID. A backbone area has an area ID of 0.0.0.0. Areas with non-zero IDs are non-backbone areas.
BFD Click to enable BFD for OSPF. When BFD is enabled, if OSPF goes down, the router is marked as being down. Password Enter the password to authenticate the OSPF peers. MD5 authentication is used with a default key ID of 0. Interface Select the interface on which to enable OSPF. - Click the
 Add icon.
Add icon. - In the OSPF profile section, you can monitor, edit, or delete an OSPF profile.
- Click the
 Edit icon to edit a profile.
Edit icon to edit a profile. - Click the
 Delete icon to delete a profile.
Delete icon to delete a profile. - Click the
 Monitor icon to go to the Monitor > Network screen and monitor an OSPF routing instance. For more information, see Monitor OSPF Routing Status.
Monitor icon to go to the Monitor > Network screen and monitor an OSPF routing instance. For more information, see Monitor OSPF Routing Status.
- Click the
- Click Redistribute to SD-WAN to configure the policy to control the advertisement of OSPF routes received by the enterprise VPN network.

- If necessary, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Save Reordered Rules to save the changes to the Titan cloud.
- Click the
 Add Rule icon to add a new OSPF redistribution rule. Enter information for the following fields.
Add Rule icon to add a new OSPF redistribution rule. Enter information for the following fields.

Field Description Rule Name Enter a name for the rule. Match Criteria Enter the IPv4 address prefix to match. Action Select the action to take on matching routes:
- Allow—Click to allow routes that match this prefix list.
- Deny—Click to deny routes that match this prefix list.
- Click the
 Add icon, and then click Save.
Add icon, and then click Save. - Click Redistribute From SD-WAN to configure the policy to control the advertisement of enterprise VPN routes received by the OSPF network.

- Click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Save Reordered Rules to save the changes to the Titan cloud.
- Click the
 Add Rule icon to add a new OSPF redistribution rule. Enter information for the following fields.
Add Rule icon to add a new OSPF redistribution rule. Enter information for the following fields.

Field Description Rule Name Enter a name for the rule. Match Criteria Enter the IPv4 address prefix to match. Action Select the action to take on the routes:
- Allow—Click to allow routes that match this prefix list.
- Deny—Click to deny routes that match this prefix list.
- Click the
 Add icon, and then click Save.
Add icon, and then click Save.
Configure EBGP
The Border Gateway Protocol (BGP) is an exterior gateway protocol (EGP) used for exchanging routing information between gateway hosts in a network. BGP is the protocol commonly used between gateway hosts on the Internet.
You can configure an outbound routing policy that controls and filters prefixes that are advertised to the BGP peer and an inbound routing policy that controls and filters prefixes that are received from the BGP peer.
For an outbound policy, it advertises all routes when there is no policy configured, by default. If a policy is configured, only matched routes will be advertised or denied based on the set action and all other routes will be denied.
For an inbound policy, it accepts all routes when there is no policy configured, by default. If a policy is configured, only matched routes will be accepted or denied based on the set action and all other routes will be denied. After application of the policy, the routes are automatically advertised into the enterprise VPN network.
You use 0.0.0.0/0 as a wildcard to match all IP prefixes.
To configure EBGP:
- Click Configure in the left menu bar to open the Configure dashboard.
- Hover over the device in the honeycomb, and then click Configure to open the site information window.
- Click the Routing tab, and then click the EBGP tab. Enter information for the following fields.

