Manage Users
![]() For supported software information, click here.
For supported software information, click here.
The Users screen displays users and their roles. Two roles are available for service providers—Service Provider Administrator and Service Provider Operator—and two roles are available for enterprises—Enterprise Administrator and Enterprise Operator.
In Releases 10.2.1 and later, the Users screen contains the Active column to show which users are currently active.
If a user has an account on an external server, such as an LDAP, a RADIUS, a TACACS+, or other server, the External User column displays Yes in the row for that user.
Create a New User
You can create users at the top-level Service Provider tenant or at the Enterprise tenant level.
To create users:
- If you are a Service Provider administrator and want to create a new top-level Service Provider user:
- Log in as Service Provider administrator. The Tenants screen displays.

- Click the Users lifecycle in the left navigation bar. The Users home screen displays all current users.

- Click the + User button. The Create User screen displays.
- Continue with Step 5.
- Log in as Service Provider administrator. The Tenants screen displays.
- If you are a Service Provider administrator and want to create a new user for a child tenant:
- In the top-level Service Provider screen, click the Tenant lifecycle in the left navigation bar. The Tenants screen displays all current tenants.

- Click the name of the tenant to which you want to add a new user or users (ACME in the above example). The landing page for the tenant displays. Note that the landing page for each tenant is configured when the tenant is created, so it may differ from tenant to tenant.
- Select the Users lifecycle in the left navigation bar. The Users screen for the tenant displays all currently configured users.

- Click the +User button. The Create User screen displays.
- Continue with Step 5.
- In the top-level Service Provider screen, click the Tenant lifecycle in the left navigation bar. The Tenants screen displays all current tenants.
- If you are an Enterprise administrator and want to create a new Enterprise user:
- Log in as Enterprise Administrator. The landing page for the tenant displays. Note that the landing page for each tenant is configured when the tenant is created, so it may differ from tenant to tenant.
- Select the Users lifecycle in the left navigation bar. The Users screen for the tenant displays all currently configured users.

- Click the +User button. The Create User screen displays.
- Continue with Step 5.
- If you are an Enterprise administrator and want to create a new Enterprise user for a child tenant:
- Log in as Enterprise Administrator. The landing page for the tenant displays. Note that the landing page for each tenant is configured when the tenant is created, so it may differ from tenant to tenant.
- Select Tenant lifecycle in the left navigation panel. The Enterprise Tenants screen displays the tenant and its child tenants.

- Click the name of the tenant to which you want to add a new user or users.
- Select the Users lifecycle in the left navigation bar. The Users screen for the tenant displays all currently configured users.
- Click the +User button. The Create User screen displays.
- Continue with Step 5.
- In the User lifecycle screen, click + User. In the Create User screen, enter information for the following fields.
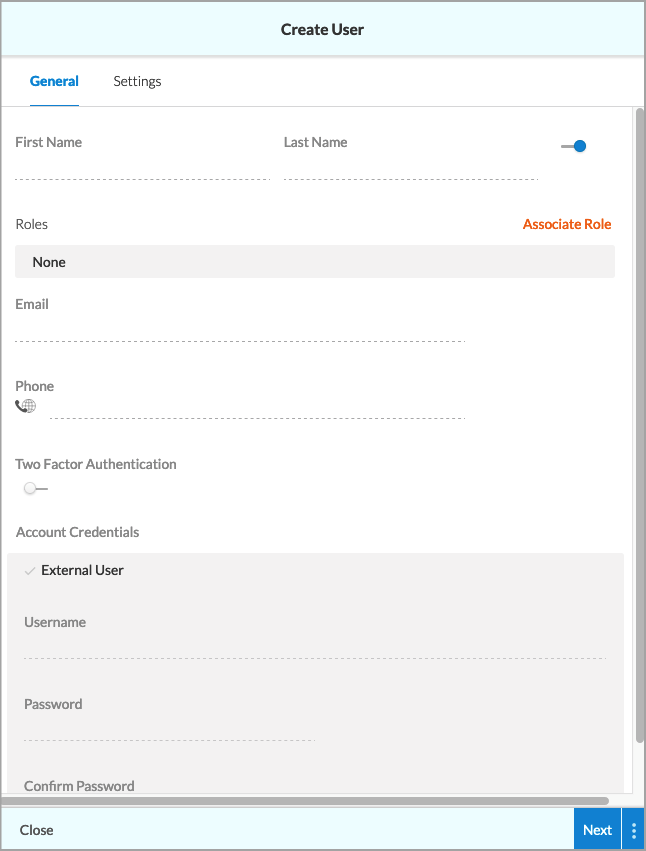
Field Description First name (Required) Enter the user's first name. Last name (Required) Enter the user's last name. The slide bar to the right indicates that the user's status is enabled. Click the slide bar to disable the user's status. Role (Required) Click Associate Role. The Associate Role screen displays. Choose a role for the new user, and then click Save. The example below shows that a default service provider operator role has been selected.

