Configure Threat Intelligence from VMS
![]() For supported software information, click here.
For supported software information, click here.
Threat intelligence enhances your organization's security posture by providing real-time, actionable insights into potential threats. It helps you identify, track, and mitigate cyber threats proactively.
You enable the threat intelligence microservice from Versa Messaging Service (VMS) and configure it to receive threat feeds from external sources. You can configure different threat feeds for each tenant, using criteria such as IP address, IP address combined with a port, domain name, and URL. You can configure each tenant for preferred threat feed categories and use these in access policy rules to filter traffic.
When the threat intelligence microservice receives a threat feed, it validates the data, removes any invalid entries, and stores the valid entries in a local database. If a database exists for the downloaded feed, threat intelligence compares the new feed with the existing entries in the database and adds new entries or deletes outdated ones. VMS then sends the delta threat feed to Versa Operating SystemTM (VOSTM) devices.
To receive threat feeds, you activate threat intelligence for the VMS connector of your tenant, and then enable relevant threat intelligence feeds.
Enable and Configure Threat Intelligence
To enable and configure threat intelligence for a tenant:
- In Director view, select the Administration tab in the top menu bar.
- Select Connectors > VMS in the left menu bar.
- To add a VMS connector, click + Add. To update a connector, select an existing one. The Configure VMS Connection configuration wizard displays.
- Add or update the required information in the VMS Connection and VMS Cluster screens. For more information, see Configure a VMS Connector.
- Select step 3, Tenants and Services, in the top menu bar.

- Select the tenant or tenants for which you want to enable threat intelligence. Click Select All to select all tenants. Selected tenants display in the Tenant Selected section. For example:
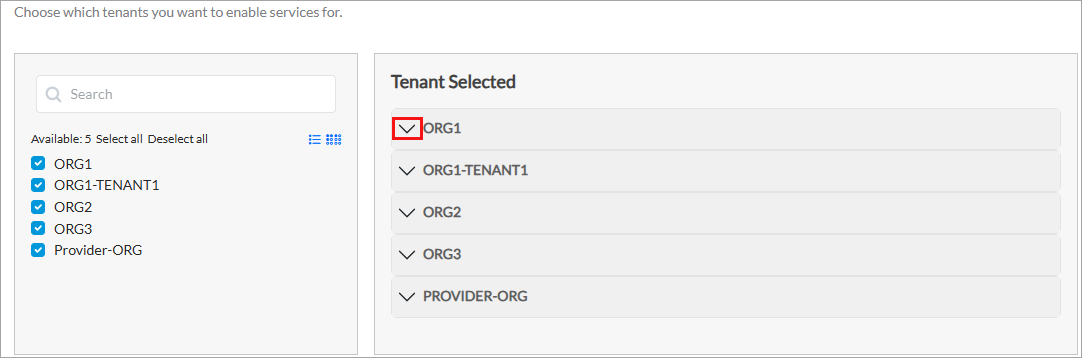
Note that to clear a tenant selection for an existing VMS connector, you must first disable the VMS services on the VOS devices for that tenant. - From the Tenant Selected section, click the down arrow of the tenant for which you want to enable threat intelligence. The list of services displays, as shown below.

- Click the Threat Intel toggle to enable threat intelligence, and then enter information for the following fields.
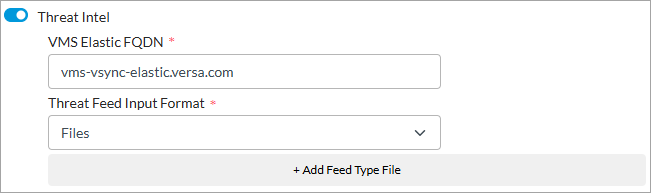
Field Description VMS Elastic FQDN Enter the FQDN of the VMS host to which the external server connects to share threat intelligence data. Threat Feed Input Format Select the format in which to share or save threat feeds. Currently, the Files option is supported. - To add threat feed categories, click + Add Feed Type File, and then enter information for the following fields.

Field Description Threat Feed Category
Select the threat feed category from these options:
- IP and Port—These threat feeds include combinations of IP addresses and specific ports, IP address range, and port range associated with malicious activity. For example, 11.0.0.1|11001, 12.0.0.1|12000-12009,
13.0.0.1-13.0.0.100|1300, 14.0.0.1-14.0.0.100|14000-14009, 15.0.0.1-15.0.0.100. - IP—These feeds contain standalone IP addresses and IP addresses with subnet mask that have been observed to participate in malicious activities. For example, 1.0.1.0/24, 1.0.2.0/24, 8.8.8.8.
- FQDNs—These feeds include domain names associated with malicious infrastructure. For example, google.com, cnn.com.
- URL Patterns—These feeds consist of specific URL paths to match URLs that fall within a defined pattern. This otpion supports hyperscan regex patterns. For example, cnn.com, bbc.com, ^(www|maps|news)?\.?google.com.
- URL Strings—These feeds consist of URL strings used to perform an exact match against the specified URL. For example, amazon.in/gift-card-store/b/?ie=UTF8&node=3704982031&ref_=nav_cs_gcflipkart.com/travel/flights?otracker=nmenu_Flights.
Threat Feed Type
Select the type of threat feed. For example, user-defined. Threat Feed Name
Enter a name for the threat feed. Threat Feed File Format
Select a file format for the feed, such as Text. Threat Feed Endpoint FQDN
Enter the FQDN of the external threat feed server to which VMS connects. Threat Feed Port
Enter the port number of the external threat feed server. Threat Feed Endpoint Path
Enter the path of the threat feed server from which VMS downloads threat feed data. Threat Feed Refresh Frequency (mins)
Enter the frequency, in minutes, to refresh the threat feed.
Default: 5 minutes.Threat Feed Authentication Mode
Select the authentication mode for the feed:
- No Authentication
- API Authentication Header
- Password Authentication
+ Add Cert
Click to select and upload a CA certificate to connect to the threat feed server.

