Configure Service and Session Options
![]() For supported software information, click here.
For supported software information, click here.
A Versa Operating SystemTM (VOSTM) device is preconfigured with service options that define optimal operational and performance parameters for the device. In most cases you should never modify these parameters without explicit guidance from a Versa Networks technical team member. However, you can choose to modify the following:
- Maximum number of sessions allowed on a VOS device. This maximum is the total number of sessions for all tenants on the VOS device.
- Session-related parameters, such as the timeout values for a session and for particular protocols, and the TCP MSS adjustment.
- IPsec cipher key check, to comply with NIAP FCS_IPSEC_EXT.1.14 requirements (for Releases 22.1.1 and later).
- Least loaded worker thread mode. You can configure this option to monitor the service load for each worker thread and distribute new sessions to minimize the maximum worker thread service load.
Note: For options not discussed in this article, do not modify them without explicit guidance from a Versa Networks technical team member.
Change the Maximum Number of Allowed Sessions
The default maximum number of sessions that a VOS device supports is automatically adjusted down or up based on the total amount of system memory.
The following table shows the maximum number of sessions supported for different amounts of memory. It is recommended that you not increase the maximum number of sessions beyond the values shown in the table, because the VOS software is tuned to handle the maximum values.
| Total Memory (RAM) | Maximum Number of Sessions |
|---|---|
| 4 GB | 32,000 |
| 8 GB | 100,000 |
| 16 GB | 500,000 |
| 32 GB | 1,000,000 |
| 64 GB | 2,500,000 |
| 96 GB | 4,000,000 |
| > 96 GB | 5,000,000 |
For an amount of RAM not listed in the table above, the default maximum number of sessions is 5,000,000.
Note that you should change the maximum number of sessions only during a service maintenance window, because as soon as you make the change, all services on the VOS device restart automatically.
For Releases 21.1.3 and later, and Releases 21.2.1 and later, you can modify the default maximum of sessions. However, before you change the values, it is recommended that you contact Versa Networks Customer Support.
It is recommended that you monitor the number of sessions and change the maximum number of sessions based on your peak production loads. For a VOS device to be operational, memory consumption should always be less than 90 percent. For VOS devices that have more than 32 GB RAM, you should also change the session limit at the tenant level. Otherwise, the maximum number of sessions is limited to 1 million per tenant regardless of the maximum limit set on the device. Note that when you change the session limit at the tenant, you do not need to restart services on the VOS device. To change the session limit for a tenant, see Configure Organization Limits.
Because the earlier default value for the session limit was 1,000,000 (for releases prior to Release 21.2.1) , if you configure a value of 1,000,000, you cannot distinguish between an explicitly configured value and the earlier system default. It is recommended that you configure a value slightly more or less than 1,000,000 to override the older default value of 1,000,000.
To change the maximum number of allowed sessions on a VOS device:
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Devices > Devices in the left menu bar.
- Select an organization in the left menu bar.
- Select a device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > System > Configuration > Configuration in the left menu bar.

- In the Service Options pane, click the
 Edit icon.
Edit icon. - In the Edit Service Options popup window, select the General tab.
- In the Maximum Allowed Session field, enter the number of sessions.

- Click OK. Note that you should change the maximum number of sessions only during a service maintenance window, because as soon as you click OK, all services on the VOS device restart automatically.
Configure IPsec Cipher Key Check
For Releases 22.1.1 and later.
You can configure a VOS device to meet NIAP FCS_IPSEC_EXT.1.14 requirements by enabling the IPsec cipher key check option. Enabling IPsec cipher key check affects the VOS device only when FIPS mode is enabled on the device. For information about enabling FIPS mode, see FIPS Compliance.
To view, enable, or disable IP cipher key check for a VOS device:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > System > Configuration > Configuration in the left menu bar. The following screen displays.

- In the Service Options pane, scroll down to view the setting for IPsec Cipher Key Check. A checked box icon indicates that a feature is enabled, and an unchecked box icon indicates that a feature is disabled.

- To enable or disable the IPsec cipher key check option, click the
 Edit icon. The Edit Service Options screen displays.
Edit icon. The Edit Service Options screen displays.