Email (Required) Enter the user's email address. Phone Enter the user's phone number. This is required when you enable two-factor authorization. Two-Factor Authentication (For Releases 10.2.1 and later.) Click the slide bar so that it is blue to enable two-factor authentication. Account Credentials (Group of Fields) - External User
Click if the user is an external user. - Username (Required)
Enter the user's username. - Password
Enter the user's password for an internal user. You cannot change the password for an external user. - Confirm password
For internal users only, enter the user's password again. - Select the Settings tab, or click Next, and enter information for the following fields.
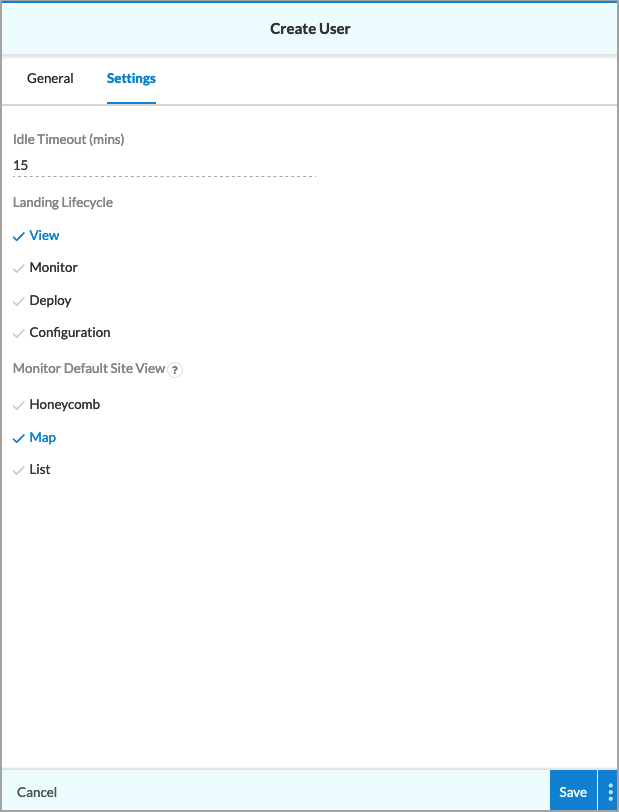
Field Description Idle Timeout Enter how long, in minutes, the user can be idle before being logged out. Landing Lifecycle Choose the lifecycle screen to display when the user first accesses Concerto orchestrator. Monitor Default Site View Choose which view to display when the user first accesses Concerto orchestrator. - Click Save.
Configure User Settings
For Releases 11.4.1 and later.
You can configure settings for users in the User Settings screen, including settings for the password policy. The User Settings screen is available at the Service ;Provider level and is applicable to all users at the Service Provider and Enterprise levels.
To configure user settings:
- In Service Provider view, click the Users lifecycle in the left navigation panel, and then select User Settings.

- In the User Settings screen, enter information for the following fields.

