SD-WAN–SSE Hub Integration
This article describes how to integrate the Versa cloud-hosted Secure Service Edge (SSE) provided by Versa Concerto into an existing on-premises Versa Director SD-WAN deployment to create a unified SD-WAN–SSE solution, also called a SASE solution. Two commonly architectures for a united SD-WAN–SSE solution are the SD-WAN SSE hub interconnect architecture and the branch SSE tunnel architecture.
The SD-WAN–SSE hub interconnect architecture, illustrated in the following figure, leverages the SD-WAN SSE hubs that are already deployed in the customer SD-WAN environment. This architecture extends the on-premises, Director-managed SD-WAN to the Versa cloud-hosted SSE environment. It uses SSE hub deployments that are close to or colocated with Versa-hosts cloud gateways. The Versa-hosted cloud gateway connects to the SSE hub using GRE or IPsec tunnels, which allows for secure and scalable user internet access and for work-from-anywhere (WFA) access to customer-hosted applications

The branch SSE tunnel architecture, which is illustrated in the following figure, leverages GRE and IPsec tunnel connectivity between the Versa-hosted cloud Gateway and on-premises SD-WAN branches to provide secure user internet access and WFA access to customer hosted applications. Tunnels are configured for each SD-WAN branch as required by Versa Secure Private Access (VSPA) and Versa Secure Internet Access (VSIA).

This article describes the SD-WAN SSE hub interconnect architecture, providing examples of how to provision the necessary components and software.For information about the branch SSE tunnel architecture, see Versa Secure SD-WAN Integration with SSE.
Customer SD-WAN–SSE Hub Deployment Overview
In the SD-WAN–SSE hub interconnect architecture, the customer SD-WAN is extended by leveraging SSE hub deployments that are close to or colocated with Versa SSE cloud gateways. The following are some of the advantages by extending an SD-WAN network to SSE cloud gateways:
- Full SD-WAN feature set, including multitenancy, load balancing, SLA-based traffic steering, SLA aggressive monitoring, forward error correction (FEC), class of service/quality of service (CoS/QoS), adaptive shaping, and workflow templates
- Common SD-WAN control and forwarding (data) planes between customer-managed SSE hubs and the customer's data center and branch locations
- Simplified traffic paths based on SD-WAN spoke groups and regions.
- Leverages standard SD-WAN data center and branch high-availability (HA) connectivity
- Can be used with both Versa Secure Private Access (VSPA), which connects an organization's employees working from anywhere to enterprise applications hosted in the enterprise environment, private clouds, or public clouds, and with Versa Secure Internet Access (VSIA), which provides protection for all traffic bound for the internet and SaaS bound traffic.
- Horizontally scalable.
- Minimizes architectural and configuration complexity.

This section provides an overview of the components required for configuring SD-WAN SSE hub interconnection:
- Connectivity between the Versa Cloud Gateway (VCG) and the customer hub
- Site-to-site tunnels and the configuration of BGP AS numbers
- Dynamic routing and traffic flow
- Versa secure access, either private access (VSPA) or internet access (VSIA)
Connectivity between the VCG and the Customer Hub
To facilitate connectivity between SSE and the SD-WAN, you configure redundant site-to-site IPsec tunnels and EBGP between the VCG enterprise LAN-VR and the SD-WAN SSE hub customer LAN-VR, as illustrated in the following figure. You configure VCGs using the Versa Concerto GUI, and you configure the SD-WAN SSE hubs using the GUI on the on-premises Director node.

You deploy a minimum of two customer SSE hubs per region, using full-mesh IPsec site-to-site tunnels and EBGP dynamic routing to connect to the regional VCGs. For SSE-to-SD-WAN connectivity, you can use either an active–standby or active–active traffic path model. By default, Layer 3 symmetric forwarding is enabled on Versa Cloud Gateways.
You use customer SD-WAN spoke groups to leverage SSE hubs. The prefixes learned from the VCGs are redistributed to the relevant LAN-Export VR of SSE hubs, allowing for simplified configuration of the SD-WAN traffic path.
For the active–standby traffic path model:
- Customer leverages EBGP metrics to establish the traffic path.
- VCGs are configured with the following:
- Export policies for advertisements towards the customer SSE hubs. For export policies for the configuration example in this article, the local AS number of the active device is prepended once, and for the standby the local AS number is prepended twice.
- Import policies for advertisements received from customer SSE hubs. In this example, the local AS number of the active device is prepended once, and for the standby it is prepended twice.
- BGP communities are marked on all inbound and outbound prefixes. You can use communities for traffic path engineering and loop prevention.
For the active–active traffic path model:
- Customer leverages equal-cost EBGP metrics to establish traffic paths.
- As mentioned previously, Layer 3 symmetric forwarding is enabled by default on VCGs.
For more information about the active–standby and active–active traffic path models, see Versa Secure Private Access and Versa Secure Internet Access, below.
Site-To-Site Tunnel Configuration and BGP ASN Assignment
The customer manages and configures IP address assignment for the VCP and the customer SD-WAN hub IP address assignment, as illustrated in the following figure.

The VCG (Concerto) IPsec TVI interface numbering is configured by default when you configure site-to-site tunnels.
The customer configures the SD-WAN SSE hub (Director) IPSec TVI interface numbering. It is recommended that you use TVI interface numbering that does not conflict with workflow-generated TVI interfaces. For example, use tvi-15/number, where tvi-15/1999 is the highest acceptable interface number.
TVI IP addresses on both the VCG (Concerto) and SD-WAN SSE hub (Director) are assigned from the customer-managed IP address space. Versa TVI interfaces support the /31 subnet mask length. Do not use the IP address space 169.254.0.0/16, because it may conflict with the workflow-generated configuration.
The customer configures IKE and IPsec parameters. Versa Networks supports IKEv1 and IKEv2. The Concerto and Director GUIs list additional parameters.
The customer configures EBGP between the necessary LAN-VRs, leveraging customer-assigned tunnel IP neighbor addresses and customer-assigned BGP AS numbers.
Customer-specific BGP attributes are configured on both the VCG (Concerto) and SD-WAN SSE hub (Director), as required.
Dynamic Routing Configuration and Traffic Flow
You use dynamic routing, configuring EBGP between VCGs and customer SSE hubs. You configure EBGP peering between the TVI IP addresses. You can use either the active–standby and the active–active traffic path model.
The configurations for the VCGs (on Concerto) and the customer SSE hubs (on Director) are customer managed. Customers can configure these environments to meet their requirements. The configuration sections at the end of this article provide detailed examples of configurations that customers can use.
Versa Secure Private Access (VSPA)
VSPA is a software-defined, cloud-managed, cloud-delivered, private access service that efficiently connects enterprise WFA users with distributed private applications without compromising security or user experience. You can configure the connectivity between VCGs and customer SSE hubs using either the active–standby and the active–active traffic path model.
VSPA with the Active–Standby Traffic Model
In the active–standby traffic path model, you configure an active traffic path and a standby traffic path on each VCG and customer SSE hub. The following figure shows the configuration required on the VCGs to facilitate a designated traffic path configuration control point. As mentioned previously, the customer manages the VCG and customer SSE hub configurations, and they create configuration to meet their specific requirements.


