Troubleshoot Endpoint Information Profiles
Enterprise users can connect to networks and resources from a variety of locations and using a variety of endpoints, or remote computing devices. To protect the enterprise network and resources, you can create endpoint information profiles (EIPs). EIPs ensure that the endpoint devices accessing the enterprise network maintain and adhere to enterprise security standards. For more information about configuring EIP, see Configure Endpoint Information Profiles.
Reregister Versa SASE Client
You must reregister the Versa SASE client in the following scenarios if you make any changes to an EIP agent profile:
- When you update an EIP agent profile associated with an SCA policy rule. For example, if you change a predefined EIP agent profile to a user-defined EIP agent profile in an SCA rule.
- When you update any EIP objects within a user-defined EIP agent profile. For example, if you add the AntiMalware_category_vendor to an existing user-defined EIP agent profile.
- If you update any rules of an existing user-defined EIP object. For example, if you amend the match criteria of Configured from disabled to true.
The Versa SASE client automatically reregisters at the end of Portal lifetime. To reregister the Versa SASE client manually, select Settings > [tenant_name] > Reregister.
Amending the Welcome Message
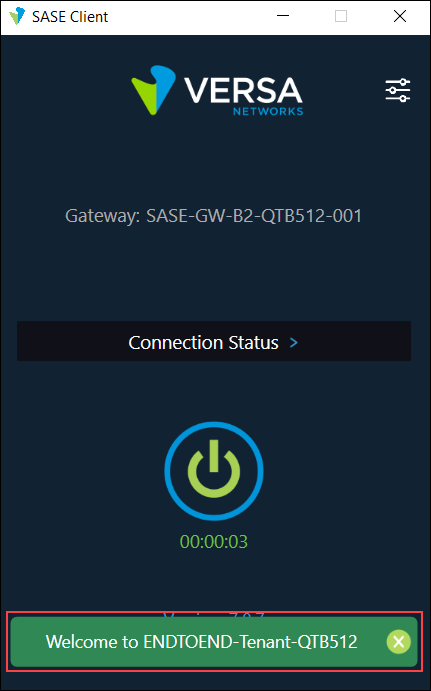
To troubleshoot EIP, you can include a reference to the SCA policy rule name in the welcome message that displays when the Versa SASE client connects to the Versa portal or Versa SASE gateway. You do this by amending the default welcome message when you configure an SCA policy rule. The default welcome message format is Welcome to <tenant name>. For example, if the default message is Welcome to Versa-SSE, you update the default message to Welcome to Versa-SSE (SWG_Demo), where SWG_Demo refers to the name of the matched SCA policy rule. When an enterprise device connects to the Versa SASE client, the welcome banner displays which SCA policy rule the end device matched.
Note that EIP information is used as a match criteria only when Versa SASE client connects to Versa gateways. Therefore, for troubleshooting purposes, focus on the welcome message when connecting to the Versa SASE gateway.
To update the welcome message with the SCA policy rule name:
- Go to Configure > Secure Services Edge > Secure Access Client > Policy Rules.
- Select the secure client access rule.
- In the Edit Secure Client Access Rule page, select Traffic Action, and then add the SCA policy rule name to the default text in the Display Message after Successful Connection field.

The Welcome message displays when the Versa SASE client connects to the Versa portal or Versa SASE gateway:
Troubleshoot EIP Profiles Using Site-to-Site Monitor
View EIP Cache Information
With EIPs, you collect information about the security status of the endpoint devices connecting to your networks. You then classify the endpoints based on multiple types of endpoint posture information, defining rules that allow the VOS SSE software to extract information from endpoint devices and then match the information to enforce security policy.
If you want to use EIP cache information to troubleshoot EIP, you must configure an EIP agent profile in the corresponding secure client access (SCA) for the entity and associate the EIP agent profile to an SCA rule. You configure an EIP agent profile that defines when the SSE client must extract information from endpoint devices. You associate predefined or custom EIP agent profiles with SCA rules to enforce EIP security. When you associate an EIP agent profile to an SCA policy, the entity gathers EIP information and sends it to the SSE gateway. The EIP cache information is populated with device posture details after you configure an EIP agent profile and associate it to an SCA rule. If EIP cache information is not available, check if an EIP agent profile is associated with the SCA policy.
An entity can match a single EIP profile or multiple EIP profiles. By matching multiple EIP profiles, entities can be permitted or denied based on simple or complex EIP profile information. For example, all entities with Chrome installed may access the internet. However, only entities with disk encryption, anti-malware software and Chrome may access an intranet website. In this example, if an entity matches both EIP profiles, a private app protection rule can be created to match the more complex EIP profile, whereas an internet protection rule can be created to match the simple EIP profile.
To view EIP cache information:
- Select View > Secure Access > Site-to-Site Tunnels.
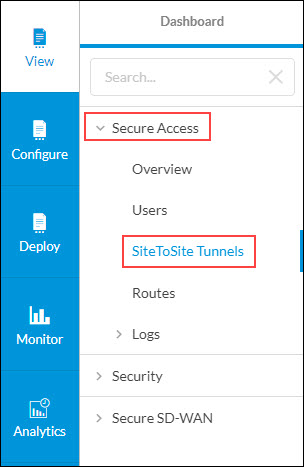
- From the list of available SSE gateways, select the SSE gateway the entity is connecting to, and then click View Advanced Monitor.