Setting Description Maximum Number of Login Attempts Allowed Before Account is Locked
Enter the number of user login attempts that are allowed before the user's account access is locked. Configuring a maximum number of login attempts protects against brute force login attacks. Default Time for Locked Account to Unlock
Enter the default time before a locked account is unlocked, in seconds. If a user enters the wrong password too many times and is locked out, the user's account is unlocked after this amount of time has passed. Number of Days of Inactivity Before Account is Deactivated
Enter the number of days that an account can be inactive before the account is deactivated. Number of Days Before Account Expires
Enter the number of days before an account expires. Time Interval Before User Can Reset Password Again (secs)
If a user resets their password, enter the amount of time, in seconds, that must pass before the user can reset their password again. Concurrent Login Policy
Select a concurrent login policy. A concurrent login allows a user to log in to a system using the same credentials but using different devices. Note that this field is supported in Versa Director Releases 22.1 and later.
- Allow—Allow concurrent logins.
- Deny—Do not allow concurrent logins.
- Force Logout—The active user is logged out before another user can log in with the same credentials.
Minimum Password Length Enter the minimum length of the password. Note that this field is supported in Versa Director Releases 22.1 and later. Require at Least One Uppercase Letter in Password
Click the slider bar to require at least one uppercase letter in a password. Require at Least One Lowercase Letter in Password
Click the slider bar to require at least one lowercase letter in a password. Require at Least One Number in Password
Click the slider bar to require at least one number in a password. Require at Least One Special Character in Password
Click the slider bar to require at least one special character in a password. Require User to Reset Password on First Login
Click the slider bar to require a user to reset their password when logging in for the first time. Prohibit Dictionary Words in Password
Click the slider bar to prohibit users from using dictionary words in their password. A password dictionary contains a list of words or characters that users may not use in their passwords. Note that this field is supported in Versa Director Releases 22.1 and later. Enable Password History
Click the slider bar to enable password history.
- Number of Passwords to Keep in Password History—Enter a number of passwords to keep in the password history (or use the up and down arrows) that the user is not allowed to reuse.
Expire Password
Click the slider bar to expire passwords.
- Number of Days Before Password Expires—Enter the number days before a password expires (or use the up and down arrows).
- Click Submit.
Map External User Roles in Concerto
For Releases 11.3.1 and later.
The external role-mapping feature allows you to map an external user's custom role to a local default Concerto role so that the external user can log in to Concerto successfully. You can map external users both at the service provider and tenent levels.
Role mapping is required in the following scenarios:;
- If a single sign-on (SSO) user role configured in an identity provider (IDP), such as Okta or Ping Identity, is a custom role (that is, a role that is not present in Concerto)
- If a user is created in Versa Director with a custom role
- If a user role configured in an external server (such as Active Directory, RADIUS, and TACACS+ servers) is a custom role (that is, a role that is not present in Concerto)
As an example, let's say that a custom user role, AcmeOperator, has been configured in an IDP. For the AcmeOperator user to login to Concerto successfully, you must map this role to a local default Concerto role, such as Enterprise Administrator or Enterprise Operator. Then, when AcmeOperator attempts to log in to Concerto, Concerto maps the AcmeOperator role to its Enterprise Administrator or Enterprise Operator role and allows AcmeOperator to log in to Concerto.
In Releases 11.4.1 and later, you can map the external custom role created in Versa Director, an IDP, or an external server to a local custom Concerto role and to a local default Concerto role.
To map an external user with a custom role to a local Concerto role:
- Go to Users lifecycle and click External Role Mapping.

- Click + External Role Mapping in the main screen.

- In the New Role Mapping screen, enter information for the following fields.

Field Description External Role Enter the name of the external role. Local Role Select the local Concerto role that to map to the external role. - Click Save.
The following example shows a list of external user roles and the local Concerto roles to which they are mapped.

