Configure Traffic-Steering Policies and Rules
![]() For supported software information, click here.
For supported software information, click here.
To add traffic-steering policies and rules, you first create an application policy to classify incoming traffic based on match criteria, such as application, source IP address, destination IP address, and incoming zone. Then, you specify the action to take when traffic matches the configured criteria.
Traffic-steering policies and rules belong to the Application subprofile type. You can attach only one traffic-steering policy to an Application subprofile. You can add a traffic-steering policy to an existing Application subprofile, or you can add it when you create a new subprofile. You can add a traffic-steering policy as a profile element that can then be used in one or more Application subprofiles.
You can build reusable application policies by navigating to Policies > Application > Traffic Steering. You can also build policies and rules inline. These inline rules apply only to the policies currently being configured. You cannot reuse them in other subprofiles until you add them to the reusable Subprofiles folder by clicking the ellipsis to the right of Next and then selecting Save As:

To add a traffic-steering policy to an existing Application subprofile:
- Go to Configure > Profiles > Sub Profiles > Application.

The screen displays the existing Application subprofiles.

- To add a traffic steering policy, click an application subprofile (Application-SP in the example above), or click the
 Elipsis icon, and then click the
Elipsis icon, and then click the  Edit icon in the popup menu. The Edit Application Sub Profile screen displays with the General tab selected by default.
Edit icon in the popup menu. The Edit Application Sub Profile screen displays with the General tab selected by default.

- Select the Policy tab, and then click + Policy.

- In the popup menu, select Traffic Steering. To create a new policy, click Create New Policy. To use an existing policy, click Choose Existing and select a policy from the list.

The Add Traffic Steering Policy screen displays with Step 1, Rules selected by Default.

- If desired, you can specify the columns to display, or you can accept the default selections and go to the next step. To change the settings, click the Select Columns down arrow and select the columns to be displayed. To restore the default column settings, click Reset.

- In the Add Traffic Steering Policy screen, click Add Rule. The following screen displays.
- To create a new rule for the application policy, continue to Step 8. To add an existing rule:
- Click Add Existing Rule. The Add Existing Traffic Steering Rules screen displays the existing traffic steering rules.
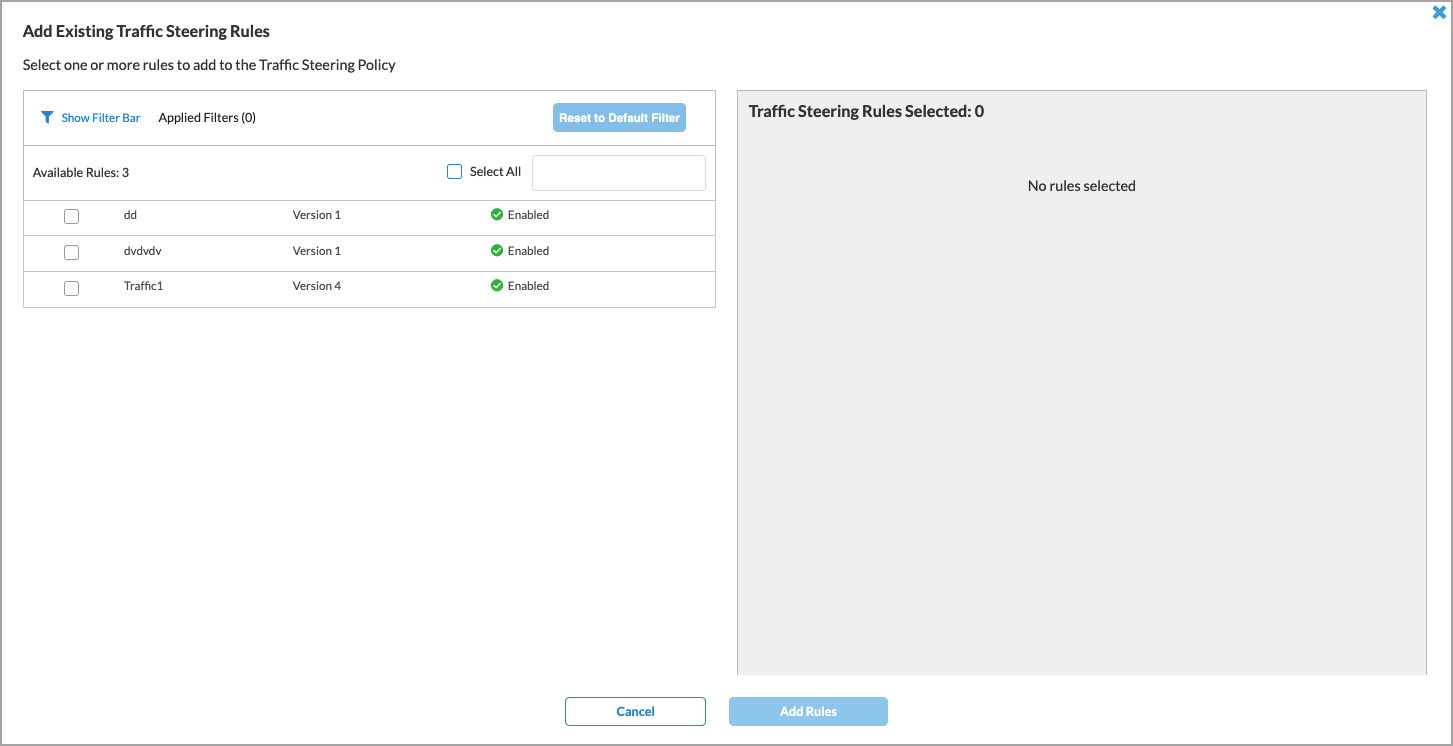
- Select one or more rules. The selected rules move to the Traffic Steering Rules Selected panel.