Field Description Interface Select the interface to which to connect to the BGP neighbor (peer). BFD Click to enable BFD, to provide fast forwarding-path failure detection and decrease reconvergence time. Neighbor Enter the IP address of the BGP peer. Redistribute Click Redistribute to advertise the BGP IP prefixes learnt from WAN transport VRF to default LAN VRF and other SD-WAN branches. If not selected, the route is redistributed to LAN VRF. The other SD-WAN branches do not get the routes.
Password Enter the password to authenticate the BGP instance. Local AS Enter the local AS number.
Range: 0 through 4294967295 or (0 through 65535).(0 through 65535)
AS Override Click to replace neighbor AS numbers with the local AS numbers from the AS path. Remote AS Enter the remote peer's AS number.
Range: 0 through 4294967295 or (0 through 65535).(0 through 65535)
Remove All Private AS# Click to remove all private AS numbers from a prefix's AS path before redistributing the same to BGP peers. - Click the
 icon.
icon. - In the BGP profile section, you can monitor, edit, or delete a BGP profile.
- Click the
 Edit icon to edit a profile.
Edit icon to edit a profile. - Click the
 Delete icon to delete a profile.
Delete icon to delete a profile. - Click the
 Monitor icon to go to the Monitor > Network screen and monitor a BGP routing instance. For more information, see Monitor BGP Routing Status.
Monitor icon to go to the Monitor > Network screen and monitor a BGP routing instance. For more information, see Monitor BGP Routing Status.
- Click the
- Click Outbound Policy to configure a routing policy that controls and filters prefixes that are advertised to the BGP peer.
- If necessary, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Save Reordered Rules to save the changes to the Titan cloud.
- Click the
 icon to add a new outbound routing policy. Enter information for the following fields.
icon to add a new outbound routing policy. Enter information for the following fields.
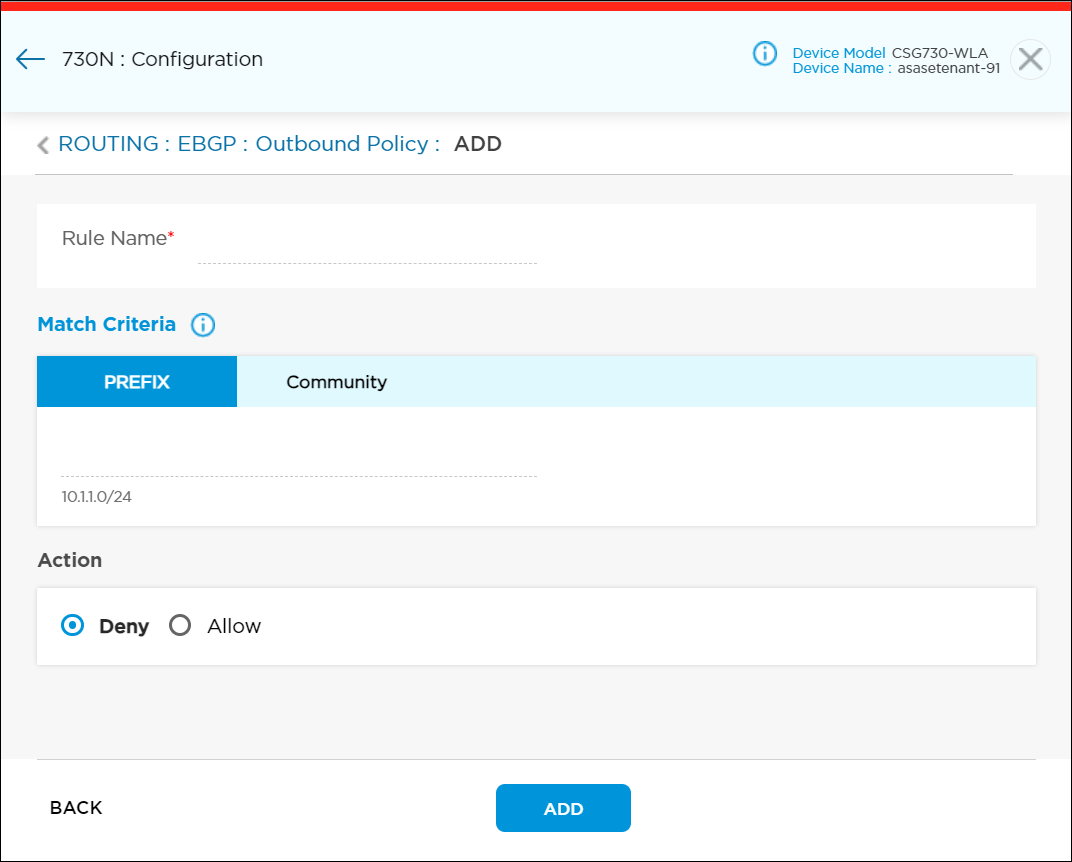
Field Description Rule Name (Required) Enter a name for the rule. Match Criteria Select one or more match criteria:
- Click the Prefix tab, and then enter the IP prefix to match.
- Click the Community tab, and then enter the BGP community string to match. Enter the community string in one of the following formats:
- 2-byte or 4-byte decimal number
- 2-byte decimal number:2-byte decimal number
- Regular expression pattern
Action Select the action to apply to matched prefixes. - Allow
Click to allow the prefixes that match the match criteria.

If you add a BGP peer for a WAN interface, you can add the following additional criteria:
- Community Value—Enter the BGP community value to set. Community value can be set in the format 2-byte decimal number:2-byte decimal number. For example, <0-65535>:<0-65535>.
- Local AS Path Prepend—Enter the number of times to prepend the local AS number to the AS path.
Range: 1 through 255
If you add a BGP peer for a LAN interface, you can add the following additional criteria:
- Community Value—Enter the BGP community value to set. Community value can be set in the format 2-byte decimal number:2-byte decimal number. For example, <0-65535>:<0-65535>.
- Local AS Path Prepend—Enter the number of times to prepend the local AS number to the AS path.
Range: 1 through 255
- Deny
Click to deny the prefixes that match the match criteria. - Click the
 icon.
icon. - Click Inbound Policy to configure a routing policy that controls and filters prefixes that are received from the BGP peer.

- If necessary, click Reorder Rules to enter rule reorder mode.
- To change a rule order, click the colored circle and drag the rule to a different spot in the rule set. The rule numbers are updated automatically.
- Click Save Reordered Rules to save the changes to the Titan cloud.
- Click the
 icon to add a new inbound routing policy. Enter information for the following fields.
icon to add a new inbound routing policy. Enter information for the following fields.

Field Description Rule Name (Required) Enter a name for the rule. Match Criteria Select one or more match criteria:
- Click the Prefix tab and enter the IP prefix to match.
- Click the Community tab, and then enter the BGP community string to match. Enter the community string in one of the following formats:
- 2-byte or 4-byte decimal number
- 2-byte decimal number:2-byte decimal number
- Regular expression pattern
Action Select the action to apply to matched prefixes. - Allow
Click to allow the prefixes that match the match criteria:
- If you add BGP peer for a WAN interface, you can add the following additional criteria:

- Community Value—Enter the BGP community value to set. Community value can be set in the format 2-byte decimal number:2-byte decimal number. For example, <0-65535>:<0-65535>.
- If you add a BGP peer for a LAN interface, you can add the following additional criteria:

- Community Value—Enter the BGP community value to set. Community value can be set in the format 2-byte decimal number:2-byte decimal number. For example, <0-65535>:<0-65535>.
- Administrative Distance—Enter the administrative distance value. Administrative distance is a measure used by routers to determine the trustworthiness of a routing source. The low administrative distance indicates that eBGP routes are highly trusted compared to other routing protocols. The route with the lowest preference is the most likely to become the active route.
Range: 1 through 255
Default: For static route—1; For eBGP—20
- Deny
Click to deny the prefixes that match the match criteria. - Click the
 icon, and then click Save.
icon, and then click Save.
Supported Software Information
Releases 11.2 and later support all content described in this article.