- IP and Port—These threat feeds include combinations of IP addresses and specific ports, IP address range, and port range associated with malicious activity. For example, 11.0.0.1|11001, 12.0.0.1|12000-12009,
- Perform the remaining steps as described in Configure a VMS Connector to complete the configuration.
Use Threat Feeds in Access Policies
You associate threat feeds for the following categories with access polices, as follows:
- IP address—Configure External Dynamic address group and associate with access policy.
- URL patterns—Configure Custom URL category and associate with access policy or URL filtering profile.
Currently, categories 'FQDN' and 'IP address and port', support only Block by default.
Associate IP Address Threat Feeds with an NGFW Access Policy Rule
To associate IP address threat feeds with an NGFW access policy:
- Configure an address group, and then add the IP address threat feed type to that group:
- In Director view > Appliance view, select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Address Groups. The main pane displays the configured address group objects.
- Select an existing address object or click + Add. The Add/Edit Address Group window displays.

- For the Type field, select External Dynamic Address. The Kind field displays.
- For the Kind field, select one of the following:
- Exclusive—Specific to a tenant.
- Shared—Shared address group configured in a parent tenant and can be shared with tenants.
- From the User-defined Address Feeds field, click the
 icon, and then enter the name of IP threat feed you entered in the Threat Feed Name while configuring a VMS connector. For more information, see Step 7 in Enable and Configure Threat Intelligence above.
icon, and then enter the name of IP threat feed you entered in the Threat Feed Name while configuring a VMS connector. For more information, see Step 7 in Enable and Configure Threat Intelligence above. - For information about configuring other parameters, see Configure Address Group Objects.
- Click OK.
- To use the same address group in other tenants, add an address group for the provider organization as shown in Step 1, and for the Kind field, select Shared. To add this address group in other tenants:
- In Director view > Appliance view, select the Configuration tab in the top menu bar.
- Select Others > Organization > Limits in the left menu bar. The main pane displays the organizations associated with the Controller node.
- Click an organization name in the main pane for which you want to add the address group from the provider organization. The Edit Organization Limit popup window displays.

- Select the Resources tab.
- Under Available Address Groups, click the
 icon. All Shared address groups of the provider organization display. Select the shared address group or groups.
icon. All Shared address groups of the provider organization display. Select the shared address group or groups. - For information about configuring other parameters, see Configure Organization Limits.
- To associate an address group for IP threat feeds with an NGFW policy rule:
- Select the Configuration tab in the top menu bar.
- Select Services > Next Gen Firewall > Security > Policies in the left menu bar, and select the Rules tab.
- Select an existing rule or click + Add to add one. The Add/Edit Rule window displays.

- Select the Destination tab.
- Under Destination Address, Click the
 icon, and then select an address group (shared or exclusive) that you added in Step 1, above.
icon, and then select an address group (shared or exclusive) that you added in Step 1, above. - For configuring other parameters, see Configure Access Policy Rules (ACL Rules).
Associate URL Patterns Threat Feeds with an NGFW Access Policy Rule or URL Filtering Profile
- Configure a URL category, and then add the URL Patterns threat feed type to that category:
- In Director view > Appliance view, select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Custom Objects > URL Categories in the left menu bar.
- Select an existing category or click + Add. The Add/Edit URL Category window displays.

- In the General tab, from the Kind field, select one of the following:
- Exclusive—Specific to a tenant.
- Shared—Shared URL category configured in a parent tenant and can be shared with tenants.
- From the User-defined Feeds field, click the
 icon, and then enter the name of URL Pattern feed you entered in the Threat Feed Name while configuring a VMS connector. For more information, see Step 7 in Enable and Configure Threat Intelligence, above.
icon, and then enter the name of URL Pattern feed you entered in the Threat Feed Name while configuring a VMS connector. For more information, see Step 7 in Enable and Configure Threat Intelligence, above. - For information about configuring other parameters, see Configure Custom URL Categories.
- Click OK.
- To use the same URL category in other tenants, add the URL category for the provider organization as shown in Step 1, and from the Kind field, select Shared. To add this category in other tenants:
- In Director view > Appliance view, select the Configuration tab in the top menu bar.
- Select Others > Organization > Limits in the left menu bar. The main pane displays the organizations.
- Click an organization name in the main pane for which you want to add the address group from the provider organization. The Edit Organization Limit popup window displays.

