Configure Service Objects
![]() For supported software information, click here.
For supported software information, click here.
In the Versa Operating SystemTM (VOSTM) software, security policies can reference service objects, which define match criteria based on protocol name and number, and on source and destination port number. Versa Networks provides predefined services and object definitions, which are essentially factory defaults.
Predefined services and objects are periodically updated through security packages (SPacks). You can use the security package to update the predefined objects at any time, without any operational impact to the Director node or to VOS devices. To provide feedback about the predefined objects, including input about adding or modifying them, send email to support@versa-networks.com.
You can also create custom service objects. One reason to do this might be if a well-known service runs on a non-standard port, or if the predefined services are missing a desired port and protocol combination. Another reason might be to limit the number of ports that an application can use. For example, you could limit FTP to use only port 21 instead of using both ports 20 and 21.
The custom service objects that you define for a tenant can be used only by that tenant, and they are not visible or available to any other tenants.
View Predefined Services
To view the predefined services on a VOS device:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Predefined > Services to view the list of predefined service objects.

- Click the
 Column Filter icon to restrict the columns to display in the table.
Column Filter icon to restrict the columns to display in the table. - Click the
 Filter icon to filter the display by the protocol name, protocol value, source port, and destination port.
Filter icon to filter the display by the protocol name, protocol value, source port, and destination port.
Configure Custom Service Objects
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Custom Objects > Services in the left menu bar.

- Click + Add in the main pane to add a custom service. In the Add Service window, enter information for the following fields.

Field Description Name Enter a name for the custom service object. Description Enter a text description for the custom service object. Tags Enter a text string to describe the custom service object. Protocol Click to define a custom service object by protocol name. Then, in the Protocol field, select the protocol:
- AH
- ESP
- ICMP
- ICMPv6 (for Releases 22.1.1 and later.)
- TCP
- TCP or UDP
- UDP
Protocol Value Click to define a custom service object by protocol number. Then, in the Protocol Value field, enter the number of the protocol.
Port Range Click to configure a port range for the custom service object. Then, in the Port field, enter the port number range.
You can enter a single port number (for example, 20000), multiple comma-separated port numbers (for example, 20000,22000,5600), or a hyphen-separated range of port numbers (for example, 20000-22000).
Source/Destination Port Click to associate the custom service object with a single source or destination port, or with a combination of source and destination ports. Then, in the Source Port and Destination Port fields, enter the port numbers.
You can enter a single port number (for example, 20000), multiple comma-separated port numbers (for example, 20000,22000,5600), or a hyphen-separated range of port numbers (for example, 20000-22000).
ICMP (For Releases 22.1.1 and later.) If you select the ICMP or ICMPv6 protocol, click to define a custom service object by ICMP values:
- ICMP Code—Enter the ICMP code. You can enter an individual value, a comma-separated list of values, or a range of values.
- ICMP Type—Enter the ICMP type. You can enter an individual value, a comma-separated list of values, or a range of values (for example, 9-12).
- Click OK.
Configure Custom Service Group Objects
For Releases 23.1.1 and later.
You can create service group objects that combine multiple custom services into a single service group in order to simplify network configurations, particularly in firewalls and other security devices.
To configure custom service group objects:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Custom Objects > Services Groups in the left menu bar.

The following screen displays.

- Click the
 Add icon. In the Add Service Group popup window, enter information for the following fields.
Add icon. In the Add Service Group popup window, enter information for the following fields.

Field Description Name (Required) Enter a name for the service group. Description Add a description of the service group. User Defined Service List Select a user-defined service, then click the  Add icon to add it to the list of records. You can add multiple services.
Add icon to add it to the list of records. You can add multiple services.Predefined Service List Select a predefined service, then click the  Add icon to add it to the list of records. You can add multiple services.
Add icon to add it to the list of records. You can add multiple services. -
Click OK to save the new service group.
Apply a Service Object to an Access Policy
You can apply a service object to a security access policy to define a security policy. To define and configure a security access policy, see Configure Security Access Policy Rules.
To apply a service object to an access policy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Services > Next-Gen Firewall > Security > Policies in the left menu bar, and then select the Rules tab.