- To view the configuration elements for a selected rule, click the down arrow next to the rule, and then select a category to display the configuration elements for that category. The categories are:
- Applications and URLs
- Destination Traffic
- Enforcement
- Forwarding Profile an TCP Optimization Profile
- Services and DSCP
- Source Traffic
- Variable Type
- Click Add Rules to add the traffic-steering rule to the application policy.
- Click Add Existing Rule. The Add Existing Traffic Steering Rules screen displays the existing traffic steering rules.
- To create a new rule for the application policy, select Create Rule only for this Policy. The Add Traffic Steering Rule screen displays with Step 1, Applications & URLs, the Applications radio button, and the Application Group tab selected by default.

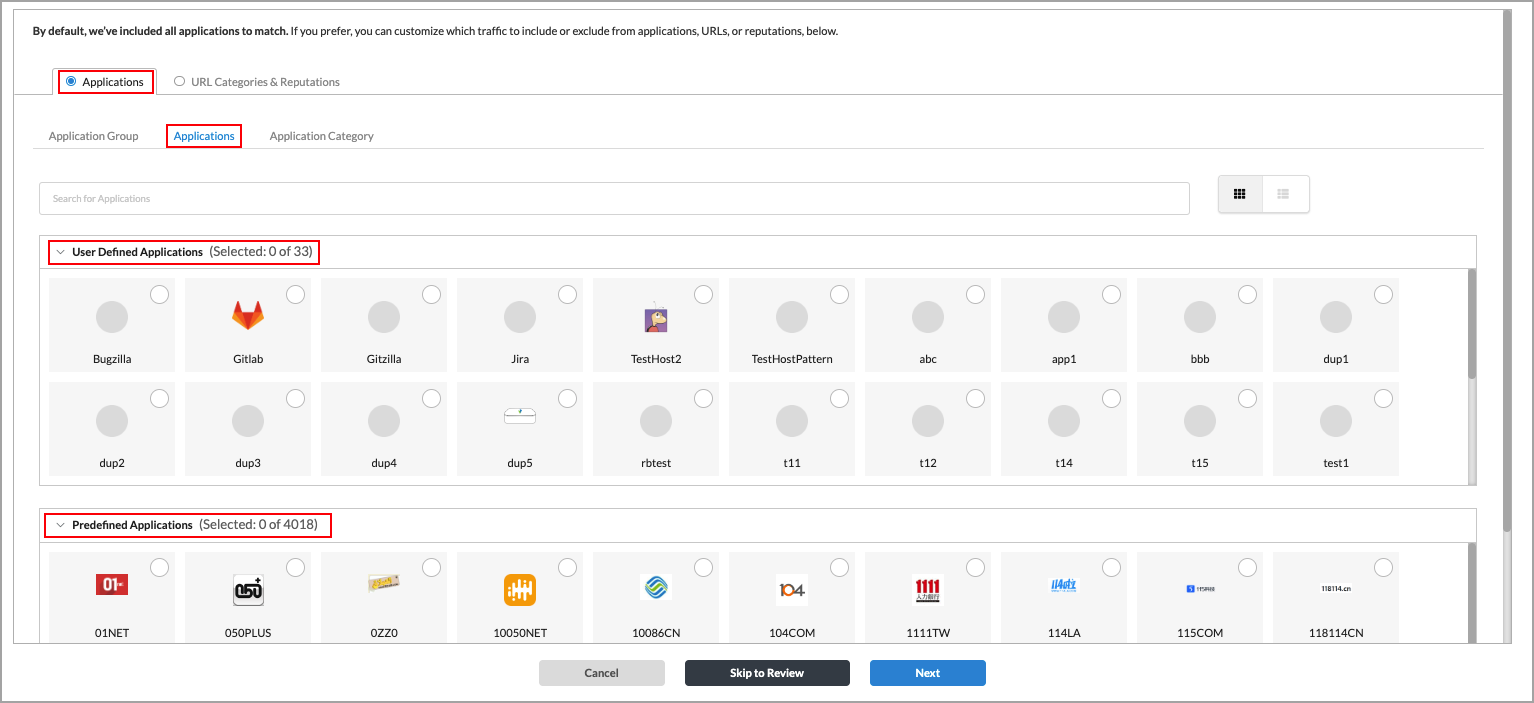
- From here, you can select specific applications, application groups, or application categories to include in the match criteria. All applications, URL categories, and reputation are included by default. You can use this screen to customize which applications, URL categories, and reputation to include in the match criteria.
- To select application groups for the rule to match, on the Application Group tab, click the group category (User Defined Application Groups or Predefined Application Groups), and then select the application groups for the rule to match. You can also use the Search bar to find specific application groups.

- To select applications for the rule to match, select the Applications > Applications tab, click the group category (User Defined Application Groups or Predefined Application Groups), and then select the applications. You can also use the Search bar to find specific applications.
- To select predefined application categories for the rule to match, select the Applications > Application Category tab, and then select one or more predefined application categories. You can also use the Search bar to find specific application categories.

- To select application groups for the rule to match, on the Application Group tab, click the group category (User Defined Application Groups or Predefined Application Groups), and then select the application groups for the rule to match. You can also use the Search bar to find specific application groups.
- Select the URL Categories and Reputations tab. The following screen displays.

- In the URL Categories field, click the down arrow, and then select one or more URL categories for the rule to match.
- In the Reputations field, click the down arrow, and then select one or more reputations to include in the rule:
- High risk
- Low risk
- Moderate risk
- Suspicious
- Trustworthy
- Undefined
- Click Next or select Step 2, Users & Groups.

- To add an existing user group, click Select Users & Groups Profile and click the name of one or more user groups (Group in the figure below).