You can find example configuration corresponding to these figures in Configure VSPA, below. In the example configuration, Community C is configured as follows to provide a loop prevention mechanism:
- VCG export policy is applied to the active traffic path (SSE VCG-A: A1 and SSE VCG-B: B1).
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- VSPA user prefixes (VSPA-A and VSPA-B) are matched, prepended once, marked with community C, and accepted (that is, advertised) for traffic destined to customer SSE hubs.
- VCG export policy is applied to the standby traffic path (SSE VCG-A: A2 and SSE VCG-B: B2).
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- VSPA user prefixes (VSPA-A and VSPA-B) are matched, prepended twice, marked with community C, and accepted (that is, advertised (accept) destined to customer SSE hubs.
- VCG import policy is applied to the active traffic path (SSE VCG-A: A3 and SSE VCG-B: B3).
- Community C is matched and rejected.
- All other prefixes advertised by the customer SSE hub advertised are prepended once, marked with community C and with community 64513:64513, which is the default Versa DIA community, and accepted.
- VCG import policy applied to the standby traffic path (SSE VCG-A: A4 and SSE VCG-B: B4).
- Community C is matched and rejected.
- All other prefixes advertised by the customer SSE hub are prepended twice, marked with community C and with community 64513:64513, and accepted.
The following figure shows the active–standby steady-state traffic flow for VSPA.

If the active traffic path fails, the standby traffic path is used for connectivity. The following figure illustrates the failure of the active traffic path between SSE VCG-A and customer SSE Hub CPE-A. The identical traffic path failover would occur if the active traffic path between SSE VGC-A and SSE hub CPE-B were to fail.

VSPA with the Active–Active Traffic Model
In the active–active traffic path model, you configure each VCG and customer SSE hub with two redundant active traffic paths. In the example configuration described later in this article, you perform the configuration on the VCGs to facilitate a control point for the designated traffic path configuration. As mentioned previously, the customer manages the VCG and customer SSE hub configurations, and they create configurations to meet their specific requirements.


You can find example configuration corresponding to these figures in Configure VSPA, below. In the example configuration, Community C is configured as follows to provide a loop prevention mechanism:
- VCG export policy is applied to active–active traffic paths.
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- VSPA user prefixes (VSPA-A and VSPA-B) are matched, marked with community C, and accepted (that is, advertised) for traffic destined to customer SSE hubs.
- VCG import policy is applied to active traffic paths.
- Community C is matched and rejected.
- All other prefixes advertised by the customer SSE hub are marked with community C and with community 64513:64513, which is the default Versa DIA community, and accepted.
The following figure shows the active–active steady-state traffic flow.

If either of the active traffic path fails, the other active traffic path is used for connectivity. The following figure illustrates the failure of the active traffic path between SSE VCG-A and customer SSE Hub CPE-A.

Versa Secure Internet Access (VSIA)
VSIA is a Versa cloud-managed service that helps secure enterprise sites, home offices, and traveling users who are accessing distributed applications without compromising either security and the user experience. For VSIA, you can configure connectivity between VCG and customer SSE hubs for both the active–standby and active–active traffic path models.
The Versa client extends SD-WAN to client devices and provides configuration flexibility to ensure the best application and internet experience to WFA customers. This article does not include the Versa client configuration.
VSIA with the Active–Standby Traffic Model
In the active–standby traffic path model, which is illustrated in the following figures, you configure each VCG and customer SSE hub with an active traffic path and a standby traffic path. For the example discussed later in this article, you perform that configuration on the VCGs to facilitate a designated traffic path configuration control point. As mentioned previously, the customer manages the VCG and customer SSE hub configurations, and they create configurations to meet their specific requirements.
The example discussed in this article uses dynamic routing, specifically, EBGP. You can use static routing instead of of dynamic routing. For the static routing active–standby model, you configure the SSE hub static routes to prefer the static default route towards the active VCG. You configure IP SLA or SaaS monitors (for example, to monitor the VCG next hop, internet-based DNS server, and specific SaaS application), and you assign them to default routes to support failover. Layer 3 symmetric forwarding is configured by default on VCGs to ensure traffic path symmetry.


You can find example configuration corresponding to these figures in Configure VSIA, below. In the example configuration, Community C is configured as follows to provide a loop prevention mechanism:
- VCG export policy is applied to the active traffic path (SSE VCG-A: A1 and SSE VCG-B: B1).
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- The default route is matched, prepended once, marked with community C, and accepted (that is, advertised) for traffic destined to customer SSE hubs.
- VCG export policy is applied to the standby traffic path (SSE VCG-A: A2 and SSE VCG-B: B2).
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- The default route is matched, prepended twice, marked with community C, and accepted (that is, advertised) for traffic destined to customer SSE hubs.
- VCG import policy is applied to the active traffic path (SSE VCG-A: A3 and SSE VCG-B: B3).
- Community C is matched and rejected.
- All other customer prefixes advertised by the SSE hub are prepended once, marked with community C and with community 64513:64113, which is the default Versa DIA community, and accepted.
- VCG import policy applied to the standby traffic path (SSE VCG-A: A4 and SSE VCG-B: B4).
- Community C is matched and rejected.
- All other prefixes advertised by the customer SSE hub are prepended twice, marked with community C and with community 64513:64113, and accepted.
The following figure shows the active–standby steady-state traffic flow for VSIA.

If the active traffic path fails, the standby traffic path is used for connectivity. The following figure illustrates the failure of the active traffic path between SSE VCG-A and customer SSE Hub CPE-A. The identical traffic path failover would occur if the active traffic path between SSE VGC-A and SSE hub CPE-B were to fail.

VSIA with the Active–Active Traffic Model
In the active–active model, you configure each VCG and customer SSE hub with two redundant active traffic paths. In the example configuration described later in this article, you perform the configuration on the VCGs to facilitate a control point for the designated traffic path configuration. As mentioned previously, the customer manages the VCG and customer SSE hub configurations, and they create configurations to meet their specific requirements.
The example discussed in this article uses dynamic routing, specifically, EBGP. You can use static routing instead of of dynamic routing. For the static routing active–standby model, you configure the SSE hub static routes to prefer the static default route towards the active VCG. You configure IP SLA or SaaS monitors (for example, to monitor the VCG next hop, internet-based DNS server, and specific SaaS application), and you assign them to default routes to support failover. Layer 3 symmetric forwarding is configured by default on VCGs to ensure traffic path symmetry.


You can find example configuration corresponding to these figures in Configure VSIA, below. In the example configuration, Community C is configured as follows to provide a loop prevention mechanism:
- VCG export policy is applied to the active–active traffic paths.
- Community C is matched and is rejected (that is, not advertised) for traffic destined to customer SSE hubs.
- The default route is matched, marked with community C, and accepted (that is, advertised) for traffic destined to customer SSE hubs.
- VCG import policy is applied to active traffic paths.
- Community C is matched and rejected.
- All other customer SSE hub advertised prefixes are marked with community C and with community 64513:64513, which is the default Versa DIA community, and accepted.
The following figure shows the active–active steady-state traffic flow for VSIA.

If either of the active traffic path fails, the other active traffic path is used for connectivity. The following figure illustrates the failure of the active traffic path between SSE VCG-A and customer SSE Hub CPE-A.

