Configure AAA
![]() For supported software information, click here.
For supported software information, click here.
This article describes how to configure authentication, authorization, and accounting (AAA) for users who access Versa Operating SystemTM (VOSTM) devices.
Authentication identifies users to determine whether they are allowed to access a VOS device, the network, and related services. To authenticate a user, you can use an internal or an external user database. The external database can be on a RADIUS or TACACS+ server.
After a user is authenticated on a VOS device, each user action that they perform must be authorized. Authorization is the method for remote access control, including one-time authorization and service authorization based on user or user account and profile. The VOS software provisions three user types, or roles—System, Tenant, and Remote—that determine the access level for individual users. When you create a user, you assign them to the desired role.
Authorization uses a database to define the authorization methods. The database can be located locally on the access server or on a router, or it can be hosted remotely on a RADIUS or TACACS+ server. The authorization process assembles a set of attributes that describe what the user is authorized to perform, compares them to the information in the authorization database database, and then returns to AAA the user's permissions and restrictions.
Accounting collects and sends security server information that is used for billing, auditing, and reporting, such as user identities, start and stop times, executed commands (such as PPP), number of packets, and number of bytes. The accounting information allows you to track the services that users are accessing and the amount of network resources they are consuming.
Note: In Release 23.1.1, Director only supports Central Authentication Director servers running Release 23.1.1, and does not support backward compatibility. Concerto can only manage Directors that are both running either in Release 22.1.4 or Release 23.1.1, not a mix of both. For example, a Director node running Release 23.1.1 cannot use a Director node running 22.1.4 as the Central Authentication server.
Configure TACACS+
TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes.
To configure TACACS+:
- In Director view, select the Workflows tab in the top menu bar.
- Select an organization in the Organization field in the horizontal menu bar.
- Select Template > Templates in the horizontal menu bar.
- Select SD-WAN in the horizontal menu bar.
- Click
 Add to add a new template, or click the
Add to add a new template, or click the  Edit icon in the Actions column to edit an existing template. The Configure Basic screen displays.
Edit icon in the Actions column to edit an existing template. The Configure Basic screen displays.

- For Releases 21.2 and earlier, in Director view, select the Workflows tab in the top menu bar, select Templates in the left menu bar., and then click the
 Add icon to add a template, or select a template to edit it.
Add icon to add a template, or select a template to edit it.

- Select the Management Servers tab, and then select the TACACS+ Servers tab.

