Configure MDM Profiles
![]() For supported software information, click here.
For supported software information, click here.
You create a mobile device management (MDM) profile to retrieve device information from a graph server. You can use an MDM profile to retrieve device information from a Microsoft Intune server using the device ID and other information, such as user profile using user ID.
You can associate MDM profiles with a Secure Access Portal or a Secure Access Gateway to verify device information during Versa secure access (VSA) client registration (Portal) and after registration (Gateway).
After you link an MDM profile to a graph server, when a user tries to connect to a Versa gateway using a VPN client, a check verifies whether the device is enrolled with the graph server and if the device is compliant with the policies you have configured. If the device is managed and compliant, the VPN session is established, and the user is allowed to access internal resources.
Configure an MDM Profile
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > MDM Profile in the left menu bar. The main pane displays the MDM profiles that are already configured.

- Click + Add. In the Add MDM Profile popup window, enter information for the following fields.

Field Description Name Enter a name for the MDM profile. Description Enter a text description for the MDM profile.
Directory ID Enter the tenant or directory ID registered on the graph (Intune) server. Authentication Profile Select the authentication profile, which is a cloud profile, to use to retrieve access token for secure access. For more information, see Configure a Cloud Profile in the Configure File Filtering article. Client ID Enter the client identifier provided by the graph (Intune) server, in string format. Client Secret Enter the client secret provided by the graph (Intune) server, in string format. Graph Profile Select the graph server profile, which is a cloud profile, to use to retrieve data from the graph server. For more information, see Configure a Cloud Profile in the Configure File Filtering article.
Activation Click to enable MDM lookup for the profile. Default Profile Click to make this the default MDM profile. Graph Type
(Group of Fields)
- Provider Name
Select the graph provider for which to retrieve information, for example, Microsoft. - Resource
Select the resource or device from which to retrieve information, for example, Device ID. - Click OK.
Associate an MDM Profile with a Secure Access Portal
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Templates > Device Templates in the horizontal menu bar.
- Select an organization in the left menu bar.
- Select a template in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Secure Access > Portal > General in the left menu bar. The main pane displays the General settings pane.

- In the General pane, click the
 Edit icon. The Add Services popup window displays.
Edit icon. The Add Services popup window displays.

- Click Query MDM to enable MDM checking.
- Select the MDM profile you configured in Configure an MDM Profile, above.
- For information about configuring other parameters, see Configure a Secure Access Portal in Configure Versa Secure Access Gateway.
- Click OK.
Associate an MDM Profile with a Secure Access Gateway
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Templates > Device Templates in the horizontal menu bar.
- Select an organization in the left menu bar.
- Select a template in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Secure Access > Gateway > General in the left menu bar.

- Click the
 Edit icon. The Add Services popup window displays.
Edit icon. The Add Services popup window displays.

- Click Query MDM to enable MDM check.
- Select the MDM profile you added in Configure an MDM Profile, above.
- For information about configuring other parameters, see Configure a Secure Access Gateway in Configure Versa Secure Access Service.
- Click OK.
Associate MDM Profiles with Secure Access Portal and Gateway Policies
To ensure that graph server information from devices managed by MDM is in a compliant state, you can create secure access portal and gateway policies to enforce compliance. These policies are checked when a user tries to connect to a Versa gateway using a VPN client. If the managed device is compliant, the VPN session is established, and the user is allowed to access internal resources.
To create the policies, you perform configuration steps both on the VOS device and on Microsoft Intune.
To associate MDM profiles with secure access portal and secure access gateway policies:
- On Microsoft Intune, check that the device is registered.
- In the appliance certificate store, go to Certificates - Local Computer > Personal > Certificates.
- Check that the device is registered.

- If the device is not registered, an admin user can register the device on Intune by entering the following URL in the browser URI:
ms-device-enrollment:?mode=aadj
- On the VOS device, add a DNS forwarder so that the cloud profile can connect to Microsoft Graph and the authentication server.
- In Director View, select the Configuration tab in the top menu bar.
- Click Device > Devices in the horizontal menu, select a tenant in the left menu bar, and click a device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Network > DNS > Settings in the left menu bar.
- In the DNS Settings pane, click the
 Edit icon.
Edit icon. - In the Edit DNS Settings popup window, enter information for the following fields.
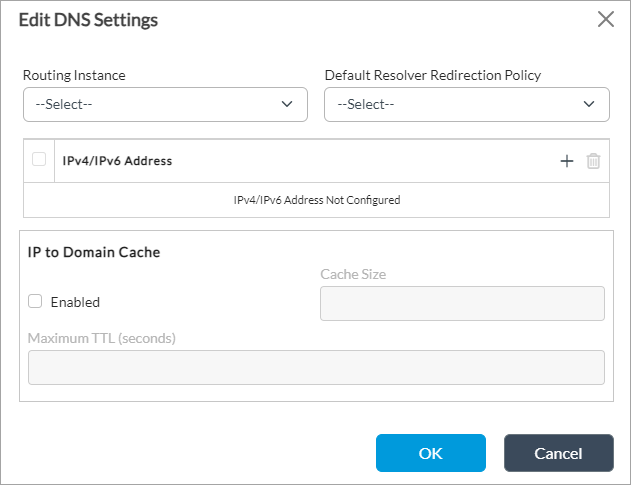
Field Description Routing Instance Select the routing instance to use to reach the DNS server. Default Resolver Redirection Policy Select the default resolver redirection policy to resolve domains IPv4/IPv6 Address Click + and enter the IP address of the DNS server. IP to Domain Cache (Group of Fields) - Enabled
Click to enable caching of IP address to domain lookup information. - Cache Size
Enter the maximum number for cache entries. - Maximum TTL (Seconds)
Enter the cache TTL upper limit, in seconds. - Click OK.
- On the VOS device, create two profiles to use for Intune, an authentication profile and a graph profile. For more information, see Configure a Cloud Profile. The following screenshot shows an example of an authentication profile.