- To add a new user group, click + Add New User Group. The following screen displays.
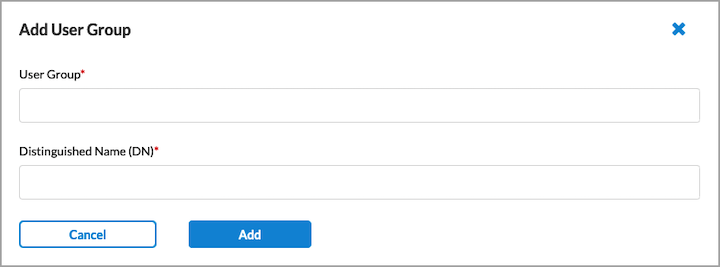
- Enter a user group name and a distinguished name (DN).
- Click Add.
- Select the Users tab.
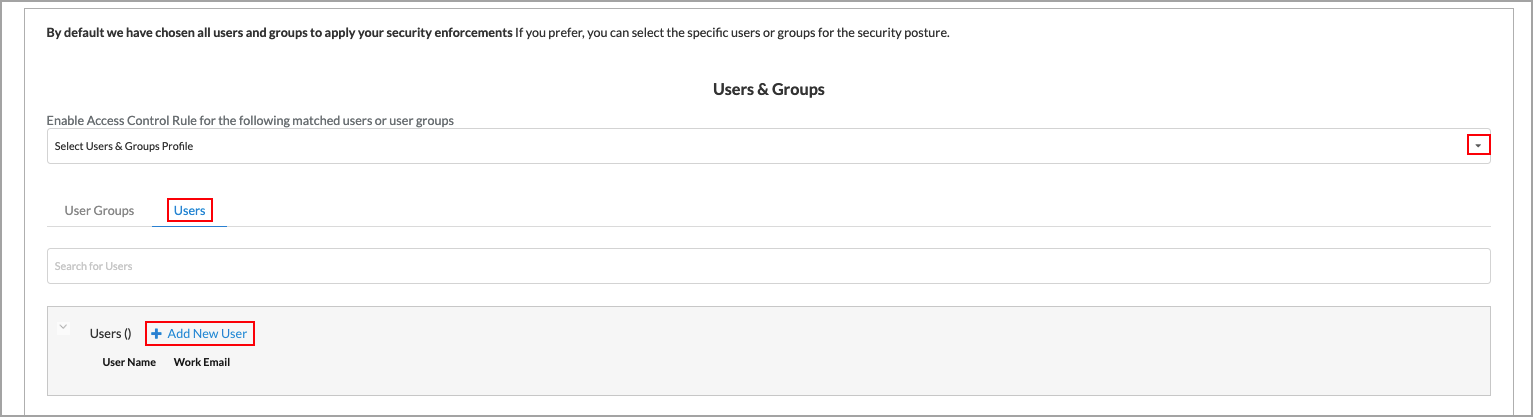
- To add existing users, click Select Users & Groups Profile and click the name of one or more users.

- To add a new user, click + Add New User. The following screen displays.
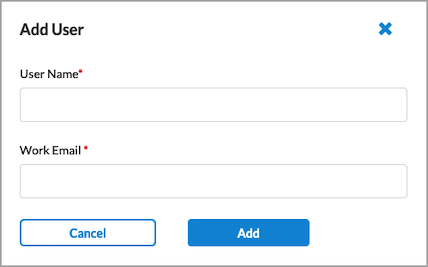
- Enter a user name and a work email address.
- Click Add.
- Click Next or select Step 3, Source & Destination Traffic. The following screen displays. All source and destination traffic is included in the match criteria by default. You can use this screen to customize the source and destination traffic to include in the match criteria.

- To customize the source traffic, on the Source Address tab, use one of the following methods:
- To specify source addresses to include in the match criteria, continue to Step 21.
- To specify source addresses to exclude from the match criteria, select Negate Source Address to match all source addresses except the source addresses that you specify, and then continue to Step 21.
- To specify a source address to include or exclude in the match criteria, you can select a source address from the list or use the search box to find a source address. To create a variable for the source address, click + Add Variable to the right of the source address list. Enter a name for the variable, click the
 Plus icon, then click Add. You can add multiple variables.
Plus icon, then click Add. You can add multiple variables.

You can also enter values for the fields IP address or IP range, IPv4 or the IPv6 subnet, or the IP wildcard as part of the match criteria. To create variables for these values, click + Add Variable for that field.- To add a variable for the IP address or IP range, select IPv4 Address, IPv4 Range, or IPv6 Address from the drop-down list, click the
 Plus icon, the click Add. You can add multiple variables.
Plus icon, the click Add. You can add multiple variables.

- To add a variable for the IP subnet, select IP Subnet or IPv6 Subnet from the drop-down list, click the
 Plus icon, the click Add. You can add multiple variables.
Plus icon, the click Add. You can add multiple variables.

- To add a variable for the IP wildcard, enter a name for the variable, click the
 Plus icon, then click Add. You can add multiple variables.
Plus icon, then click Add. You can add multiple variables.

- (For Releases 12.2.1 and later.) On the Source Address tab, in the VPN Name field, select the VPN through which the IP address is reachable.

- To add a variable for the IP address or IP range, select IPv4 Address, IPv4 Range, or IPv6 Address from the drop-down list, click the
- Click the Destination Address tab. The following screen displays.