- Click a security access policy rule name in the main pane. The Edit Rule popup window displays.
- Select the Headers/Schedule tab.

- In the Service List table, select the
 Add icon, and then select a service object.
Add icon, and then select a service object. - Click OK.
Configuration Example
The following example shows how to deny HTTP traffic based on a service object and associated access policy rule, and how to monitor the effects of the rule.
To configure the service object:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Configuration tab in the top menu bar.
- Select Objects & Connectors > Objects > Custom Objects > Services in the left menu bar.
- Select + Add.
- In the Add Service popup window, add a service object.
- Enter a name for the service object. In this example, the name is Custom_HTTP_Service.
- Click the Protocol field, and select TCP as the protocol.
- Click the Source/Destination field, and enter a value for Destination Port. In this example, the port is 8080.
- Click OK.

- Click OK.
- Select Services > Next-Gen Firewall > Security > Policies in the left menu bar, and then select the Rules tab.
- Click + Add. The Add Rule popup window displays.
- Create an access policy rule that includes the scheduled object.
- Select the General tab, and then enter the name of the access policy rule (here, Block_HTTP_Service_to_Port_8080).

- Select the Headers/Schedule tab, and then select the service you created in Step 5 (here, Custom_HTTP_Service).
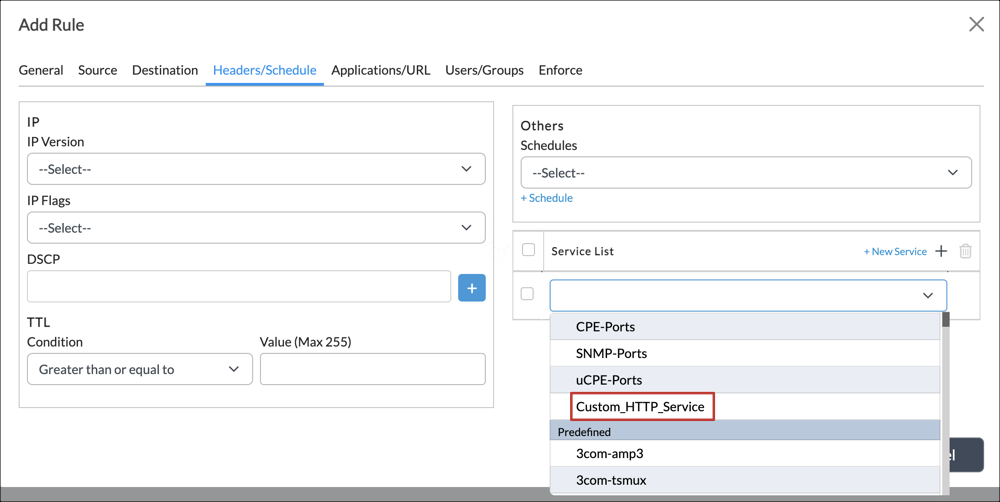
- Select the Enforce tab, and then select Deny under Actions.

- Click OK to creates a rule that denies HTTP traffic to port 8080.
- Select the General tab, and then enter the name of the access policy rule (here, Block_HTTP_Service_to_Port_8080).
To see how the service object associated with a policy affects the traffic flow, you monitor the policy:
- In Director view:
- Select the Administration tab in the top menu bar.
- Select Appliances in the left menu bar.
- Select a device name in the main panel. The view changes to Appliance view.
- Select the Monitor tab in the top menu bar.
- Select a provider organization in the Organization field.
- Select the Services tab in the horizontal menu bar.
- Select NGFW > Policies. The NGFW policy statistics display, and the Rule Name column displays statistics about the access policy rule that you created.

Supported Software Information
Releases 20.2 and later support all content described in this article, except:
- Release 22.1.1 adds support for ICMPv6. You can specify the ICMP type and code for ICMPv4 and ICMPv6 custom service objects.
- Release 23.1.1 adds support for configuring custom service group objects.
Additional Information
Configure Stateful Firewall
Monitor Device Services
Use Security Packages