The following screenshot shows an example of a graph profile.

- On Microsoft Intune, create an MDM profile. To fetch the device information from Intune, you create an Inlune App for the Azure tenant with permissions that allow Microsoft Graph to provide the data. In the profile, for the Client ID, enter the application ID on the Azure portal. If you need to specify the client secret, use the secret value of the Azure application. Note that this is not a value that you configure. For example:


- On the VOS device, configure the MDM profile, as described in Configure an MDM Profile, above. For example:

- On the VOS device, enable a query MDM on the secure access portal and secure access gateway, as described in Associate an MDM Profile with a Secure Access Portal and Associate an MDM Profile with a Secure Access Gateway, above. The following screenshot shows an example of a query MDM for the secure access portal.

The following screenshot shows an example of a query MDM for the secure access gateway:

- On the VOS device, create a secure access portal and gateway policy to enforce that graph server information from devices managed by MDM is in a compliant state. For more information, see Add Secure Access Portal Policy in Configure Versa Secure Access Service. In the policy rule, configure the source compliance state and an enforcement message. For example:


The following screenshot shows the permissions required on the Azure application to retrieve device information.

View MDM Profile Statistics
Note that the MDM statistics display based on the SSL cloud profile settings. For more information, see Configure a Cloud Profile.
To view MDM profile statistics:
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the horizontal menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select the provider organization in the horizontal menu bar.
- Select the Services tab in the horizontal menu bar.
- Select the Secure Access tab > MDM Profiles tab.

The table displays the following information:
Counter Name Description MDM Access Token Req Count Number of times request was sent to fetch an access token. MDM Access Token Response Count Number of times an access token response was received successfully. MDM Access Token Fail Count Number of times an access token request failed. MDM Access Token Null Response Count Number of times an access token request received a null response, which generally occurs because a timeout occurs or a session closes. MDM Resource Req Count Number of times an MDM request was sent to fetch a resource (device ID). MDM Resource Response Count Number of times an MDM response was received successfully. MDM Resource Req Fail Count Number of times an MDM request failed. MDM Resource Null Response Count Number of times MDM received a null response, which generally occurs because a timeout occurs or a session closes.
To view MDM profile statistics, using CLI:
admin@cli> show orgs org-services tenant-name objects mdm-profile statistics
For example:
admin@cli> show orgs org-services AMP objects mdm-profile statistics objects mdm-profile statistics AMPIntune-ZS mdm-access-token-req-cnt 430 mdm-access-token-resp-cnt 222 mdm-access-token-req-fail-cnt 0 mdm-access-token-null-resp-cnt 208 mdm-resource-req-cnt 432 mdm-resource-resp-cnt 405 mdm-resource-req-fail-cnt 0 mdm-resource-null-resp-cnt 27
The following table explains each counter:
| Counter Name | Description |
|---|---|
| mdm-access-token-req-cnt | Number of times request was sent to fetch an access token. |
| mdm-access-token-resp-cnt | Number of times an access token response was received successfully. |
| mdm-access-token-req-fail-cnt | Number of times an access token request failed. |
| mdm-access-token-null-resp-cnt | Number of times an access token request received a null response, which generally occurs because a timeout occurs or a session closes. |
| mdm-resource-req-cnt | Number of times an MDM request was sent to fetch a resource (device ID). |
| mdm-resource-resp-cnt | Number of times an MDM response was received successfully. |
| mdm-resource-req-fail-cnt | Number of times an MDM request failed. |
| mdm-resource-null-resp-cnt | Number of times MDM received a null response, which generally occurs because a timeout occurs or a session closes. |
Debug MDM Issues
To debug MDM issues, issue the following CLI commands:
- set debug mdm all-flags level all
- set debug saccess all-flags level all
Supported Software Information
Releases 21.2.1 and later support all content described in this article.
Additional Information
Configure File Filtering
Configure Versa Secure Access Service