- In the Devices > Services tab, select the Secure Access > EIP Cache tab.

- In the Serial Number column, click the
 Eye icon to view the EIP information that the entity sends to the SSE gateway.
Eye icon to view the EIP information that the entity sends to the SSE gateway.

The following screenshot shows the EIP cache information for the selected entity.

View EIP History Information
You must have an administrator privilege level to view the EIP history information. By default, entities send EIP information to the SSE gateway every 10 minutes.
To view secure access history:
- Select View > Secure Access > Site-to-Site Tunnels.

- From the list of available SSE gateways, select the SSE gateway the entity is connecting to, and then click View Advanced Monitor.

- In the Devices > Services tab, select the Secure Access > History tab, and then select Gateway in the drop-down list.

- In the ID column, click the ID link to view the EIP history information. You can select multiple IDs.
The following screenshot shows EIP history information for the 10-minute interval.
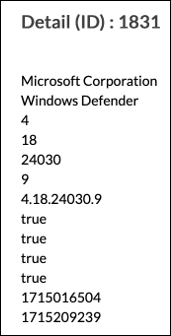
The following screenshot shows multiple IDs (1831 through 1833) are selected, and the Timestamp shows that the entity is sending EIP information every 10 minutes.

View Session Information
If an EIP is associated with real-time protection rules, you can troubleshoot EIP using the View > Devices > Services > Sessions tab. You can check the access policy associated with a session that is created for every flow of information between the source and destination.
In the following example, the internet protection rule controls the data flow from Versa SSE client to the internet. The rule matches the CORP-DEVICE EIP profile.

The EIP profile matches the EIP information as shown in the following screenshot. Note that all elements in R1 must match for entities to be associated with the CORP-DEVICE EIP profile.

The entity has the following objects in running state:
- Windows firewall
- Bitlocker
- Defender and realtime
When a user attempts to ping 8.8.8.8, the session table shows the access policy associated with the stream. The following screenshot shows the policy that meets the match criteria of the rule. To view the access policy, select Extensive in the drop-down list, and apply the filter to the session table to display sessions containing 8.8.8.8.

If the session is associated with an unexpected access policy, check the EIP Profile List column. The following screenshot shows one of the EIP profiles associated with the entity is CORP-DEVICE, and this profile is used as match criteria for the internet protection rule.

Troubleshoot EIP Profiles Using Versa Analytics
View Entity Registration Information
You can access registration information for an entity using one of the following navigation paths in Concerto:
- Analytics > Dashboard > View > Secure Access > Users > Registry
- View > Secure Access > Users > Registry
The Registrations metrics show the secure client access profile associated with the entity during the registration to the SASE service. Note that recall EIP information is not considered as match criteria during registration, so there may be a profile name change in the output.
The following screenshot shows the SCA profile name from the registry information using the Analytics menu.

View EIP Log Information
The EIP log screen shows the historical record of the EIP profile associations that the entity makes over time. You can access the EIP logs from the Analytics > Dashboard > Logs > EIP > Logs tab.
In the following screenshot, the SSE gateway associated the entity with two EIP profiles based on the information received from the Versa SASE client. You can also use the EIP rule name to troubleshoot the EIP issues.

The following screenshot shows that the entity is disassociated from the IAN-CORP-DEVICE EIP profile, and associated with the CORP-DEVICE EIP profile because of a poster change in the entity.

The change is because of the automatic updates that Versa SASE client sends to the SSE gateway, and does not need the Versa SASE client to disconnect and reconnect. This allows the SSE gateway to control access to resources based on the dynamic posture of the entity.
View Versa SASE Web Logs
You can access the Versa SASE web logs that have session information and associations to real-time protection rules from the Analytics > Dashboard > Logs > SASE Web Monitoring > Logs tab. You can check the rule that is associated with the session and compare the rules.