- To customize the destination traffic, use one of the following methods:
- To specify destination addresses to include in the match criteria, continue to Step 24 to select addresses.
- To specify destination addresses to exclude from the match criteria, select Negate Source Address to match all destination addresses except the addresses that you specify, and then continue to Step 24 to select addresses.
- To specify a destination address to include or exclude in the match criteria, you can select a destination address from the list or use the search box to find a destination address. To create a variable for the destination address, click + Add Variable to the right of the destination address list. You can also enter values for the fields IP address or IP range, IPv4 or the IPv6 subnet, or the IP wildcard as part of the match criteria. To create variables for these values, click + Add Variable for that field. For more information on adding variables, see step 21.
- Select the Source Zone and Sites tab. The following screen displays. All source zones and source sites are included in the match criteria by default. To customize the source zones and source sites to be included in the match criteria, enter information for the following fields.
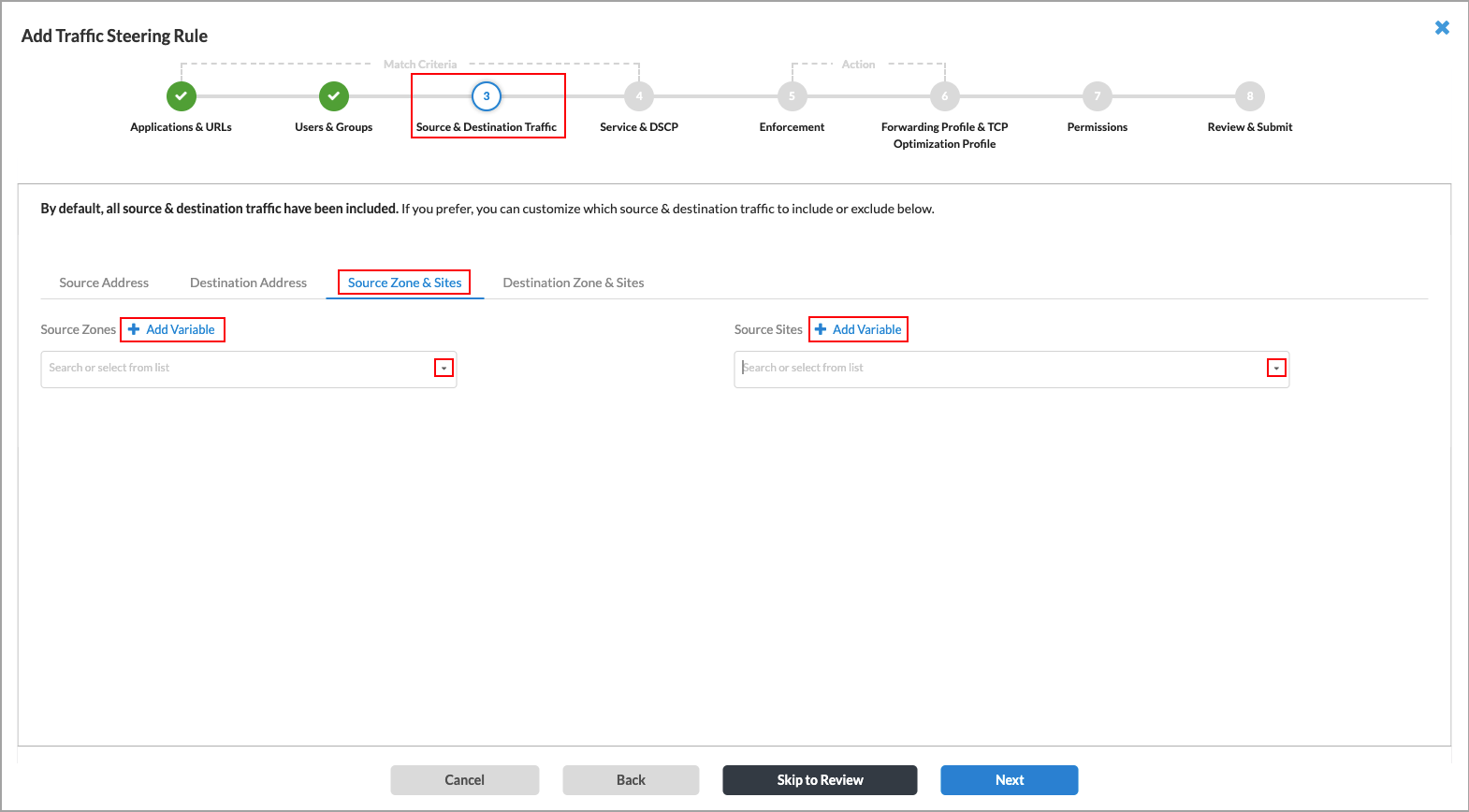
Field Description Source Zones Click the down arrow, and then select one or more zones. To create a variable for the source zone, click
Add Variable.
Source Sites Click the down arrow, and then select one or more sites. To create a variable for the source zone, click
Add Variable.
- Select the Destination Zone and Sites tab. By default, all destination zones and destination sites are included in the match criteria. To customize the destination zones and destination sites to be included in the match criteria, enter information for the following fields.