For Releases 21.2 and earlier:
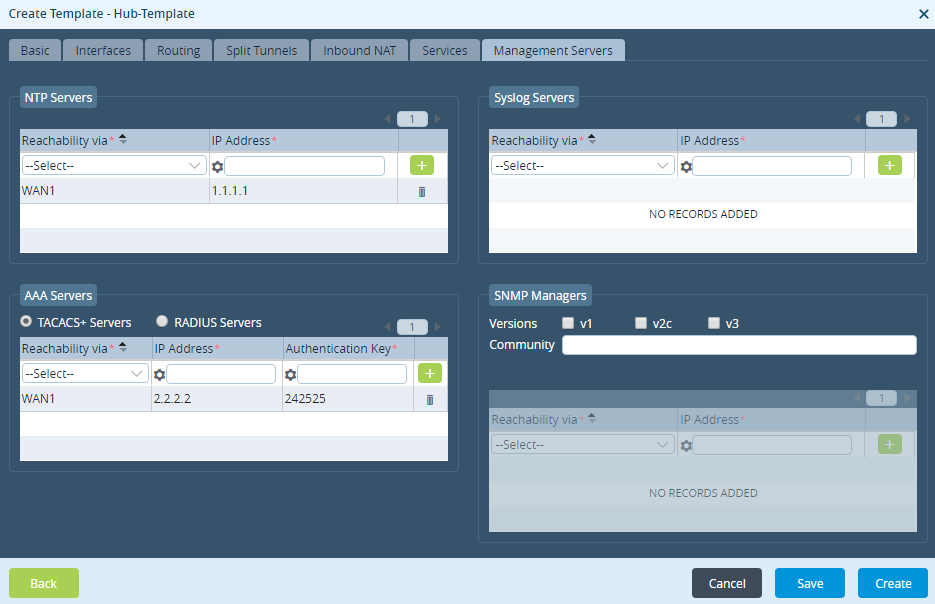
- Enter information for the following fields.
Field Description Reachability via (Required)
Select the reachability network between the Controller and TACACS+ server. IP Address (Required)
Enter the IP address of the server to which to connect. Authentication Key (Required)
Enter the authentication key. The key can consist of both numbers and letters, and it cannot include a hash mark (#) or spaces. Actions (For Releases 22.1 and later.) Select the TACACS+ action:
- Accounting
- Authentication
- Click Save.
Configure RADIUS
RADIUS is a distributed client-server system that secures networks against unauthorized access.
To configure RADIUS:
- In Director view, select the Workflows tab in the top menu bar.
- Select an organization in the Organization field in the horizontal menu bar.
- Select Template > Templates in the horizontal menu bar.
- Select SD-WAN in the horizontal menu bar.
- Click
 Add to add a new template, or click the
Add to add a new template, or click the  Edit icon in the Actions column to edit an existing template. The Configure Basic screen displays.
Edit icon in the Actions column to edit an existing template. The Configure Basic screen displays.

- For Releases 21.2 and earlier, in Director view, select the Workflows tab in the top menu bar, select Templates in the left menu bar., and then click the
 Add icon to add a template, or select a template to edit it.
Add icon to add a template, or select a template to edit it.

- Select the Management Servers tab, and then select the RADIUS Servers tab.

For Releases 21.2 and earlier:

- In the Create Template popup window, select the Management Servers tab. Enter information for the following fields.
Field Description Reachability via (Required)
Select the reachability network between the controller and the RADIUS server. IP Address (Required)
IP address of the server to connect to. Authentication Key (Required)
Enter the authentication key. The key can consist of both numbers and letters, and it cannot include a hash mark (#) or spaces. Actions (For Releases 22.1 and later.) Select the TACACS+ action:
- Accounting
- Authentication
- Click Save.
Configure Local Authentication
VOS devices support the following users:
- Default users
- System users
- Organization users
Default users are system users created by default and cannot be deleted. VOS devices have the following default users:
- admin—Superuser with sudo privileges. An admin use can SSH to the VOS device using port 22.
- versa—Console user. These users can log in to the physical device or through a virtual console.
System users can log in to the VOS underlying operating system. The user is created in Linux when a system user is configured. System users can have the following roles:
- Admin—Can modify any part of the configuration.
- Operator—Can only view the configuration.
System users can have the following login types:
- Shell—Land at bash post-authentication prompt
- CLI—Land on at CLI prompt post-authentication prompt
Organization users can log in only to the VOS CLI. Organization users can SSH only to port 2024. SSH to port 22 is prohibited for all Organization users. Currently, VOS devices support password-less authentication for organization users.
The following predefined RBAC roles are available for organization users:
| User | Description |
|---|---|
| adc-admin | Can view/modify ADC specific configuration only. |
| cgnat-admin | Can view/modify CGNAT specific configuration only. |
| sdwan-admin | Can view/modify configuration related to SDWAN. |
| security-admin | Can view/modify security configuration only. |
| tenant-admin | Can view/modify all tenant configuration. |
| oper | Can view all tenant configuration. No modification allowed. |
To create unique Org usernames in the system, when an Organization user is created, the VOS device appends @Orgname to the username. For example, if the username is john@kayak, the user must SSH as ssh'john@kayak'@77.1.1.1 OR ssh77.1.1.1 -l john@kayak.
VOS devices also support password-less authentication for system users using SSH public key. This provides enhanced security and the system is then protected against SSH brute force password attacks. Multiple SSH keys can be configured for a system user.
Add System Users
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the left menu bar.
- Select an organization in the left menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > System > Appliance User Management > System Users in the left menu bar
- Click the
 Add icon. In the Add System User popup window, enter information for the following fields.
Add icon. In the Add System User popup window, enter information for the following fields.