Unlock a User Account
For Releases 10.2.1 and later.
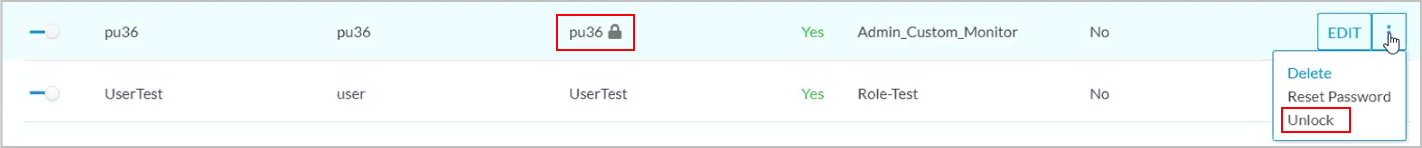
If a user account becomes locked, you can unlock the account from the Concerto Users lifecycle screen. In the following screen, user pu36 has been locked, as indicated by the lock icon. To unlock the user's account, click the More icon in the row for that user pu36 and select Unlock. The user account is unlocked.
Delete a User or Reset a User Password
You can delete a user or reset a user's password from both the Users lifecycle on the service provider home screen and the Users lifecycle within a tenant home screen.
To delete a user:
- Click the
 More icon in the row for that user on the Users lifecycle screen.
More icon in the row for that user on the Users lifecycle screen. - Click Delete and enter information as prompted.
To reset a user password:
- Click the
 More icon in the row for that user on the Users lifecycle screen.
More icon in the row for that user on the Users lifecycle screen. - Click Reset Password. The Reset Password screen displays.
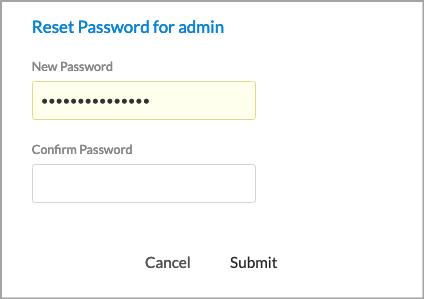
- Enter the new password and confirm the new password.
- Click Submit. If you reset a user password, the user is prompted to change their password the next time they attempt to log in. For more information, see Change Your Initial User Password.
Force a User Logout
For Releases 10.2.1 and later.
You can force an active user to be logged out of Concerto.
To perform a forced logout on an active user:
- Click the
 More icon in the row for that user on the Users lifecycle screen.
More icon in the row for that user on the Users lifecycle screen.
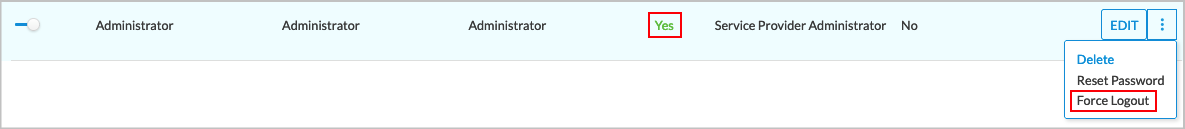
- Select Force Logout. The user is logged out immediately.
Change Your Initial User Password
For Releases 10.2.1 and later.
When you log in as a new user to Concerto for the first time, or if the administrator changes your password, you are prompted to change your password.
To change your password:
- Log in to Concerto using your configured password. The following screen displays, prompting you to change your password.

- Enter your current password, enter a new password, and confirm the new password by entering it again.
- Click Submit. The following screen displays, and you can now log in with your new password.

Reset a Forgotten Password
For Releases 10.2.1 and later.
If you forget your Concerto password, you can reset it:
- In the log in screen, click Forgot Password.
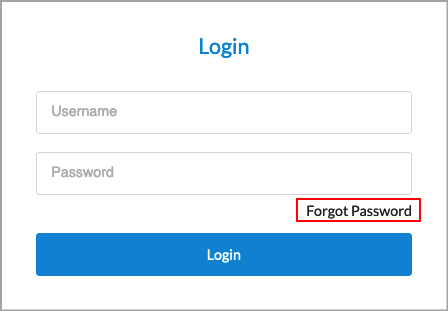
- In the next screen, enter your username and email address.

- Click Submit. You then receive an email with a temporary password.
- Enter the temporary password. You are then prompted to create a new password, as described in Change Your Initial User Password. After you reset your password, the following screen displays.

Edit User Information
- On the Users lifecycle screen, hover over a row and click the Edit box, or click a row to display the Edit User screen for that user.

- Select the General tab, and make the desired changes.

- Select the Settings tab, and make the desired changes.

- Click Save.
View Audit Logs
For Releases 11.4.1 and later.
Internal audit logs capture information about all activity on Concerto, including all internal URLs that were visited, the payloads for each request, the actions that occur as a result of the request, and all errors that were encountered. The logs are placed in the Concerto audit tables, and they are also sent to Versa Director.
You use audit logs to view activity history on Concerto and to perform debugging.
You view the audit logs in the Users lifecycle screen either at the system or tenant level. Note that to view the audit logs, you must be a Service Provider Administrator or an Enterprise Administrator.
To view audit logs:
- Go to the Users lifecycle, and then click Audit Log.
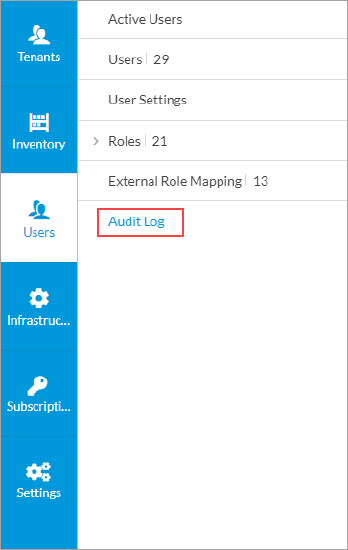
- The Audit Logs screen displays the audit log information.