- Select the Resources tab.
- Under Available URL Categories, click the
 icon. All Shared URL categories of the provider organization display. Select the the required URL categories.
icon. All Shared URL categories of the provider organization display. Select the the required URL categories. - For information about configuring other parameters, see Configure Organization Limits.
- To associate a URL category for URL Patterns feeds with an NGFW policy rule:
- Select the Configuration tab in the top menu bar.
- Select Services > Next Gen Firewall > Security > Policies in the left menu bar, and then select the Rules tab.
- Select an existing rule or click + Add to add one. The Add/Edit Rule window displays.

- Select the Applications/URL tab.
- Under URL Category List, click the
 icon, and then select a URL category that you added in Step 1, above.
icon, and then select a URL category that you added in Step 1, above. - For configuring other parameters, see Configure Access Policy Rules (ACL Rules).
- To associate URL Patterns threat feeds with a URL filtering Profile:
- In Director view > Appliance view, select the Configuration tab in the top menu bar.
- Select Services > Next Gen Firewall > Security > Profiles > URL Filtering in the left menu bar.
- Select an existing URL filtering profile or click the
 icon add to add one. The Add/Edit URL Filter window displays.
icon add to add one. The Add/Edit URL Filter window displays.

- Select the Category-Based Action tab, and click the
 icon to add actions for categories. The Add Category Based Action window displays.
icon to add actions for categories. The Add Category Based Action window displays.

- Enter a name and select the action (here, Block).
- Under User Defined Categories, select the URL category you added in the steps to configure a URL category (here, ORG1-URL-Feed-Exclusive-1).
- For configuring other parameters, see Configure a URL-Filtering Profile.
- Click OK.
Enable Streaming Feeds for Threat Intelligence
You can enable the VOS device (branch) to receive threat intelligence streaming feeds from the VMS server. To do this, you associate a messaging server profile with the threat intelligence microservice that you configured in Enable and Configure Threat Intelligence, above. For more information about VMS messaging server profiles, see Configure a Messaging Server Profile.
To enable streaming feeds for threat intelligence:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select an Appliance in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Others > Organization > Messaging Service > VMS Service in the left menu bar. You can enable streaming feeds for threat intelligence IP address, IP Port, FQDN, and URLs, as highlighted in the following screenshot.

- Click the
 Edit icon next to the threat intelligence category for which you want to enable streaming feeds. The Edit Threat Intel <category name> VMS Service popup window displays. For example, the screenshot below displays when you select Threat Intel IP Address. Note that the fields are the same for all the categories you select from the VMS Service screen.
Edit icon next to the threat intelligence category for which you want to enable streaming feeds. The Edit Threat Intel <category name> VMS Service popup window displays. For example, the screenshot below displays when you select Threat Intel IP Address. Note that the fields are the same for all the categories you select from the VMS Service screen.
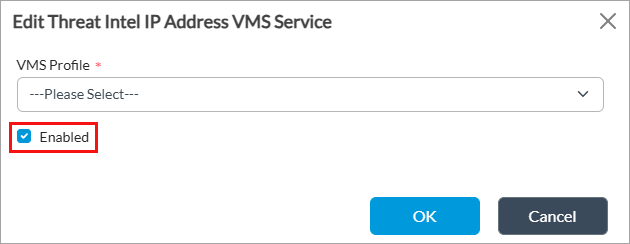
- In the VMS Profile field, select a VMS server profile. For more information, see Configure a Messaging Server Profile, above.
- Click Enabled to enable the service.
- Click OK. For more information, see Enable Stream Feeds for VMS Services.
Monitor Threat Intelligence Statistics
You can monitor VMS threat intelligence statistics for threat intelligence categories such as IP address and port, IP address, FQDNs and URL patterns. For more information, see Monitor Device Services.
To monitor threat intelligence services:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select an organization and click Devices.
- Select a device, and then click Services > VMS. The threat intelligence statistics display, as shown below.

- Click View in the Current column to view current statistics for the server, such as the number of messages received, dispatched, dropped, connection status and connect time, and the last sequence number. For example:

- Click View in the Total column to view total statistics for the server, such as the number of messages received, dispatched, dropped, and failovers detected. For example:

Display Threat Intelligence Logs
- In Director view, select the Analytics tab from the top menu bar. The view changes to Analytics view.
- Select Logs > Threat Intelligence in the left menu bar.

- Select the organization, tenant, and the period for which to display threat intelligence analytics logs. The following screen displays.

- Select the Exception tab to view exception logs for threat intelligence. In the example below, download has failed and action taken is Deny.

Supported Software Information
VMS Releases 5.2.2 and later support all content described in this article.