Configure VSPA
This section provides a VSPA configuration example for the active–standby traffic path model. For this configuration, you do the following:
- On Versa Concerto, configure BGP peering policies.
- On Versa Concerto, configure site-to-site tunnels.
- On Versa Director, configure the SSE hub devices. For these devices, you configure tunnel (TVI) interfaces, VPN profiles, BGP, and route redistribution policies.
If you want to configure the active–active traffic path model instead, the configuration is similar, but you apply the primary BGP peering policies to both tunnel interfaces. Also, you must configure symmetric forwarding on the branches in the customer SD-WAN environment.
Configure BGP Peering Policies Using Versa Concerto
On Versa Concerto, you configure BGP peering policies. You configure export policies to filter the advertisements that are sent to customer SSE hubs and import policies to filter the advertisements that are received from the customer SSE hubs.
To configure the BGP peering policies:
- Log in to Versa Concerto.
- Go to Configure > Secure Services Edge > Settings, and then click BGP Peer Policies.

- Click + Add Policy Term. The Add BGP Peer Policy screen displays.
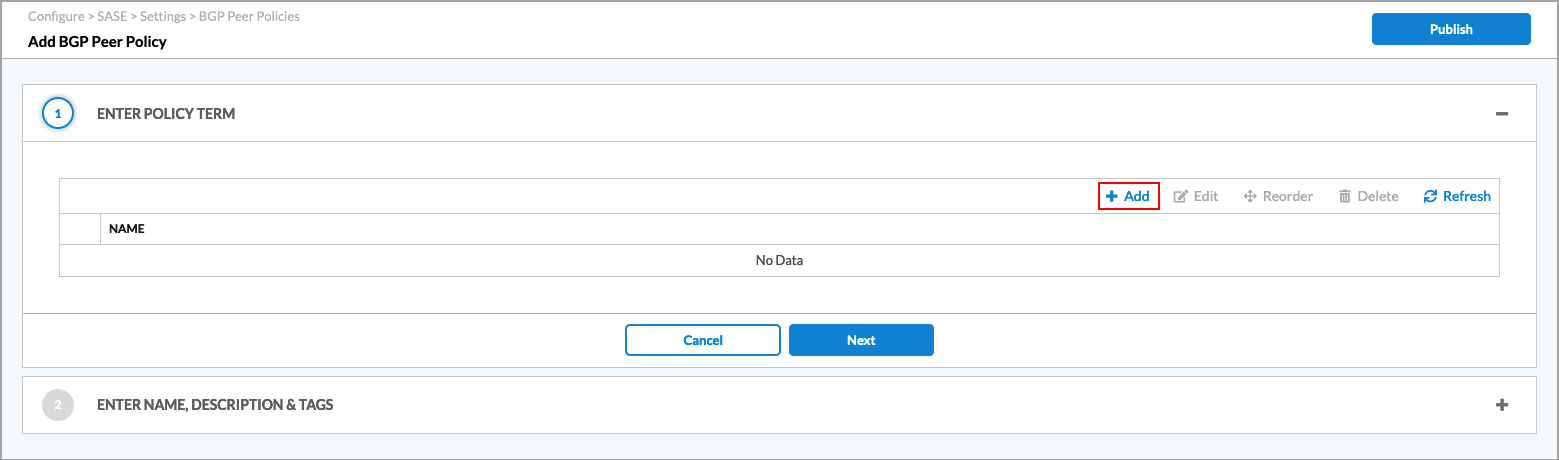
From this screen, you configure the import and export policies.
Configure an Export Policy
You configure one export policy (here, called To-SSE-Hub-Primary) that contains two policy terms, one for Community C (here, called VCG-SSE_Hub-Community) and the second for local client prefixes (here, called Local-Client-Prefixes). This export policy applies for advertisements towards customer SSE hubs.
To configure the export policy:
- Click + Add under Enter Policy Term. The Add Policy Term screen displays.
- Configure an export policy term for Community C:
- Click Criteria.

- In the Community field, enter the community string to match, here, 1000:1000.
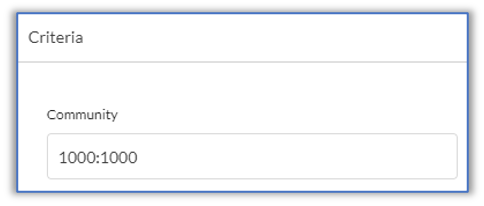
- Click Action.

- In the Action field, select Reject.

- Click General Information.

- Enter a name for the Policy Term, here, VCG-SSE_Hub-Community. Optionally, enter a description for the policy term.

- Click Save.
- Click Criteria.
- In the Add BGP Peer Policy screen, click + Add under Enter Policy Term again, to configure a second policy term for local client prefixes. The Add Policy Term screen displays.
- Click Criteria.
- In the NLRI field, enter the IP prefix of the file. This example uses the IPv4 prefixes 10.10.1.0/24, which is referred to as the VSPA client prefix for VCG-A.

- Click Action, and then enter information for the following fields.

Field Description Action
Select Accept.
Community (Group of Fields) - Community Action
Select Replace all communities with the single community specified by set-community. - Community Value
Enter 1000:1000, which is community C. AS Path (Group of Fields) - AS Path Action
Select Prepend the local AS path the number of times specified by local AS prepend count. - AS Path Prepend
Enter the local AS path for the primary hub, here, 65000. For a secondary hub, use the local AS path multiplied by 2. - Click General Information.
- Enter a name for the Policy Term, here, Local-Client-Prefixes. Optionally, enter a description for the policy term.

- Click Save.
- In the Add BGP Peer Policy screen, click Enter Name, Description & Tags.
- Enter a name for the policy, here, To-SSE-Hub-Primary. Optionally, enter a description of the policy and tags to help you search for policies.
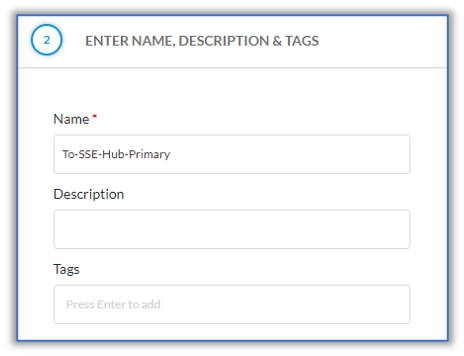
- Click Save.
Configure an Import Policy
You configure one import policy (here, called From-SSE-Hub-Primary) that contains two policy terms, one for Community C (here, called VCG-SSE_Hub-Community) and the second for all other advertised prefixes (here, called Allow-All). This import policy applies for advertisements received from customer SSE hubs.
To configure the import policy:
- Click + Add under Enter Policy Term. The Add Policy Term screen displays.
- Configure an import policy term for Community C:
- Click Criteria.
- In the Community field, enter the community to match, here, 1000:1000.
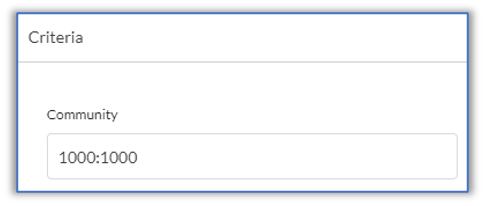
- Click Action.
- In the Action field, select Reject.

