Versa Secure SD-WAN Licensing Overview (2025)
This article describes Versa Secure SD-WAN subscription licenses from the year 2025.
Versa Secure SD-WAN 2025 Licensing Overview
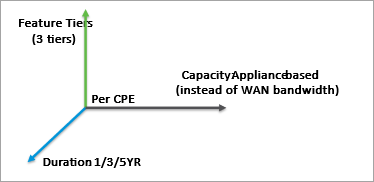
Versa Secure SD-WAN licensing has three-dimensions: solution tier, appliance model and subscription duration. There are three solution tiers, each associated with a set of features. Subscription durations are one, three, and five years, with an upfront payment model.
Each customer premises equipment (CPE) deployed in your network must be associated with a software subscription license. This includes each CPE deployed in high availability (HA) or active-standby configurations.
This model of subscription, based on device model number instead of WAN bandwidth, provides the following benefits:
- Provides more flexibility
- Groups devices as classes based on capacity and feature-set for pricing purposes
- SKU clearly spells out actual device name
Solution Tiers
The Versa Secure SD-WAN product offering comes with integrated routing, SD-WAN and next-generation firewall (NGFW) features to provide effective WAN edge coverage options. Versa Secure SD-WAN features are grouped into solution tiers to align with popular deployment scenarios. Solution tiers provide comprehensive coverage for these scenarios, along with ease of purchase, ease of deployment and cohesive value at each tier:
- Essential—Provides robust set of platform features, carrier class routing and switching, along with core features of SD-WAN plus NGFW (L4-7 class security features).
- Professional—Adds advanced SD-WAN features built to optimize user application experience.
- Elite—Adds unified threat management (UTM) features on top of the Professional tier features to provide comprehensive security coverage and eliminates the need to deploy a separate firewall appliance.
The feature set for each tier is described below.
Essential Tier Features
The Essential solution tier provides the following features:
- Platform level features:
- Ethernet and select non-Ethernet interfaces with associated encapsulation options
- Support for wired and wireless interfaces (LTE, 5G, WiFi)
- Comprehensive set of Layer-2 switching or bridging on LAN and on WAN interfaces of WAN Edge devices
- IPv4, IPv6, unicast and multicast support
- Quality of service (QoS), including hiearchical quality of service (HQoS) and more
- Multitenancy across each feature or capability
- uCPE to host and service chain third-party VMs
- Carrier class routing protocols and their extensions for multicast and IPv6
- DHCP client, server, relay
- Zero-touch provisioning (ZTP)
- Core SD-WAN functions
- Secure, dynamic, and encrypted VPN overlays
- Application identification or detection and visibility
- Application traffic management (by policy)
- Application QoS
- SLA-based path measurement
- L4-7 security features:
- Stateful firewall
- DOS protection
- CGNAT with ALG support
- IKEv2 IPsec
- URL reputation feeds, classification, and filtering
- IP reputation feeds, classification, and filtering
- SSL-TLS proxy (including TLS1.3) to break HTTPS sessions for captive portal purposes
- Captive portal
- DNS proxy, DNS reputation feeds and filtering
Professional Tier Features
The Professional solution tier adds the following features in addition to those in the Essential tier:
- Voice, video, and unified collaboration CODECs to measure user experience and grading by MOS metrics
- Automated MOS-score based traffic management
- Forward error correction (FEC), packet cloning to minimize retransmissions and to accelerate application experience across lossy links
- Packet striping to treat a bunch of links as one fat pipe
- Direct internet access (DIA) and direct cloud access (DCA) traffic optimizations
- Distributed traffic engineering based on Traffic Engineered Link State (TELS) protocol
- TCP optimization
- Tunnelless SD-WAN deployments targeting satellite-based WAN links and more
- IoT device identification, classification, and device-class based actions
Elite Tier Features
The Elite solution tier adds the following UTM features in addition to those in the Professional tier:
- Full scope of TLS proxy for scanning
- File reputation feeds and filtering
- Intrusion prevention system (IPS)
- Antivirus and malware protection
- Versa cloud-delivered advanced logging service (ALS) at a certain capacity (60 GB per CPE with Elite tier)
License Capacity
In the license models before the year 2025, Versa Secure SD-WAN capacity was based on WAN bandwidth. With the 2025 licensing model, Versa Secure SD-WAN license is based on device capacity. With this new model, Versa provides usage capacity flexibility to use up to the maximum capacity a device supports, regardless of whether the licensed WAN bandwidth is used or not. This avoids potential overuse charges and the need for monitoring and accounting for used WAN bandwidth versus purchased WAN bandwidth.