Field Description Destination Zones Click the down arrow, and then select one or more zones. To create a variable for the source zone, click
Add Variable.
Destination Sites Click the down arrow, and then select one or more sites. To create a variable for the source zone, click
Add Variable.
- Click Next or select Step 4, Service & DSCP. The following screen displays. All services, service groups, and DSCPs are included in the match criteria by default. You can use this screen to customize the services, service groups, and DSCPs to include in the match criteria.

- To specify the services to include, do one or both of the following:
- In the search box under Services, enter the service name.
- Select one or more services from the list below the search box. You can select one of the following categories to filter the list:
- All Services
- Predefined
- User Defined
- Select the Service Groups tab, then select the service group to which you want to apply security access control rules. You can select User-Defined, Predefined, or both. Click the
Toggle Row Expand icon next to the service group name to view the details for each service group.

- Select one or more service groups to include in the match criteria. The service groups are added to the Services list.
- Select the DSCP tab. All DSCP decimal values are included by default. You can specify which DSCP decimal values to include in the match criteria.
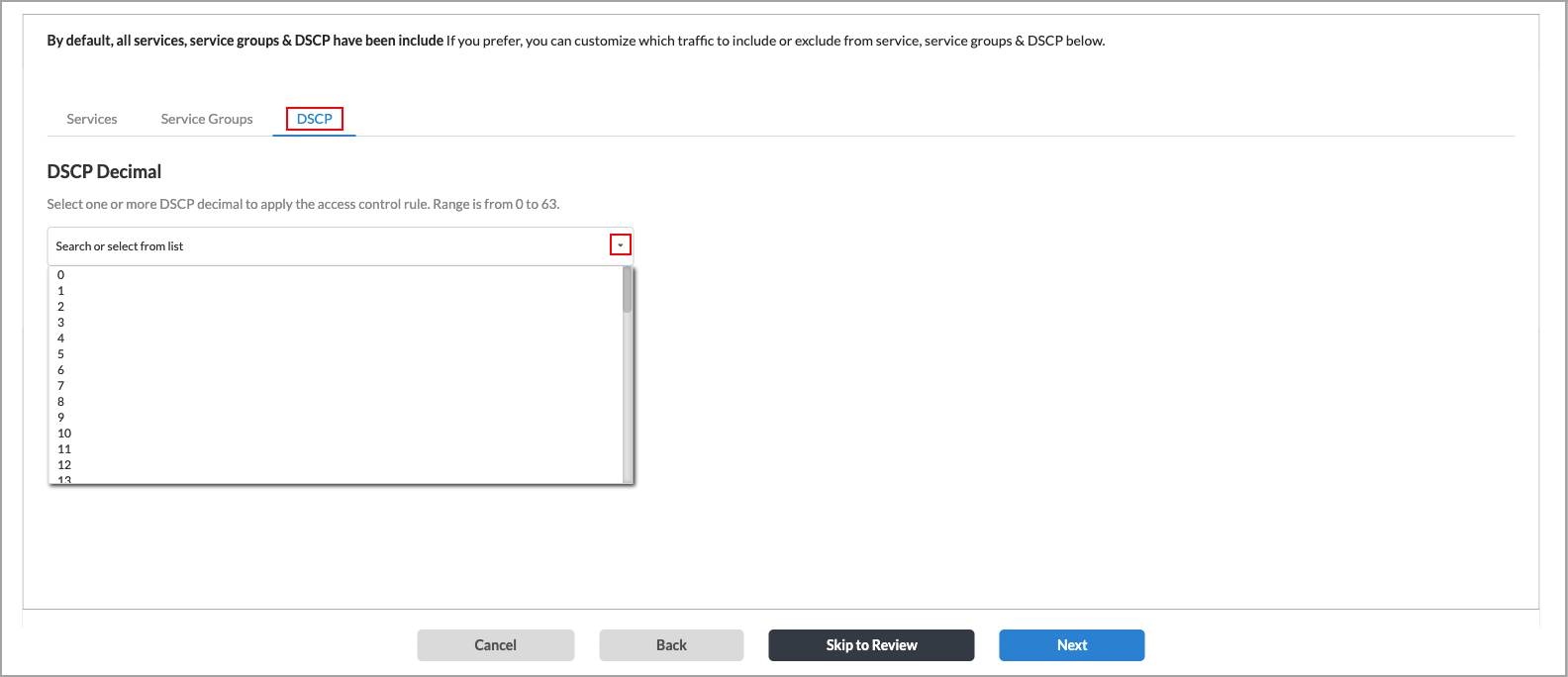
- Select one or more DSCP decimal values from the drop-down list, or use search to locate one or more values.
- Click Next to go to Step 5, Enforcement. Security enforcement rules define the actions to take on traffic that meets the previously defined match conditions, and defines the security enforcement actions to apply to matching traffic. The following screen shows the available security enforcement actions.
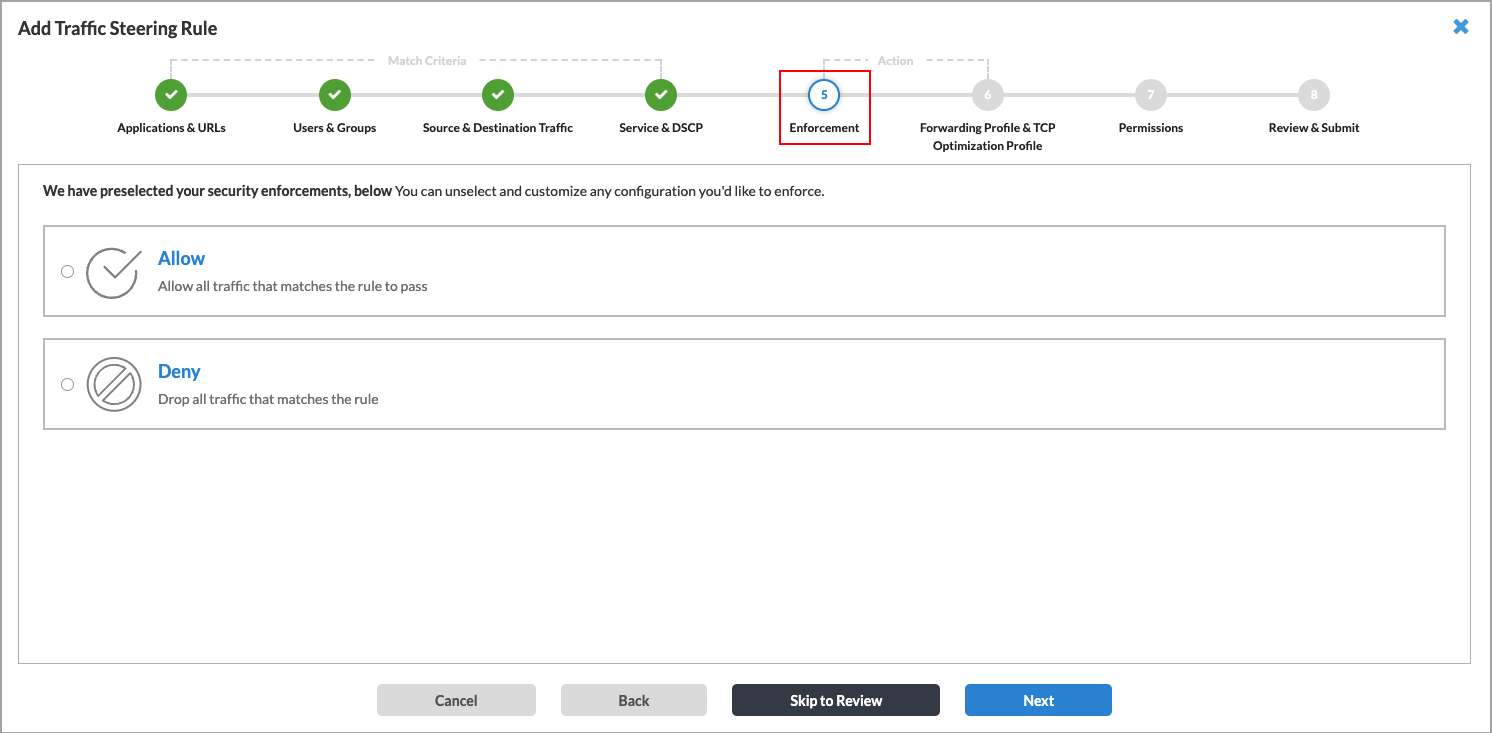
- Click one of the following options to apply a security enforcement action:
- Allow—Allow all traffic that matches the rule to pass unfiltered.
- Deny—Drop all traffic that matches the rule.
- Click Next to go to Step 6, Forwarding Profile & TCP Optimization Profile and enter the following information.

