Configure SSL VPN Profiles
![]() For supported software information, click here.
For supported software information, click here.
SSL VPN is an alternative to IPsec VPN for allowing remote users to connect to Versa gateways using the Versa SASE client. The Versa proprietary SSL VPN protocol is based on Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS). SSL VPN generally uses port 443 to establish a secure connection with Versa gateways, and ensures that you can deploy a Versa SASE client in any customer deployment.
You configure SSL VPN profiles to allow remote users to connect to an enterprise network on an SSL tunnel using a Versa SASE client. An SSL VPN profile defines the secure VPN tunnel that connects the remote user to the enterprise network.

SSL VPN is ideal for secure remote access from restricted networks where firewall rules often block uncommon ports. SSL VPN operates over TCP 443 (standard HTTPS) and bypasses these restrictions without requiring additional firewall changes. This makes SSL VPN a reliable choice for maximum reachability and ease of use, enabling secure access connections from highly restrictive network locations where IPsec VPN fails to establish connections.
The supported DTLS/TLS version is 1.2.
Configure SSL VPN
To configure an SSL VPN profile:
- Go to Configure > Security Service Edge > Secure Access > Client-based Access > Policy Rules.

- In the Client-based Access Rules screen, select a rule to edit. To create a secure client access rule, see Configure SASE Secure Client-Based Access Rules.

- In the Edit Client-based Access Rule screen, select step 7, Client Configuration, and then select TLS and/or DTLS for VPN Type.

(For Releases 12.2.1 and later.) If you select more than one VPN type, you can specify the order in which the Versa secure access client uses the VPN types, including the two types of SSL: TLS or DTLS.
- The following screen shows that both the TLS and DTLS SSL VPN types are selected, and that the secure access client uses TLS first and DTLS second.

- The following screen shows that both the TLS and DTLS SSL VPN types are selected, and that the secure access client uses DTLS first and TLS second.

- The following screen shows that IPsec, TLS, and DTLS VPN types are all selected, and the secure access client uses DTLS tunnel first to establish a connection. If the DTLS tunnel fails to connect, the SASE client tries to establish a connection with the TLS tunnel (the next priority). If both DTLS and TLS tunnels fail, the SASE client establishes a connection using the IPsec tunnel.

- The following screen shows that both the TLS and DTLS SSL VPN types are selected, and that the secure access client uses TLS first and DTLS second.
- Click Next. To save and deploy the secure client-based access rule, see Review and Configure SASE Secure Client-Based Access Rules.
Enable DTLS and TLS Tunnels From the SASE Client
By default, DTLS and TLS tunnels are disabled. When you enable the DTLS tunnel or TLS tunnel, the client tries to establish a tunnel based on the tunnel type order it receives from the portal. If the first attempt fails, the client tries to connect to the next tunnel type in the configuration order.
To enable the DTLS tunnel and TLS tunnel in the Versa SASE Client:
- In the SASE client home screen, click the
 Settings icon.
Settings icon. - Click App Settings.

The App Settings screen displays.
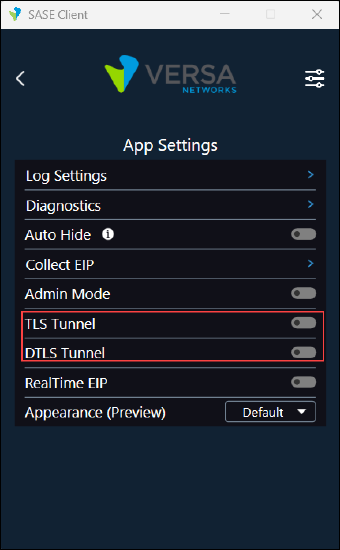
- Click the TLS Tunnel and DTLS Tunnel toggles. When you enable DTLS tunnel and TLS tunnel, the toggle color changes from gray to blue.
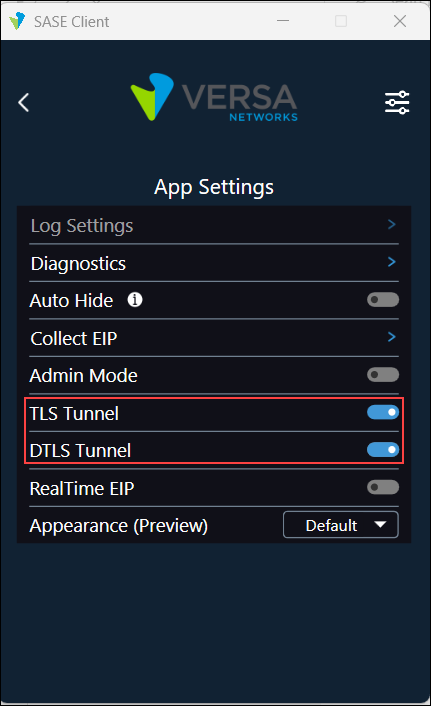
- The following screen shows that the SASE client establishes a connection with the TLS tunnel, which is the first ordered tunnel type.

- The following screen shows that the SASE client establishes a connection with the DTLS tunnel if the TLS tunnel fails to connect, since DTLS is the second ordered tunnel type.

- The following screen shows that the SASE client establishes a connection using an IPsec tunnel if both TLS and DTLS tunnels fail, since IPsec is the third ordered tunnel type.

- The following screen shows that the SASE client establishes a connection with the TLS tunnel, which is the first ordered tunnel type.
Supported Software Information
Releases 11.4.3 and later support all content described in this article, except:
- Release 12.2.1 adds support for specifying the order in which the Versa secure access client uses VPN types, including the two types of SSL VPNs: TLS or DTLS.
Additional Information
Concerto SASE End-to-End Configuration
Configure SASE Secure Client-Based Access Rules