To select the appropriate CPE devices, see the platform datasheets located on the Versa website.
License Duration
Versa Secure SD-WAN is available in one (1) year, three (3) year, and five (5) year subscription license terms.
Versa Orchestration Suite
Versa Networks provides a comprehensive suite of management, analytics, orchestration, monitoring, and controller capabilities through the Versa Orchestration layer. The Versa Orchestration suite consists of the following components:
- Versa Concerto
- Versa Director
- Versa Analytics
- Versa Controller
- Versa Messaging Service
Every orchestration component and Versa Operating SystemTM (VOSTM) instance has multitenant and granular RBAC capabilities. Among the orchestration components, Versa Director, Versa Controller, and Versa Analytics are minimum requirements, while Versa Concerto and Versa Messaging Server are recommended components.
The 2025 Versa Secure SD-WAN license includes Versa cloud-based orchestration (right to use, or RTU). This allows you to use Versa Networks' always available, backed-up and maintained multitenant orchestration to facilitate quick deployment and management of your secure SD-WAN CPEs with no setup delay or hurdles. Versa cloud-based orchestration eliminates the need to deploy Versa orchestration on-premises, providing RTU for the duration of the subscription. Additionally, Versa Networks still provides the flexibility to deploy Versa Orchestration on-premises or on a dedicated cloud instance for additional fees.
On-Premises Orchestration
You can deploy Versa Orchestration on-premises for data sovereignty, specific regulatory, or other reasons. If you purchase the on-premises option, you or your partners must first download software images from Versa software repositories and install them on your environment based on the procedures described in Versa documentation. After installation, you must install an appropriate license file on Versa Director to activate the on-premises orchestration setup.
To request the license key, contact Versa TAC team. For more information about on-premises Versa Orchestration suite installation, see the Versa documentation at https://docs.versa-networks.com.
The Versa Orchestration on-premises license option is sold in different setup sizes to address all deployment requirements. Each of these allows you to manage up to a specific number of CPEs. The following sizes are available: 250, 1000, 2500, 4000, 5000, 10000, 15000 and 20000 CPEs.
The on-premises orchestration SKU of 1000 capacity entitles the customer to manage up to 1000 CPEs with that orchestration instance. Note that Secure SD-WAN (or Secure SD-LAN or NGFW) licenses are separate from the on-premises orchestration licenses. The on-premises orchestration license with specific capacity can be a superset of the actual number of Secure SD-WAN CPE licenses that you purchase. In such cases, you are entitled to deploy SD-WAN CPEs based on the number of CPE software subscription licenses purchased, and not based on orchestration capacity.
As an example scenario, you buy on-premises orchestration license to manage up to 1000 CPEs. You currently have plans to deploy 742 CPEs, so you purchased 742 Secure SD-WAN subscription licenses. You are now entitled to deploy only 742 Secure SD-WAN CPEs using on-premises orchestration software. On request, the Versa TAC team can provide you with an SD-WAN license key for 742 CPEs to activate these devices. Subsequently, you can purchase an additional 258 instances of Secure SD-WAN licenses to be managed by the same orchestration without paying extra for the orchestration suite.
Dedicated Cloud-Hosted Orchestration
Versa Networks offers the option of a dedicated cloud-hosted orchestration as a SaaS service. This provides the flexibility to run your own software version, independent software upgrade timelines, maintenance windows, cloud orchestration locations, and have no dependencies on other Versa Networks customers.
The dedicated cloud-hosted orchestration SaaS service includes instantiation of the Versa Orchestration suite on one or more Versa cloud instances, with high availability, by Versa Networks personnel. This option includes monitoring and maintenance by the Versa Managed Services team. For more details, including SLAs, see the Versa Networks Hosted and Managed Head-End (VHM) datasheet.
The dedicated cloud-hosted orchestration SaaS service is offered at capacities of 500, 1000, 2500, 4000, 5000, 10,000, 15000, and 20,000 CPEs. When you purchase a particular capacity and geography-based, cloud-hosted orchestration suite, the Versa Managed Services team will instantiate and provide access to the SaaS service.
The multitenant Versa cloud-based orchestration stack, as well as the dedicated orchestration stack for a customer, are set up in full redundancy. This is to ensure maximum uptime and serviceability with minimal to no service interruption.