- Click General Information
- Enter a name for the Policy Term, here, VCG-SSE_Hub-Community. Optionally, enter a description for the policy term.

- Click Save.
- In the Add BGP Peer Policy screen, click + Add under Enter Policy Term again, to configure a second policy term for all other advertised prefixes. The Add Policy Term screen displays.
- In the Criteria section, leave all entries blank, to match all criteria.

- Click Action, and then enter information for the following fields.

Field Description Action
Select Accept.
Community (Group of Fields) - Community Action
Select Replace all communities with the single community specified by set-community. - Community Value
Enter 1000:1000 64513:64513. The 64513:64513 is community C. AS Path (Group of Fields) - AS Path Action
Select Prepend the local AS path the number of times specified by local AS prepend count. - AS Path Prepend
Enter the local AS path for the primary hub, here, 65000. For a secondary hub, use the local AS path multiplied by 2. - Enter a name for the Policy Term, here, Allow-All. Optionally, enter a description for the policy term.
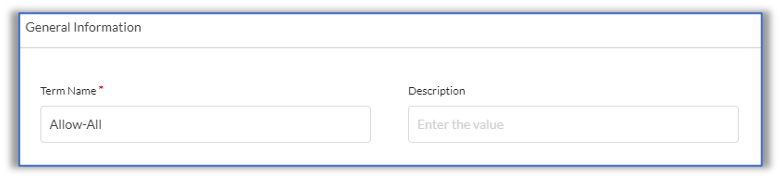
- Click Save.
- In the Criteria section, leave all entries blank, to match all criteria.
- In the Add BGP Peer Policy screen, click Enter Name, Description & Tags.
- Enter a name for the policy, here, From-SSE-Hub-Primary. Optionally, enter a description of the policy and tags to help you search for policies.
- Click Save.
Configure Site-to-Site Tunnels Using Versa Concerto
You must configure site-to-site IPsec tunnels for both the active (primary) and the standby (secondary) paths.
To configure the site-to-site IPsec tunnels:
- Log in to Versa Concerto.
- Go to Configure > Settings > Site-To-Site Tunnels, and then click + Add.

- In the Add Site-to-Site Tunnel screen, click Step 1, Enter Type, and then enter information for the following fields.
- In the Type field, click IPsec.
- In the Versa Gateway field, select the VCG that you want to connect to the customer SSE hub.
- Enter the remote (SD-WAN) public IP address (or FQDN) of the remote device.

- Click Next.
- In the Step 2, Enter IPSec Information screen, enter information for the following fields. The following screenshots show example values. Modify them as necessary for your deployment.
- In the IKE group of fields, select the IKE version, transform, and Diffie-Hellman (DH) group, and enter values for the the dead-peer-detection (DPD) timeout and the IKE rekey time. It is recommended that you should use a strong key exchange transform and DH group.

- In the Local group of fields, select the local identity type, enter a value for the identity type, and enter the shared key for the local device.

- In the Remote group of fields, select the remote identity type, enter a value for the identity type, and enter the shared key for the remote device.

- Click Next.
- In the IKE group of fields, select the IKE version, transform, and Diffie-Hellman (DH) group, and enter values for the the dead-peer-detection (DPD) timeout and the IKE rekey time. It is recommended that you should use a strong key exchange transform and DH group.
- In the Step 3, Enter Address and Routing/Policy Configurations screen, enter information for the following fields.
- In the Tunnel Virtual Interface IP Address field, enter the IP address prefix and mask associated with the VCG tunnel to SSE hub tunnel.
- In the VPN Name field, select name of the VPN between the VCG and the LAN-VR.
- In the MTU field, enter the MTU value of the largest protocol data unit that the port can receive or transmit, here, 1336 bytes.
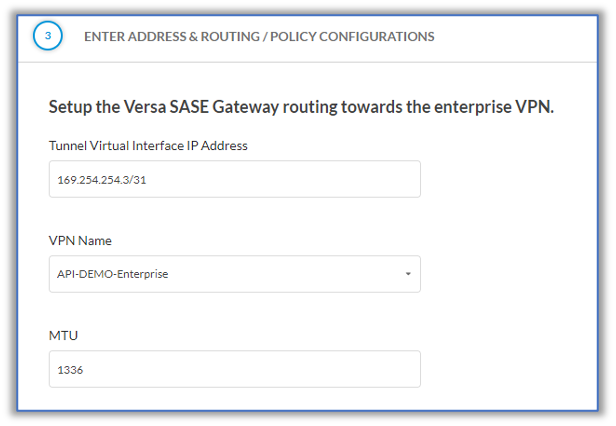
- In the Routing Protocol field, select EBGP.
- In the Local ASN field, enter the AS number of the local VCG customer.
- In the Neighbor Address field, enter the IP address of the SSE hub tunnel that is associated with the VCG-to-SSE hub tunnel.
- In the Import/Export Policy field, select the import and export policies, here, From-SSE-Hub-Primary and To-SSE-Hub-Primary.

- Click Next.
- In the Step 4, Enter Name, Description and Tags screen, enter a name for the site-to-site configuration. Optionally, enter a description of the site-to-site tunnel and tags to help you search for tunnels.
- Click Save.
Configure SSE Hub Devices Using Versa Director
You configure the SSE hub devices on Versa Director. For these devices, you configure tunnel (TVI) interfaces, VPN profiles, BGP, and route redistribution policies.
Configure TVI Interfaces
- In Director View:
- Select the Configuration tab in the top menu bar.
- Select Template > Device Templates.
- Select the SSE hub device that terminates the IPsec tunnel from the VOS VCG. The view changes to Template view.

- Select the Configuration tab in the top menu bar.
- Select Networking > Interfaces > Tunnel in the left menu bar. The following screen displays.

- Click the + Add icon to add a TVI interface.
- Configure the TVI interface to use for the IPsec tunnel. Then, in the Add Tunnel Interface popup window, select the Tunnel tab and enter information for the following fields.
- In the Interface field, enter the slot and port numbers for the TVI interface. The highest interface available is tvi-15/19999.
- Enter a description, for the tunnel interface, here, SSE-VCG-A-IPsec Tunnel.
- Enter the MTU value, here, 1336 bytes.
- In the Mode field, select IPsec.
- In the Tunnel Type field, select Point-to-Point IPsec tunnel.
- In the Subinterfaces table, click Unit 0 to edit it.

- In the Edit Subinterface popup window, select the IPv4 tab.
- In the IP Address and Mask field, click the gear icon to parameterize the IP address and mask. When you use a device template, enter the IP Address in Workflow > Devices > Device > Bind Data.

- Click OK.
- To configure another TVI interface, repeat Step 5.
- Click OK.
The following example shows the CLI commands to add two TVI interfaces (here, tvi-15/100 and tvi-15/101) for the two IPsec tunnels (SSE-VCG-A and SSE-VCG-B).

Add Tunnel Interfaces to Traffic Identification
- In Template view, select the Configuration tab in the top menu bar.
- Select Others > Organization > Limits in the left menu bar.
- Click the organization name. The Edit Organization Limit popup window displays.
- Select the Traffic Identification tab, and then select the two TVI interfaces that you configured in Configure TVI Interfaces, above.