Example: EIP Updates from a Windows Entity
The following example is an EIP update from a Windows entity based on the EIP agent profile Versa_Recommended:
<eip>
<antimalware>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows Defender</product>
<major>4</major>
<minor>18</minor>
<service>24030</service>
<patch>9</patch>
<raw_version>4.18.24030.9</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
<realtime-protection>true</realtime-protection>
<last-scan-time>1715016504</last-scan-time>
<last-definition-update>1715189346</last-definition-update>
</software>
</softwares>
</antimalware>
<firewall>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows Firewall</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1852</patch>
<raw_version>10.0.17763.1852</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</firewall>
<disk-backup>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Microsoft OneDrive</product>
<major>24</major>
<minor>76</minor>
<service>414</service>
<patch>5</patch>
<raw-version>24.076.0414.0005</raw-version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
<last-backup-time/>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows Backup and Restore</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1</patch>
<raw-version>10.0.17763.1</raw-version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
<last-backup-time/>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows File History</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1</patch>
<raw-version>10.0.17763.1</raw-version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
<last-backup-time/>
</software>
</softwares>
</disk-backup>
<disk-encryption>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>BitLocker Drive Encryption</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1</patch>
<raw_version>10.0.17763.1</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
<locations>
<location>
<path>C:\</path>
<status>encrypted</status>
</location>
</locations>
</software>
</softwares>
</disk-encryption>
<data_loss_prevention>
<softwares/>
</data_loss_prevention>
<patch_management>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows Update Agent</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1852</patch>
<raw_version>10.0.17763.1852</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</patch_management>
<public_file_sharing>
<softwares/>
</public_file_sharing>
<antiphishing>
<softwares>
<software>
<vendor>Google Inc.</vendor>
<product>Google Chrome</product>
<major>124</major>
<minor>0</minor>
<service>6367</service>
<patch>119</patch>
<raw_version>124.0.6367.119</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Internet Explorer</product>
<major>11</major>
<minor>1790</minor>
<service>17763</service>
<patch>0</patch>
<raw_version>11.1790.17763.0</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Internet Explorer</product>
<major>11</major>
<minor>1790</minor>
<service>17763</service>
<patch>0</patch>
<raw_version>11.1790.17763.0</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Microsoft Edge</product>
<major>124</major>
<minor>0</minor>
<service>2478</service>
<patch>80</patch>
<raw_version>124.0.2478.80</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</antiphishing>
<browser>
<softwares>
<software>
<vendor>Google Inc.</vendor>
<product>Google Chrome</product>
<major>124</major>
<minor>0</minor>
<service>6367</service>
<patch>119</patch>
<raw_version>124.0.6367.119</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Internet Explorer</product>
<major>11</major>
<minor>1790</minor>
<service>17763</service>
<patch>0</patch>
<raw_version>11.1790.17763.0</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Internet Explorer</product>
<major>11</major>
<minor>1790</minor>
<service>17763</service>
<patch>0</patch>
<raw_version>11.1790.17763.0</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Microsoft Edge</product>
<major>124</major>
<minor>0</minor>
<service>2478</service>
<patch>80</patch>
<raw_version>124.0.2478.80</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</browser>
<health_agent>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Windows Security Health Agent</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1</patch>
<raw_version>10.0.17763.1</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</health_agent>
<virtual_machine>
<softwares/>
</virtual_machine>
<cloud_storage>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Microsoft OneDrive</product>
<major>24</major>
<minor>76</minor>
<service>414</service>
<patch>5</patch>
<raw_version>24.076.0414.0005</raw_version>
<is-running>true</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</cloud_storage>
<messenger>
<softwares/>
</messenger>
<remote_control>
<softwares>
<software>
<vendor>Microsoft Corporation</vendor>
<product>Remote Desktop Connection</product>
<major>10</major>
<minor>0</minor>
<service>17763</service>
<patch>1</patch>
<raw_version>10.0.17763.1</raw_version>
<is-running>false</is-running>
<is-configured>true</is-configured>
<is-installed>true</is-installed>
</software>
</softwares>
</remote_control>
<management-status>false</management-status>
<custom>
<windows/>
<process/>
</custom>
<general>
<user-name>IEUser</user-name>
<hostname>WIN10-BITLOCKER</hostname>
<windows-domain>WORKGROUP</windows-domain>
<os-major>10</os-major>
<os-minor>0</os-minor>
<os-service>17763</os-service>
<os-patch>0</os-patch>
<os-product>Microsoft Windows 10 Enterprise Evaluation</os-product>
<os-vendor>Microsoft Corporation</os-vendor>
<host-id>406A27228DBE4BEFA1F5A0BEA27ABED5</host-id>
<tpm-enabled/>
</general>
<context>
<generation-time>1715202751</generation-time>
<report-time>1715202764</report-time>
<device-tunnel-ip>192.168.104.6</device-tunnel-ip>
<device-mac>0C-6A-27-22-00-00</device-mac>
<vsac-version>7.8.8</vsac-version>
<realtime-posture>false</realtime-posture>
</context>
</eip>
Supported Software Information
Releases 11.3.1 and later support all content described in this article.