Field Description Username (Required) Enter the username. Login (Required) Select the login method: - CLI
- No Login
- Shell
Role (Required) Select the user's role: - Admin
- Operator
Password (Required) Enter a password for the user. Confirm Password (Required) Confirm the password. SSH Public Key Enter the SSH details, if required.
- Click OK.
Add Organization Users
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the left menu bar.
- Select an organization in the left menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > System > Appliance User Management > Organization User in the left menu bar.

- Click the
 Add icon, and in the Add Organization User popup window, enter information for the following fields.
Add icon, and in the Add Organization User popup window, enter information for the following fields.
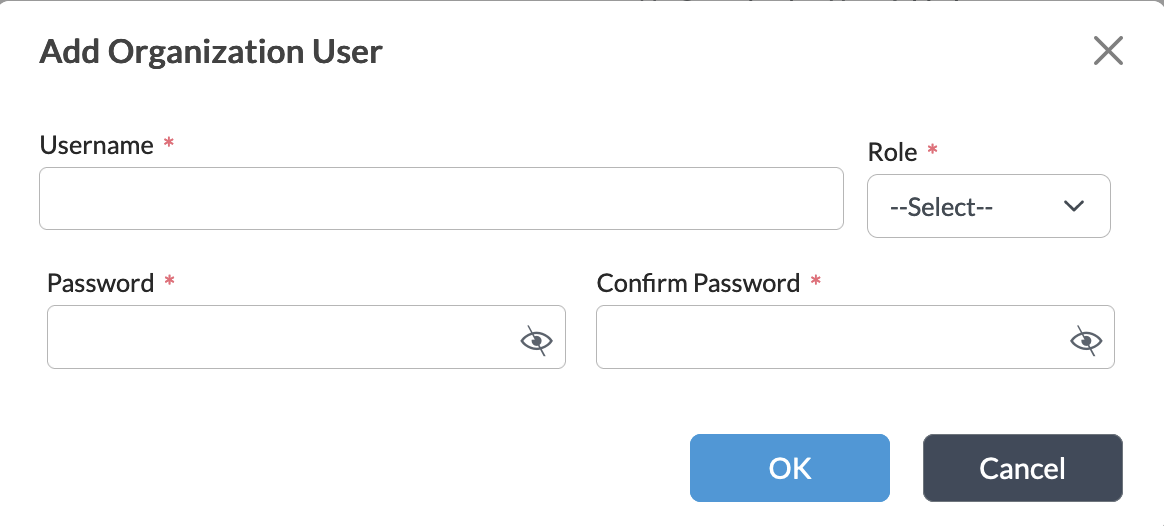
Field Description Username (Required) Enter the username. Role (Required) Select the role to be assigned to the user. Password (Required) Enter a password for the user.
Confirm Password (Required) Confirm the password.
- Click OK.
Configure AV Pairs for RADIUS and TACACS+
For RADIUS and TACACS+, VOS devices support the following attribute–value (AV) pairs:
- versa-admin-login—Allows users assigned to the admin group to access a shell or the CLI. This AV allows a remote administrator to land on a shell or the CLI.
- versa-cli-idle-timeout—Sets the idle timeout for a user who has logged in, in seconds.
- versa-user-group—Defines the user role that can be assigned to the remote AAA user. The following are the commonly used roles:
- admin—Provides read and write permissions on the device to the user system administrator.
- oper—Provides read-only permission to the user system operator.
For the versa-user-group AV, VOS devices support the following other roles at the tenant level:
- tenant-name-adc-admin-group
- tenant-name-cgnat-admin-group
- tenant-name-network-admin-group
- tenant-name-oper-admin-group
- tenant-name-sdwan-admin-group
- tenant-name-security-admin-group
- tenant-name-tenant-admin-group
For RADIUS and TACACS+, you must define a service name that is used by the user named “versa.” For example:
group = network_oper {
default service = permit
expires = "Jan 1 2025"
service = versa
{
versa-user-group = oper
}
}
Configure AV Pairs for RADIUS
For RADIUS, you configure AV pairs on the RADIUS server. In this section, we show example configurations on a FreeRADIUS server that is running on a Linux platform. Here, you configure entries in the dictionary.versanetworks, /etc/freeradius/client.conf, and /etc/freeradius/users files on the RADIUS server.
To define the attributes, ensure that the directionary.versanetworks file contains the following entries:
VENDOR VersaNetworks 42359 BEGIN-VENDOR VersaNetworks ATTRIBUTE Versa-User-Group 1 string ATTRIBUTE Versa-Acct-Command 2 string ATTRIBUTE Versa-User-Role 3 string ATTRIBUTE Versa-Tenant 4 string ATTRIBUTE Versa-Admin-Login 5 string END-VENDOR VersaNetworks
To allow clients from specific networks, add entries similar to the following in the /etc/freeradius/client.conf file:
client 172.18.0.0/24 {
secret = "secret"
shortname = network-1
}
client 192.168.0.0/16 {
secret = “secret”
shortname = network-2
}
To configure the RADIUS users, add entries similar to the following in the /etc/freeradius/users file:
User1 Cleartext-Password := "password"
Reply-Message = "Hello, %{User-Name}",
Versa-User-Group = "oper"
User2 Cleartext-Password := "password"
Reply-Message = "Hello admin, %{User-Name}",
Versa-User-Group = admin
User3 Cleartext-Password := "password"
Versa-User-Group = "admin",
Versa-Admin-Login = "shell",
Reply-Message = "Hello Ella, %{User-Name}"
Configure AV Pairs for TACACS+
For TACACS+, you configure AV pairs on the TACACS+ server. In in this section, we show example configurations for tac_plus that is being used as a TACACS+ process (daemon) on a Linux platform. Here, you edit the /etc/tacacs/tacacs.conf configuration file on the TACACS+ server, adding entries similar to the following:
# commands authorization, scripting authorization.
# See the man page for these features.
key = "password"
accounting syslog;
accounting file = /var/log/tac_plus/tac_plus.acct
group = network_admin {
default service = permit
expires = "Jan 1 2025"
service = versa {
versa-user-group = admin
versa-admin-login = shell
}
}
group = network_oper {
default service = permit
expires = "Jan 1 2025"
service = versa {
versa-user-group = oper
}
}
group = tenant1_admin {
default service = permit
expires = "Jan 1 2025"
service = versa {
versa-user-group = Tenant1-tenant-admin-group
Versa-cli-idle-timeout = 10
}
}
user = test-user {
member = network_admin
login = cleartext "password1234"
enable = cleartext "password1234"
global = cleartext "password1234"
}
user = test-user2 {
member = network_oper
login = cleartext "password1234"
enable = cleartext "password1234"
global = cleartext "password1234"
}
Disable External Authentication
To disable TACACS+ and other external authentication:
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the left menu bar.
- Select an organization in the left menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others
 > System > Appliance User Management > External in the left menu bar.
> System > Appliance User Management > External in the left menu bar.

- In the External AAA pane, select the external authentication device.
- Click the
 icon.
icon.
Supported Software Information
Releases 20.2 and later support all content described in this article.
Additional Information
Configure AAA (on Director nodes)
Create and Manage Staging and Post-Staging Templates
Configure Single Sign-On Using Director
Configure TACACS+ (on Analytics nodes)