- Click OK.
The following example shows the CLI command to configure TVI interfaces for traffic identification:

Configure VPN Profiles
- In Template View, select Configuration in the top menu bar.
- Select Services > IPsec > VPN Profiles in the left menu bar.

- Click the + Add icon. The Add IPsec VPN popup window displays.
- Select the General tab.
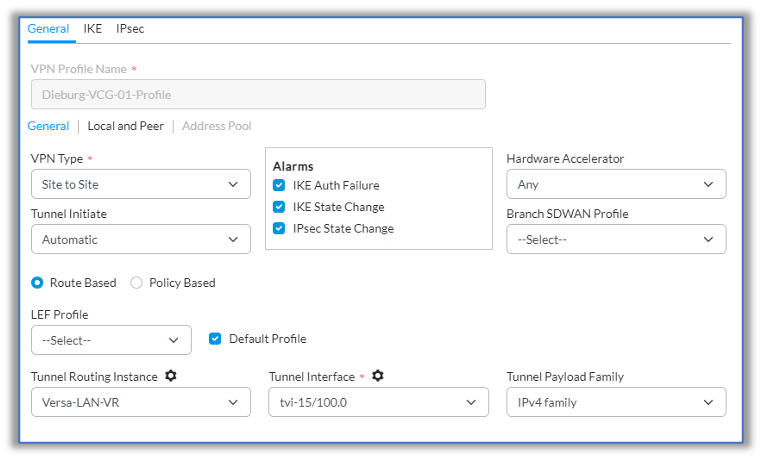
- In the VPN Profile Name field, enter a name for the VPN profile.
- Select the General tab in the horizontal menu bar, and then enter information for the following fields.
- In the VPN Type field, select Site to Site.
- In the Tunnel Routing Instance field, select Versa-LAN-VR.
- In the Tunnel Interface field, select tvi-15/100.0.
- In the Tunnel Payload Family, select IPv4 family.
- Select the Local and Peer tab in the horizontal menu bar, and then enter information for the following fields:
- In the Routing Instance field, select Internet-1-Transport-VR.
- In the Peer group of fields, click Peer IP, and then enter the VCG public IP address, here, 192.168.122.60.
- In the Local group of fields, click Local IP, and then enter the local public IP address.

- In IPsec VPN popup window, select the IKE tab, and the nenter information for the following fields:
- In the Version field, select IKE V2.
- In the Transform and DH Group group of fields, configure the transform and DH group based on customer requirements.
- In the Local Authentication group of fields, configure the local authentication. In the Authentication Type field, select PSK. In the Shared Key field, click the tool icon to parameterize the value. In the Identity Type field, select FQDN. In the FQDN Identity field, click the tool icon to parameterize the value.
- In the Peer Authentication group of fields, configure the peer authentication. Use the same values that you configure for local authorization.

- In IPsec VPN popup window, select the IPsec tab, and then, in the Transform group of fields, configure the transform based on customer requirements.
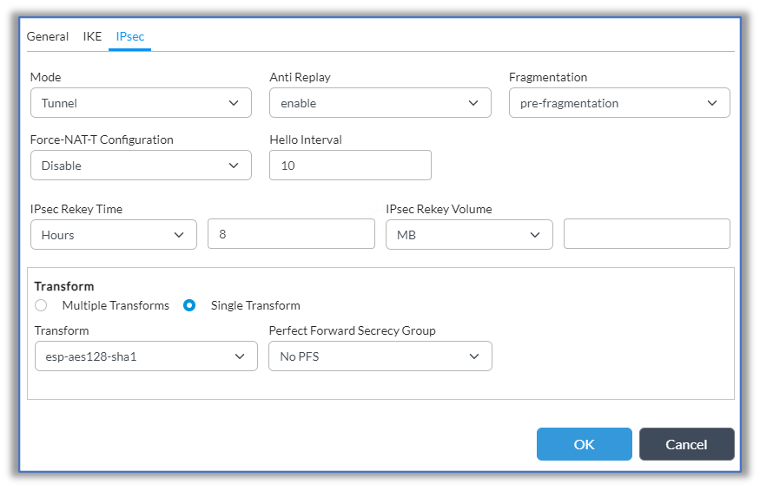
- Click OK.
The following example shows the CLI commands to configure the VPN profile:

Configure the Virtual Router
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu bar.

- Select the virtual router, here, Versa-LAN-VR. The Edit Versa-LAN-VR popup window displays.
- Select the Virtual Router Details tab.
- In the Interfaces/Networks field, select the TVI interfaces that you configured, here, tvi-15/100.0 and tvi-15/101.0.

- Click OK.
The following example shows the CLI command to configure BGP for VCG-A:

Configure BGP
- If you are continuing from the previous section, skip to Step 2. Otherwise:
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu bar.
- Select the virtual router, here, Versa-LAN-VR. The Edit Versa-LAN-VR popup window displays.
- Select the BGP tab, and then click the + Add icon. The Add BGP Instance popup window displays.
- Select the General tab, and then enter information for the following fields:
- In the Instance ID field, enter the BGP instance ID, here, 3611.
- In the Router ID field, click the tool icon to parameterize the value.
- In the Local AS field, enter the customer-assigned AS number, here, 64514.
- In the Local AS Mode field, enter 4.

- Select the Peer Group tab, and then click the + Add icon. In the Add BGP Instance Add Peer Group popup window displays, enter information for the following fields:
- In the Name field, enter a name for the peer group, here, VGP-Hub-Group.
- In the Type field, select EBGP.

- Select the Neighbors tab, and then click the + Add icon. The Edit BGP Instance Add Peer Group Add Neighbor popup window displays.
- To configure a BGP neighbor for VCG-A, enter information for the following fields:
- In the Neighbor IP field, click the tool icon to parameterize the value.
- In the Peer AS field, click the tool icon to parameterize the value.
- In the Local Address field, click the tool icon to parameterize the value.

- Click OK.
- Repeat Step 6 to configure a BGP neighbor for VCG-B.
- Click OK.
The following example shows the CLI commands to configure BGP for VCG-A:

Configure Redistribution Policies
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu bar.

- Select the virtual router (in this example, Versa-LAN-VR). The Edit Versa-LAN-VR popup window displays.
- Select the Redistribution Policies tab, and then click the + Add icon. The Add Redistribution Policy popup window displays.
- In the Name field, enter a Name for the Redistribution Policy, here, To-Versa-LAN-VR-Export.

- In the Terms group of fields, click the + Add icon to add a term. The Add Redistribution Policy Add Term popup window displays.
- Select the Match tab, and then enter information for the following fields.
- Enter a name for the term, here, SSE-Client-Prefixes.
- In the Protocol field, select BGP.
- In the Community field, enter the community number, here, 1000:1000, for community C.

- Select the Action tab and then enter information for the following fields.
- In the Accept/Reject field, select Accept.
- In the Origin field, select Local EGP.