Field Description Forwarding Profile Select a forwarding profile from the list. A forwarding profile is a configuration setting that determines how network traffic is handled and forwarded within a network device. TCP Optimization Profiles Policy (Group of Fields) TCP optimization profiles are configurations or settings that can be applied to TCP to improve its performance in specific network environments. - Mode
Select a TCP optimization mode:
- Auto
- Bypass—Disable TCP optimizations.
- Forward proxy
- Proxy
- Reverse proxy
- Splice
- Bypass Latency Threshold
Enter how much latency must be measured before TCP optimizations begin.
Range: 0 through 60000 milliseconds
Default: 10 milliseconds
- TCP Optimization Profile for LAN
Select a LAN profile.
For proxy mode, you must configure a TCP profile.If you do not select TCP profiles, a system default LAN profile is applied that uses the cubic congestion control algorithm and duplicate ACK loss detection.
- TCP Optimization Profile for WAN
Select a WAN profile.
For proxy mode, you must configure a TCP profile.
If you do not select TCP profiles, a system default WAN profile is applied that uses the BBR congestion control algorithm and RACK loss detection.
- Click Next to go to Step 7, Permissions, and revise the permissions, if needed.

- Click Next to go to Step 8, Review and Submit and enter the following information.

Field Description General (Group of Fields) - Name
Enter a name or the rule. - Description
(Optional) Enter a description for the rule. - Tags
(Optional) Enter one or more tags. A tag is an alphanumeric text descriptor with no spaces or special characters. You can specify multiple tags added for the same object. The tags are used for searching the objects. - Schedule
Select a schedule to set the time and frequency at which the rule is in effect. - Enabled
Click to disable the rule once it is saved. By default, the rule is enabled. - Logging Disabled
Click to the slider bar to enable logging for the rule. By default, logging is disabled. - Review the selected settings. Click the
 Edit icon to change a setting, as needed.
Edit icon to change a setting, as needed. - Click Save to save the rule.
- In the Add Traffic Steering Policy screen, click Step 2, Permissions. The following screen displays.

- To change the permissions for a role, select Edit, Hide, or Read in the Permissions column.
- Click Next to go to the Step 3, Review and Submit.

- In the General box, enter a name for the traffic steering policy, and optionally enter a text description for the policy and one or more tags. A tag is an alphanumeric text descriptor with no spaces or special characters. You can specify multiple tags added for the same object. The tags are used for searching the objects.
- Review the settings you have selected. Click the
 Edit icon to change a setting, as needed.
Edit icon to change a setting, as needed. - Click Save to create the traffic steering policy.
Supported Software Information
Releases 10.2.1 and later support all content described in this article, except:
- Release 12.1.1 adds support for the Negate Source Address and Negate Destination Address options when configuring a traffic-steering rule.
- Release 12.2.1 adds support for the VPN name option to include in the source address match list.
Additional Information
Configure Profiles
Configure Security Access Control Policies and Rules