- Click the IPsec Cipher Key Check box to change the setting.
- Click OK.
Configure Least Loaded Worker Thread Mode
To configure least loaded worker thread mode for a VOS device:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a VOS device in the main pane. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > System > Configuration > Configuration in the left menu bar. The following screen displays.
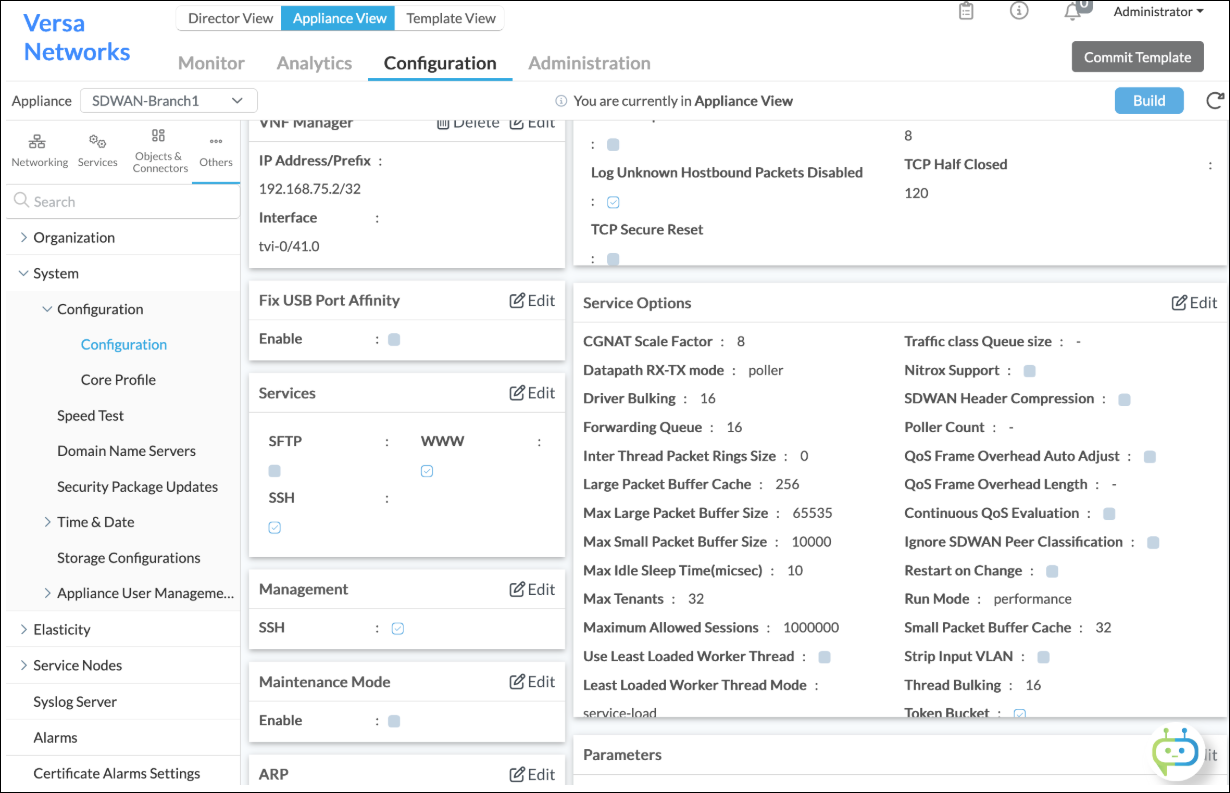
- In the Service Options pane, scroll down to view the setting for Least Loaded Worker Thread. A checked box icon indicates that a feature is enabled, and an unchecked box icon indicates that a feature is disabled. Click the
 Edit icon.
Edit icon.

- In the Edit Service Options screen, enter information for the following fields.