- Click OK.
- Click the
 Move Top icon to move the term to the top of the list of terms in the policy.
Move Top icon to move the term to the top of the list of terms in the policy. - Click OK.
- Click the + Add icon to configure a second redistribution policy. The Add Redistribution Policy popup window displays.
- Enter a Name for the Redistribution Policy, here, Default-Policy-To-BGP.
- Click the + Add icon to add a term. The Add Redistribution Policy Add Term popup window displays.
- Select the Match tab, and then enter information for the following fields.
- Enter a name for the term, here, SSE-Client-Prefixes.
- In the Protocol field, select BGP.
- In the Community field, enter the community number, here, 1000:1000, for community C.
- Select the Action tab, and then enter information for the following fields.
- In the Accept/Reject field, select Accept.
- In the Community field, enter the community number, here, 8009:8010, which is the standard Versa Hub global community for hub LAN routes.
- In the Origin field, select Local EGP.

- Click OK.
- Click the
 Move Top icon to move the term to the top of the list of terms in the policy.
Move Top icon to move the term to the top of the list of terms in the policy. - Click OK.
The following example shows the CLI commands to configure redistribution policies:

Traffic Flow Examples
The diagram below shows the steady state traffic flow for the VSPA configuration in active–standby.

The following screenshots show session statistics from SSE Hub CPE-A. For information on monitoring sessions, see Monitor VOS Devices in Real Time.

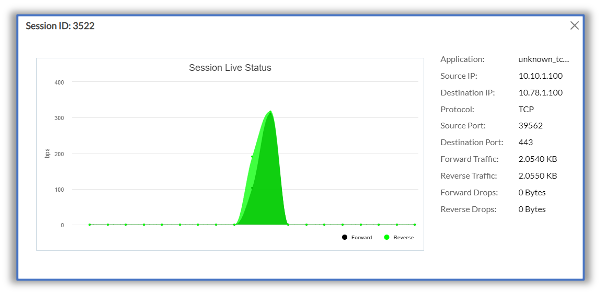
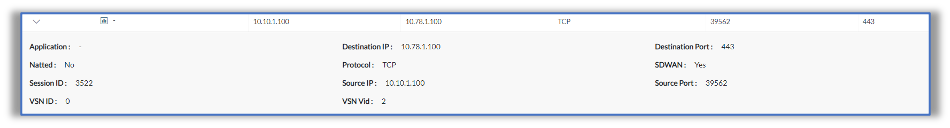
The following example shows output for the show orgs org org-name session extensive CLI command on SSE Hub CPE-A:

In the event of a failure on the active traffic path between SSE VCG-A and customer SSE Hub CPE-A, the traffic flow diverts to customer SSE Hub CPE-B, as shown in the diagram below.

The following screenshots show session statistics for customer SSE Hub CPE-B. For information on monitoring sessions, see Monitor VOS Devices in Real Time.


The following example shows output for the show orgs org org-name session extensive CLI command on customer SSE Hub CPE-B:

Configure VSIA
This section provides a VSIA configuration example for the active–standby traffic path model. For this configuration, you do the following:
- On Versa Concerto, configure BGP peering policies.
- On Versa Concerto, configure site-to-site tunnels.
- On Versa Director, configure the SSE hub devices. For these devices, you configure tunnel (TVI) interfaces, VPN profiles, BGP, and route redistribution policies.
If you want to configure the active–active traffic path model instead, the configuration is similar, but you apply the primary BGP peering policies to both tunnel interfaces. Also, you must configure symmetric forwarding on the branches in the customer SD-WAN environment.
Configure BGP Peer Policies Using Versa Concerto
On Versa Concerto, you configure BGP peering policies. You configure export policies to filter the advertisements that are sent to customer SSE hubs and import policies to filter the advertisements that are received from the customer SSE hubs.
To configure the BGP peering policies:
- Log in to Versa Concerto.
- Go to Configure > Security Service Edge > Settings, and then click BGP Peer Policies.

- Click + Add Policy Term. The Add BGP Peer Policy screen displays.

From this screen, you configure the import and export policies.
Configure an Export Policy
You configure one export policy (here, called To-SSE-Hub-Primary) that contains two policy terms, one for Community C (here, called VCG-SSE_Hub-Community) and the second for the default route (here, called Default-Route). This export policy applies for advertisements towards customer SSE hubs.
To configure the export policy:
- Click + Add under Enter Policy Term. The Add Policy Term screen displays.
- Configure an export policy for Community C:
- Click Criteria.

- In the Community field, enter the community string to match, here, 1000:1000.

- Click Action.

- In the Action field, select Reject.

- Click General Information.

- Enter a name for the Policy Term, here, VCG-SSE_Hub-Community. Optionally, enter a description for the policy term.

- Click Save.
- Click Criteria.
- In the Add BGP Peer Policy screen, click + Add under Enter Policy Term again, to configure a second policy term for the default route. The Add Policy Term screen displays.
- Click Criteria.
- In the NLRI field, enter the IP prefix to match. This example uses prefixes 0.0.0.0/0.

- Click Action, and then enter information for the following fields.
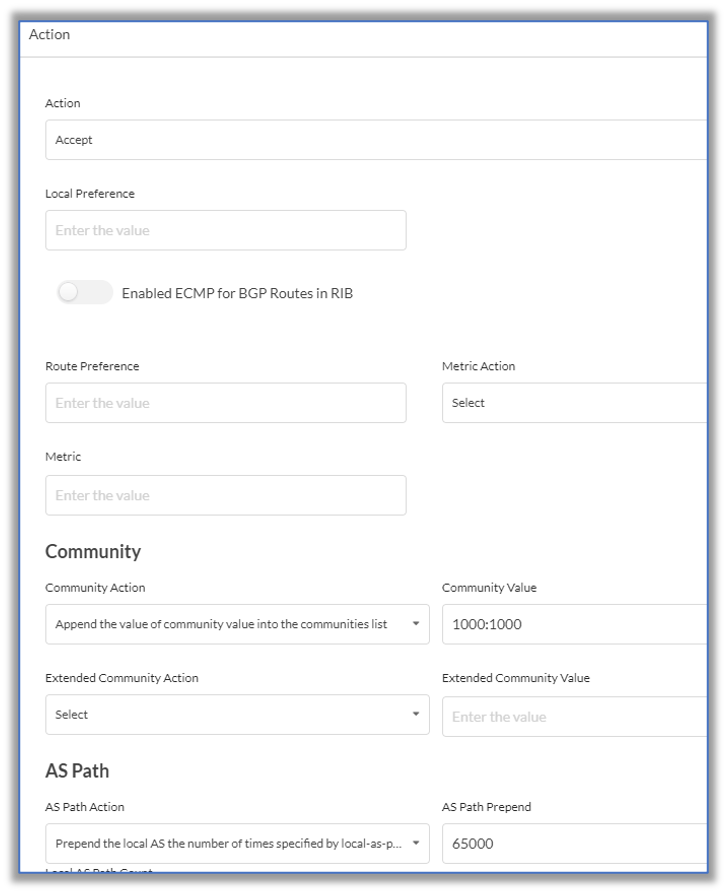
Field Description Action Select Accept. Community (Group of Fields) - Community Action
Select Replace all communities with the single community specified by set-community. - Community Value
Enter 1000:1000, which is community C. AS Path (Group of Fields) - AS Path Action
Select Prepend the local AS path the number of times specified by local AS prepend count. - AS Path Prepend
Enter the local AS path for the primary hub, here, 65000. For a secondary hub, use the local AS path multiplied by 2. - Click General Information.
- Enter a name for the Policy Term (here, Default-Route) and a description (optional).