- To view details for a log entry, click the
 Toggle Row Expanded icon next to the username. The log entry detail display. For example:
Toggle Row Expanded icon next to the username. The log entry detail display. For example:

Field Description Payload Displays the content of the request. To maintain user privacy, sensitive user information is replaced with asterisks (****). Trace ID Displays the trace ID associated with the request. When a user clicks a link in Concerto, Concerto generates a trace ID for the request. Operation Displays the action that was initiated by the request. Session ID Displays all the activity for a user during the session. Resource Group Displays the collection of resources that match the resource types specified in a query. Resource Displays all the audit logs for a user. HTTP Method Displays the HTTP method:
- DELETE
- GET
- HEAD
- PATCH
- POST
- PUT
Task Displays all the task details. This option displays in the audit log only after you publish the SD-WAN branch. View Diffs Displays the differences between last published configuration and the current published configuration. This option displays in the audit log only after you publish the SD-WAN branch. - To run audit log queries, click
 Show Filter Bar icon.
Show Filter Bar icon. - In the Action field, select an audit log actions. By default, audit logs show create, modify, and delete actions. To view read calls, select the Read action. To view the CLI commands that were issued, select the None action.
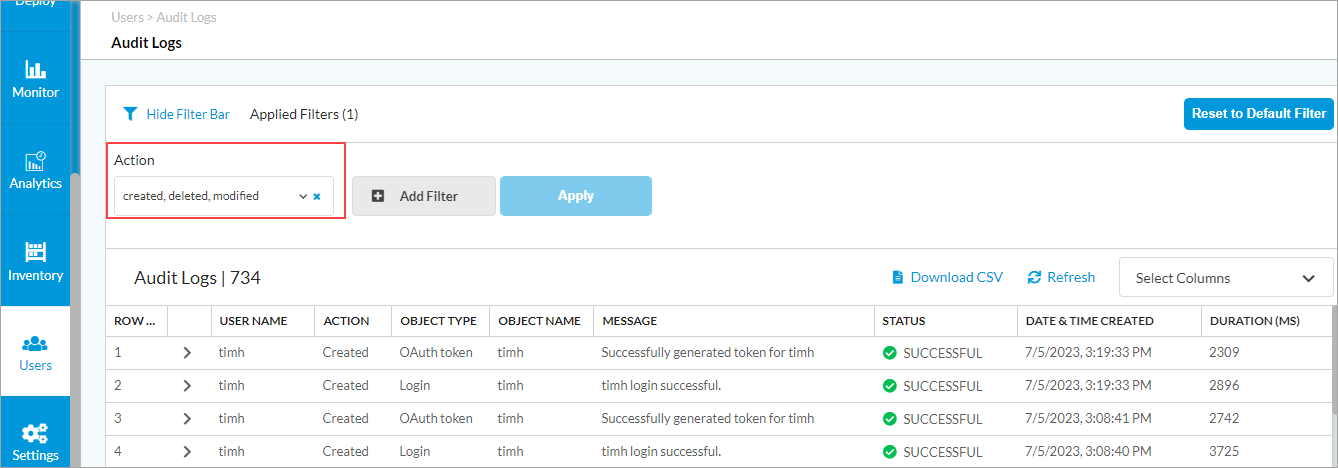
- Created—Select to view audit logs when a new user, tenant, profile, or rule was created and added in the database.
- Deleted—Select to view audit logs when an existing user, tenant, profile, or rule was deleted.
- Modified—Select to view audit logs when an existing user, tenant, profile, or rule was modified.
- Read—Select to view audit logs when existing content from database, such as visits to tenant, user page, and profile pages, was read.
- None—Select to view audit logs at the service provider level for CLI operations, such as upgrade and show commands.
- Click the
 Add Filter icon, and then select one of the following query types for filtering the log information.
Add Filter icon, and then select one of the following query types for filtering the log information.

Query Description Change Set Search on a string of characters in an error message. Select the string search type:
- Contains—Results contain the search string that you enter. This is the default.
- RegEx—Results match a regular expression that you enter.
Duration Search on the duration of the requests: - Seconds—Click to enter a search duration in seconds. This is the default.
- Milliseconds—Click to enter a search duration in milliseconds.
Object Name Search on an object name such as master profile, appliance, rule, element, profile, or subprofile name. Select the string search type:
- Contains—Results contain the search string that you enter. This is the default.
- Exact—Results contain the exact search string that you enter.
- RegEx—Results match a regular expression that you enter.
Object Type Search on an object type. Object Subtype Search on an object subtype. Object Subtype Category Search on an object subtype category. Operation Select the type of operation to query. Select the string search type:
- Contains—Results contain the search string that you enter. This is the default.
- Exact—Results contain the exact search string that you enter.
- RegEx—Results match a regular expression that you enter.
Payload Search on a string of characters in the payload. Select the string search type:
- Contains—Results contain the search string that you enter. This is the default.
- RegEx—Results match a regular expression that you enter.
Resource Search on the type of resource. Select the string search type:
- Contains—Returns results that contains search string. This is the default keyword.
- Regex—Returns results that matches regular expression search string.
Resource Group Search on the type of resource group. Select the string search type:
- Contains—Returns results that contains search string. This is the default keyword.
- Exact—Returns results that matched the exact search string.
- RegEx—Returns results that matches regular expression search string.
Date and Time Created Search on the date and time:
- Preset—Returns results within the 7 days or a week.
- Custom—Returns results within a custom start date and end date.
Status Select the status on which to query:
- Client Error
- Redirection
- Server Error
- Successful
Status Code - CLI Status Codes:
- 0—CLI exit code of 0 means that the CLI operation was successful.
- 1—CLI exit code of other than 0 means that the CLI operation was not successful.
- 126—CLI exit code of 126 means that a command was found but it is not executable.
- 127—CLI exit code of 127 means that a command was not found.
- HTTP Status Codes:
- 200—OK. The request succeeded.
- 201—Created. The request succeeded, and a new resource was created as a result.
- 204—No content. There is no content to send for this request, but the headers may be useful.
- 302—Found. The URI of requested resource was changed temporarily. Further changes in the URI may be made in the future.
- 400—Bad request. The server could not understand the request because of invalid syntax.
- 401—Unauthorized. The client must authenticate itself to receive the requested response.
- 403—Forbidden. The client does not have access rights to the content.
- 404—Not found. The server cannot find the requested resource.
- 405—Not acceptable. The web server, after performing server-driven content negotiation, found no content that conforms to the criteria given by the user agent.
- 500—Internal server error. The server encountered a situation that it does not know how to handle.
Tenant Name Select the tenant name. Trace ID Enter an exact trace ID on which to query.
Session ID Enter an exact session ID on which to query. Username Select the username on which to query. Select the string search type:
- Contains—Returns results that contains search string. This is the default keyword.
- Exact—Returns results that matched the exact search string.
- RegEx—Returns results that matches regular expression search string.
- To restore the default filters, click Apply. Click Reset to Default Filter.

Download Audit Logs in CSV Format
For Releases 11.4.1 and later.
- In the Audit Logs screen, click the
 Download CSV icon.
Download CSV icon. - In the Download Audit List popup window, enter values for the starting and ending rows. You can download a maximum of 5000 logs at a time.

- Click Download.
Supported Software Information
Releases 10.1.1 and later support all content described in this article, except:
- Release 10.2.1 adds the Active column in the Users screen; adds support for the unlocking users from Concerto, changing passwords, resetting forgotten passwords, forcing user logout, and discovering appliances created in Versa Director; adds support for two-factor authentication.
- Release 11.3.1 adds support for mapping an external user role to a local Concerto role.
- Release 11.4.1 adds support for audit logs; adds the User Settings screen; adds support for mapping external custom roles to local Concerto custom roles.
Additional Information
Concerto Home Screen Overview
Configure Single Sign-On Using Director
Configure User Account Settings