Note that Secure SD-WAN (or Secure SD-LAN or NGFW) licenses are separate from the dedicated cloud-hosted orchestration SaaS service (capacity) license, and the actual number of Secure SD-WAN CPEs you are entitled to deploy is determined by the number of CPE software subscription licenses that you purchase.
Selection of Versa Secure SD-WAN CPE Licenses
As the first step, Versa Networks recommends that our customers or partners finalize the choice for CPE devices. If scaling or performance capacity is expected to grow, we recommend that you anticipate your needs for the future. After you select the hardware device, it is easy to choose the software license for that CPE.
2025 Versa Secure SD-WAN SKUs
2025 Versa Secure SD-WAN SKUs are structured to be intuitive and easy to follow. For example:
- SDW-PRO-CSG150-3YR-S—Versa Secure SD-WAN Professional 3-year subscription for CSG150, which includes software support and RTU for Versa Cloud-based multitenant orchestration.
- SDW-ESS-CSG750-1YR-D—Versa Secure SD-WAN Essential 1-year subscription for CSG750, which includes software support. Managed by Versa cloud-based dedicated orchestration, requiring dedicated cloud-hosted orchestration purchase via an additional license.
- SDW-ELT-CSG2500-5YR-O—Versa Secure SD-WAN Elite 5-year subscription for CSG2500, which includes software support. Managed by on-premises-based Versa orchestration, requiring on-premises-based orchestration purchase via an additional license.
Note that the last suffix varies based on the orchestration type. For example:
- “-S” is for included Versa Cloud-based orchestration.
- “-D” is for the optional dedicated Versa cloud-hosted orchestration, which also requires purchase of that orchestration option.
- “-O” is for optional on-premises-based orchestration, which also requires purchase of that orchestration option.
For more information about SKUs, see the associated 2025 Versa Secure SD-WAN Pricing and SKUs document.
Add-on Options for Versa Secure SD-WAN
Versa Secure SD-WAN add-on options allow you to subscribe to specific features that are not included in the chosen license solution tier. The add-on license is also based on appliance. A base SD-WAN license is a prerequisite for subscribing to an add-on license. The following table lists the add-on options and their applicability for each tier:
| Add-On Options | Essential | Professional | Elite |
|---|---|---|---|
| Versa Advanced Network Insights (VANI) | Add-on | Add-on | Add-on |
| On-premises zero-trust network access (ZTNA) | Add-on | Add-on | Add-on |
| Identity engine | Add-on | Add-on | Add-on |
| Advanced logging service (ALS) | Add-on | Add-on | Included |
| XoT fingerprinting and security | Add-on | Included | Included |
| Data protection (inline CASB and DLP) | NA | NA | Add-on |
| Cloud-based ATP sandboxing | NA | NA | Add-on |
Data Protection Add-On Option
The data protection add-on option provides inline CASB and inline data leakage prevention (DLP) capabilities. Inline DLP provides real-time protection against data leakage outside of the enterprise perimeter. It protects you from erroneously or maliciously exfiltrating enterprise data to third-party destinations.
Inline DLP provides the following features:
- Detects confidential files being uploaded to internet-based applications or external servers. Works with Microsoft Information Protection (MIP) to detect confidentiality of files and block the channel.
- Detects patterns (for example, credit card numbers, SSN, and patient information) and blocks the channel.
- Contains pre-defined policies matching your regulatory domain (for example, PCI-DSS, HIPAA).
Inline CASB enables control and visibility of user actions within internet-based applications. For example, administrators can analyze user actions (for example, likes, comments, uploads) on social media applications and can enforce rules to protect data from being exfiltrated either maliciously or due to user error. For example, you can define a rule that an engineering user cannot comment on social media, but marketing users can comment and upload but cannot “like” content.
Inline CASB provides real time visibility, classification, and access control of SaaS-based applications. Many enterprises face the challenge of users enrolling third-party applications without the visibility or knowledge of the IT department. These applications are called unsanctioned applications, and such unauthorized or unapproved applications can cause data leakage, violation of company policies, violation of company compliance, and can act as sources that spread malicious content or code. Therefore, IT departments require reliable methods to discover and classify SaaS applications to identify such applications and users to control the usage of unsanctioned applications. Inline CASB plays a key role in achieving this goal.
Together, inline CASB and inline DLP provide SaaS-based application discovery, access control, and data leakage prevention, ultimately securing enterprises on cloud-based applications and data repository usage.
On-premises ZTNA Add-On Option
The zero trust framework secures the network by not trusting any user or device. Today, most networks use Network Access Control (NAC) to admit users and devices to an enterprise network. In this scenario, it is assumed that if the user is an authorized enterprise user, it is a trusted user, which need not be a valid assumption in many circumstances. A corporate user with valid credentials may end up being the method of delivering malware without knowledge of the user due to poor or degraded posture of the device.
After using cloud-delivered ZTNA solutions, enterprise IT administrators now demand on-premises-based ZTNA solutions. The on-premises ZTNA add-on option for decouples the right to access the network from right to access applications. It uses multiple factors such as user authentication, user behavior, device posture, and device ID to make decisions to grant access to the network or to network segment for specific applications and/or specific micro-segments.
As conditions change, IT administrators require the capability to automatically adapt to conditions, such as the security posture degrading or improving, and to automatically apply policy enforcement, segmentation or micro-segmentation actions. Effectively, the on-premises ZTNA add-on option provides ZTNA to users connected to the enterprise network while the policy enforcement point is the SD-WAN router.
XoT Device Fingerprinting and Classification Add-On Option
Devices with a wide variety of computing capabilities and device complexity connect to enterprise networks. Enterprise administrators do not always have complete knowledge of the devices connected to their network, their capabilities, and potential weaknesses of these devices. A device with known vulnerabilities can provide attackers with a launchpad for bigger attacks on the network. Though there are several tools available to maintain an inventory of devices, many of these tools are not dynamic and require manual intervention to add new devices. The exponential increase of devices requires automated mechanisms to detect and catalog devices.
XoT device fingerprinting automatically detects any device that is active on the network. It detects details of a device, such as the device manufacturer, firmware version, and open CVEs associated with the device. This allows enterprise administrators to take appropriate actions, such as quarantining a device using the on-premise ZT-LAN solution.
Advanced Threat Protection and Sandboxing Add-On Option
Malicious actors frequently stage zero-day attacks against high value targets. They exploit vulnerabilities that are not widely known or announced publicly. Signature-based intrusion prevention solutions used by traditional firewalls cannot detect and block these threats. Advanced threat protection (ATP) secures an enterprise against such threats.
ATP uses multi-stage scanning of threats to evaluate threat levels:
- Static analysis—Uses a multi-antivirus engine to scan files using different virus definition files. At this stage, even if a single antivirus vendor recognizes the threat, it gets blocked.
- AI/ML engine—Uses more than 200 data points that are indicators of exploit, which detects obfuscated files that typically pass through signature-based detection.
- Sandboxing—Deploys the file in a VM and observes the behavior of the file, for example, registry accesses and system calls.
If a threat is detected in any of these stages, the administrator is notified of the attempt and communication to the threat actors is shut down to protect the enterprise.
Stateful HA Cluster Add-On Option
Versa Networks provides stateful HA synchronization capabilities across active-standby clusters. The stateful HA cluster synchronizes long-lived flows from the active node to the standby node. The prerequisite for stateful HA synchronization is that any tier must include NGFW or UTM capabilities, including secure SD-WAN tiers. Bandwidth capacity must match the bandwidth capacity of the underlying SKU on a device.
Advanced Logging Service
As new sophisticated threats emerge, identifying, stopping, and remediating such threats is top priority for security administrators. You can evaluate the scope and seriousness of threats by analyzing the network events occurring at the time of the event. Advanced logging service (ALS) is a SaaS offering that you can integrate with your SD-WAN headend (both on-premises or Versa-hosted) to provide a scalable solution to store and efficiently retrieve network logs. ALS is a big-data based system optimized to search, filter, and retrieve logs of interest and provide them instantaneously to your security team for further analysis.
You can subscribe to ALS on the basis of the amount of logs that you store in the service in multiples of 1 TB (terabyte). The log storage required for the logs and the SKU depends on the number of logs stored in the service and the duration for which they are stored. For example, for 100 GB of logs generated each day with 30 days of storage requirement, 3 TB of ALS subscription is required. While the size of the log varies based on types of data stored, one log consumes approximately 1600 bytes of storage.
You subscribe to ALS on a geographic region basis. For example, if you need 5 TB in North America and 3 TB is APAC (Sydney), then you need to subscribe to 2 SKUs, one for 5TB and another for 3 TB of ALS.