- Click Save.
- In the Add BGP Peer Policy screen, click Enter Name, Description & Tags.
- Enter a name for the policy, here, To-SSE-Hub-Primary. Optionally, enter a description of the policy and tags to help you search for policies.

- Click Save.
Configure an Import Policy 
You configure one import policy (here, called From-SSE-Hub-Primary) that contains two policy terms, one for Community C (here, called VCG-SSE_Hub-Community) and the second for all other advertised prefixes (here, called Allow-All). This import policy applies for advertisements received from customer SSE hubs.
To configure the import policy:
- Click + Add under Enter Policy Term. The Add Policy Term screen displays.
- Configure an import policy term for Community C:
- Click Criteria.
- In the Community field, enter the community to match, here, 1000:1000.

- Click Action.
- In the Action field, select Reject.

- Click General Information
- Enter a name for the Policy Term, here, VCG-SSE_Hub-Community. Optionally, add a description for the policy term.

- Click Save.
- In the Add BGP Peer Policy screen, click + Add under Enter Policy Term again, to configure a second policy term for all other advertised prefixes. The Add Policy Term screen displays.
- Configure the policy term for all other advertised prefixes:
- In the Criteria section. leave all entries blank, to match all criteria.

- Click Action, and then enter information for the following fields.

Field Description Action
Select Accept.
Community (Group of Fields) - Community Action
Select Replace all communities with the single community specified by set-community. - Community Value
Enter 1000:1000 64513:64513. The 64513:64513 is community C. AS Path (Group of Fields) - AS Path Action
Select Prepend the local AS path the number of times specified by local AS prepend count. - AS Path Prepend
Enter the local AS path for the primary hub, here, 65000. For a secondary hub, use the local AS path multiplied by 2. - Enter a name for the Policy Term, here, Allow-All. Optionally, enter a description for the policy term.

- Click Save.
- In the Criteria section. leave all entries blank, to match all criteria.
- In the Add BGP Peer Policy screen, click Enter Name, Description & Tags.
- Enter a name for the policy, here, From-SSE-Hub-Primary. Optionally, enter a description of the policy and tags to help you search for policies.

- Click Save.
Configure Site-to-Site Tunnels Using Versa Concerto
You must configure site-to-site IPsec tunnels for both the active (primary) and the standby (secondary) paths.
To configure the site-to-site IPsec tunnels:
- Log in to Versa Concerto.
- Go to Configure > Security Service Edge > Settings > Site-To-Site Tunnels, and then click + Add.

- In the Add Site-to-Site Tunnel screen, click Step 1, Enter Type, and then enter information for the following fields.
- In the Type field, click IPsec.
- In the Versa Gateway field, select the VCG that you want to connect to the customer SSE hub.
- Enter the remote (SD-WAN) public IP address (or FQDN) of the remote device.

- Click Next.
- In the Step 2, Enter IPSec Information screen, enter information for the following fields. The following screenshots show example values. Modify them as necessary for your deployment.
- In the IKE group of fields, enter the IKE Version, Transform, DH Group, DPD Timeout and IKE Rekey Time. It is recommended that you should use a strong key exchange transform and DH group.

- In the Local group of fields, select the local identity type, enter a value for the identity type, and enter the shared key for the local device.

- In the Remote group of fields, select the remote identity type, enter a value for the identity type, and enter the shared key for the remote device.

- Click Next.
- In the IKE group of fields, enter the IKE Version, Transform, DH Group, DPD Timeout and IKE Rekey Time. It is recommended that you should use a strong key exchange transform and DH group.
- In the Step 3, Enter Address & Routing / Policy Configurations screen, enter information for the following fields.
- In the Tunnel Virtual Interface IP Address field, enter the VCG tunnel IP address and mask associated with the VCG-to-SSE hub tunnel.
- In the VPN Name field, select name of the VPN between the VCG and the LAN-VR.
- In the MTU field, enter the MTU value of the largest protocol data unit that the port can receive or transmit, here, 1336 bytes.

- In the Routing Protocol field, select EBGP.
- In the Local ASN field, enter the AS number of the local VCG customer.
- In the Neighbor Address field, enter the IP address of the SSE hub tunnel that is associated with the VCG-to-SSE hub tunnel.
- In the Import/Export Policy field, select the import and export policies, here, From-SSE-Hub-Primary and To-SSE-Hub-Primary.

- Click Next.
- In the Step 4, Enter Name, Description and Tags screen, enter a name for the site-to-site configuration. Optionally, enter a description of the site-to-site tunnel and tags to help you search for tunnels.
- Click Save.
Configure SSE Hub Devices Using Versa Director
You configure the SSE hub devices on Versa Director. For these devices, you configure tunnel (TVI) interfaces, VPN profiles, BGP, and route redistribution policies.
Configure TVI Interfaces
- In Director View:
- Select the Configuration tab in the top menu bar.
- Click Template > Device Templates.
- Select the SSE hub device that terminates the IPsec tunnel from the VOS VCG. The view changes to Template view.

- Select the Configuration tab in the top menu bar.
- Select Networking > Interfaces > Tunnel in the left menu bar. The following screen displays.

- Click the + Add icon to add a TVI interface.
- Configure the TVI interface to use for the IPsec tunnel:
- In the Interface field, enter the slot and port numbers for the TVI interface. The highest interface available is tvi-15/19999.
- Enter a description, for the tunnel interface, here, SSE-VCG-A-IPsec Tunnel.
- Enter the MTU value, here, 1336 bytes.
- In the Mode field, select IPsec.
- In the Tunnel Type field, select Point-to-point IPsec tunnel.
- In the Subinterfaces table, click Unit 0 to edit it.

- In the Edit Subinterface popup window, select the IPv4 tab.
- In the IP Address and Mask field, click the gear icon to the right to parameterize the IP address and mask. When you use a device template, enter the IP Address in Workflow > Devices > Device > Bind Data.

- Click OK.
- To configure another TVI interface, repeat Step 5.
- Click OK.
The following example shows the CLI commands to add two TVI interfaces (here, tvi-15/100 and tvi-15/101) for the IPsec tunnels (SSE-VCG-A and SSE-VCG-B).

Add Tunnel Interfaces to Traffic Identification
- In Template view, select Configuration in the top menu bar.
- Select Others > Organization > Limits in the left menu bar.
- Click the organization name. The Edit Organization Limit popup window displays.
- Select the Traffic Identification tab, and then select the two TVI interfaces that you configured in Configure TVI Interfaces, above.

- Click OK.
The following example shows the CLI command to add TVI interfaces to traffic identification.

Configure VPN Profiles
- In Template View, select Configuration in the top menu bar.
- Select Services > IPsec > VPN Profiles in the left menu bar.

- Click the + Add icon. The Add IPsec VPN popup window displays.
- Select the General tab.

- In the VPN Profile Name field, enter a name for the VPN profile.
- Select the General tab in the horizontal menu bar, and then enter information for the following fields.
- In the VPN Type field, select Site to Site.
- In the Tunnel Routing Instance field, select Versa-LAN-VR.
- In the Tunnel Interface field, select tvi-15/100.0.
- In the Tunnel Payload Family, select IPv4 family.
- Select the Local and Peer tab in the horizontal menu bar, and then enter information for the following fields.
- In the Routing Instance field, select Internet-1-Transport-VR.
- In the Peer group of fields, click Peer IP, and then enter the VCG public IP address, here, 192.168.122.60.
- In the Local group of fields, click Local IP, and then enter the local public IP address.