Field Description Least Loaded Worker Thread Mode Specify the metric to use for worker thread workload, which determines how sessions are distributed. The least loaded worker thread mode preserves the legacy (flawed) redistribution of workload based on session count for backward compatibility.
- Service load (This is the default.)
- Session count
Use Least Loaded Worker Thread Click the checkbox to enable the distribution of sessions based on worker thread workload.
For Release 22.1.3 and Release 22.1.4 builds dated 2024-11-12 or earlier, restart Versa Networks services for the changes to take effect.
- Click OK.
Configure Session Parameters
To configure session parameters:
- In Director view:
- Select the Configuration tab in the top menu bar.
- Select Templates > Device Templates in the horizontal menu bar.
- Select an organization in the left menu bar.
- Select a template in the main pane. The view changes to Appliance view.
- Select Others > System > Configuration > Configuration in the left menu bar. The main pane displays various configuration-related panes.

- In the Sessions pane, click the
 Edit icon. In the Edit Sessions popup window, enter information for the following fields.
Edit icon. In the Edit Sessions popup window, enter information for the following fields.

Field Description Timeout (Group of Fields) Define session timeout values. All session timeout values except for Hard Session are the idle time period in seconds. The idle timer starts when the last packet in either direction was last seen.
- Default
This field is deprecated and is not used. - Hard Session
Total duration of a session, after which the session times out. Note that this value is not an idle timeout but rather the lifetime of a session. - ICMP Session
Idle timeout for ICMP sessions.
Default: 10 seconds
- TCP Half Open
Timeout for a TCP sessions after it receives a SYN and before completion of the three-way handshake.
Default: 8 seconds- TCP Half Closed
Timeout for a TCP session after it receives the first FIN and before it receives the second FIN or a RST.
Default: 120 seconds- TCP Session
Idle timeout for TCP sessions.
Default: 240 seconds
- TCP Wait
Session idle timeout after a TCP session has received a FIN or RST flag in either direction.
Default: 20 seconds
- UDP Session
Idle timeout for UDP sessions.
Default: 30 seconds
Flags (Group of Fields) - Allow Unsupported Protocol
Click to accept non-IP protocol packets. The VOS device performs an IP protocol validity check to determine the packet's protocol. - Check TCP SYN
Click to reject the first packet of a TCP session if, when the TCP session is being set up, the SYN flag is not set in the first packet. To accept the first packet, ensure that this option is not clicked.
By default, the VOS device firewall rejects the first packet if the packet's SYN flag is not turned on. This security measure is taken is because normal TCP connections start with a three-way handshake, which means that if the first packet that the firewall sees is not the SYN packet, it is likely that the packet is not valid and the firewall discards it. In cases such as asymmetric routing, you might want to disable this feature.
- Reevaluate Reverse Flow
Click to reevaluate the packet policy for first packet of a reverse flow if the forward flow action is set to Drop. - Send ICMP Unreachable
Click to send ICMP unreachable messages to a source if a route lookup fails. - Session Reevaluate
Click to reevaluate a session when the configuration or a route changes. - TCP Secure Reset
Click to follow the secure criteria for accepting TCP reset (RST) packets. - TCP Send Reset
Click to send a TCP RST packet to the source if the SYN flag in the first packet of a new TCP flow is not set. TCP MSS Adjustment (Group of Fields) Configure the largest packet, in bytes, that the VOS device can receive in a single TCP segment. The MSS does not include the TCP header (20 bytes) or the IP header (20 bytes). - Enable
Click to allow the TCP MSS on an interface to be adjusted. - Interface Types
Select the interface on which to set TCP MSS adjustment value:
- All—Set on all interfaces.
- Tunnel—Set only for the traffic that goes through the tunnel interface.
- MSS Value
Enter the TCP MSS value.
Range: 512 to 8960 bytes
Interim Update (Group of Fields) Configure interim update parameters. - Disable
Click to disable interim updates. - Interim Update Interval
Enter the time between updates.
Range: 60 to 3600 seconds
Log Unknown Host-Bound Packets (For Releases 22.1.3 and later.) Configure the logging of unknown packets that are destined for a VOS IP address. - Disable
Click to disable the logging. - Interval
Enter the logging time.
Default: 60 seconds - Click OK.
Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- For Release 21.2.1, the default maximum number of sessions that a VOS device supports is automatically adjusted down or up based on the total amount of system memory.
- Release 22.1.1 adds the IP cipher key check.
- Release 22.1.3 adds the log unknown host-bound packets session option.
Additional Information
Configure Organization Limits
Configure Site-to-Site Tunnels
Versa Solution Scalability