- In IPsec VPN popup window, select the IKE tab, and the nenter information for the following fields.
- In the Version field, select IKE V2.
- In the Transform and DH Group group of fields, configure the transform and DH group based on customer requirements.
- In the Local Authentication group of fields, configure the local authentication. In the Authentication Type field, select PSK. In the Shared Key field, click the tool icon to parameterize the value. In the Identity Type field, select FQDN. In the FQDN Identify field, click the tool icon to parameterize the value.
- In the Peer Authentication group of fields, configure the peer authentication. Use the same values that you configured for local authorization.

- In the IPsec VPN popup window, select the IPsec tab, and then, in the Transform group of fields, configure the Transform group of fields based on customer requirements.

- Click OK.
The following example shows the CLI commands to configure the VPN profile.

Configure Virtual Router Details
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu.

- Select the virtual router, here, Versa-LAN-VR. The Edit Versa-LAN-VR popup window displays.
- Select the Virtual Router Details tab.
- In the Interfaces/Networks field, select the TVI interfaces that you configured, here, tvi-15/100.0 and tvi-15/101.0.

- Click OK.
The following example shows the CLI commands to configure BGP for VCG-A:

Configure BGP
- If you are continuing from the previous section, skip to Step 2. Otherwise:
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu bar.
- Select the virtual router, here, Versa-LAN-VR. The Edit Versa-LAN-VR popup window displays.
- Select the BGP tab and click the + Add icon. The Add BGP Instance popup window displays.
- Select the General tab, and then enter information for the following fields.
- In the Instance ID field, enter the BGP instance ID, here, 3611.
- In the Router ID field, click the tool icon to parameterize the value.
- In the Local AS field, enter the customer-assigned AS, here, 64514.
- In the Local AS Mode field, enter 4.

- Select the Peer Group tab, and then click the + Add icon. The Add BGP Instance Add Peer Group popup window displays.
- Enter information for the following fields.
- In the Name field, enter a name for the peer group, here, VGP-Hub-Group.
- In the Type field, enter EBGP.

- Select the Neighbors tab, and then click the + Add icon. The Edit BGP Instance Add Peer Group Add Neighbor popup window displays.
- To configure a BGP neighbor for VCG-A, enter information for the following fields.
- In the Neighbor IP field, click the tool icon to parameterize the value.
- In the Peer AS field, click the tool icon to parameterize the value.
- In the Local Address field, click the tool icon to parameterize the value.

- Click OK.
- Repeat Step 7 to configure a BGP neighbor for VCG-B.
- Click OK.
The following example shows the CLI commands to configure BGP for VCG-A:

Configure Redistribution Policies
- In Template View, select Configuration in the top menu bar.
- Select Networking > Virtual Routers in the left menu.

- Select the virtual router, here, Versa-LAN-VR. The Edit Versa-LAN-VR popup window displays.
- Select the Redistribution Policies tab, and then click the + Add icon. The Add Redistribution Policy popup window displays.
- In the Name field, enter a name for the Redistribution Policy, here, To-Versa-LAN-VR-Export.

- In the Terms group of fields, click the + Add icon to add a term. The Add Redistribution Policy Add Term popup window displays.
- Select the Match tab, and then enter information for the following fields.
- Enter a name for the term, here, SSE-Default-Route.
- In the Protocol field, select BGP.
- In the Community field, enter the community number, here, 1000:1000, for community C.

- Select the Action tab, and then enter information for the following fields.
- In the Accept/Reject field, select Accept.
- In the Origin field, select Local EGP.
- Click OK.
- Click on the
 Move Top icon to move the term to the top of the list.
Move Top icon to move the term to the top of the list. - Click OK.
- Click the + Add icon to configure a second redistribution policy. The Add Redistribution Policy popup window displays.
- Enter a Name for the Redistribution Policy, here, Default-Policy-To-BGP.
- Click the + Add icon to add a term. The Add Redistribution Policy Add Term popup window displays.
- Select the Match tab, and then enter information for the following fields.
- Enter a name for the term, here, SSE-Default-Route.
- In the Protocol field, select BGP.
- In the Community field, enter the community number, here, 1000:1000, for community C.

- Select the Action tab, and then enter information for the following fields.
- In the Accept/Reject field, select Reject.

- In the Accept/Reject field, select Reject.
- Click OK.
- Click on the
 Move Top icon to move the term to the top of the list.
Move Top icon to move the term to the top of the list. - Click OK.
The following example shows the CLI commands to configure redistribution policies:

Traffic Flow Examples
The diagram below shows the steady state traffic flow for the VSIA configuration in active–standby.

The following screenshots show session statistics from SSE Hub CPE-A. For information on monitoring sessions, see Monitor VOS Devices in Real Time.
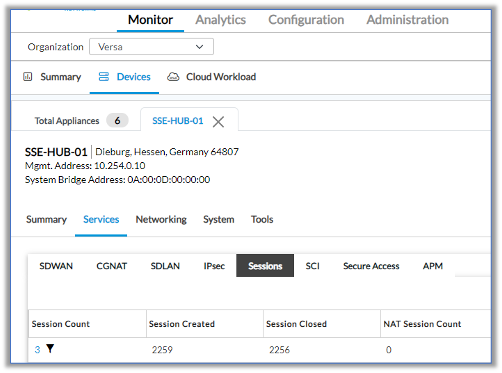

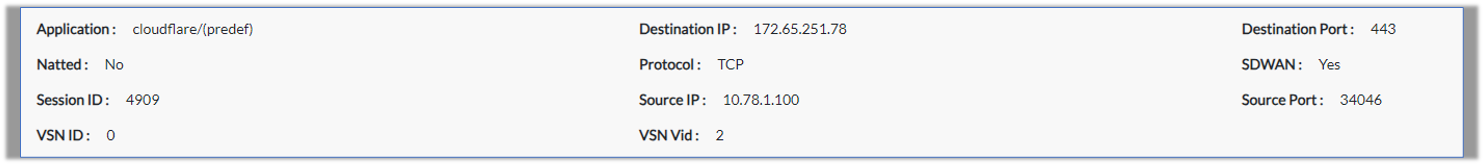
The following example shows output for the show orgs org org-name session extensive CLI command on SSE Hub CPE-A:

In the event of a failure on the active traffic path between SSE VCG-A and customer SSE Hub CPE-A, the traffic flow diverts to customer SSE Hub CPE-B, as shown in the diagram below.

The following screenshots show session statistics from SSE Hub CPE-A. For information on monitoring sessions, see Monitor VOS Devices in Real Time.



The diagram below shows the steady state traffic flow for the VSIA configuration in active–active.

The following screenshots show session statistics from SSE Hub CPE-A. For information on monitoring sessions, see Monitor VOS Devices in Real Time.

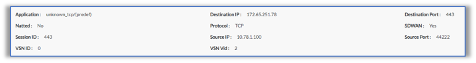
The following example shows output for the show orgs org org-name session extensive CLI command on SSE Hub CPE-A:


